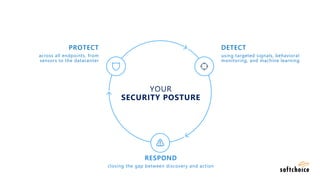
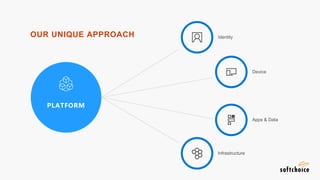
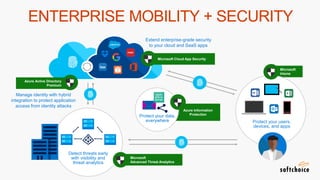
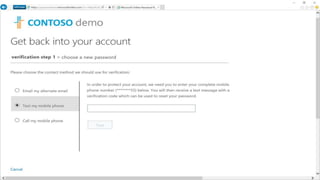
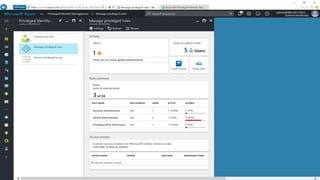
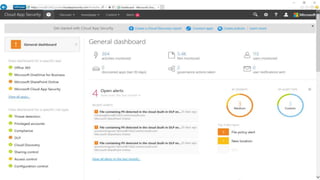
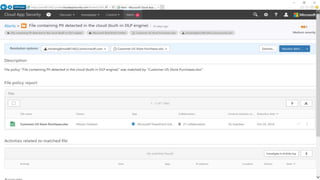
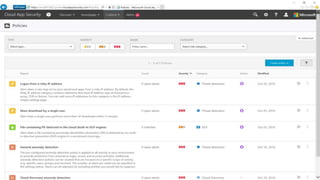
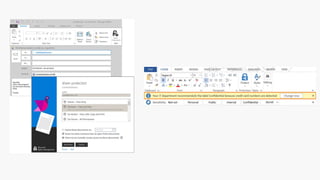
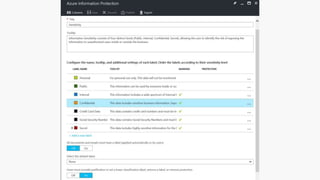
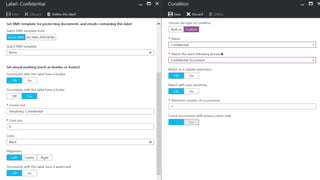
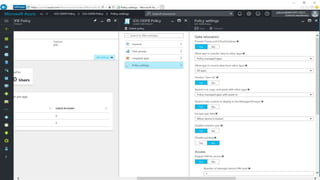
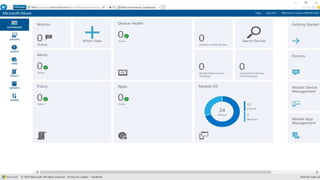
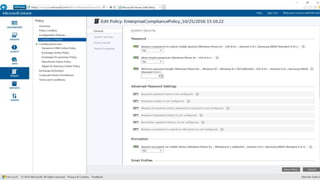
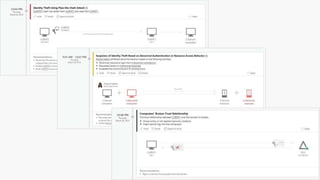
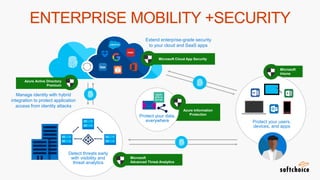
The webinar covers enterprise mobility and security (EM+S), emphasizing the importance of protecting data and detecting threats through solutions like Microsoft Intune and Azure Active Directory. Key topics include the challenges of mobility, the risks of data breaches, and the prevalence of shadow IT among employees. The presentation encourages attendees to engage with Softchoice for further assistance or queries related to EM+S.