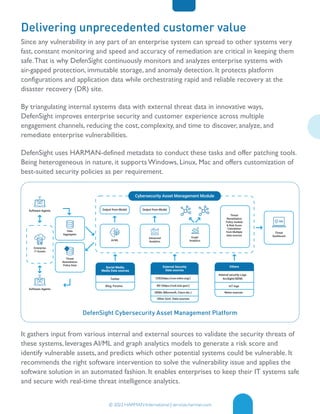
Harman Defensight is a comprehensive cybersecurity asset management platform designed to enhance cyber resilience for enterprises by addressing vulnerabilities in IT and OT systems using real-time threat intelligence and automated remediation. With the increasing complexity of cybersecurity risks due to remote work, data proliferation, and evolving attack tactics, Defensight provides ongoing monitoring, compliance analysis, and predictive threat assessment to safeguard sensitive data and minimize disruptions. The platform aims to improve organizations' security postures and streamline their cybersecurity efforts, empowering them to navigate digital transformation confidently.