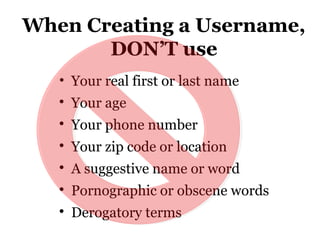
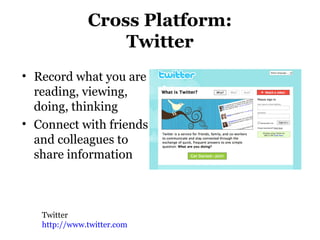
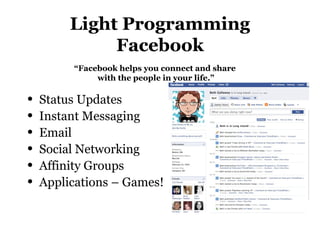
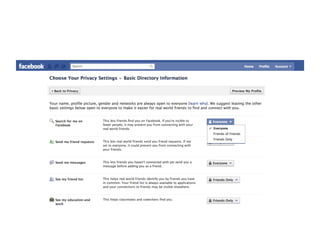
This document provides information on social networking sites like Facebook, including tips for safe usage. It discusses features of sites like Facebook, YouTube, and Twitter. It also covers topics like cyberbullying, online privacy and safety tips for teens. Recommendations are given for creating secure usernames and passwords. The document aims to help demystify social media and networking sites while promoting their safe and responsible use.