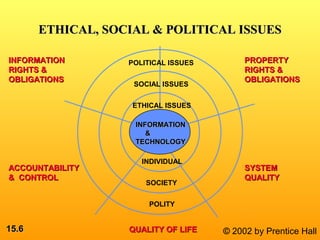
This document discusses the ethical and social impacts of information systems. It covers several topics, including privacy and intellectual property rights, accountability and control issues, system quality concerns, and the effects of technology on quality of life. The goals are to analyze ethical and social problems raised by information systems, identify the moral dimensions of the information society, and examine principles for conducting ethical analysis and designing corporate policies.