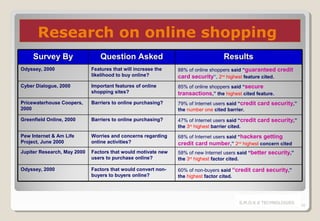
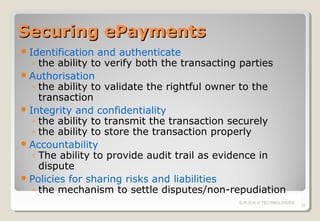
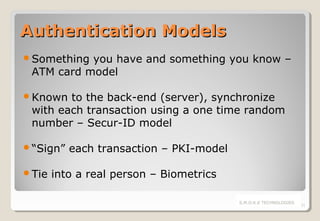
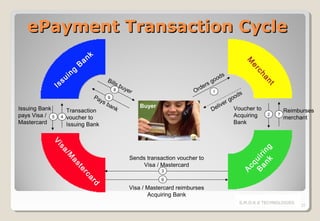
The document discusses electronic payment systems, highlighting their evolution, mechanisms, and channels while addressing current challenges such as security, infrastructure complexity, and lack of widespread adoption. Various payment instruments are detailed, including credit and debit cards, digital cash, and mobile wallets, alongside the associated risks in online transactions. Solutions for securing electronic payments, authentication models, and the importance of trust among transaction parties are emphasized.