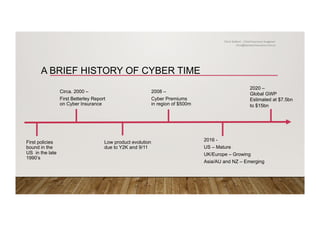
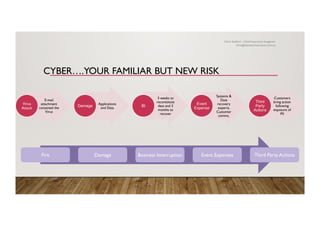
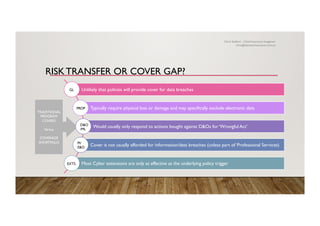
The document discusses the history and importance of cyber insurance, highlighting its evolution since the late 1990s and the increasing market demand due to rising cyber risks. It outlines reasons for purchasing cyber insurance, including privacy legislation, risk management frameworks, and exposure to cyber threats, while also explaining various scenarios that illustrate potential losses. The text emphasizes the gaps in traditional insurance coverage regarding cyber incidents and the need for specialized cyber insurance to address these risks.