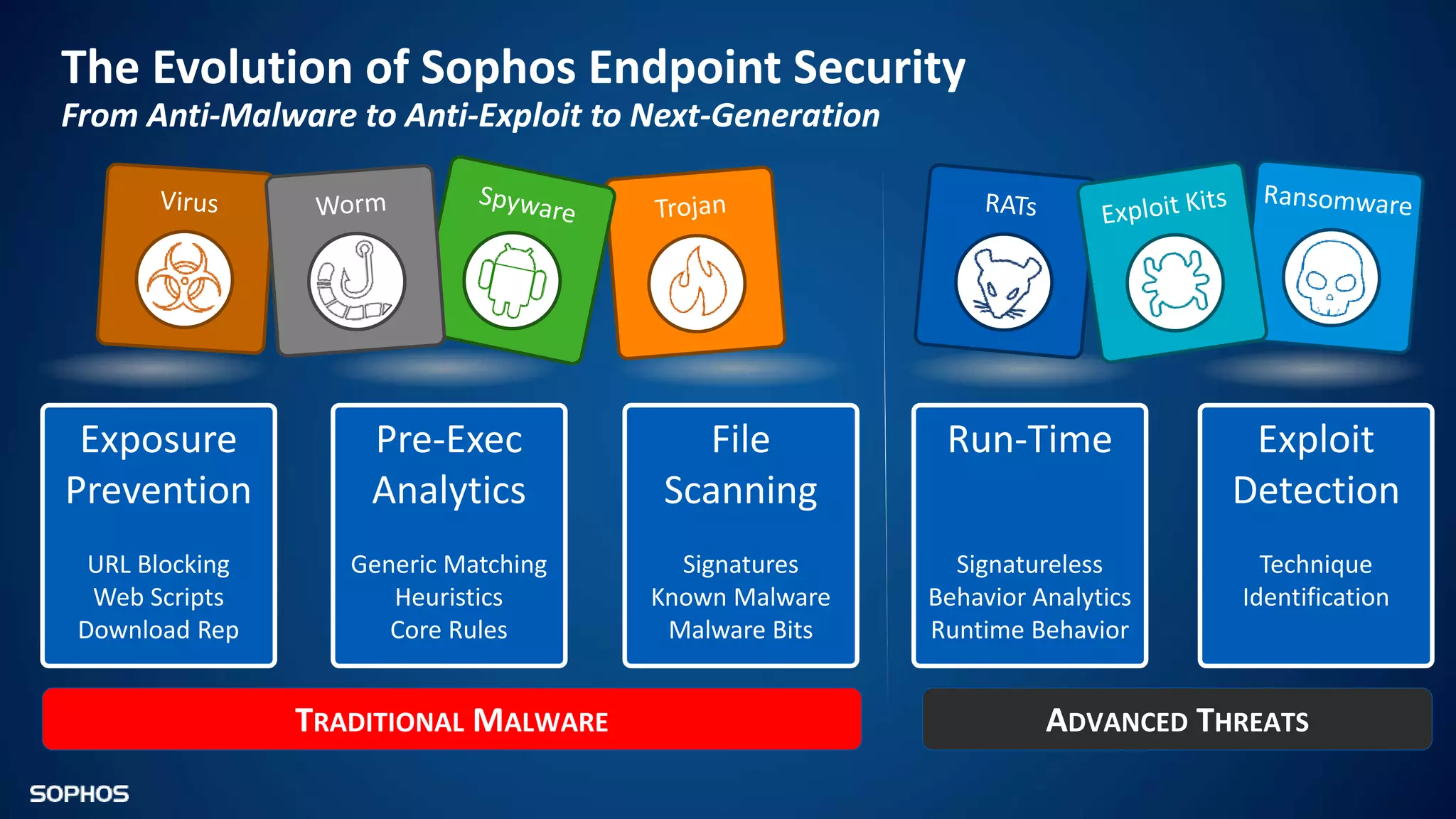
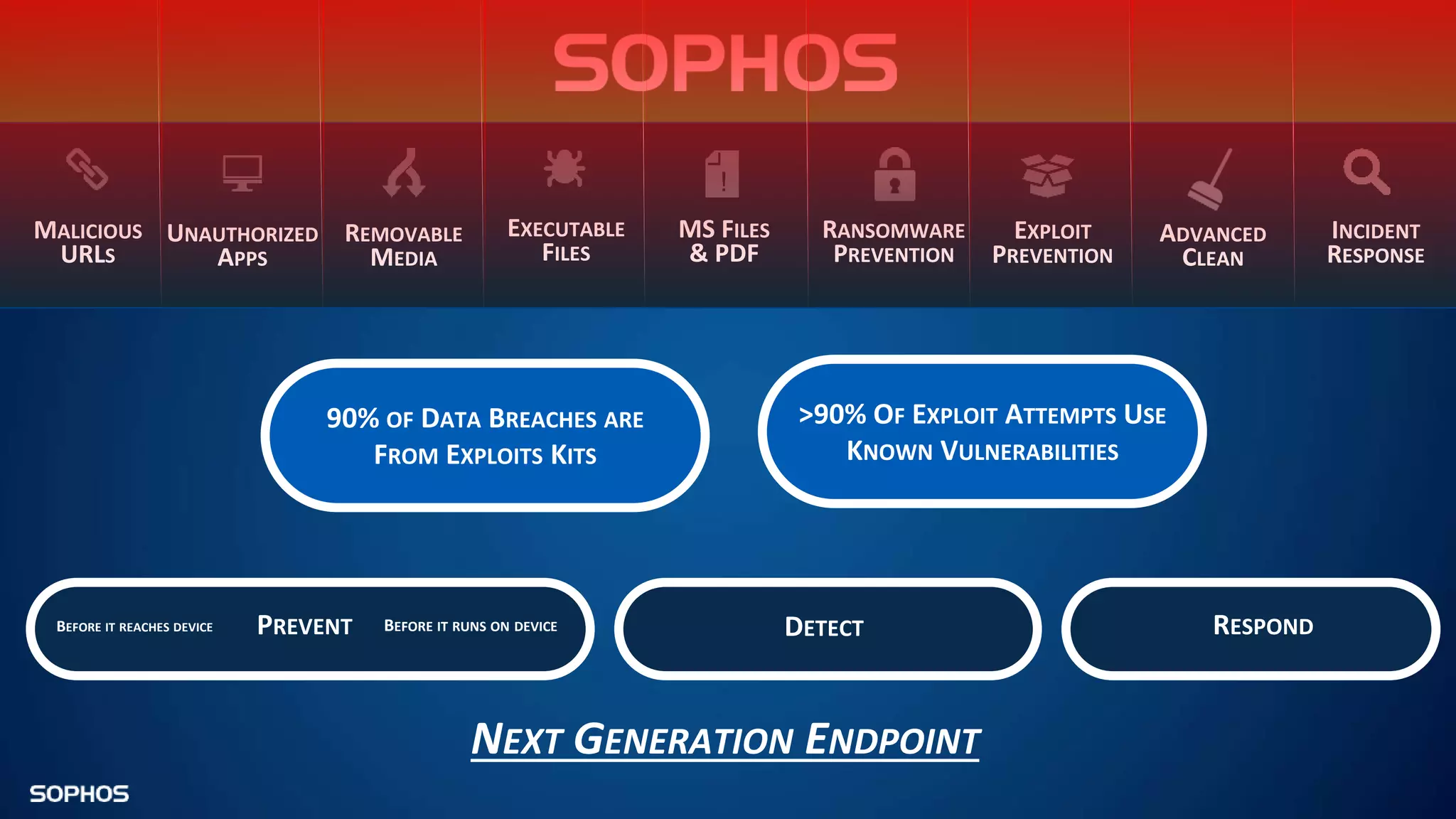
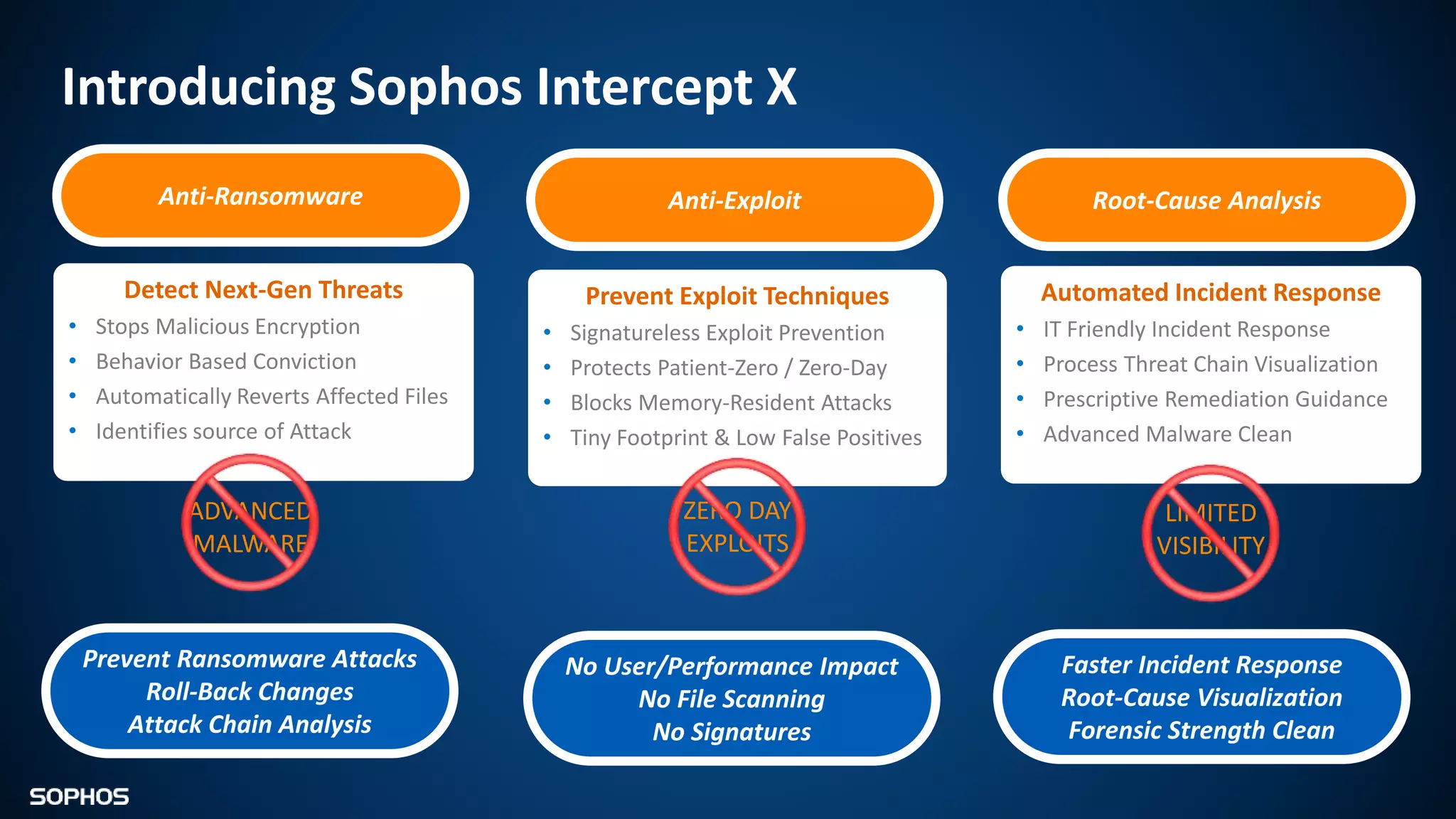
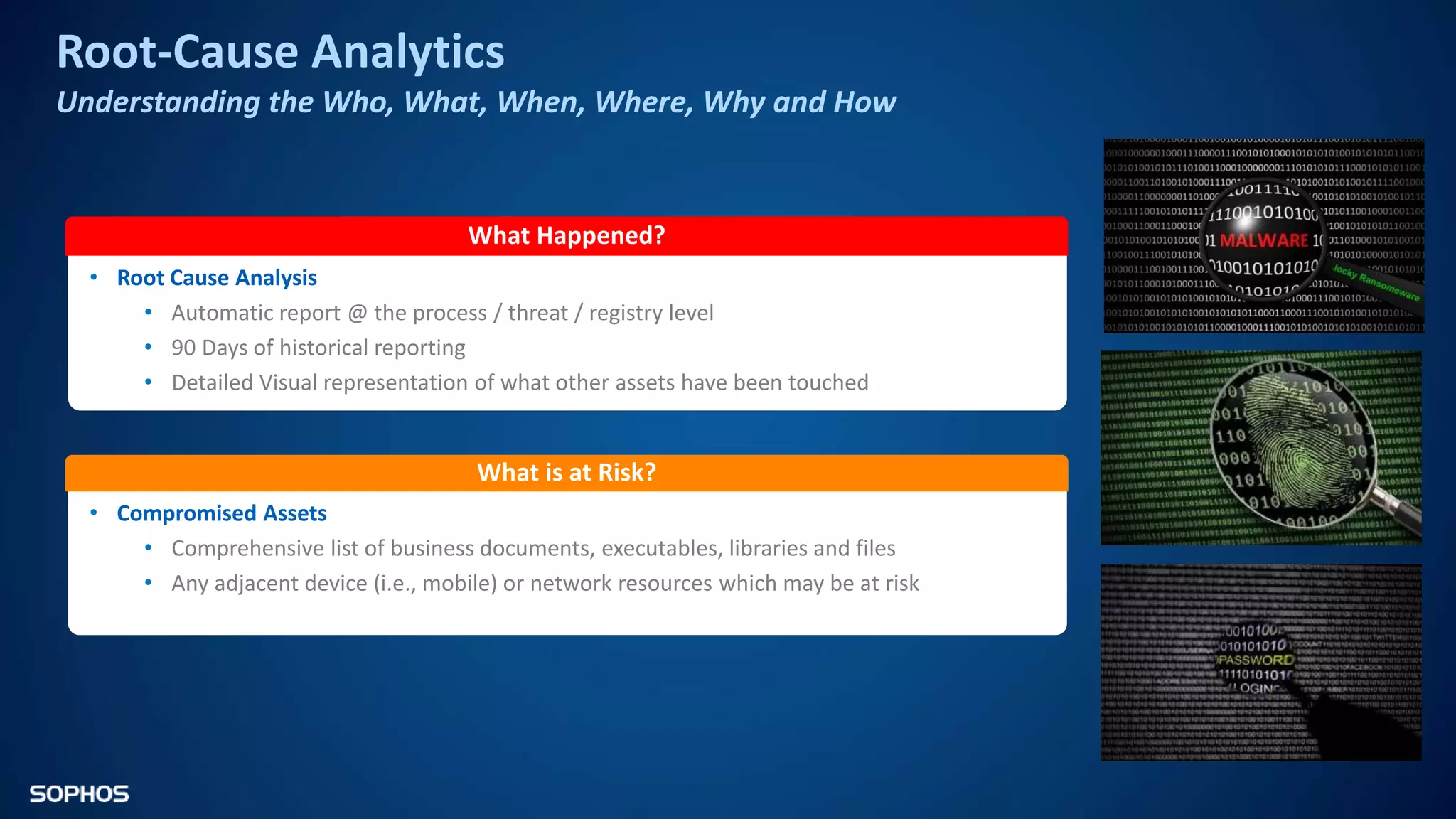
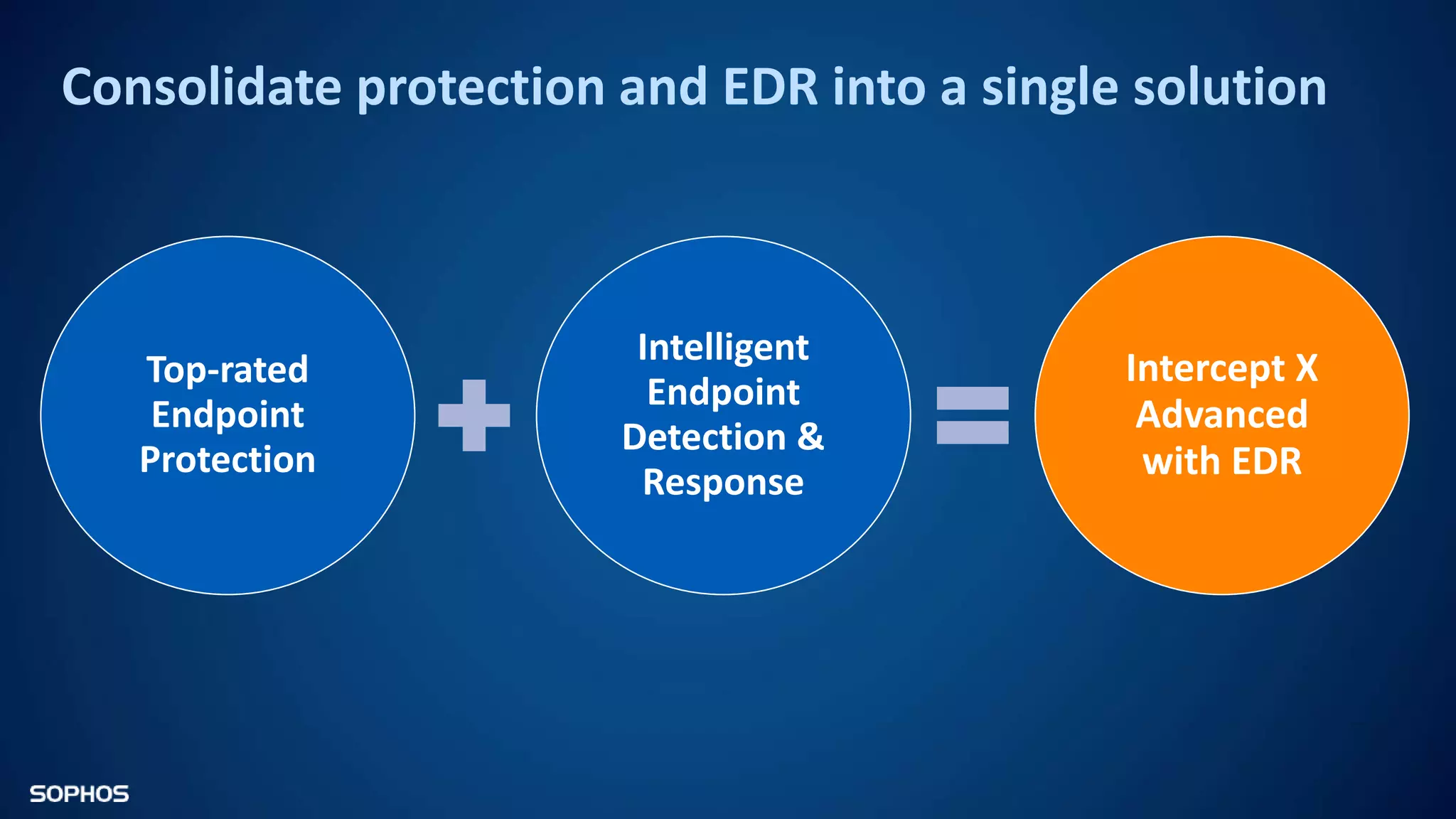
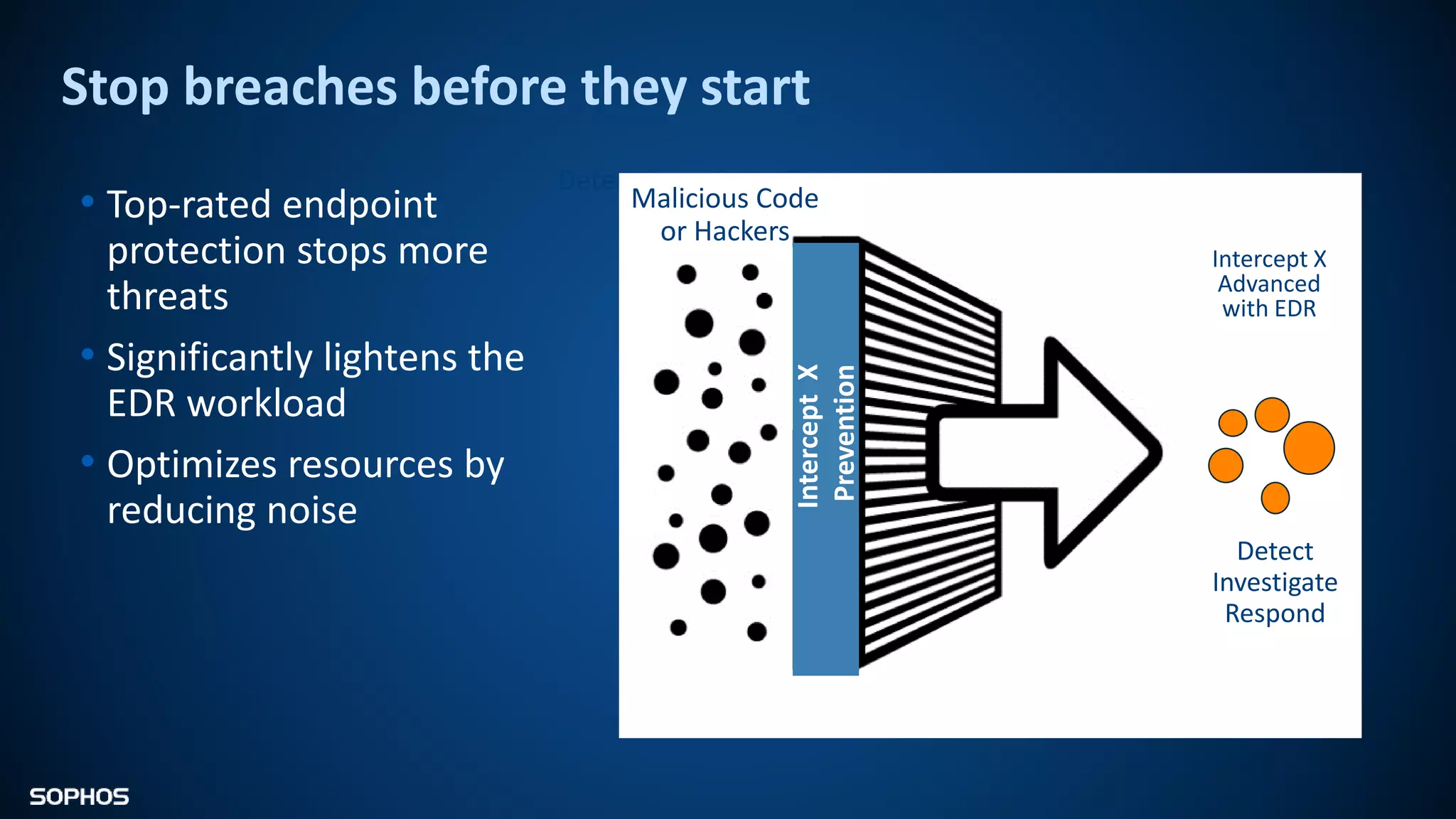
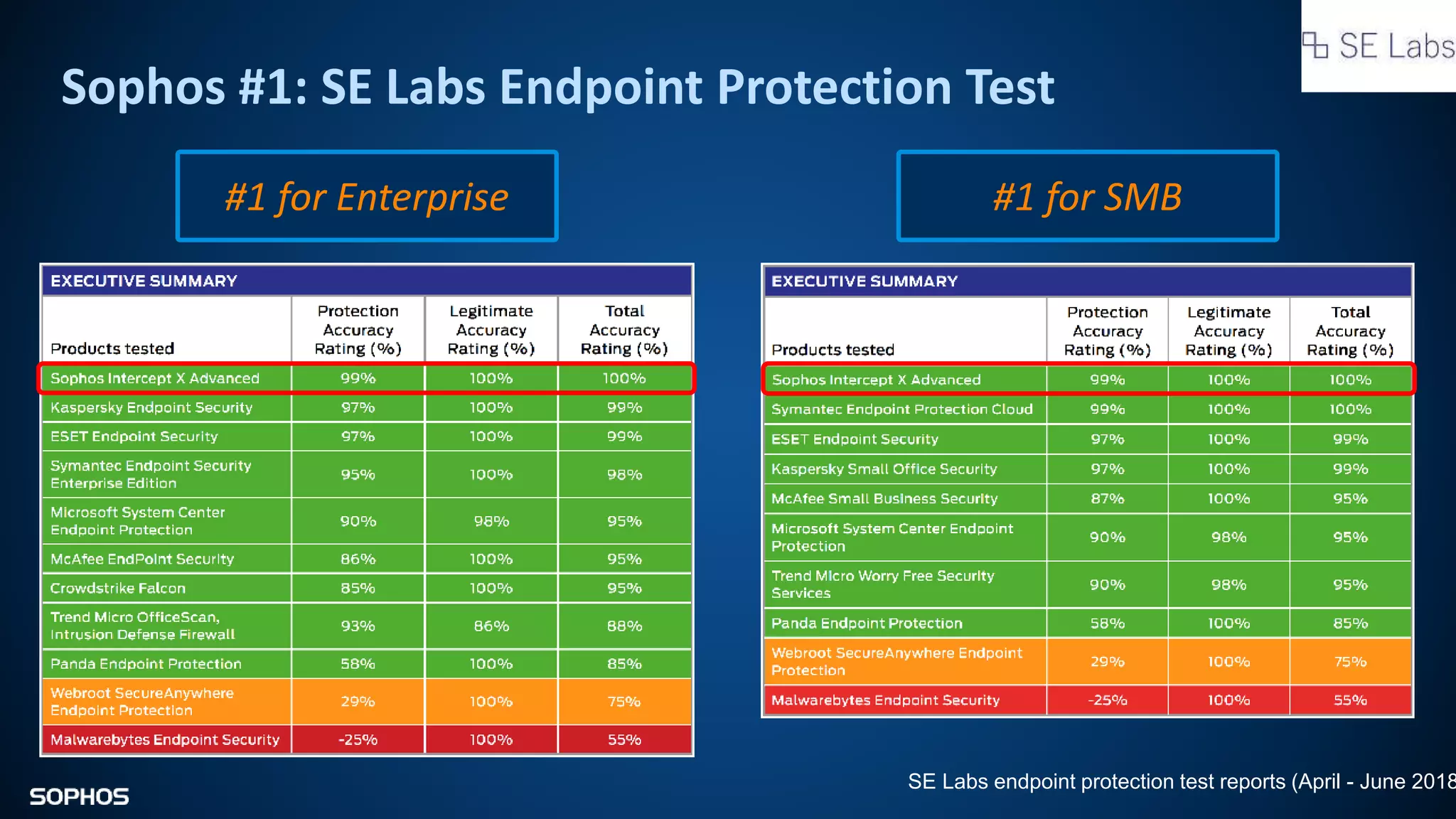
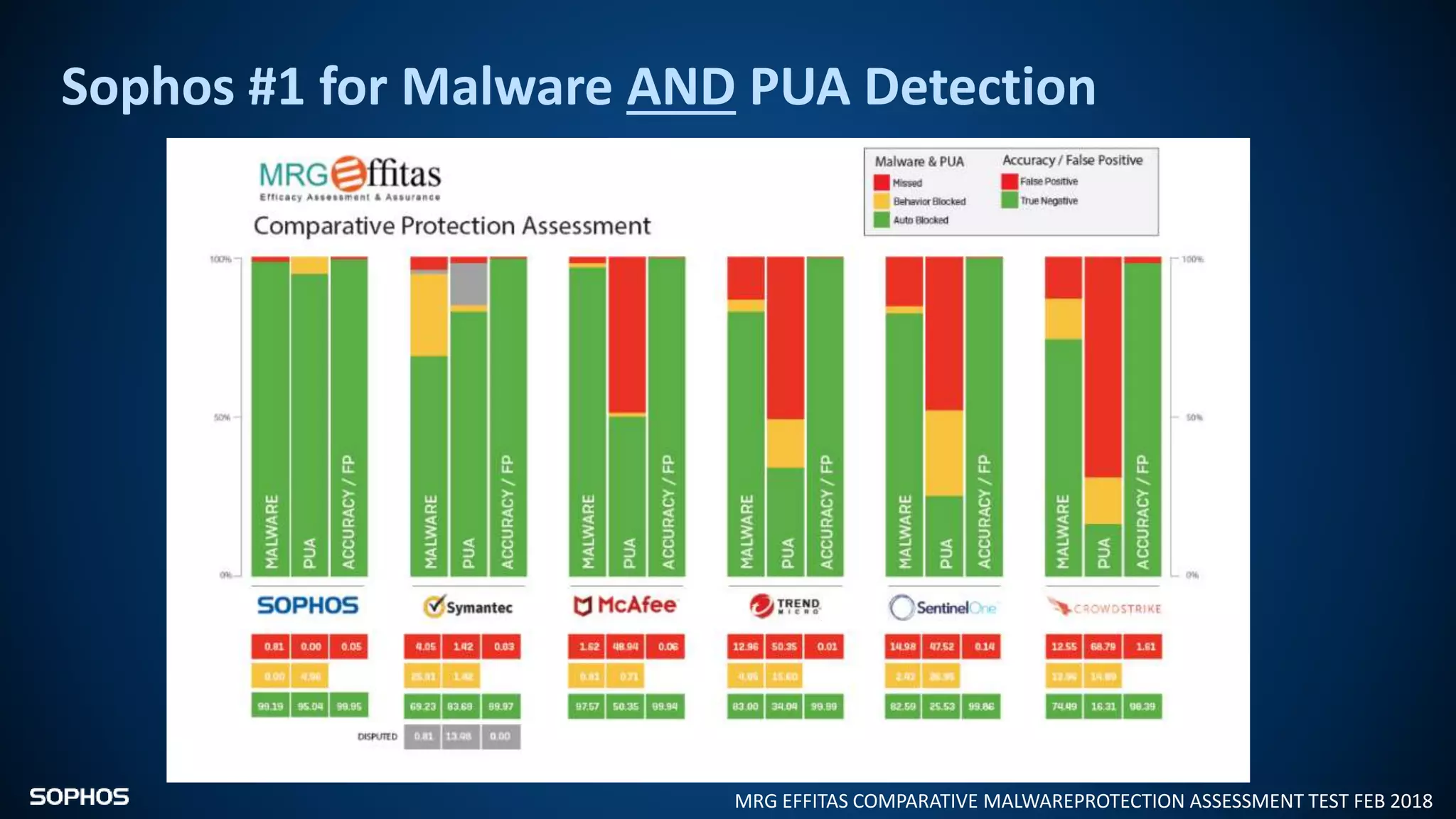
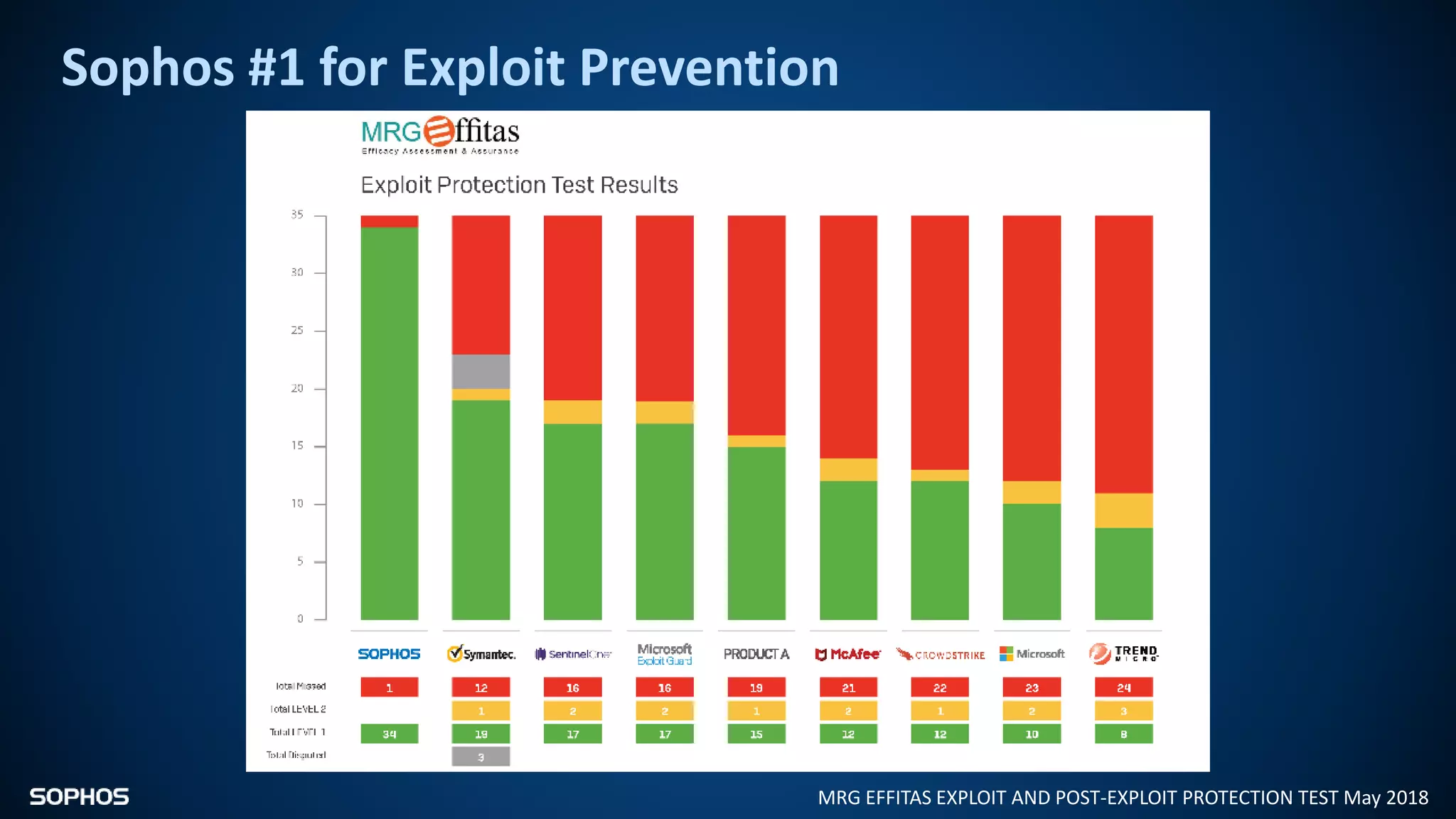
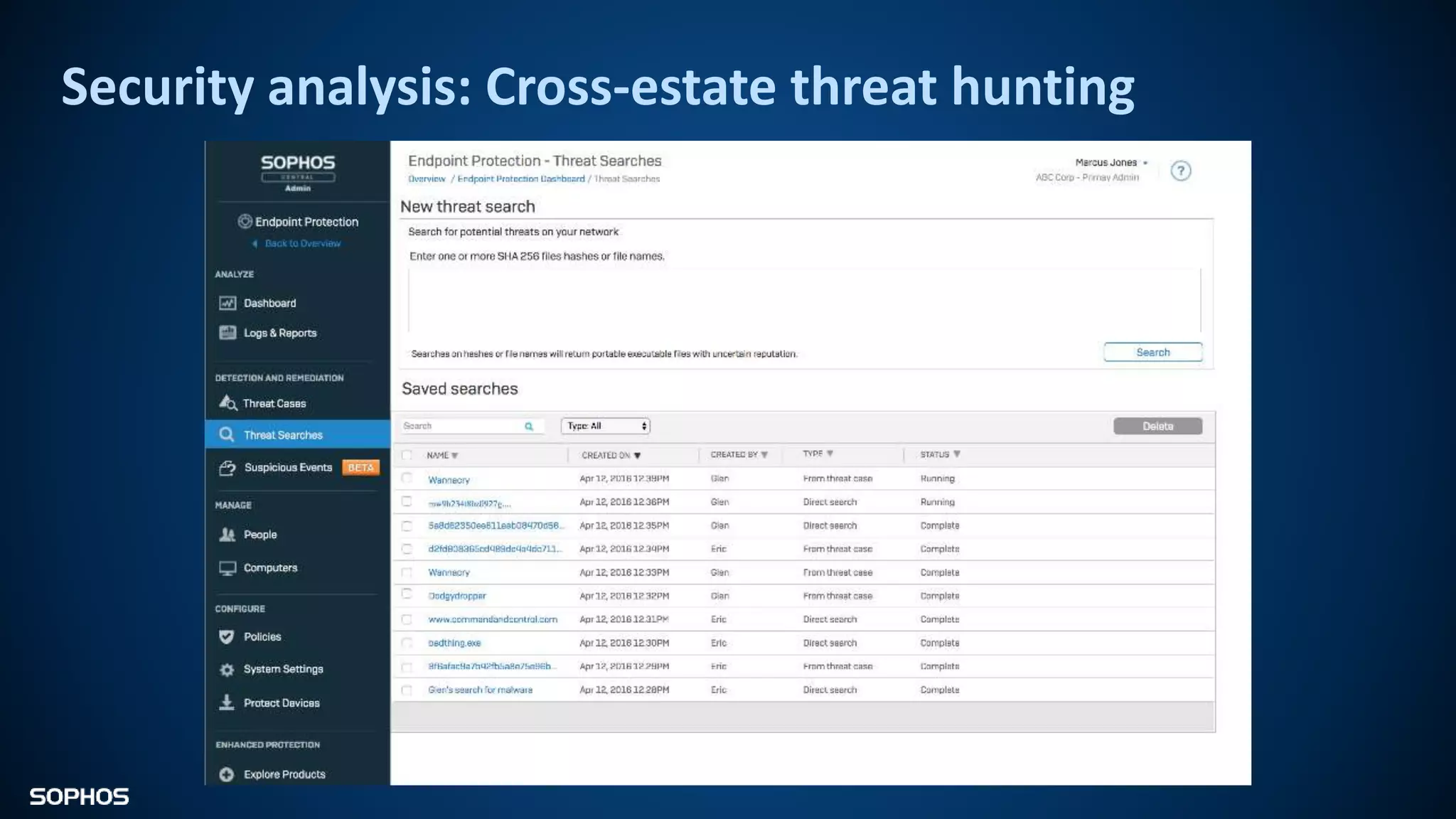
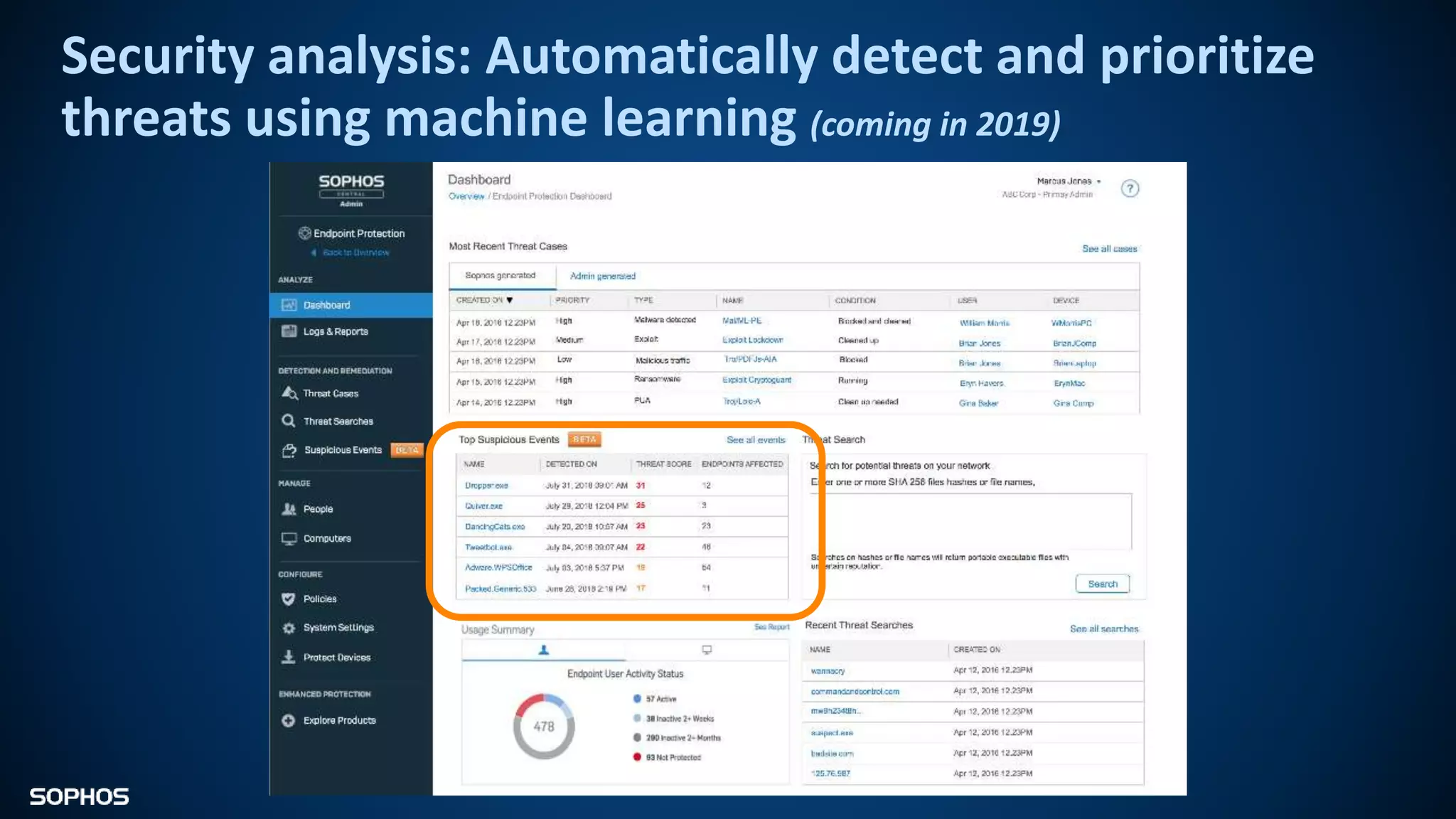
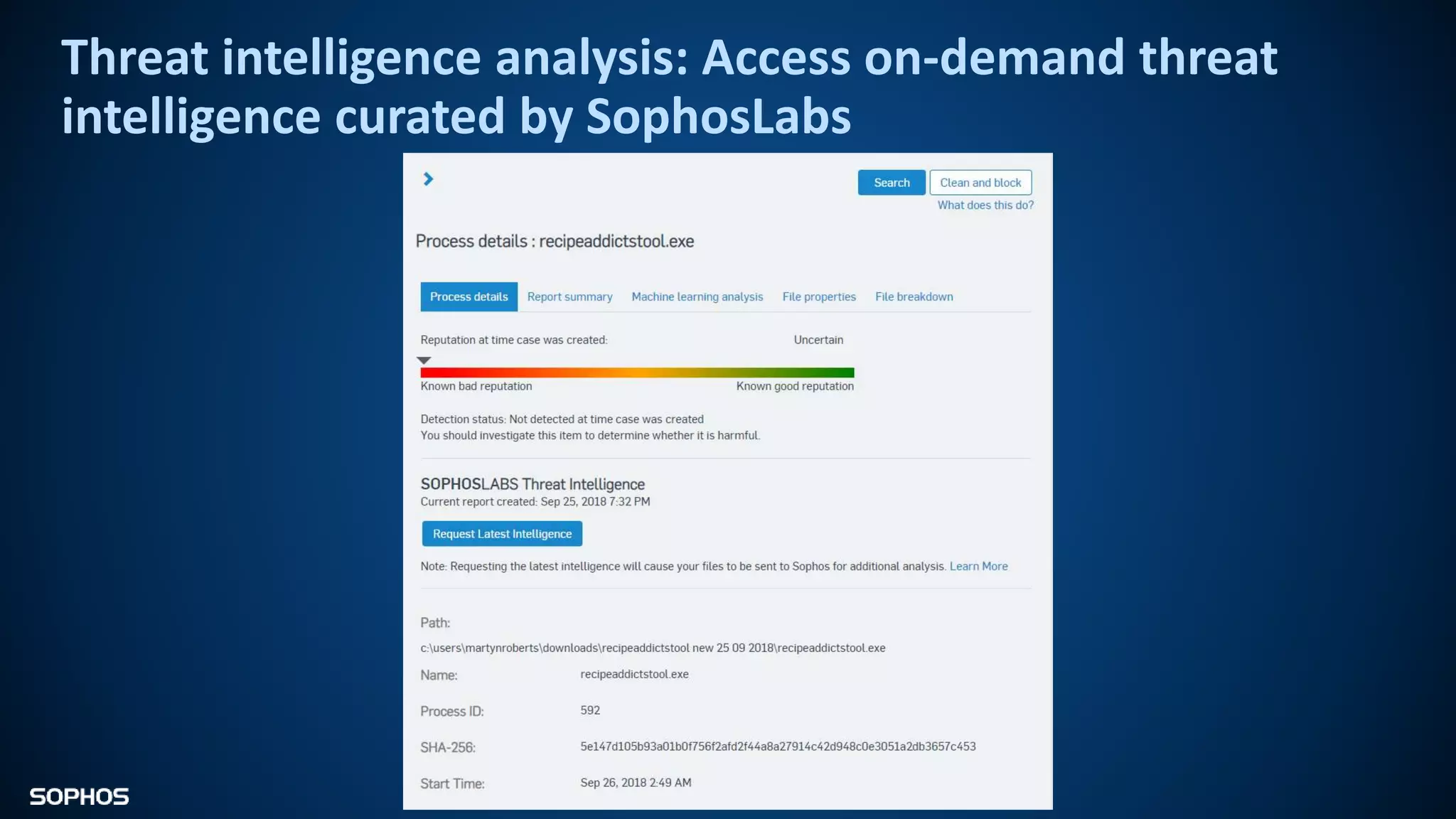
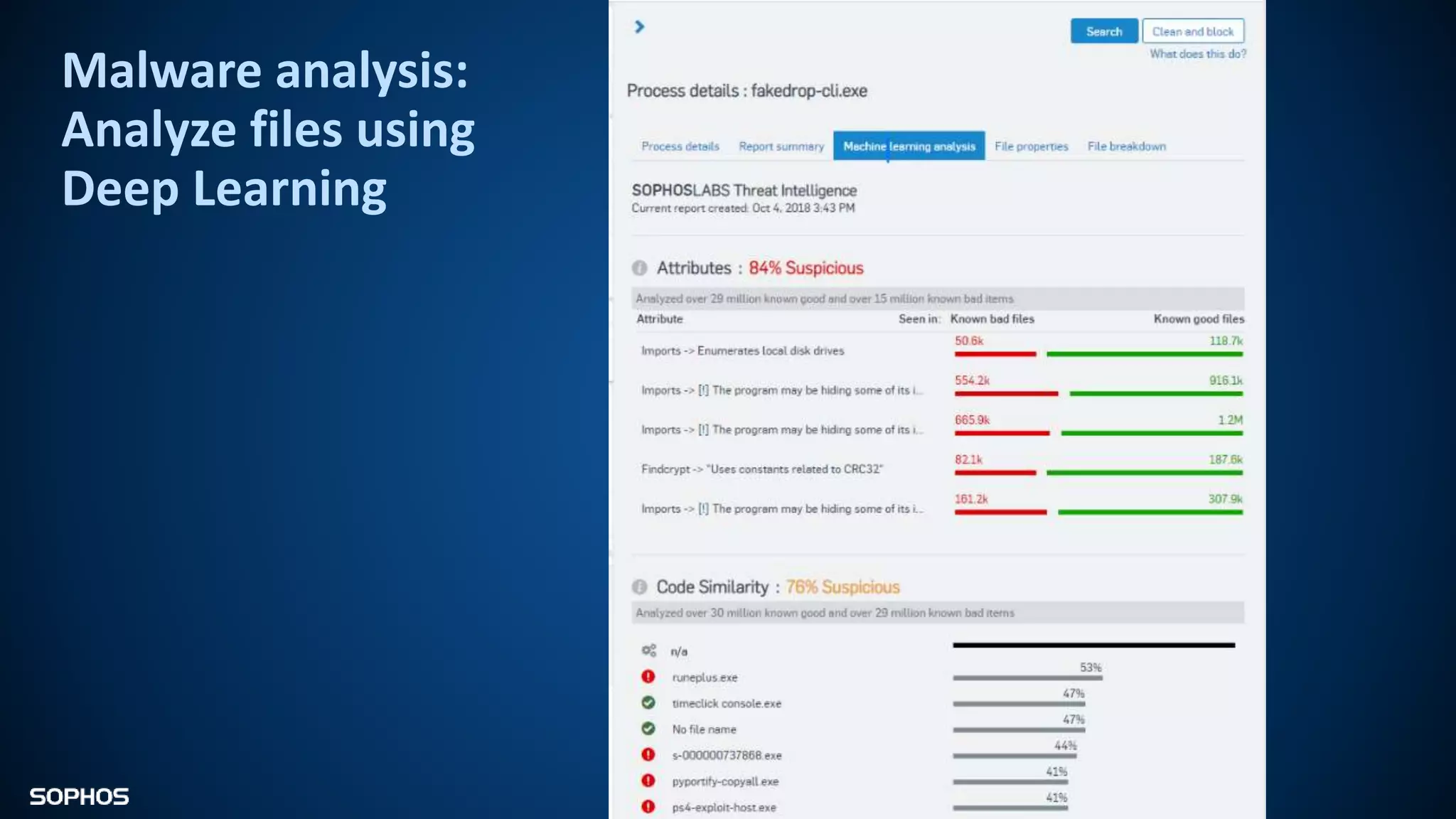
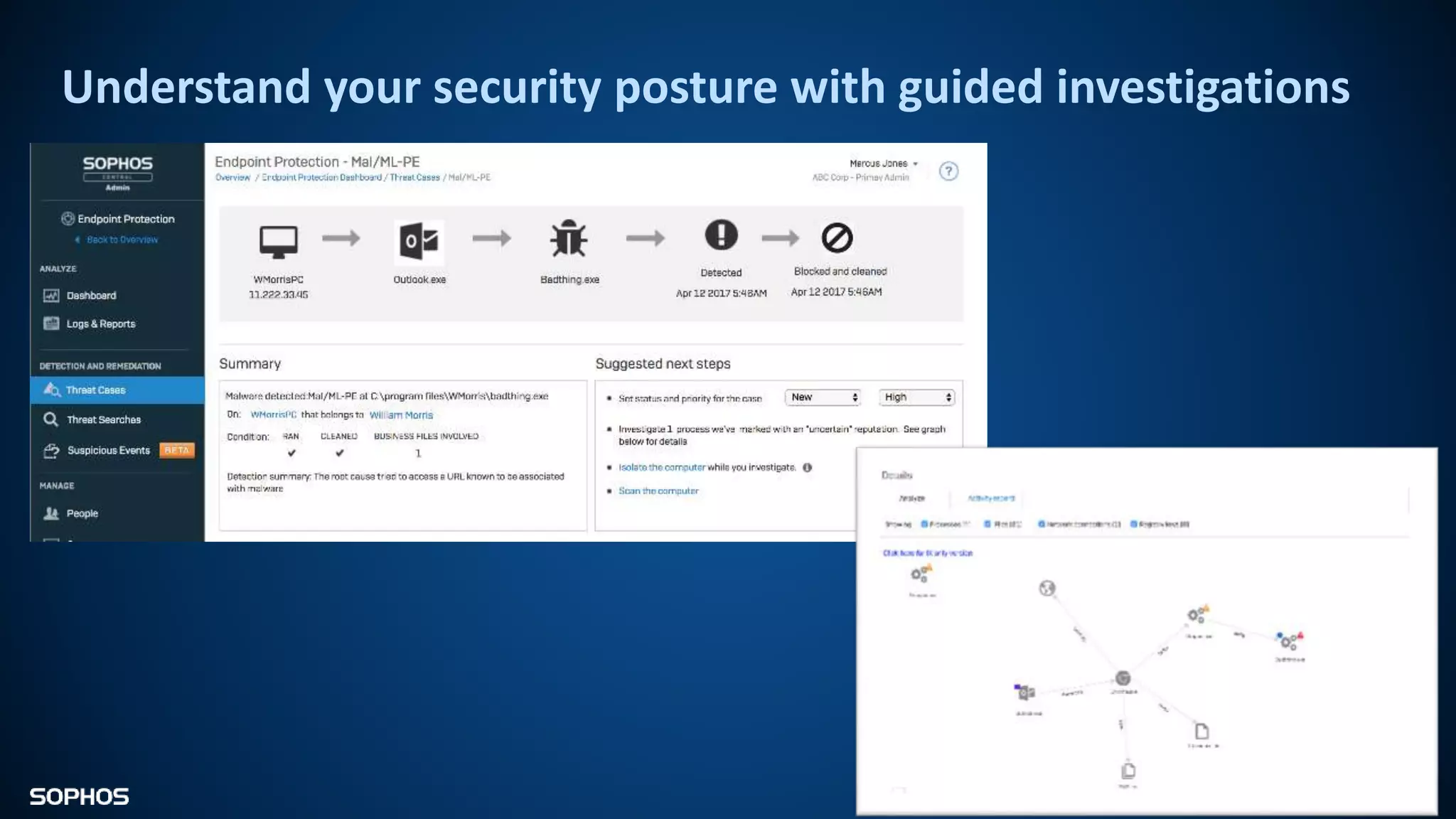
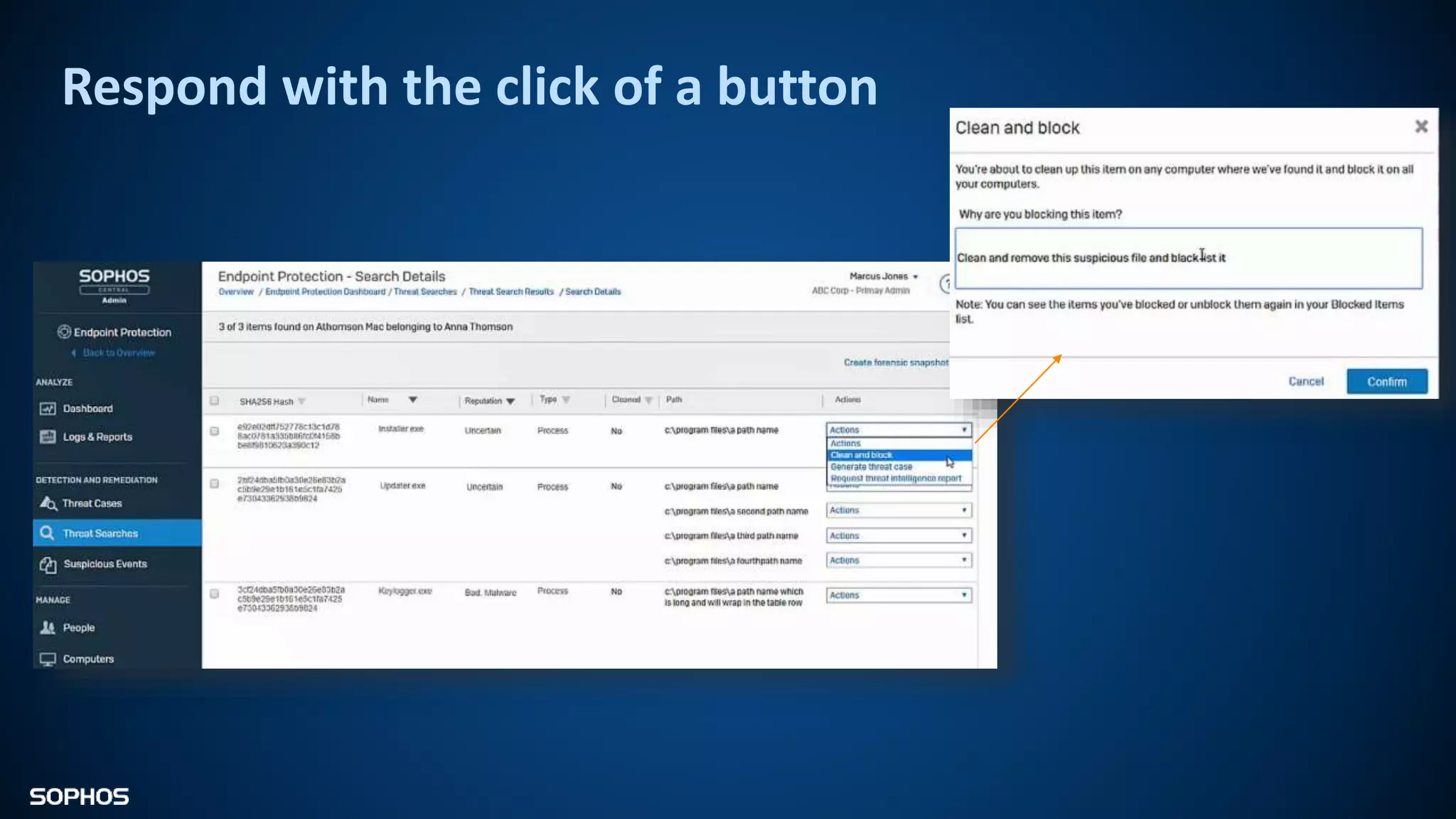
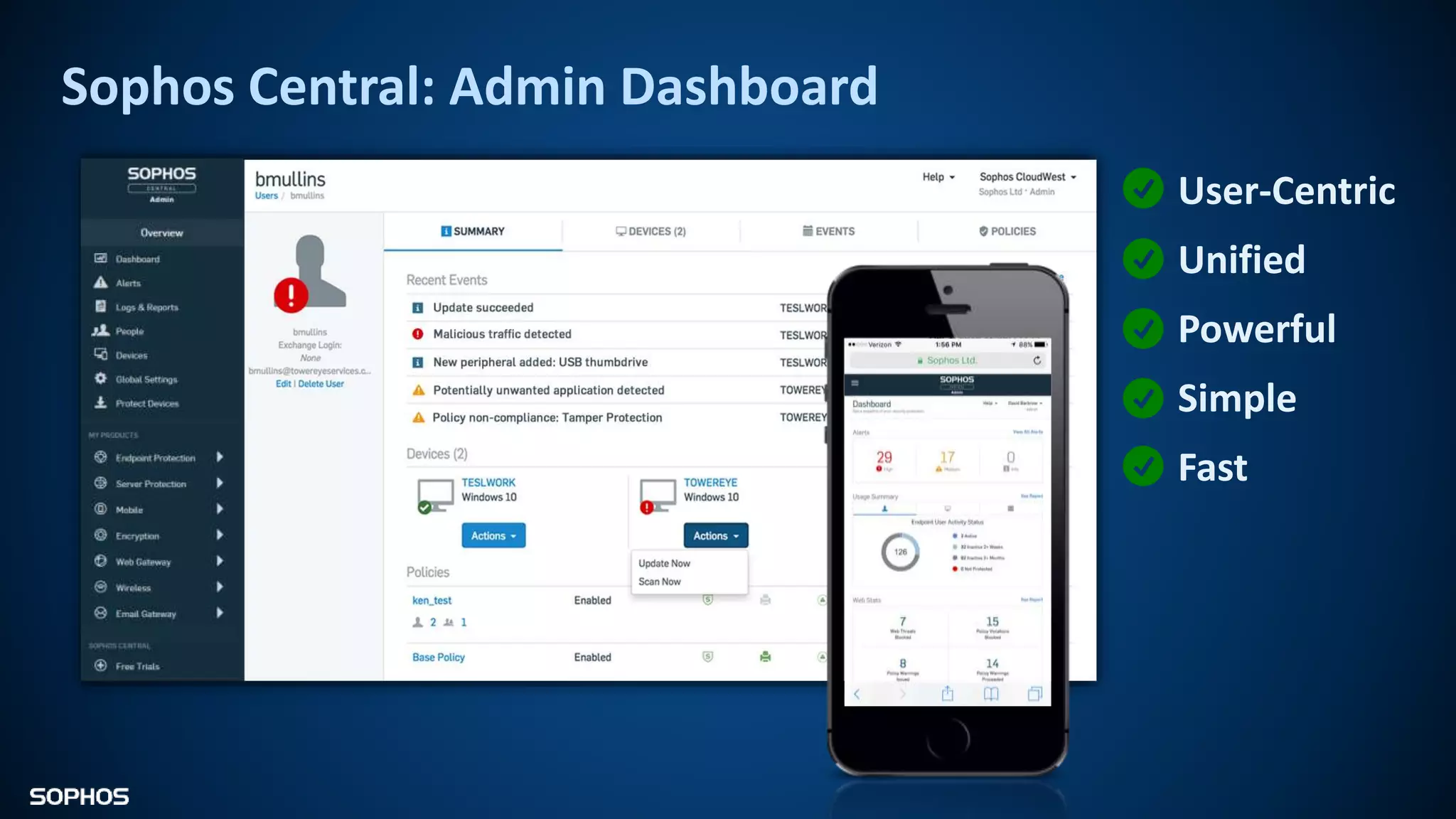
Intercept X Advanced with EDR provides next-generation endpoint protection, detection and response capabilities. It uses signatureless exploit prevention and behavior-based detection to stop zero-day and advanced threats. The solution offers guided incident response to help understand the full attack chain and scope of incidents. Root cause analysis and automated remediation aid investigation and response. Its integration of top-rated endpoint protection and intelligent EDR aims to reduce security workload through stronger prevention and expertise-adding features rather than extra headcount.