The document discusses Intel's vision for pervasive computing by 2015, including:
1) Over 1 billion additional users and more than 15 billion connected devices will require 8x more network capacity, 16x more storage, and 20x more compute capacity.
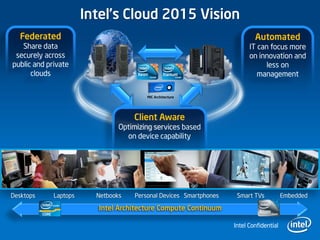
2) Intel's cloud vision includes federating data securely across public and private clouds and automating IT systems for increased innovation and reduced management.
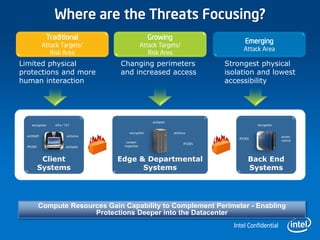
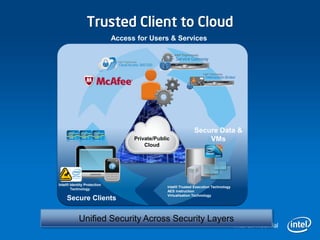
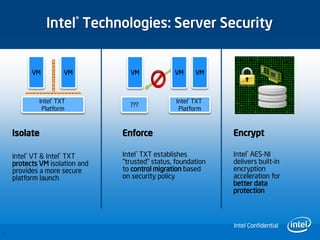
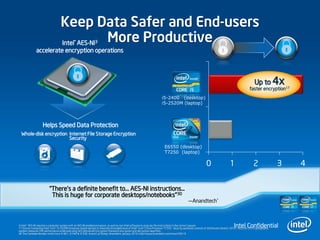
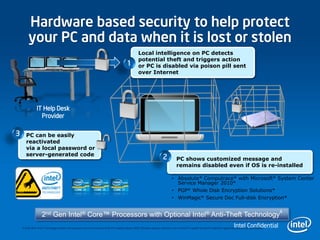
3) Intel technologies like TXT, VT, and AES-NI help provide security across layers from clients to the cloud by isolating VMs, enforcing trusted platforms, and accelerating encryption.