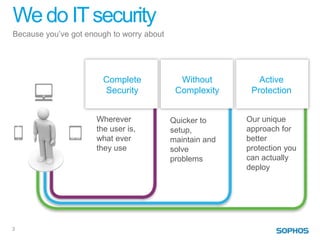
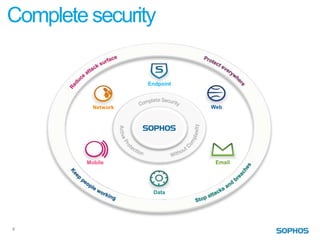
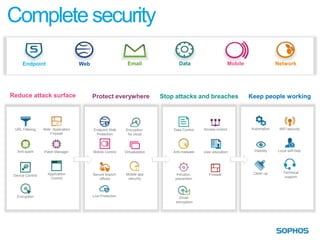
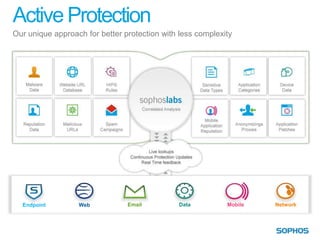
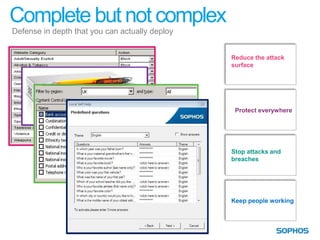
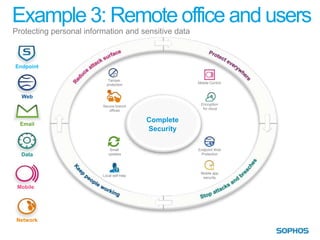
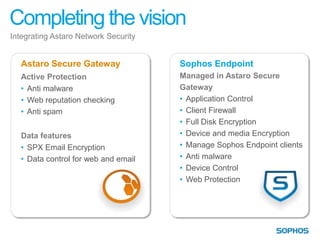
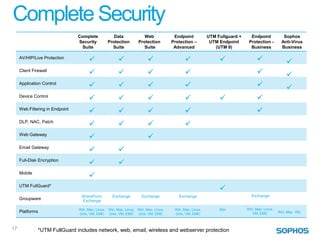
This document summarizes the services and approach of Complete Security, a security company. They focus on protecting users from evolving threats while regulations grow. Their approach provides complete security across endpoints, network, web, email, mobile, and data without complexity. They actively protect users wherever they are and whatever they use through technologies like URL filtering, encryption, anti-malware, and more. Their goal is to reduce the attack surface, protect everywhere, stop attacks and breaches, and keep people working.