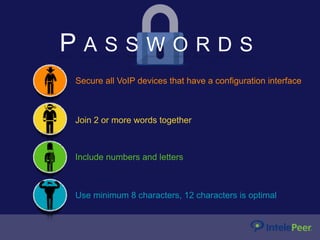
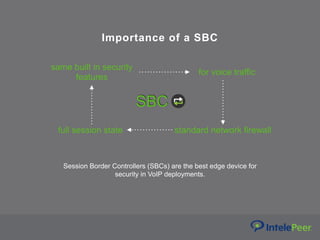
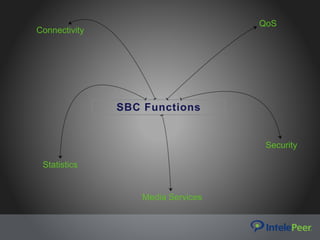
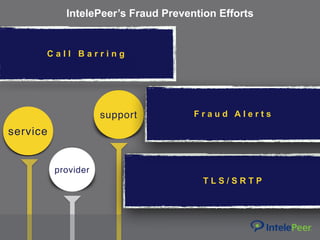
This webinar discusses VoIP security best practices. It outlines common VoIP security threats like call interception, denial of service attacks, and data exfiltration. It then provides recommendations for securing VoIP systems, including using strong passwords, keeping systems updated, limiting remote access and management, and using a session border controller. The webinar emphasizes the importance of working with a SIP provider that follows security best practices.