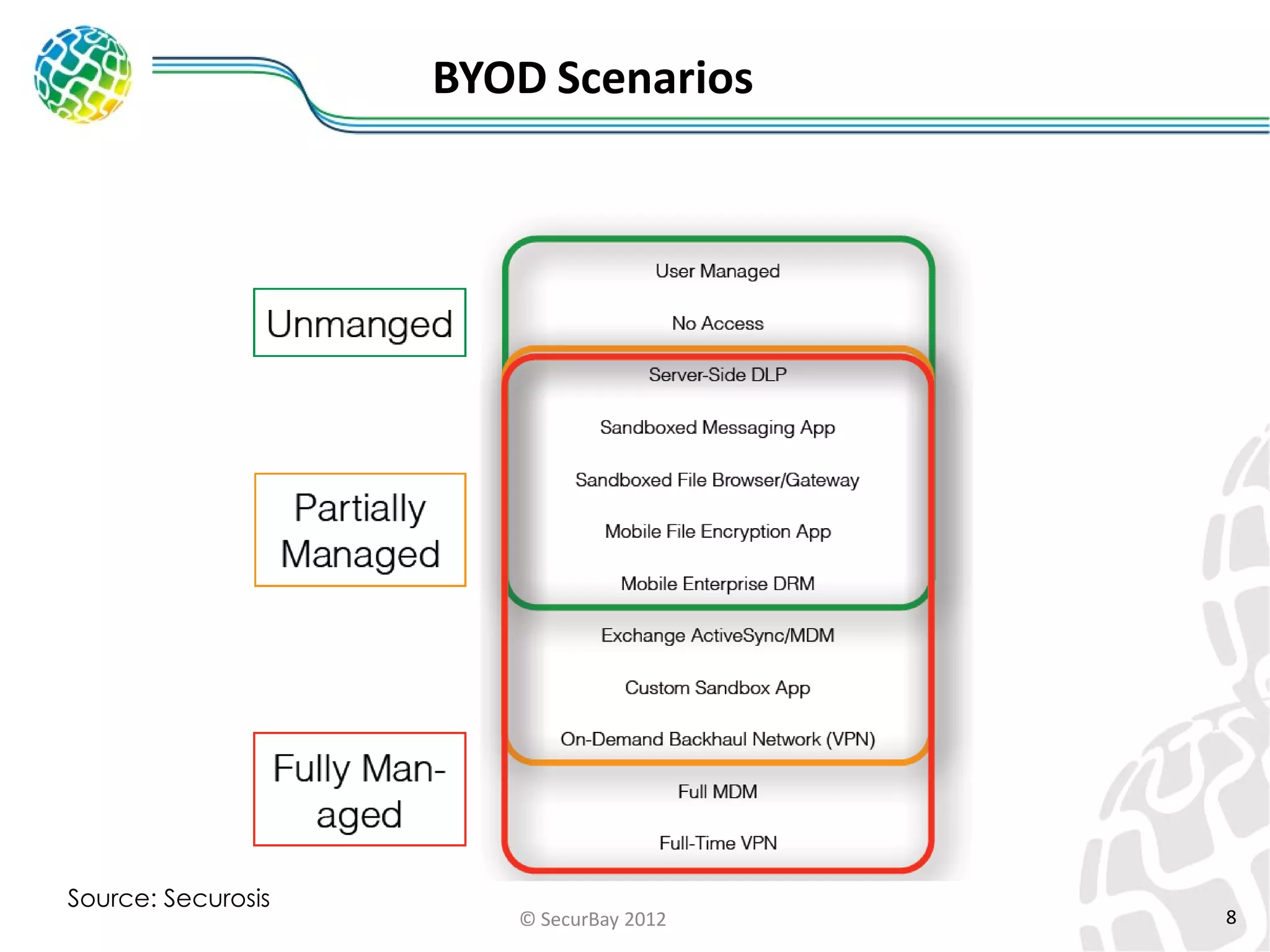
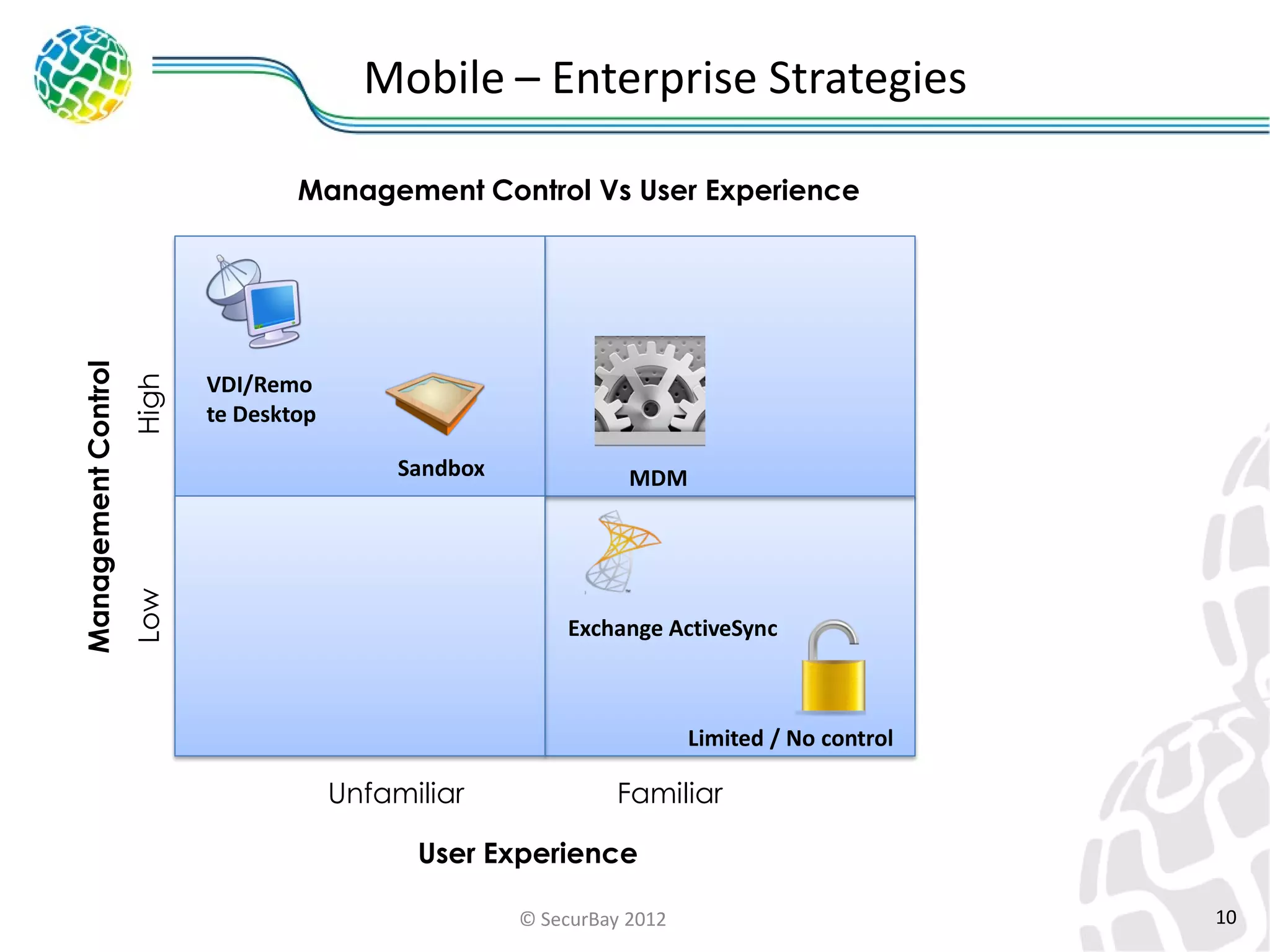
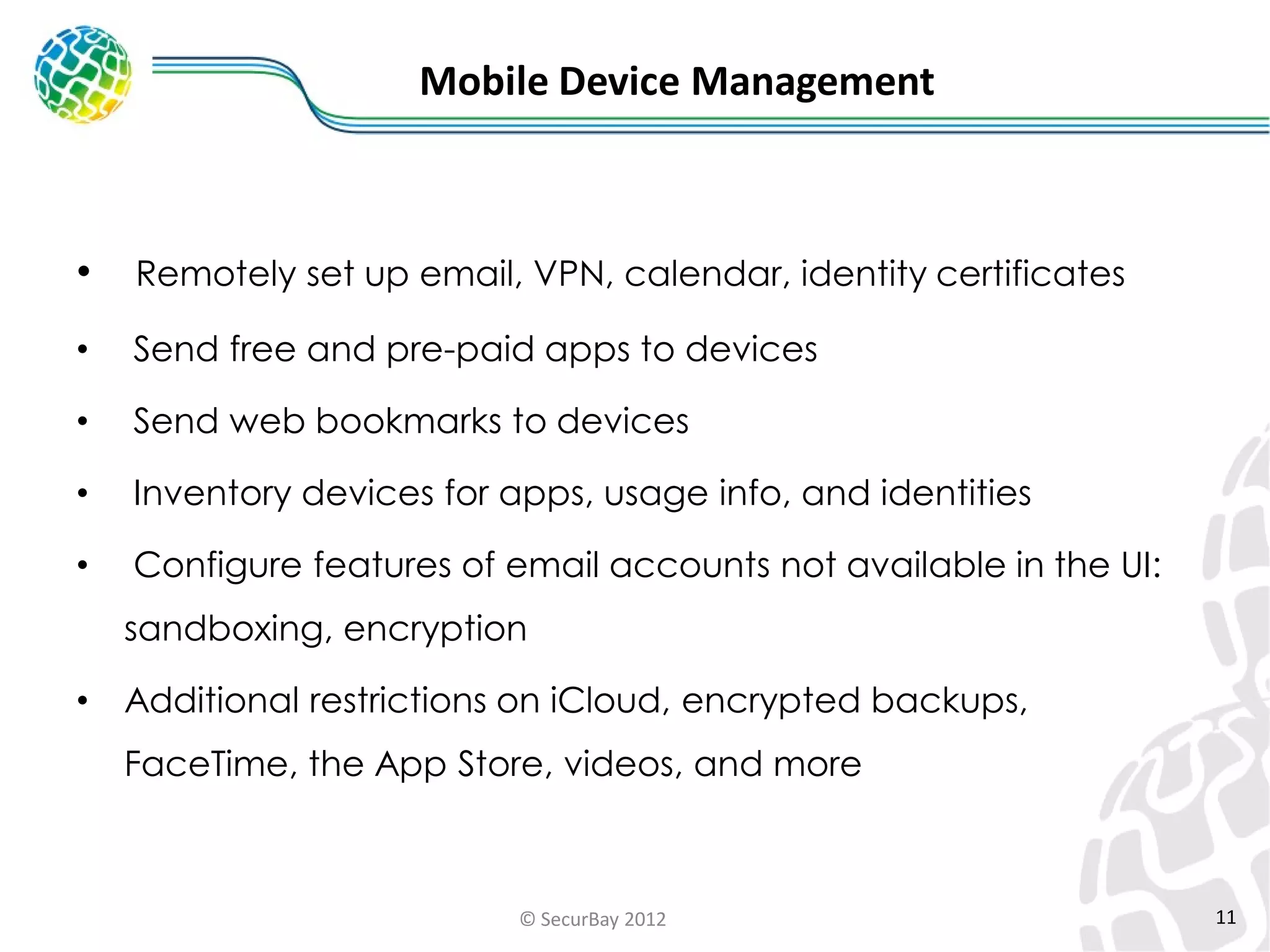
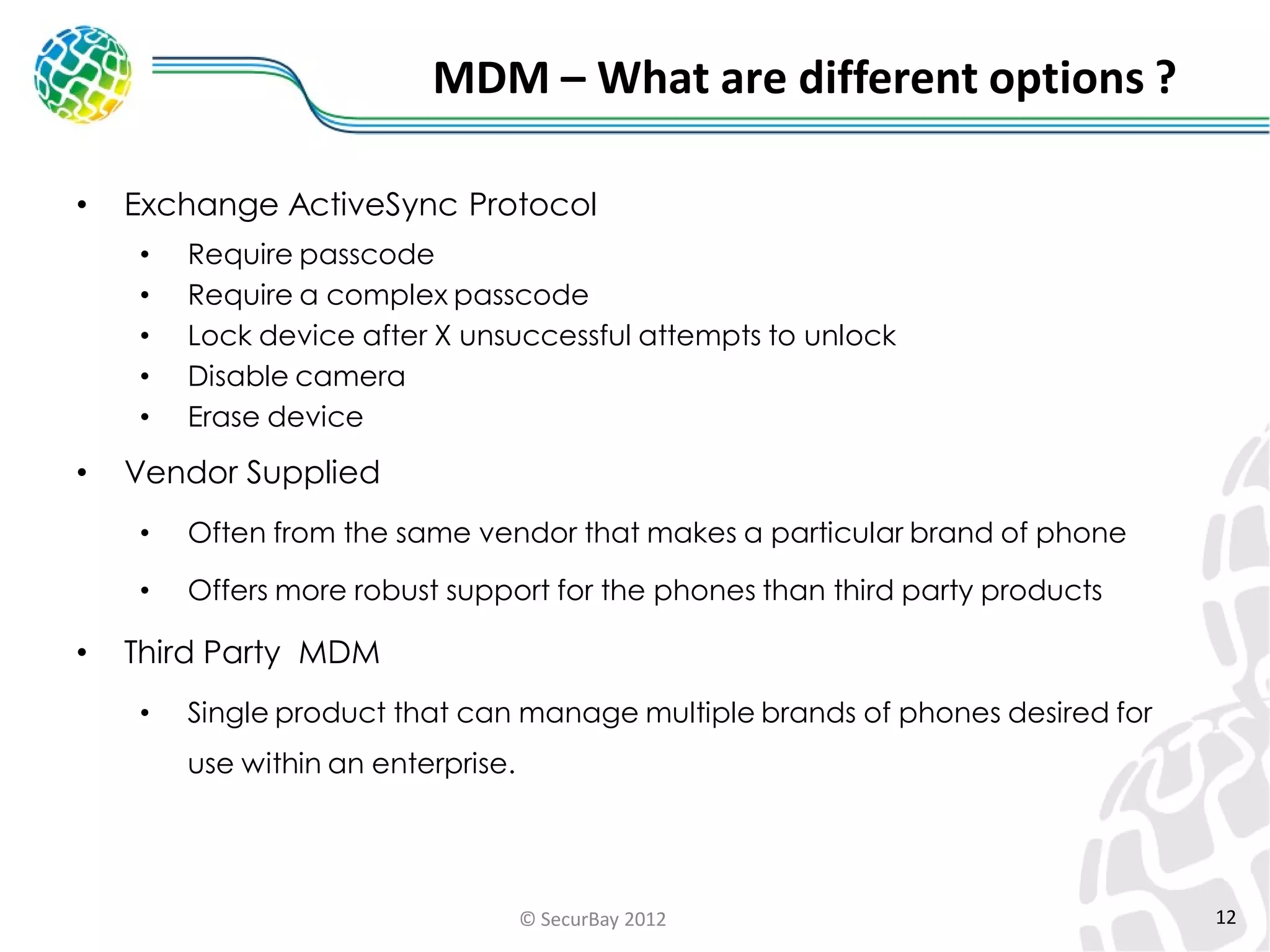
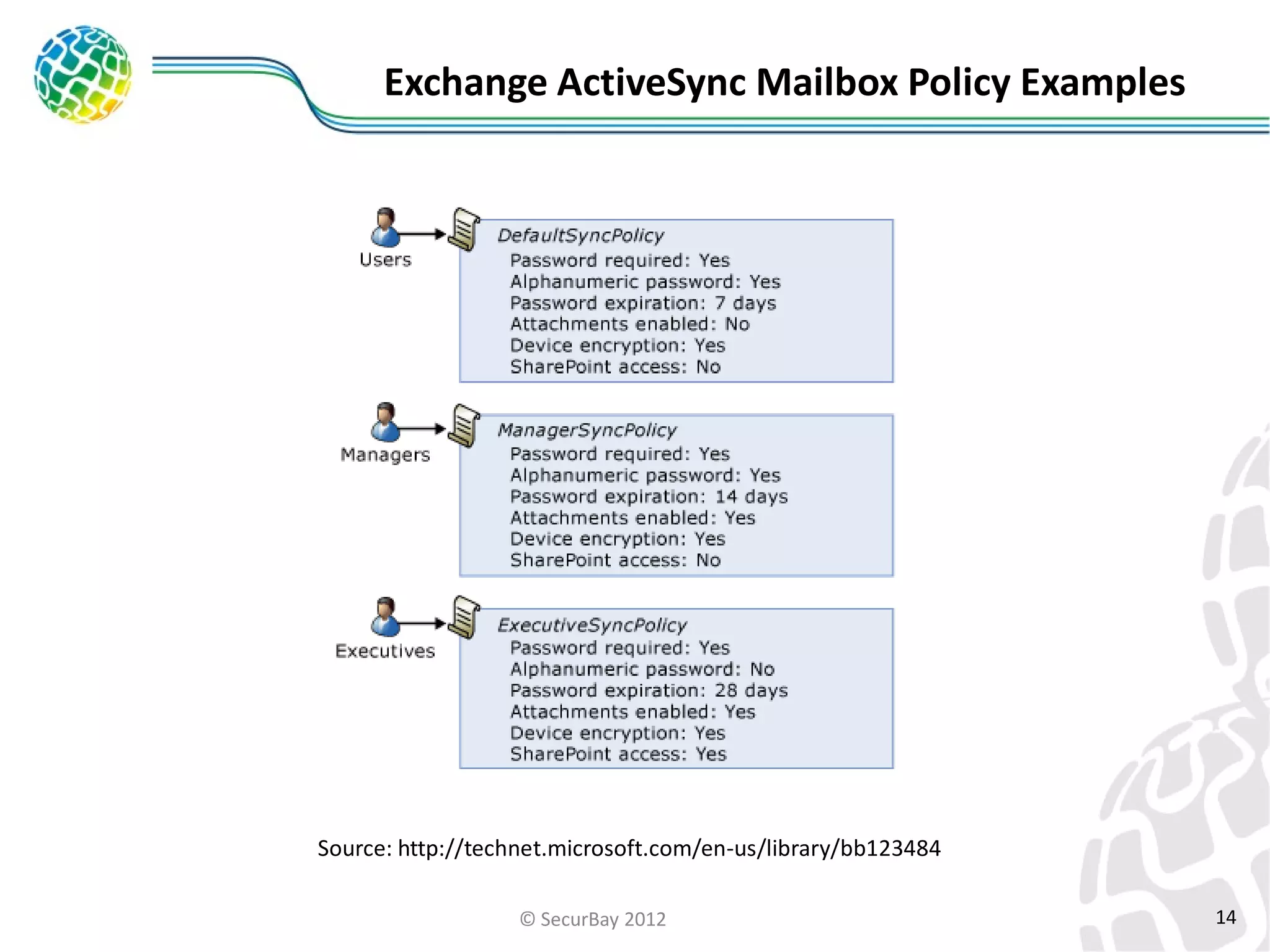
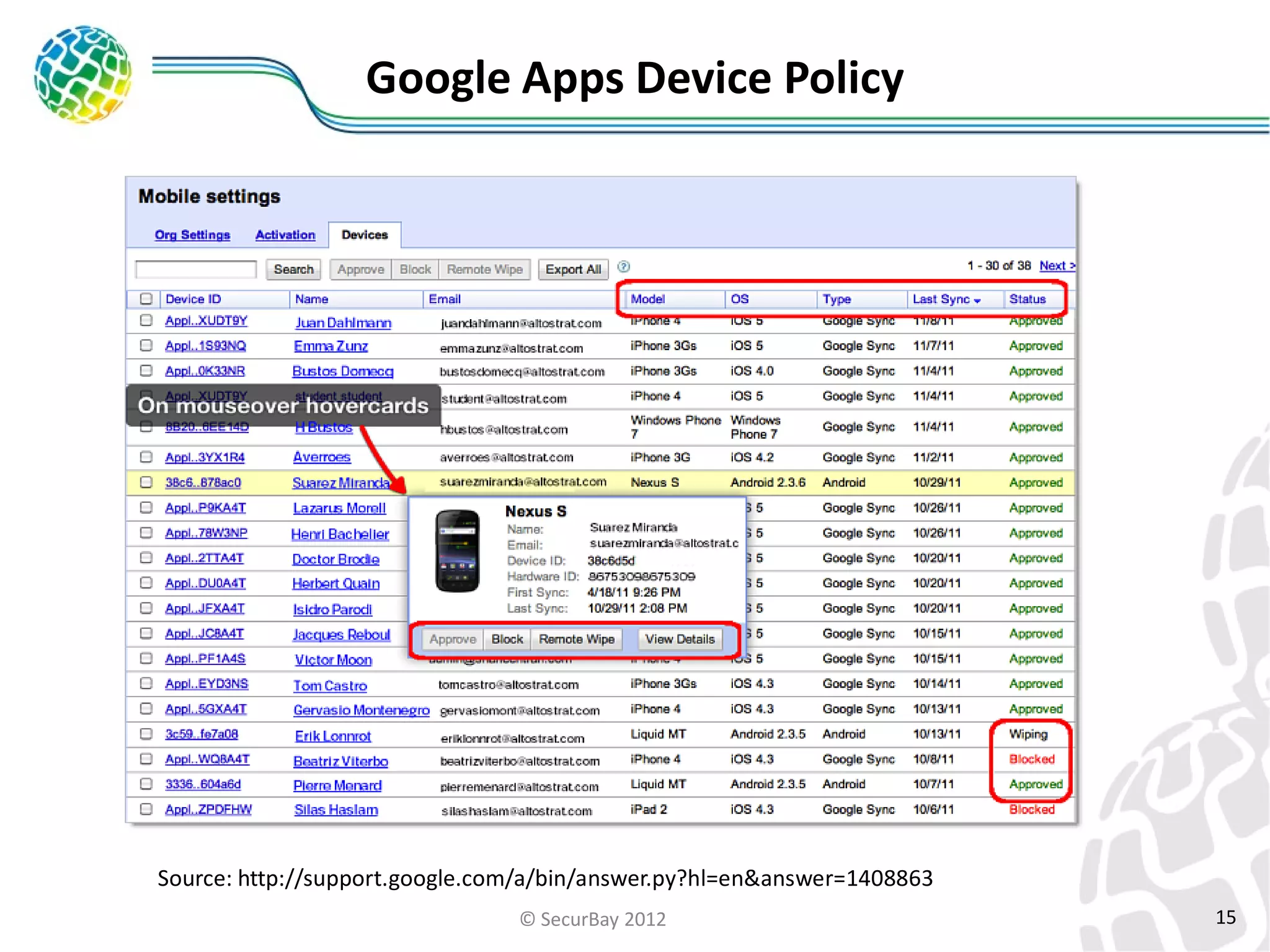
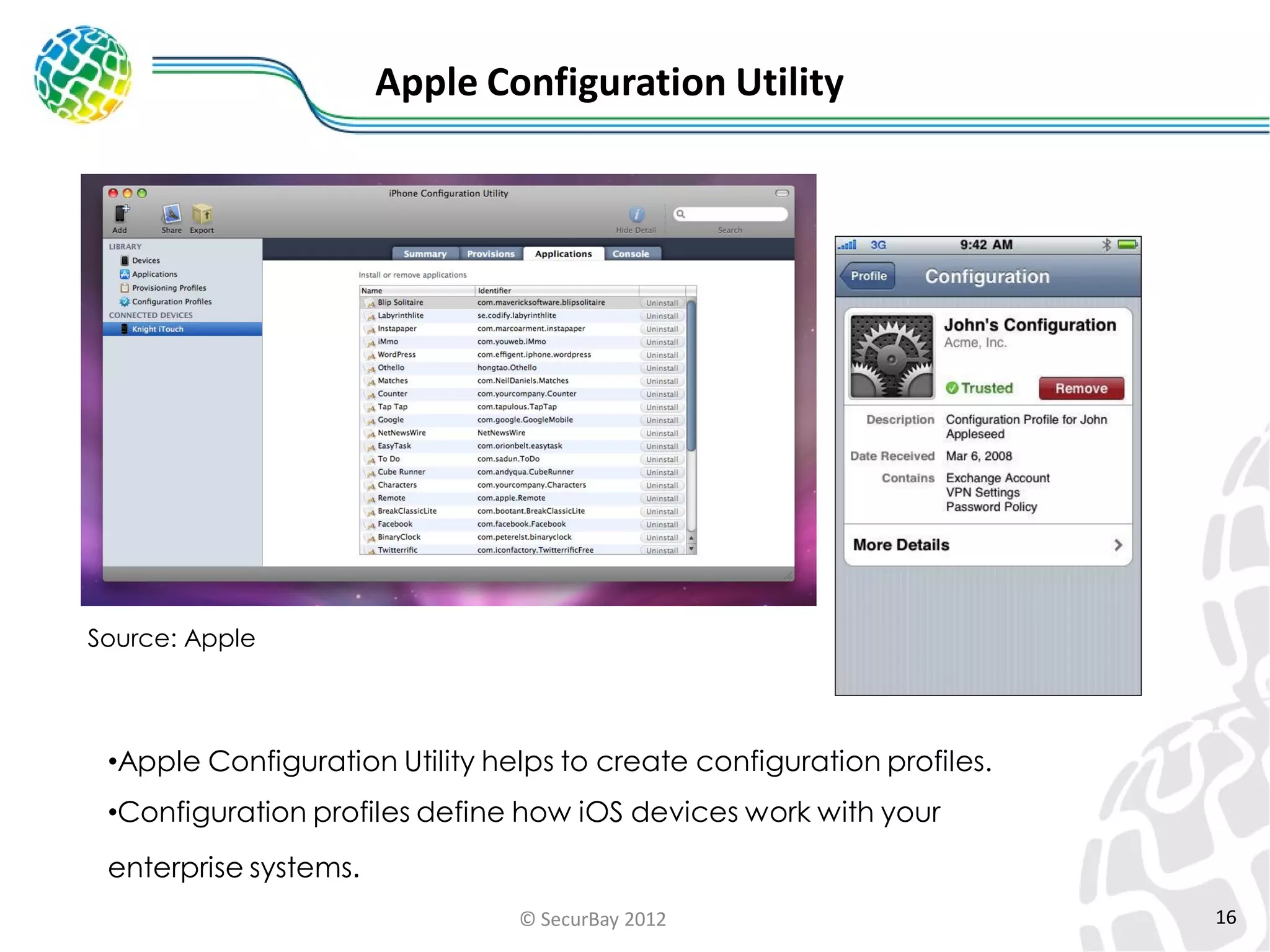
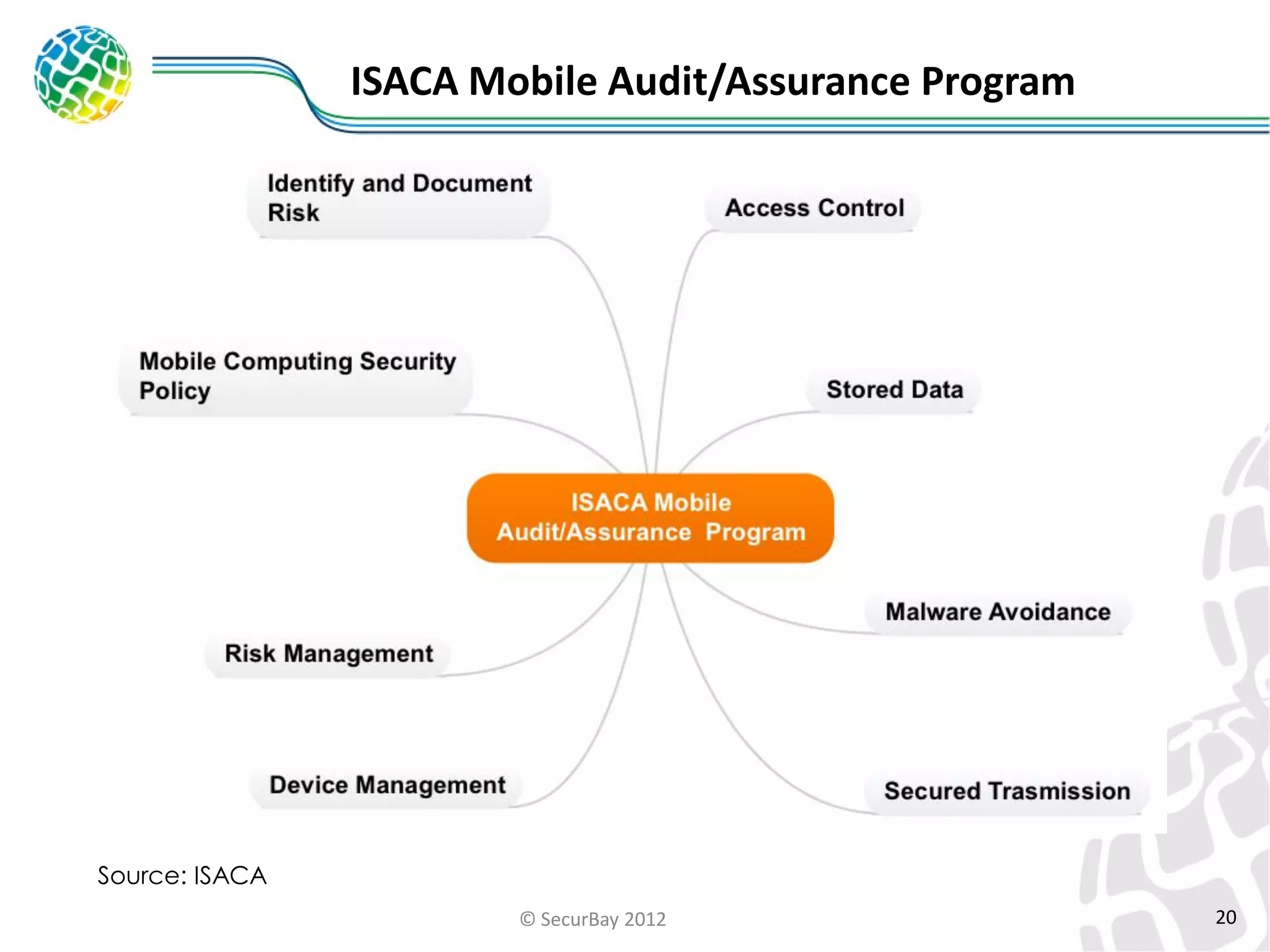
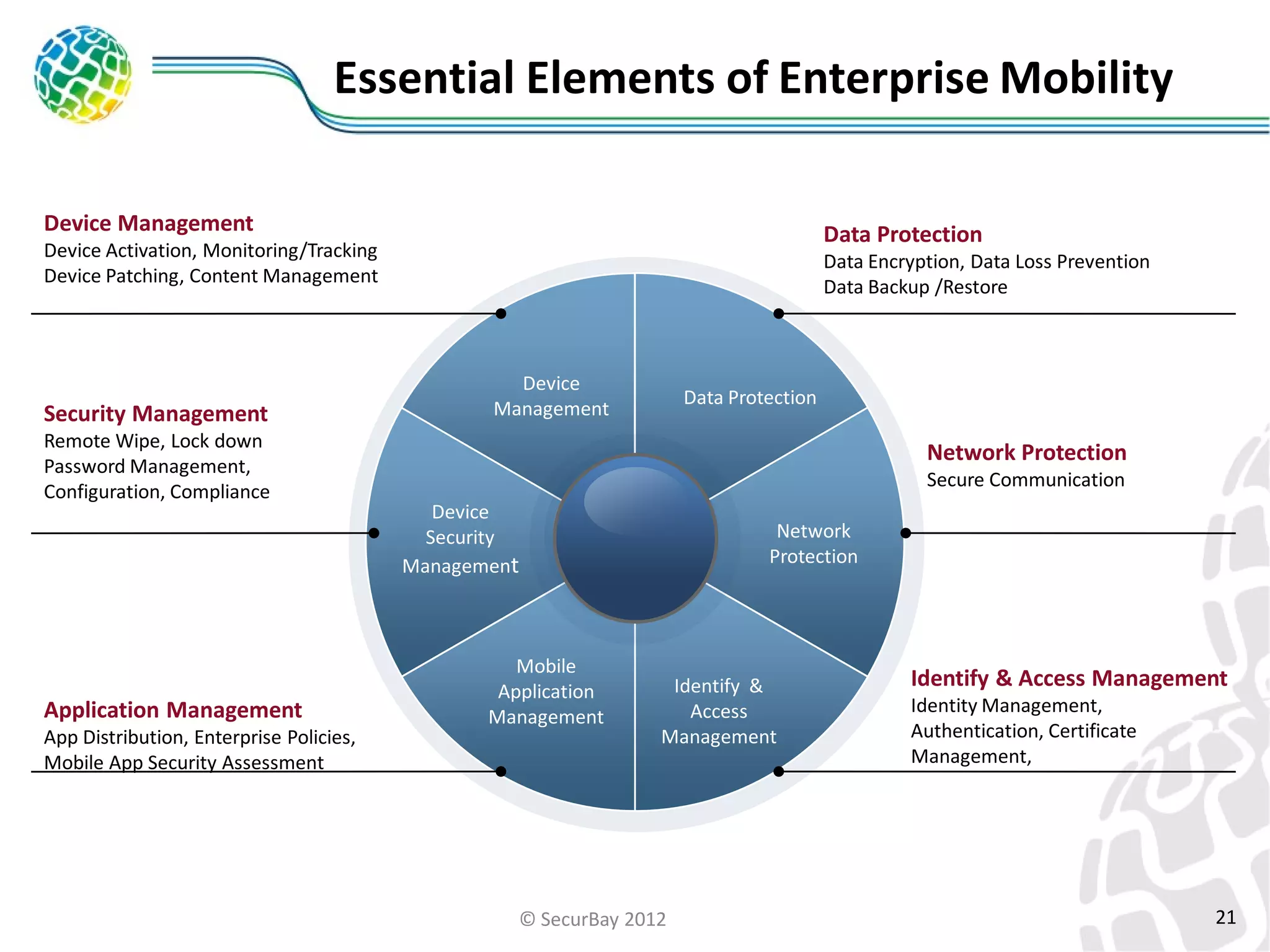
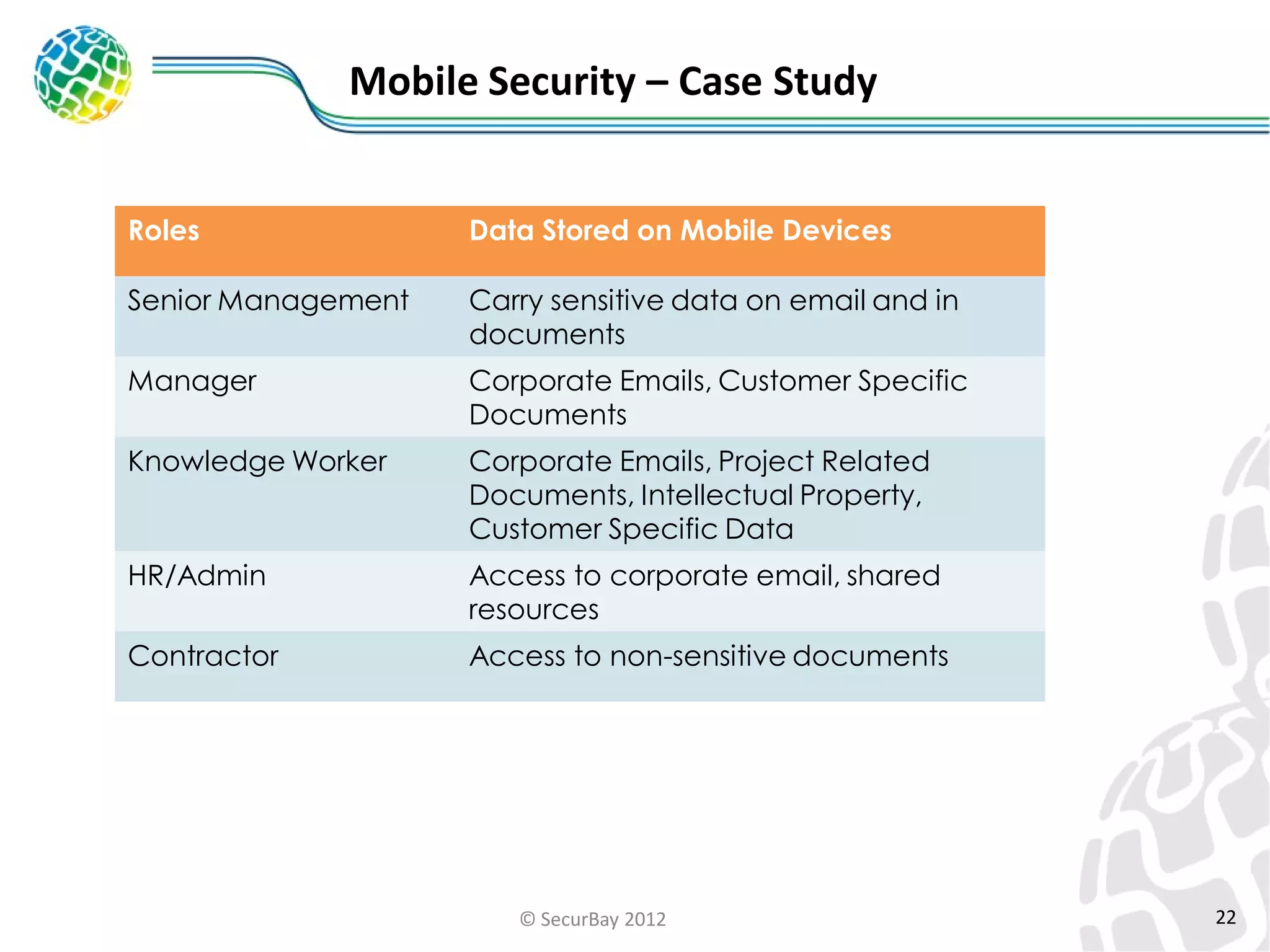
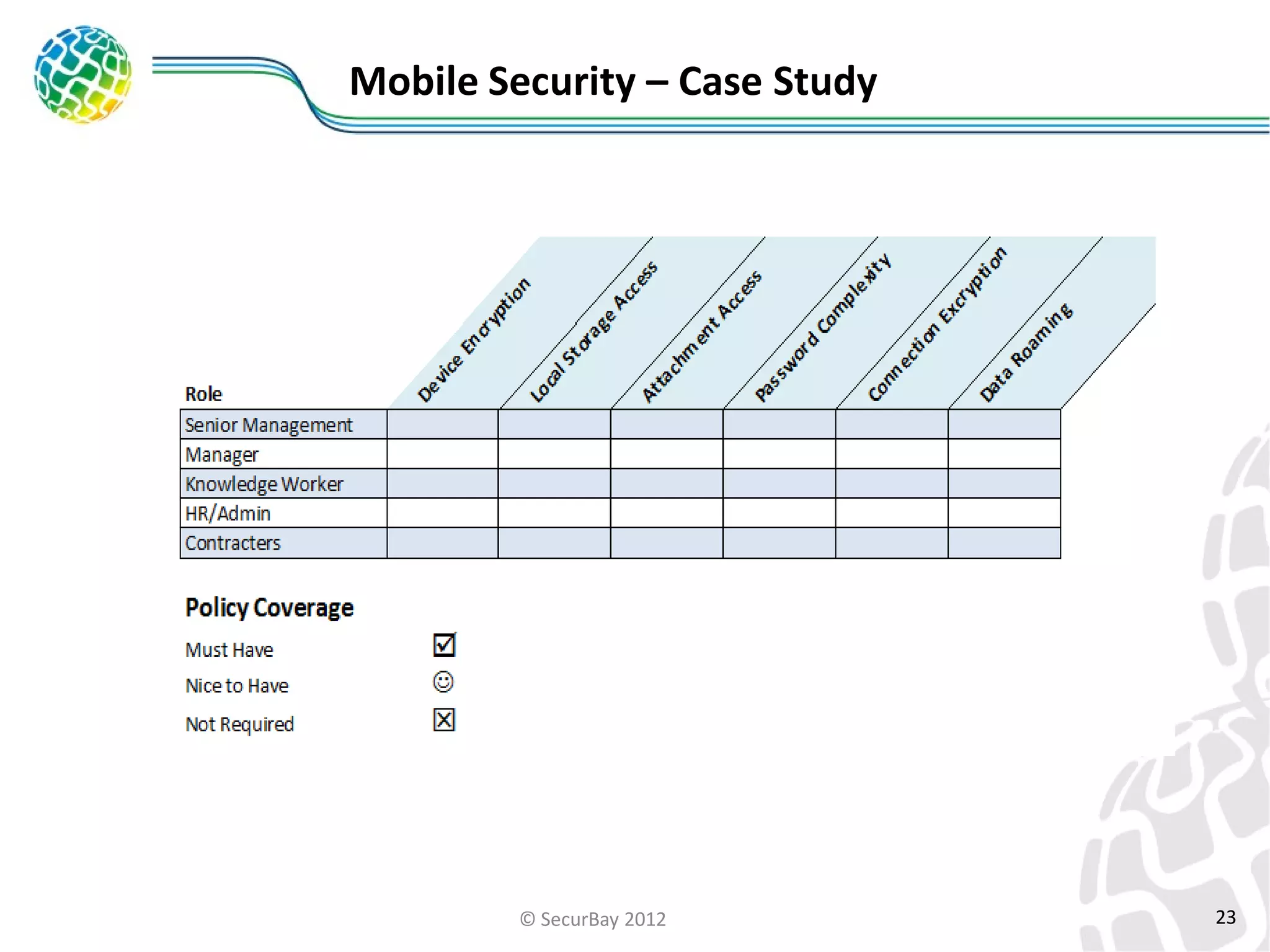
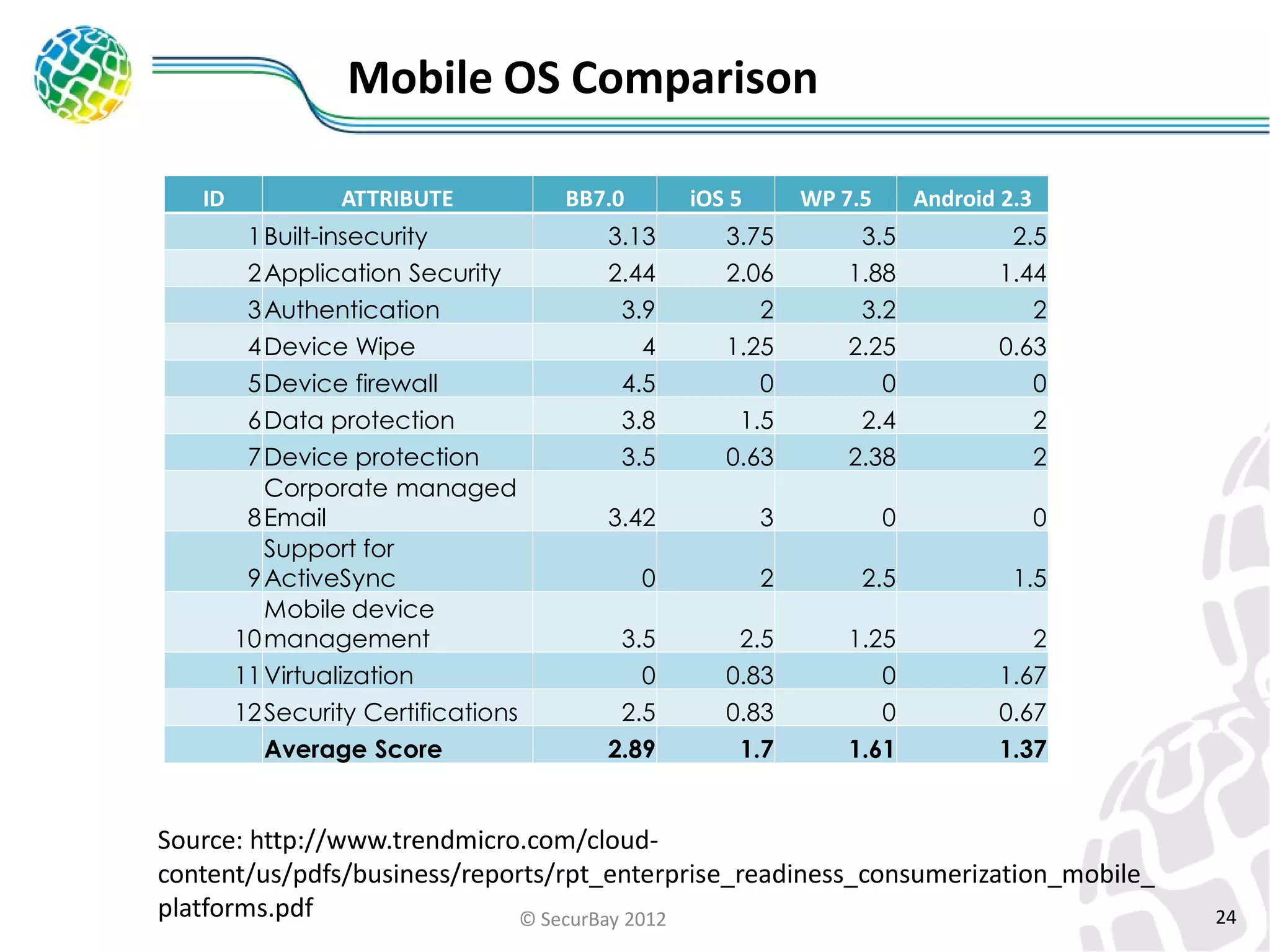
The document discusses enterprise mobile security. It covers the lifecycle of mobile device solutions within an enterprise, including initiation, development, implementation, operation and maintenance, and disposal. It also discusses developing a mobile policy using use cases, BYOD scenarios, and various MDM solutions. The key aspects of a mobile security program are identified as device management, data protection, network protection, identity and access management, and application management. A case study example is also provided.