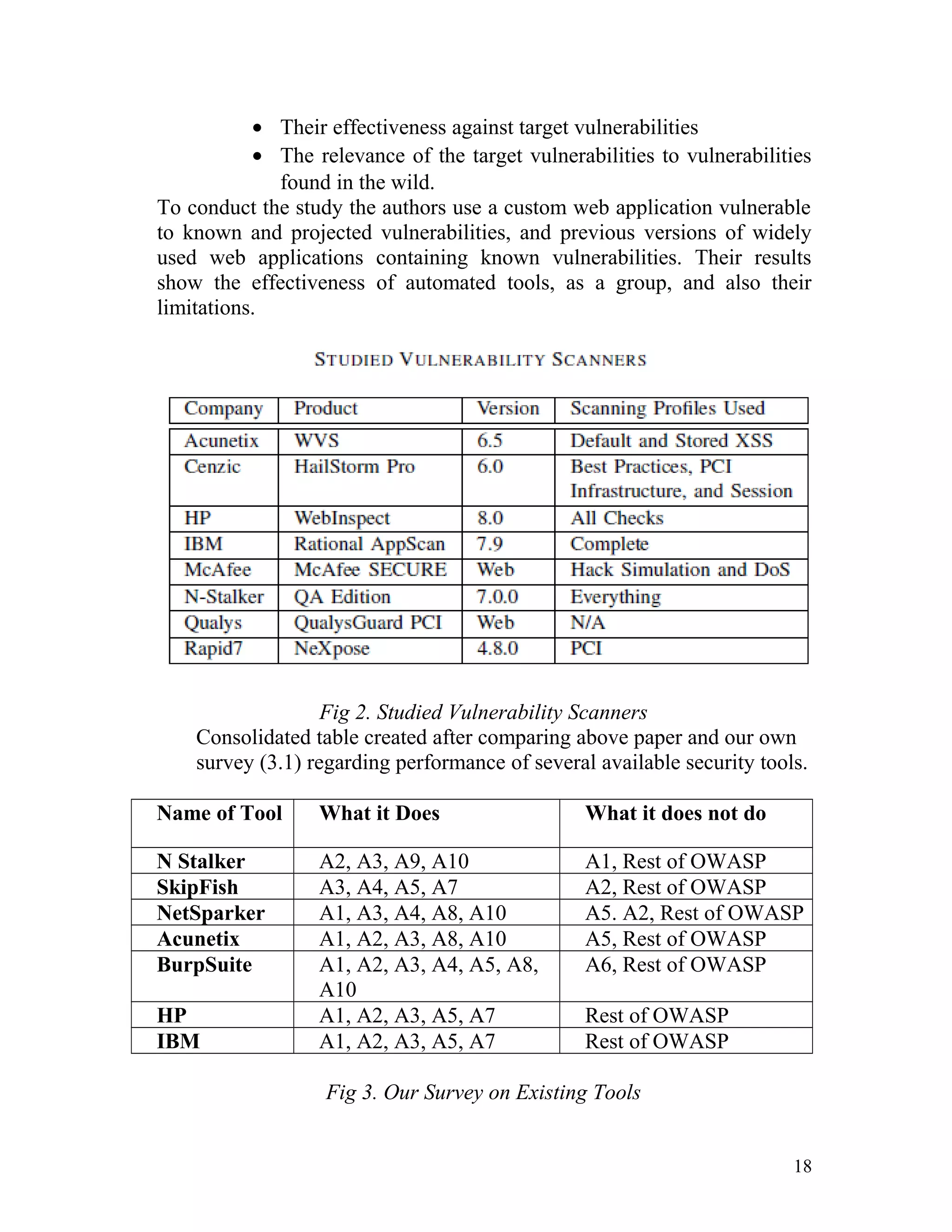
The document is a project report detailing the development of a semi-automated security testing tool for web applications, addressing critical vulnerabilities commonly found in web applications. It discusses application security, the need for automated testing tools, and outlines the objectives, methodology, and findings from testing the tool on a vulnerable web application and live sites. Additionally, the report provides recommendations for best practices and corrective actions based on identified vulnerabilities.









![1. INTRODUCTION
1.1 PROBLEM STATEMENT
To create a semi - automated testing tool for identifying vulnerabilities in
web applications.
1.1.1 Application security vulnerabilities
Application security encompasses measures taken throughout the
application's life-cycle to prevent exceptions in the security policy of
an application or the underlying system (vulnerabilities) through flaws in
the design, development, deployment, upgrade, or maintenance of the
application.
Security vulnerability is a security exposure that results from a product flaw,
and which the maker of the product should fix.
Web application security is a branch of Information Security that deals
specifically with security of websites, web applications and web services.
[Wikipedia, 2012]
1.1.2 Need for semi/automated Testing Tools
Automated tools save valuable time and money by automating tiresome and
very technical processes to find security vulnerabilities.
Such tools serve as aides for human testers, automating many tasks that are
time consuming or repetitive.
1.2 PROBLEM DESCRIPTION
The problem description clearly gives an idea of what we are trying to
achieve through our project and what our central objective/goals are.
Vulnerability scanners and more specifically web application scanners,
otherwise known as penetration testing tools have been historically used by
security organizations within corporations and security consultants to semi-
automate the security testing of http request/responses. Given the common
size of individual programs (often 500,000 lines of code or more), the
human brain cannot execute a comprehensive data flow analysis needed in
order to completely check all circuitous paths of an application program to
find vulnerability points.
12](https://image.slidesharecdn.com/semi-automatedsecuritytestingofwebapplications-140730122043-phpapp01/75/Semi-Automated-Security-Testing-of-Web-applications-11-2048.jpg)




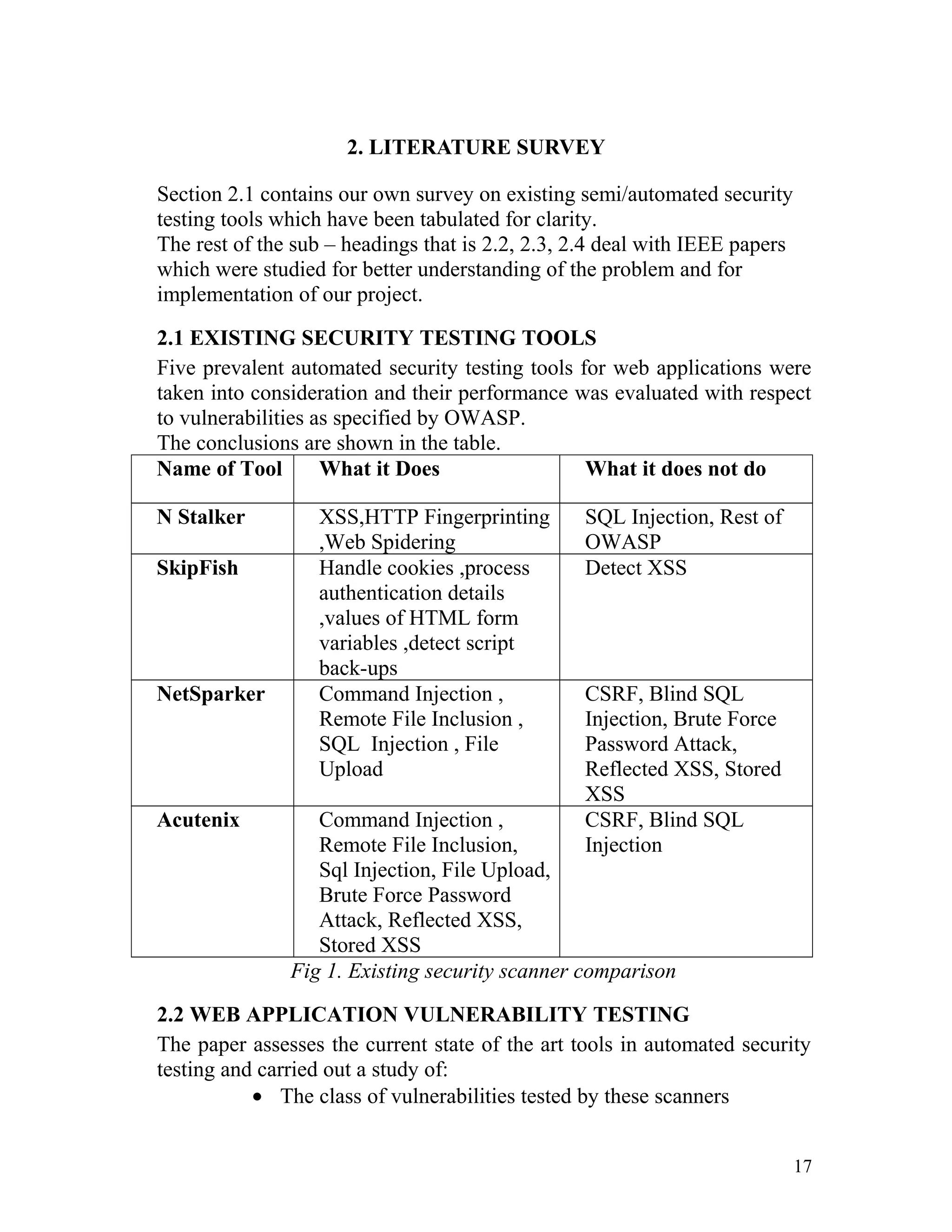
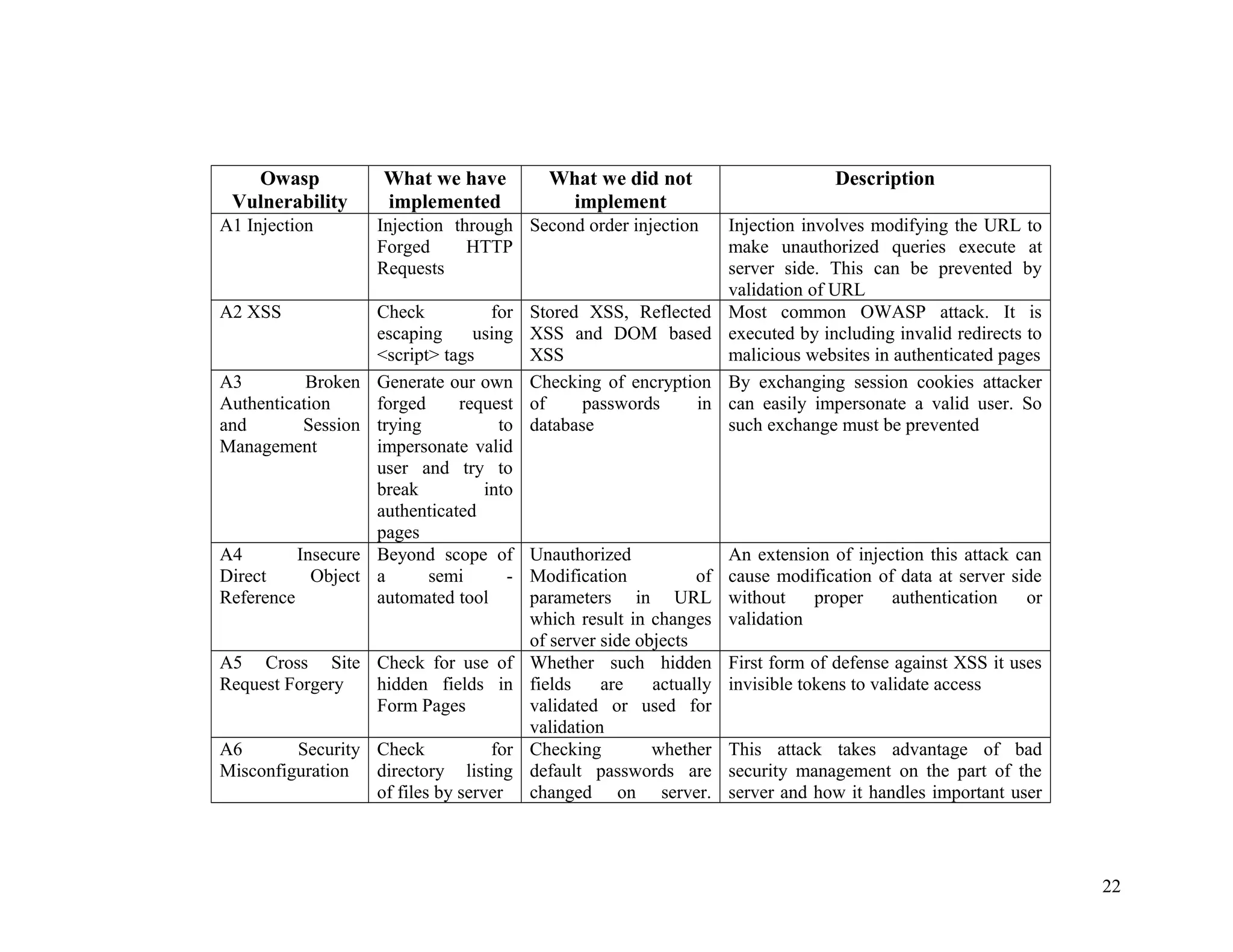
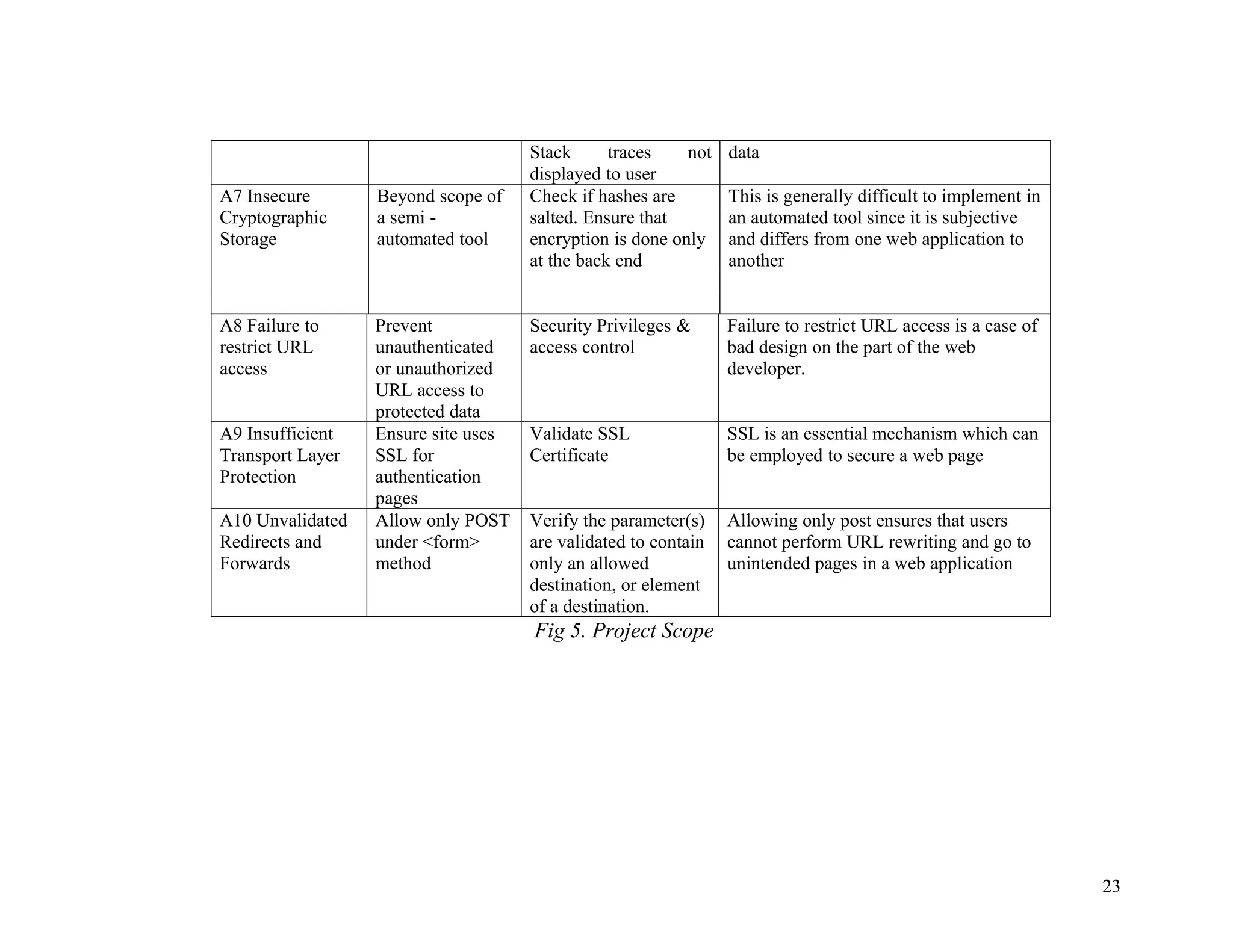
![A1 to A10 as per OWASP Top 10
2.3IMPLEMENTATION OF WEB CRAWLER
The World Wide Web is an interlinked collection of billions of documents
formatted using HTML. Due to growing and dynamic nature of the web; it
has become a challenge to traverse all URLs in the web documents and to
handle these URLs. A focused crawler is an agent that targets a particular
topic and visits and gathers only relevant web pages.The authors [Gupta
P, Johari K, Linagay's Univ, Dec. 2009] take one seed URL as input and
searches with a keyword, the search results are based on the keyword and
it will fetch the web pages where it finds that keyword.
This focused based crawler approach retrieves documents that contain
particular keywords from the user’s query. The authors implemented the
crawler using breadth-first search.
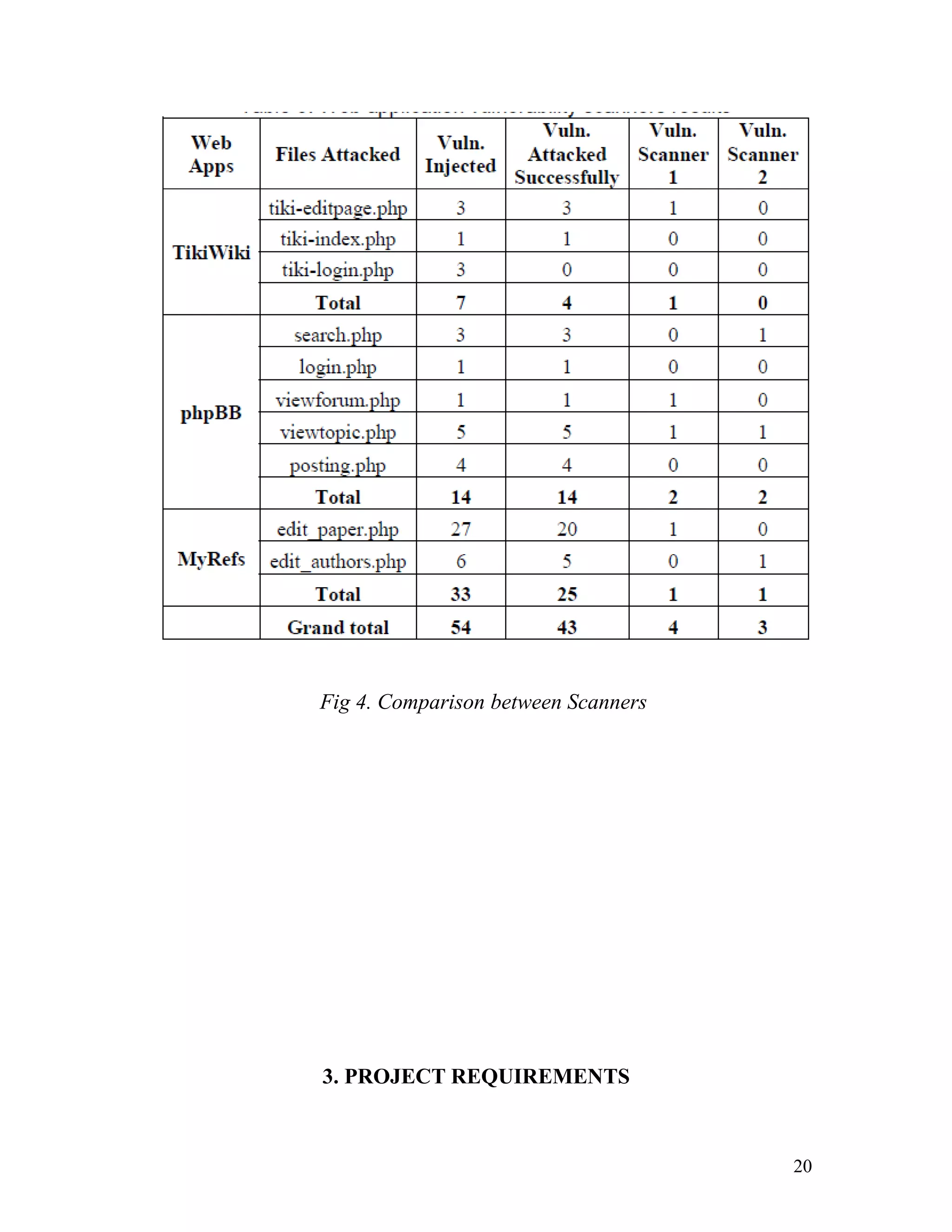
2.4 VULNERABILITY AND ATTACK INJECTION FOR WEB
APPLICATIONS
In this paper the authors [Fonseca J, Vieira M., Madeira H., CISUC, Univ.
of Coimbra, Coimbra, Portugal (2009)] proposed a methodology to inject
realistic attacks in web applications. The methodology is based on the idea
that by injecting realistic vulnerabilities in a web application and attacking
them automatically we can assess existing security mechanisms. To
provide true to life results, this methodology relies on field studies of a
large number of vulnerabilities in web applications. The paper also
describes a set of tools implementing the proposed methodology.
19](https://image.slidesharecdn.com/semi-automatedsecuritytestingofwebapplications-140730122043-phpapp01/75/Semi-Automated-Security-Testing-of-Web-applications-18-2048.jpg)


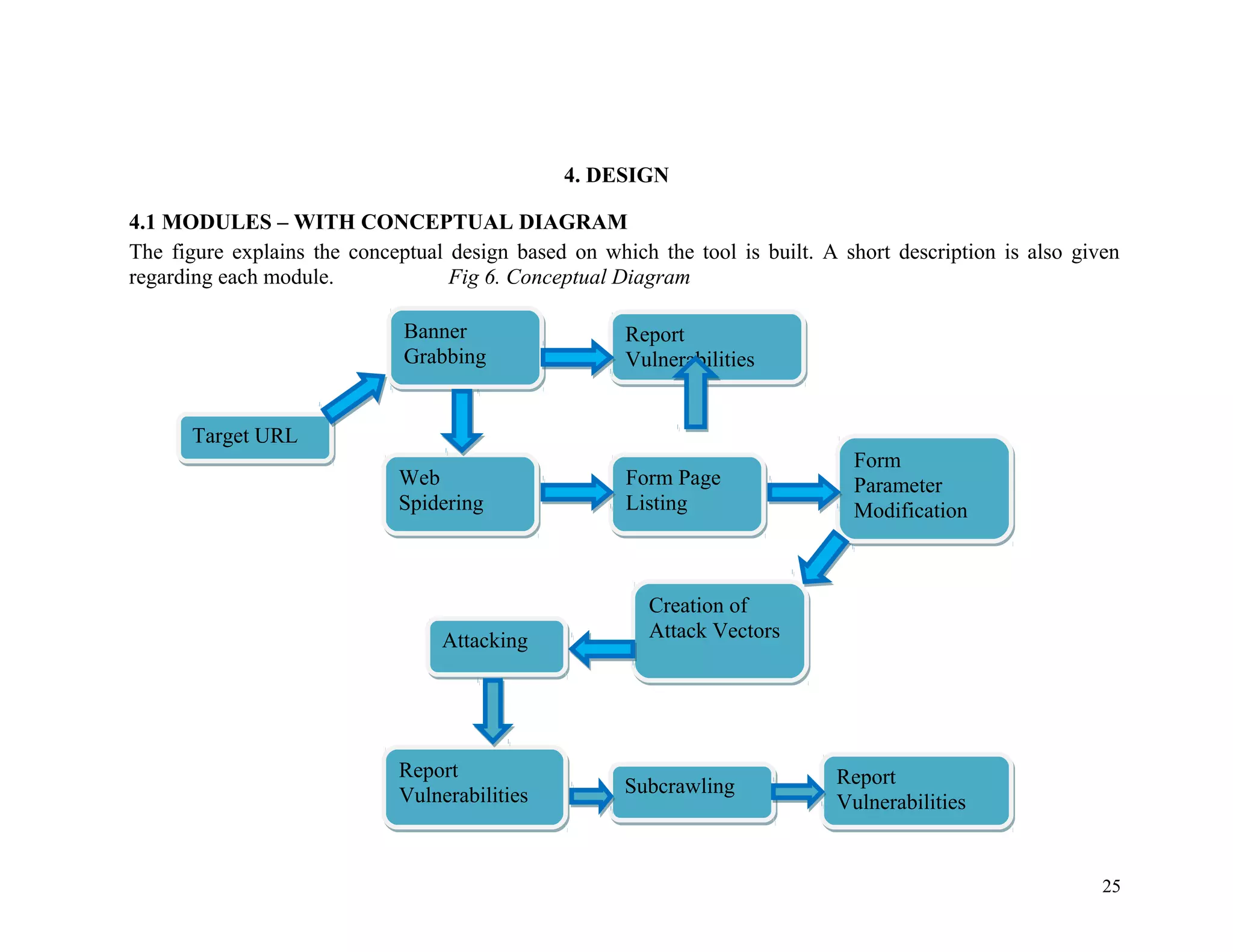
![4.1.1 Target URL
Here the target URL is supplied for testing. The target URL is usually
a domain name for example like http://www.example.com.
4.1.2 Banner Grabbing
Banner Grabbing is an enumeration technique used to glean
information about computer systems on a network and the services
running its open ports.
An intruder can use banner grabbing in order to find
network hosts that are running versions of applications and operating
systems with known exploits. This is the reason why we include
banner grabbing in our tool and we report the results that get returned
from this method.
For example one could establish a connection to a target host running
a web service with netcat, then send a bad html request in order to get
information about the service on the host:
[root@prober]ncwww.targethost.com80
HEAD/HTTP/1.1
HTTP/1.1200OK
Date:Mon,11May200922:10:40EST
Server:Apache/2.0.46(Unix)(RedHat/Linux)
Last-Modified: Thu, 16 Apr 2009 11:20:14 PST
ETag:"1986-69b-123a4bc6"
Accept-Ranges:bytes
Content-Length:1110
Connection:close
Content-Type: text/html
The administrator can now catalog this system or an intruder now
knows what version of Apache to look for exploits.
To prevent this Network Administrators should be sure to restrict
access to services on their networks to appropriate networks and be
sure to shut down unused or unnecessary services running on network
hosts. Hiding of such network information is provided by our tool as a
recommendation.
26](https://image.slidesharecdn.com/semi-automatedsecuritytestingofwebapplications-140730122043-phpapp01/75/Semi-Automated-Security-Testing-of-Web-applications-25-2048.jpg)




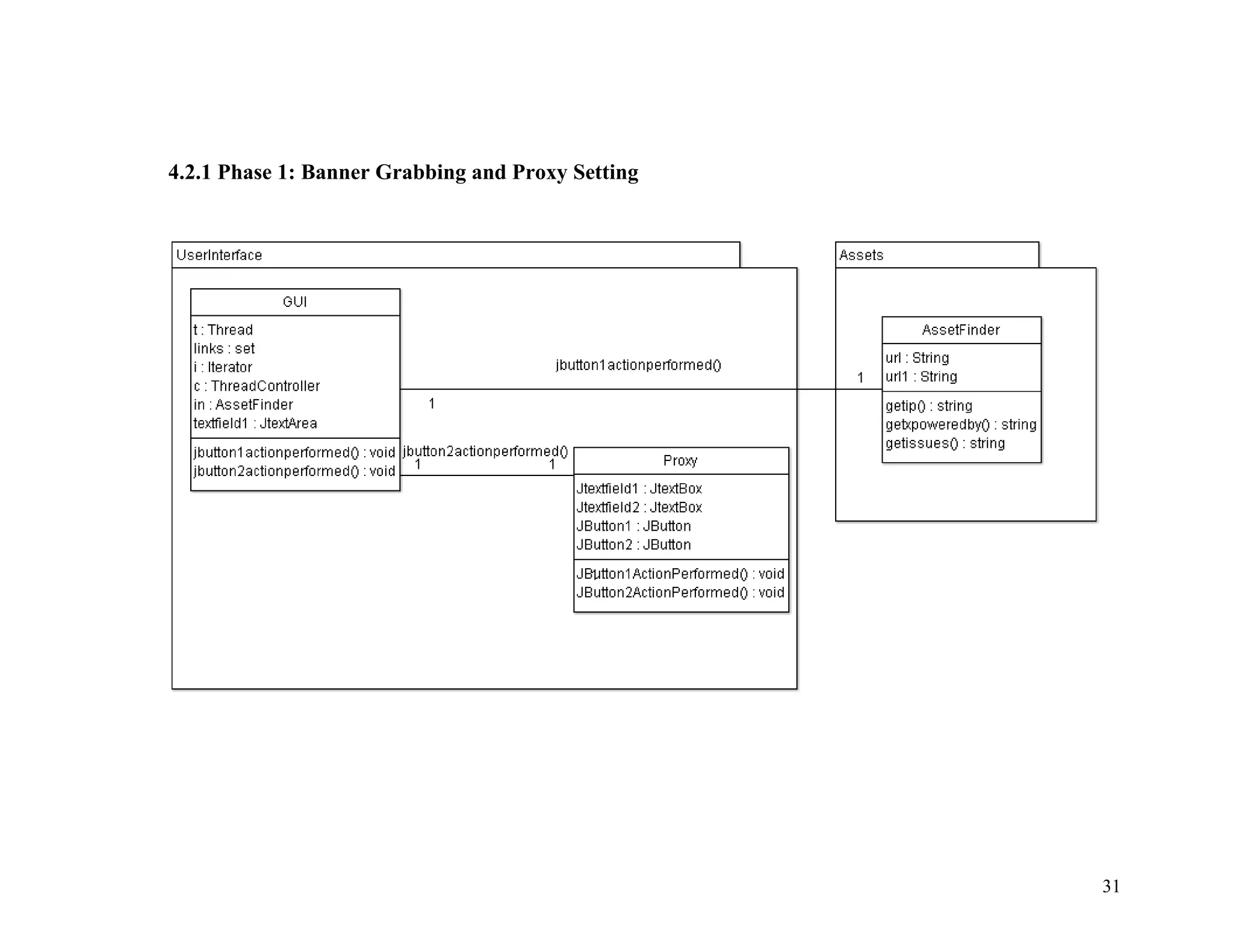
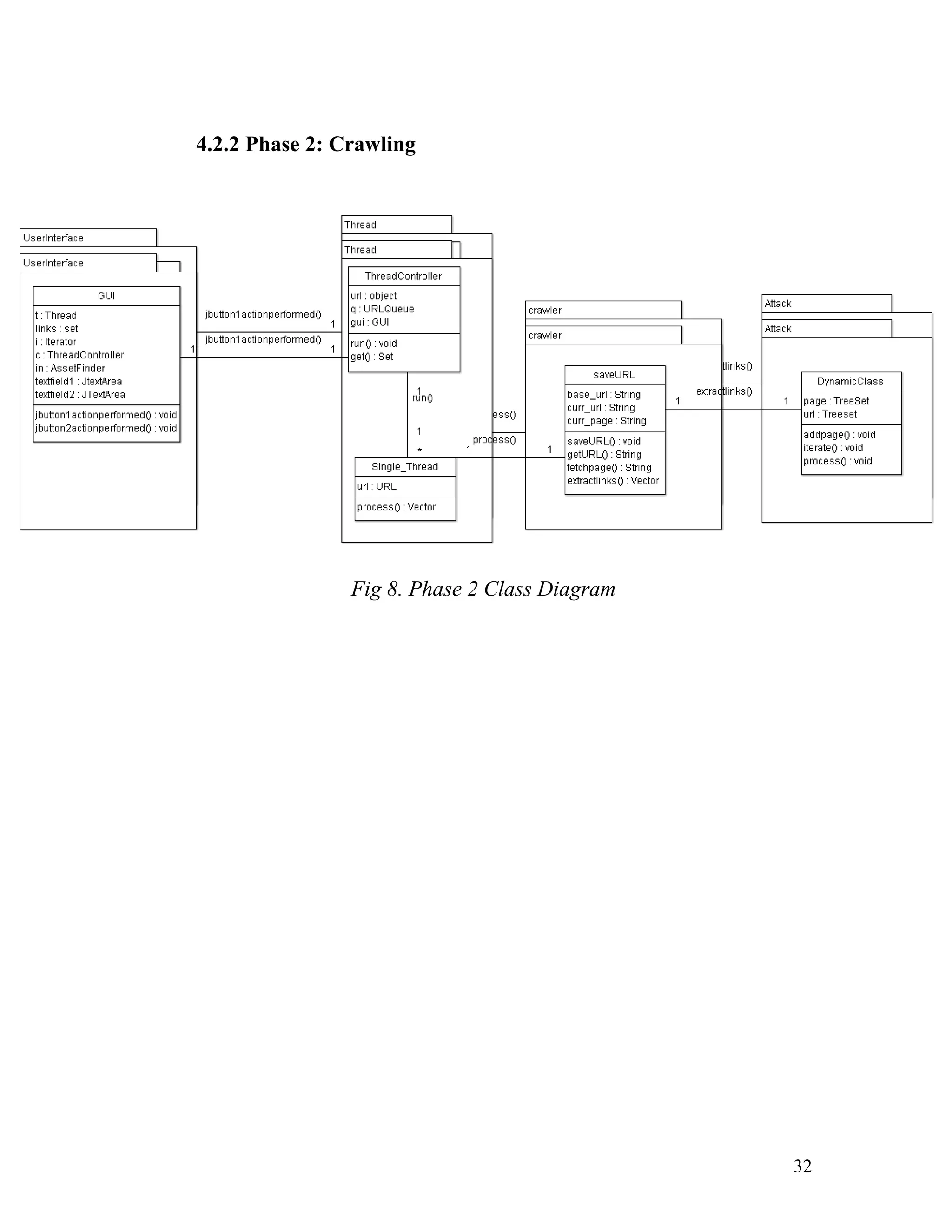





![int <index> = <page>.indexOf("<form");
<index> = <page>.indexOf("action="", <index>);
<index>+=6;
String <FormAction>=<page>.substring(<index>,
<page>.indexOf(""", <index>));
Source Code for retrieving individual parameters
public String []<params_name>=new String[100];
public String []<params_type>=new String[100];
public int <params_count>=0;
int <index>=page.indexOf("<input"), <index2>;
while(<index>!=-1)
{
<index2> = <page>.indexOf("type=", <index>);
<index2>+ = 6;
<params_type>[<params_count>] =
<page>.substring(<index2>,
<page>.indexOf(""", <index2>));
<index2> = <page>.indexOf("name=", <index>);
<index2>+ = 6;
<params_name>[<params_count>] =
<page>.substring(<index2>,
<page>.indexOf(""", <index2>));
<index> = <page>.indexOf("<input", <index>+1);
41](https://image.slidesharecdn.com/semi-automatedsecuritytestingofwebapplications-140730122043-phpapp01/75/Semi-Automated-Security-Testing-of-Web-applications-40-2048.jpg)

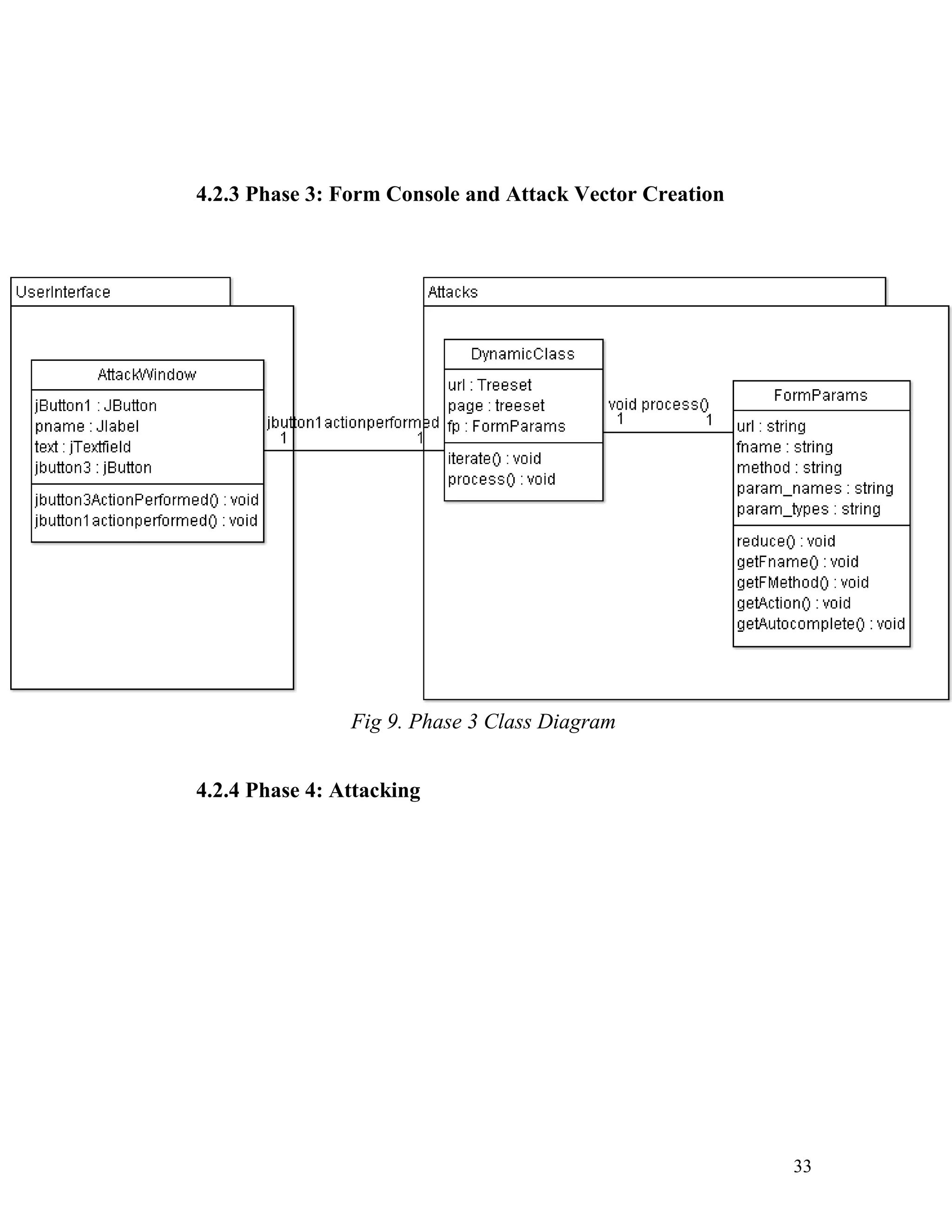
![It is also the class in which all attack vector’s query strings are
formulated.
Source Code for formulation of query strings
String <query>="?", <inject_query>="?", <xss_query>="?";
String <XSS_Injector_String> =
"%27%22%28%29%26%251%3cScRiPt%20%3eprompt
%28995001%29%3c%2fScRiPt%3e";
for(<count>=0;<count><DynamicClass.<formparams>.params_c
ount;
<count>++)
if(DynamicClass.<formparams>.params_type[<count>].equals("t
ext") ||
DynamicClass.<formparams>.params_type[<count>].equals("pas
sword"))
break;
<query>=<query>+DynamicClass.<formparams>.params_name[
<count>]+"="+Text.getText()+"&";
if(!
DynamicClass.<formparams>.params_type[<count>].equals("pas
sword"))
{<inject_query>=<inject_query>+DynamicClass.<formparams>.p
arams_name[<count>]+"="+Text.getText()+"&";
<xss_query>=<xss_query>+DynamicClass.<formparams>.params
_name[<count>]+"="+
<XSS_Injector_String>+"&";}
else
{<inject_query>=<inject_query>+DynamicClass.<formparams>.p
arams_name[<count>]+"=hi'+or+'1=1";
<xss_query>=<xss_query>+DynamicClass.<formparams>.params
_name[<count>]+"="+
43](https://image.slidesharecdn.com/semi-automatedsecuritytestingofwebapplications-140730122043-phpapp01/75/Semi-Automated-Security-Testing-of-Web-applications-42-2048.jpg)























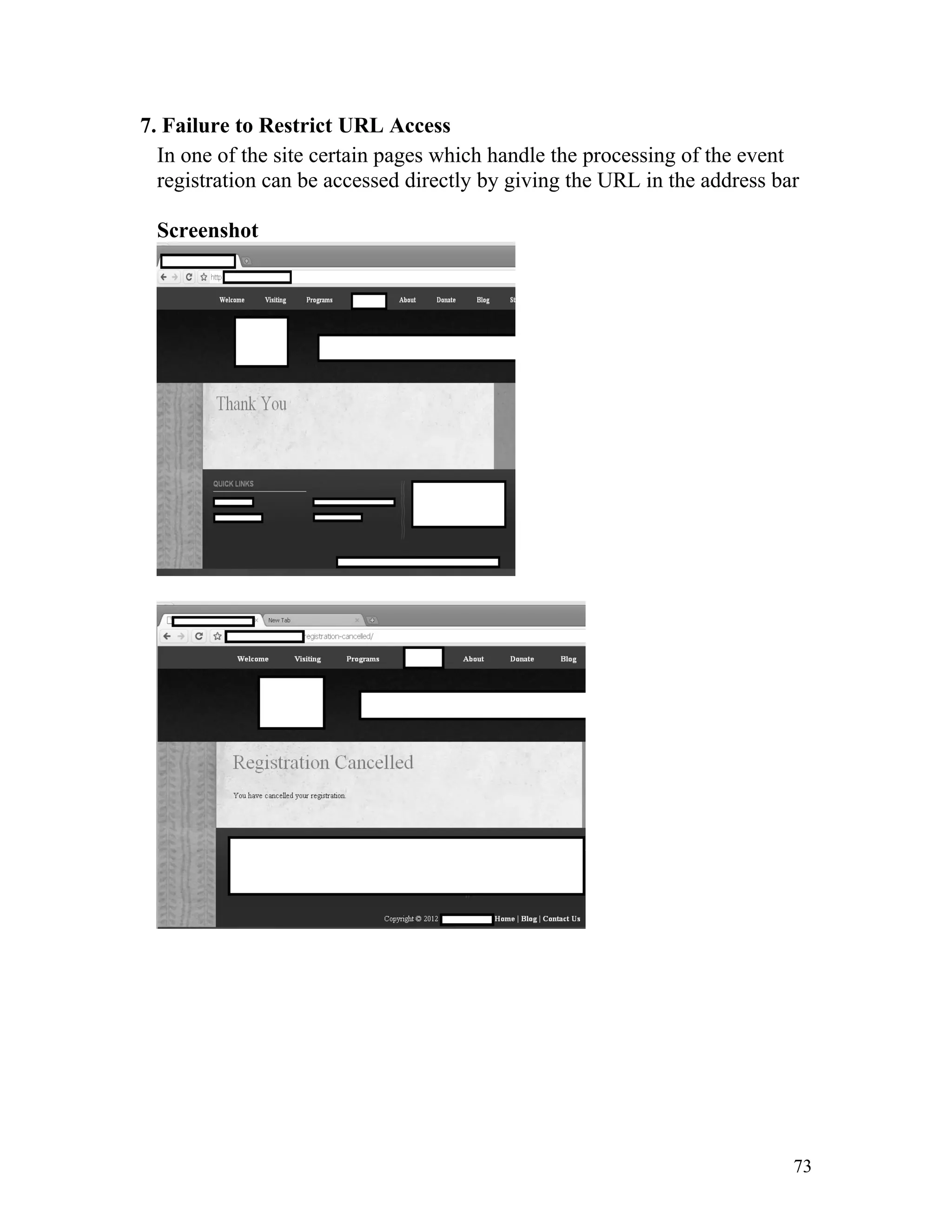
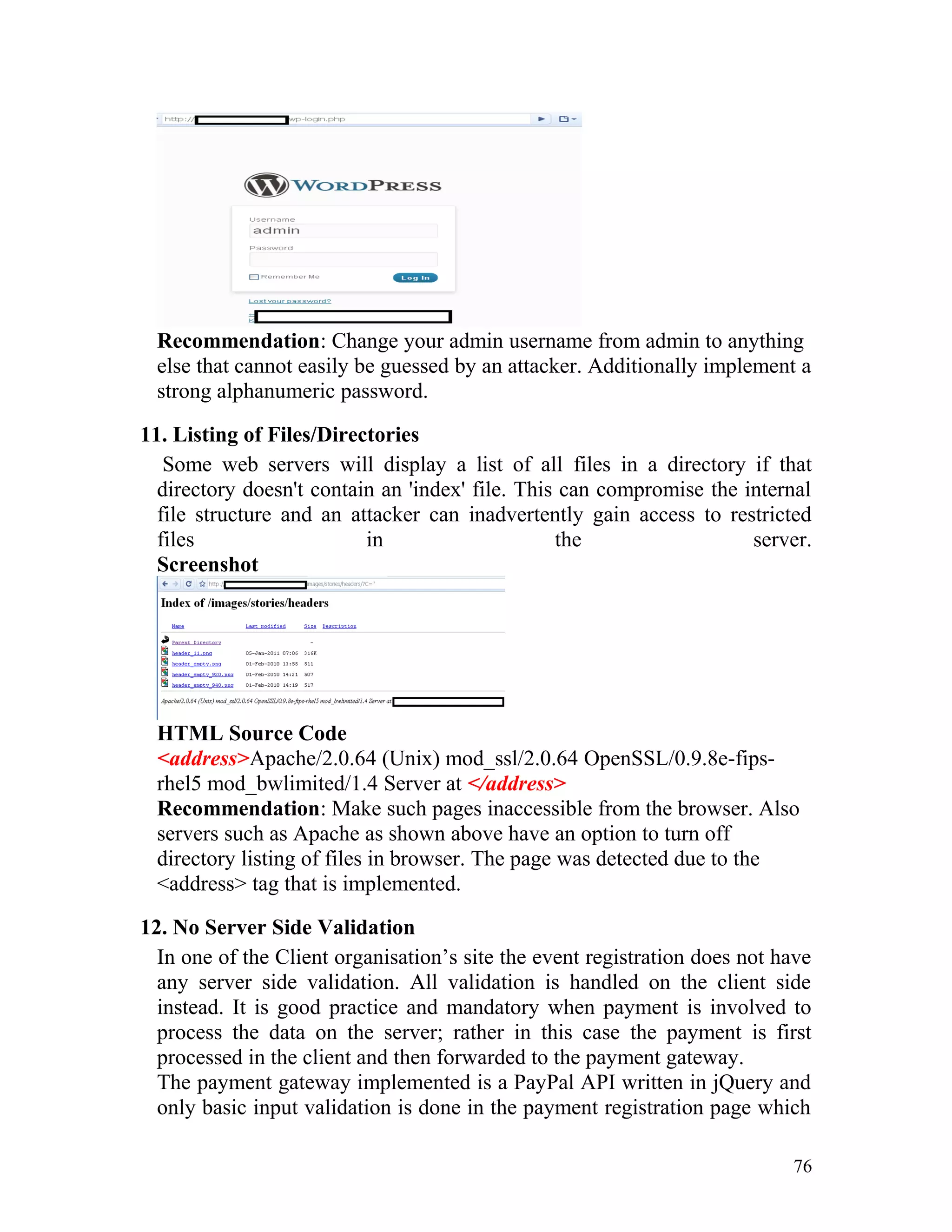
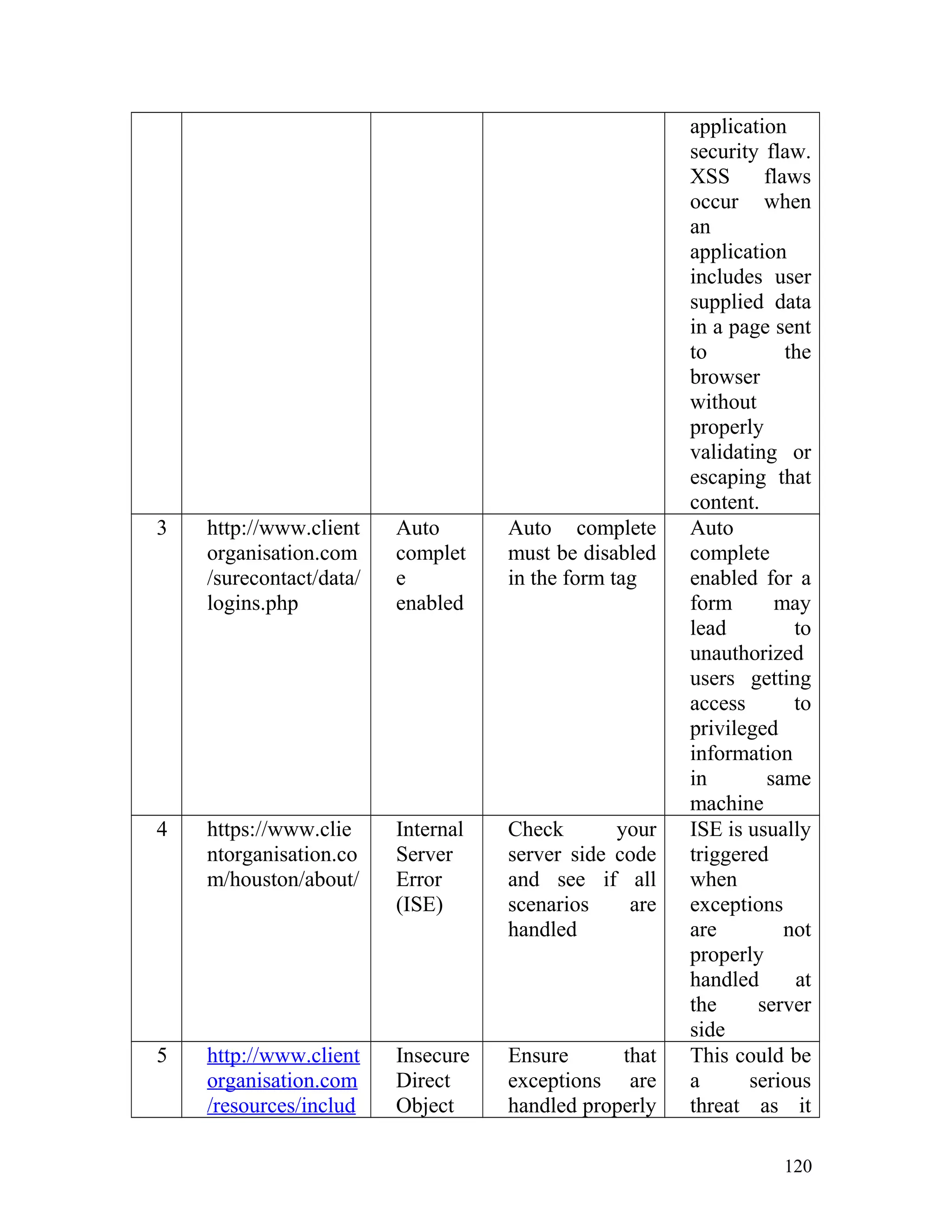
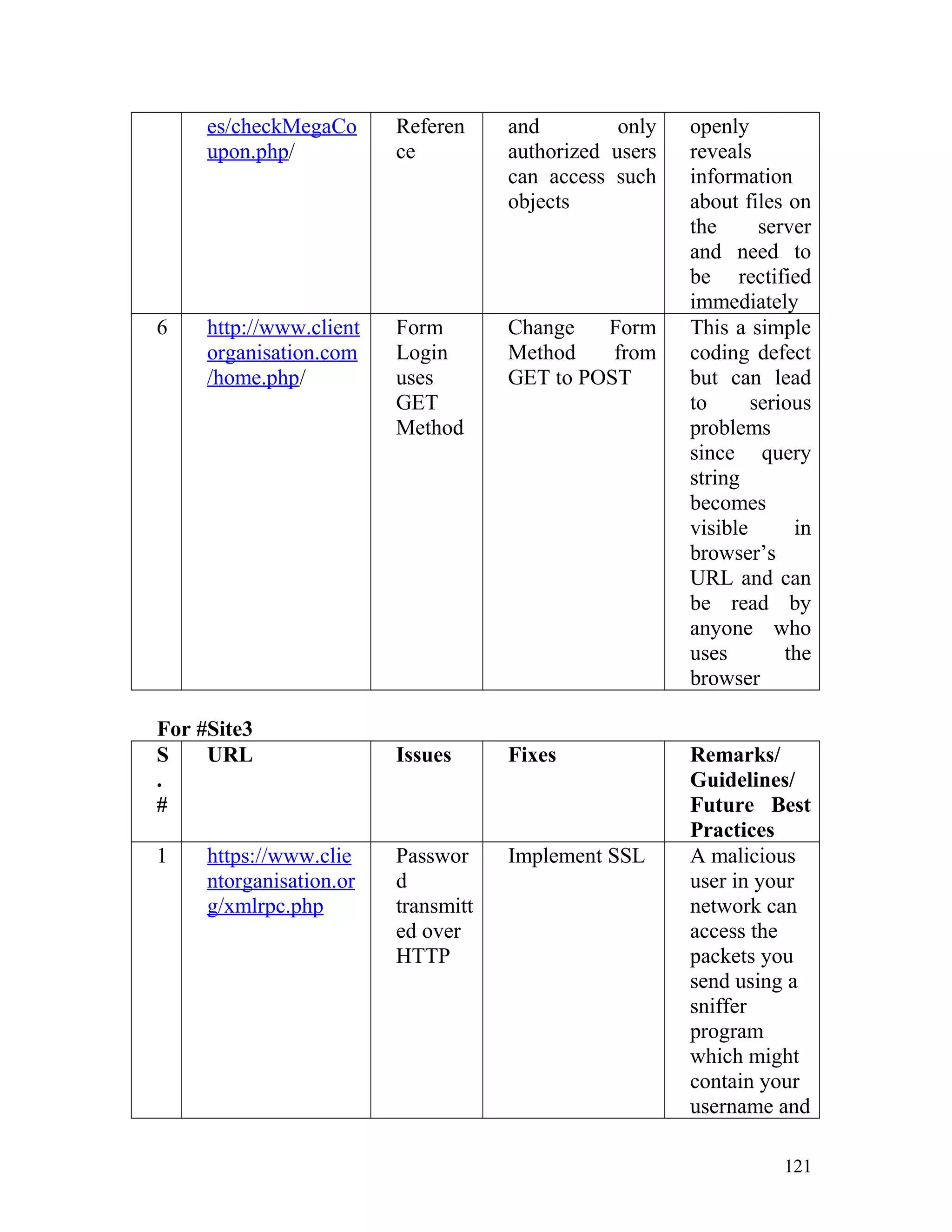
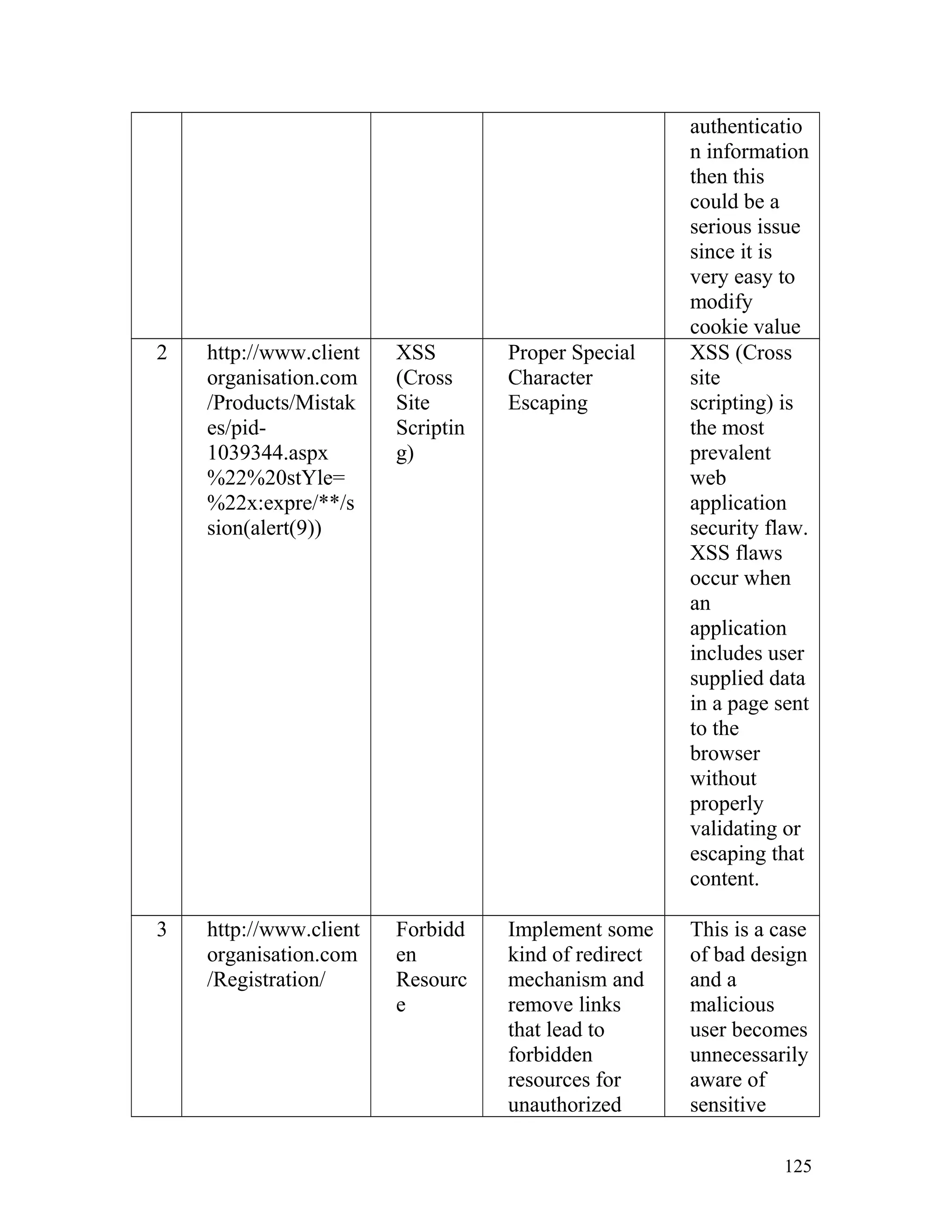
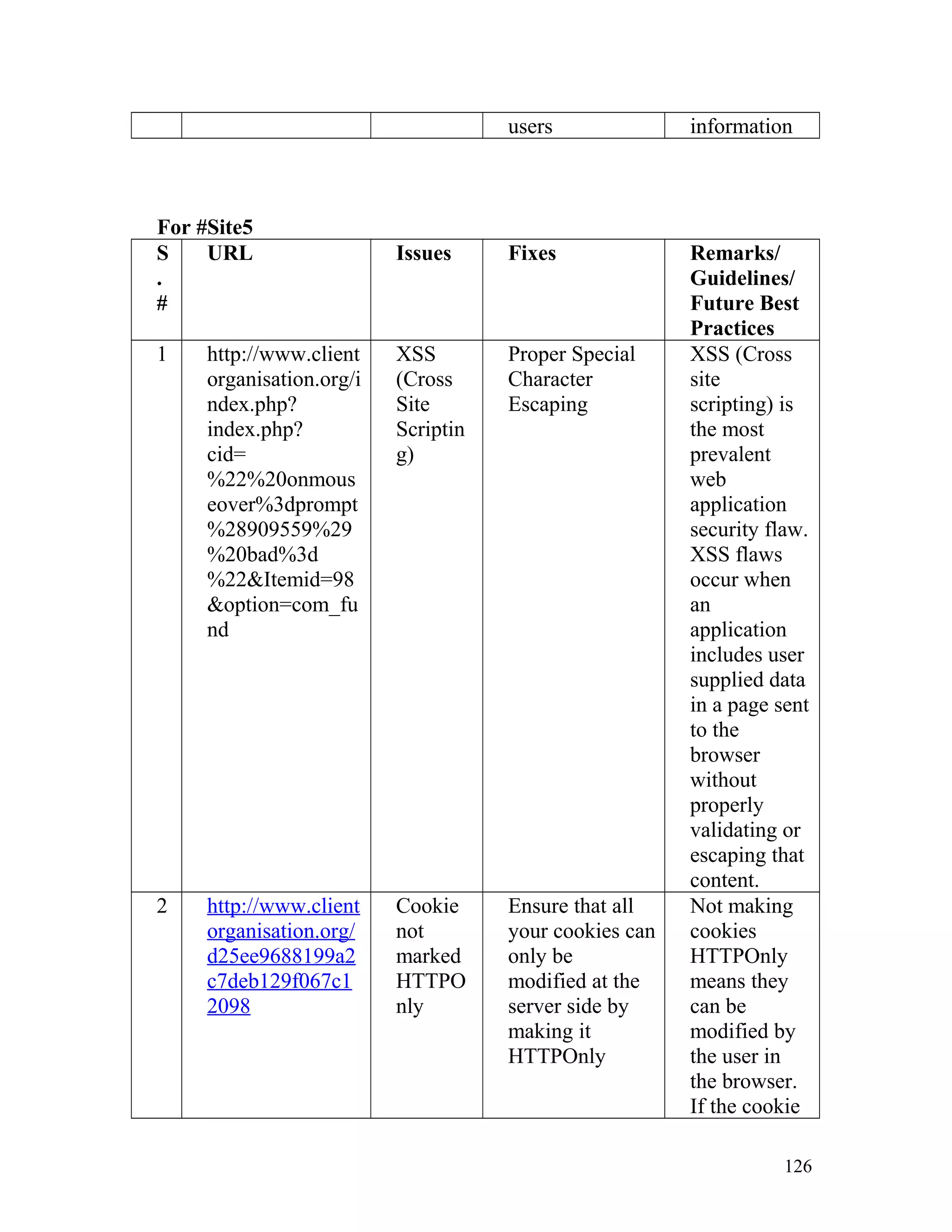
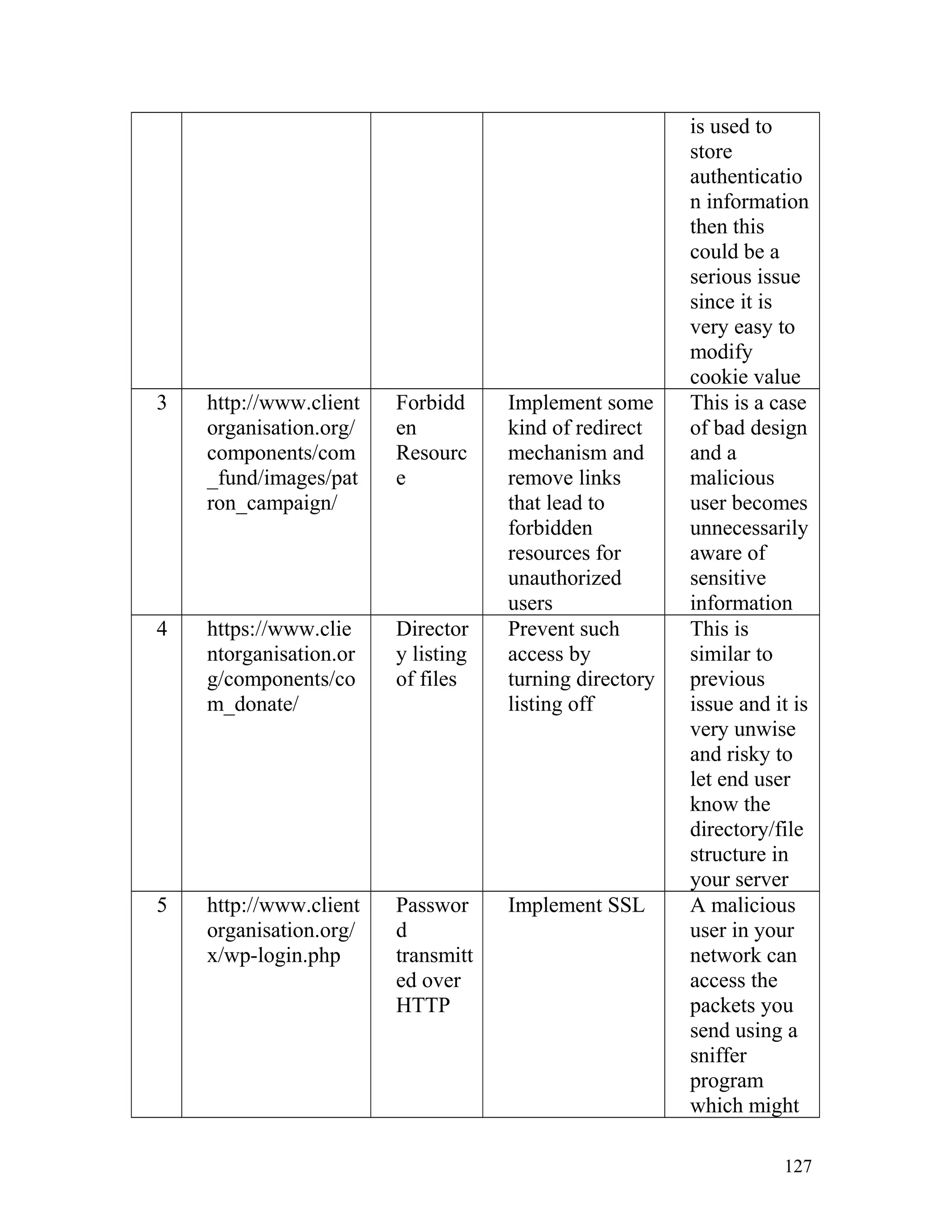
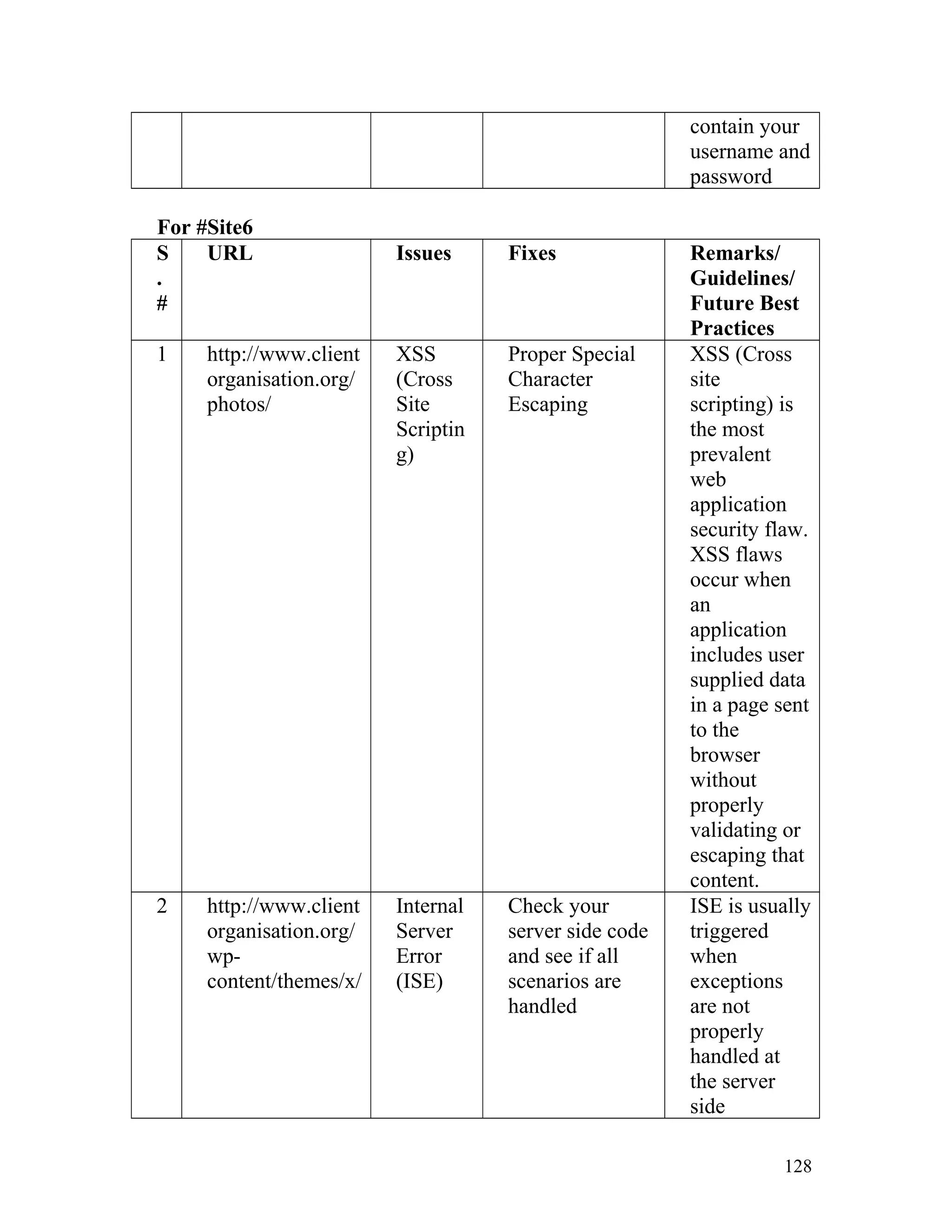
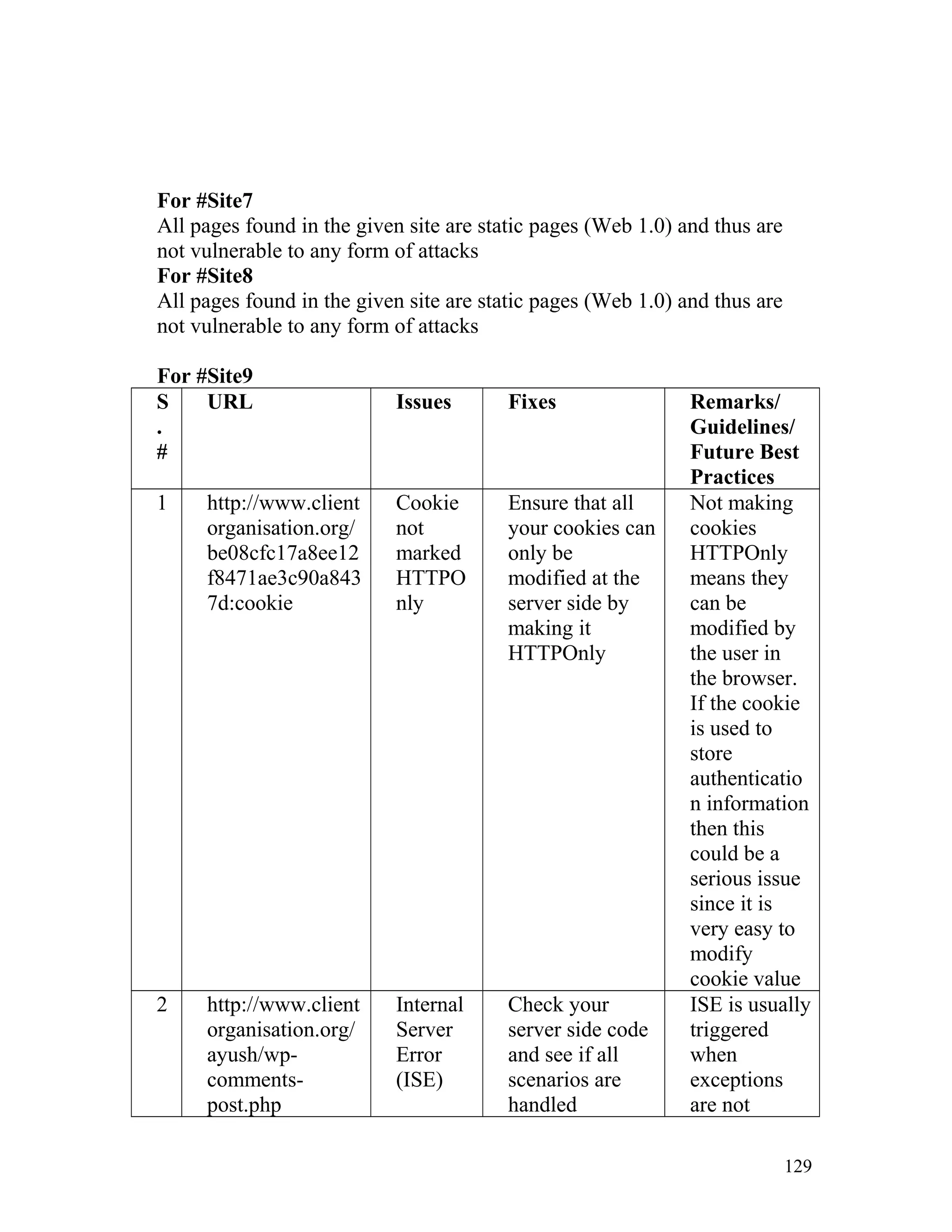
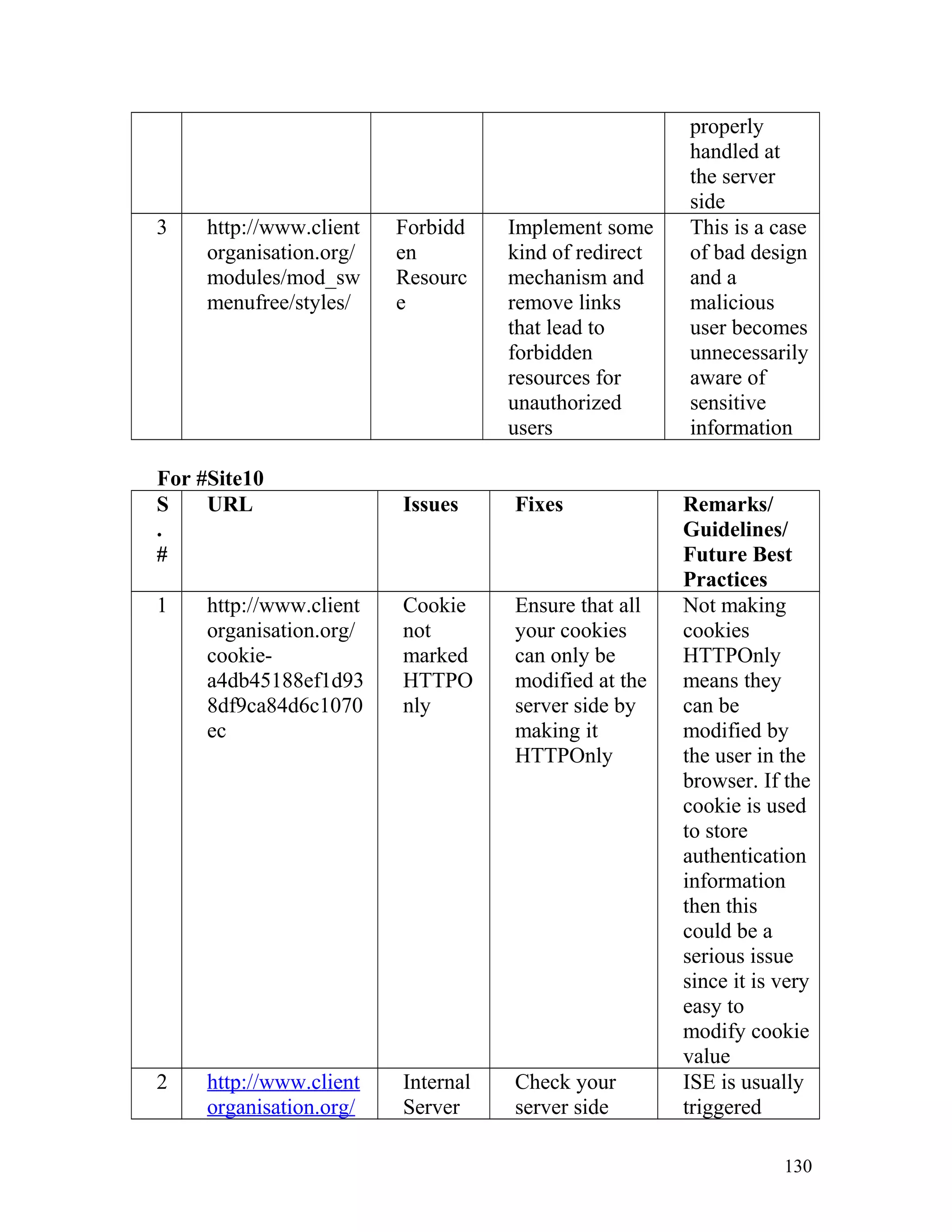
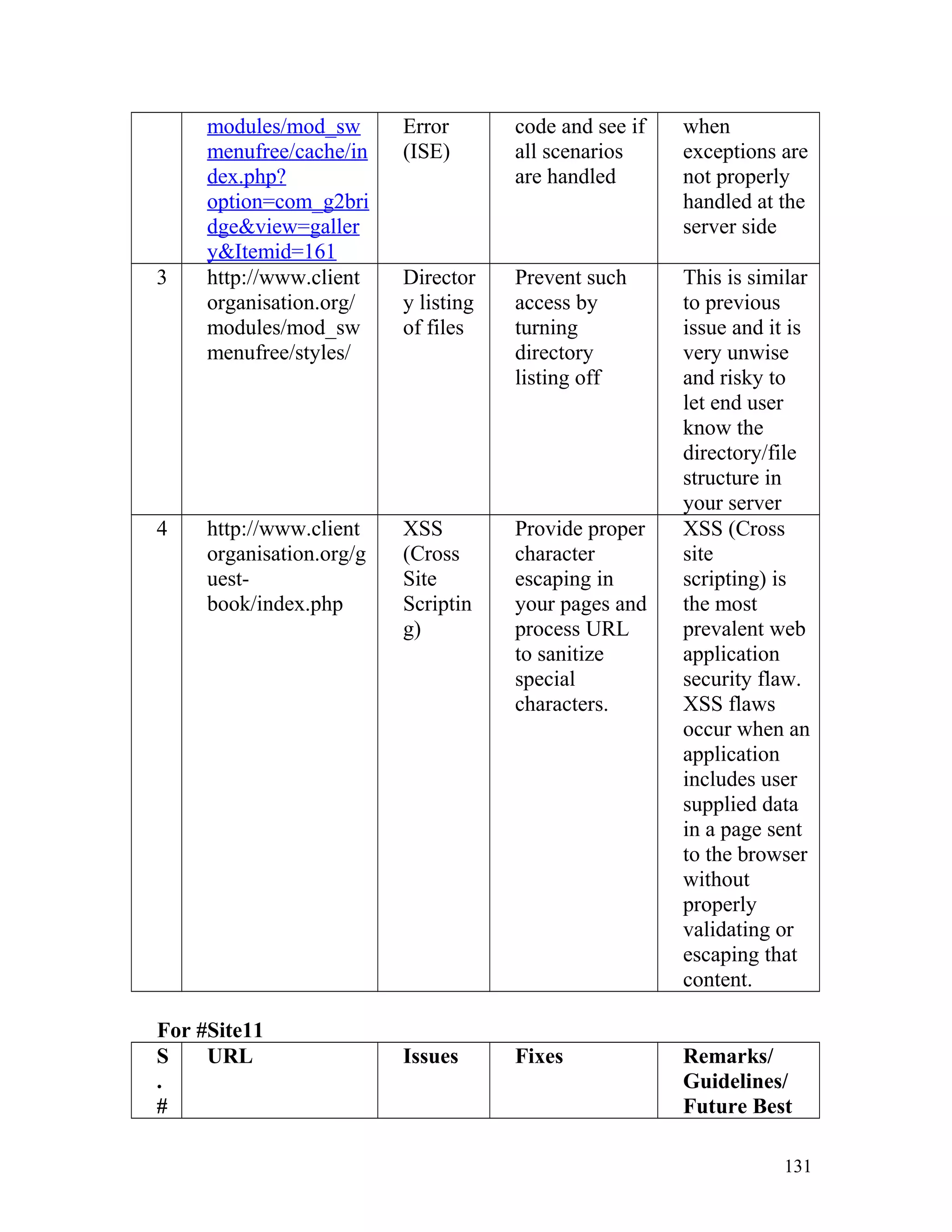
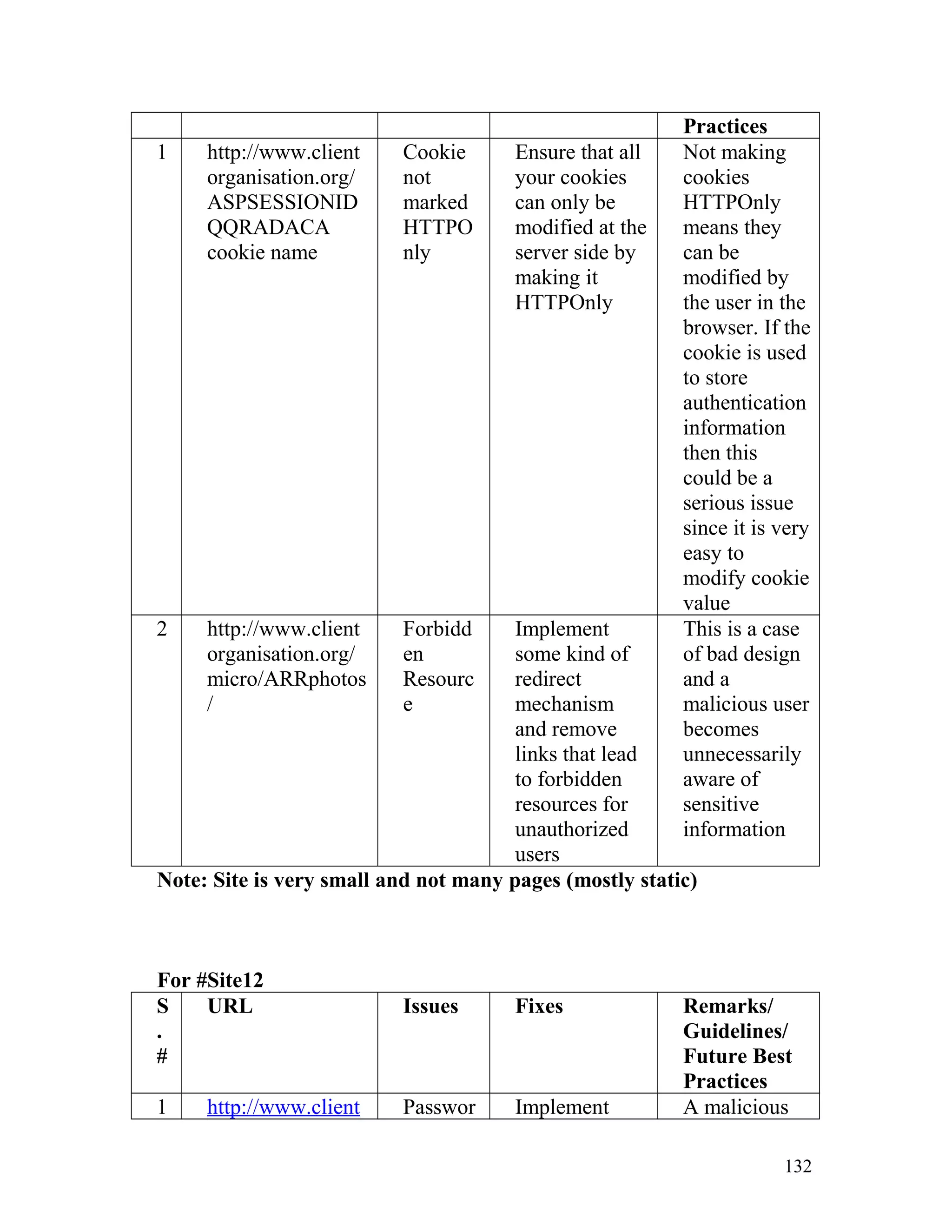
![Recommendation: Such pages must be made inaccessible directly by
users by implementing redirect mechanisms to other safer pages. Access to
above mentioned pages must only be granted after proper authorization
and authentication.
8. Insecure Direct Object Reference
In one of the client's site on the page http://www.clientorganisation.com/
(path)/checkmegacoupon.php
The following gets generated on the browser screen.
Warning: include_once(../includes/DBConfig.php) [function.include-
once]: failed to open stream: No such file or directory
in/apps/users/adminieo/public_html/ieo/resources/includes/checkMega
Coupon.php on line 2
Warning: include_once() [function.include]: Failed opening
'../includes/DBConfig.php' for inclusion
(include_path='.:/usr/lib/php:/usr/local/lib/php')
in/apps/users/adminieo/public_html/ieo/resources/includes/checkMega
Coupon.php on line 2
Warning: include_once(../ieoadmin/CommLib.php) [function.include-
once]: failed to open stream: No such file or directory
in/apps/users/adminieo/public_html/ieo/resources/includes/checkMega
Coupon.php on line 3
Warning: include_once() [function.include]: Failed opening
'../ieoadmin/CommLib.php' for inclusion
(include_path='.:/usr/lib/php:/usr/local/lib/php')
in/apps/users/adminieo/public_html/ieo/resources/includes/checkMega
Coupon.php on line 3
Invalid Coupon
74](https://image.slidesharecdn.com/semi-automatedsecuritytestingofwebapplications-140730122043-phpapp01/75/Semi-Automated-Security-Testing-of-Web-applications-73-2048.jpg)