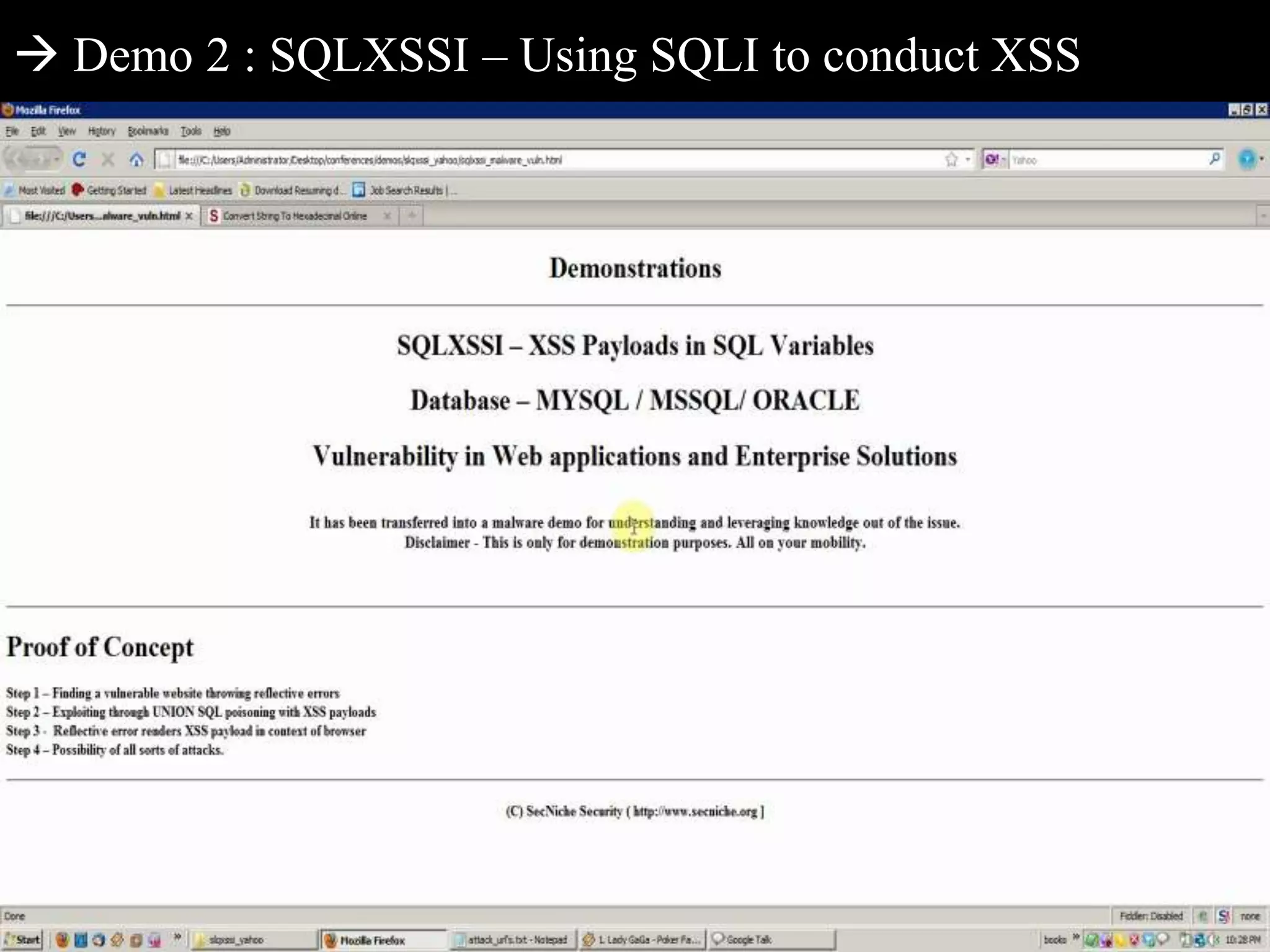
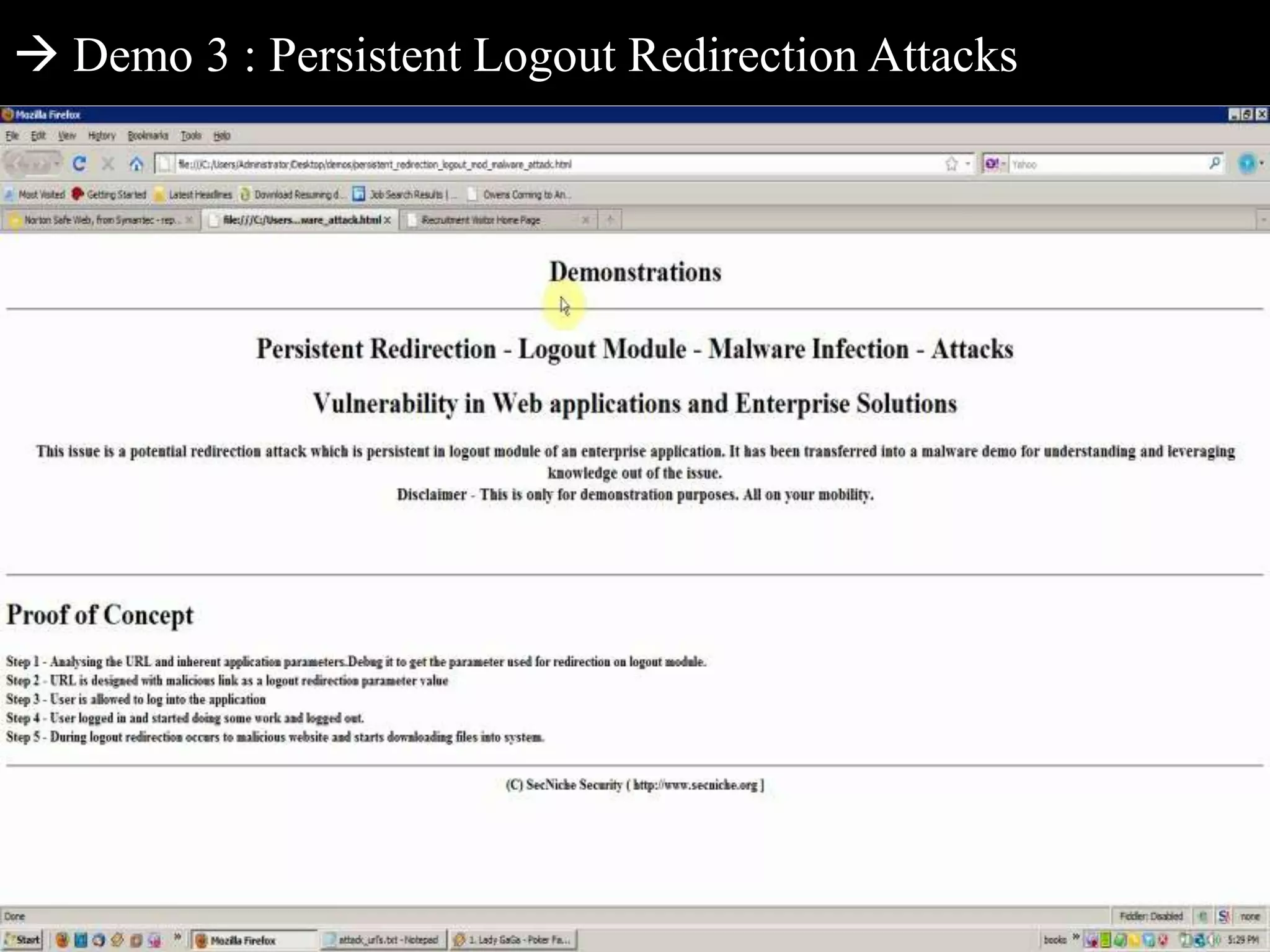
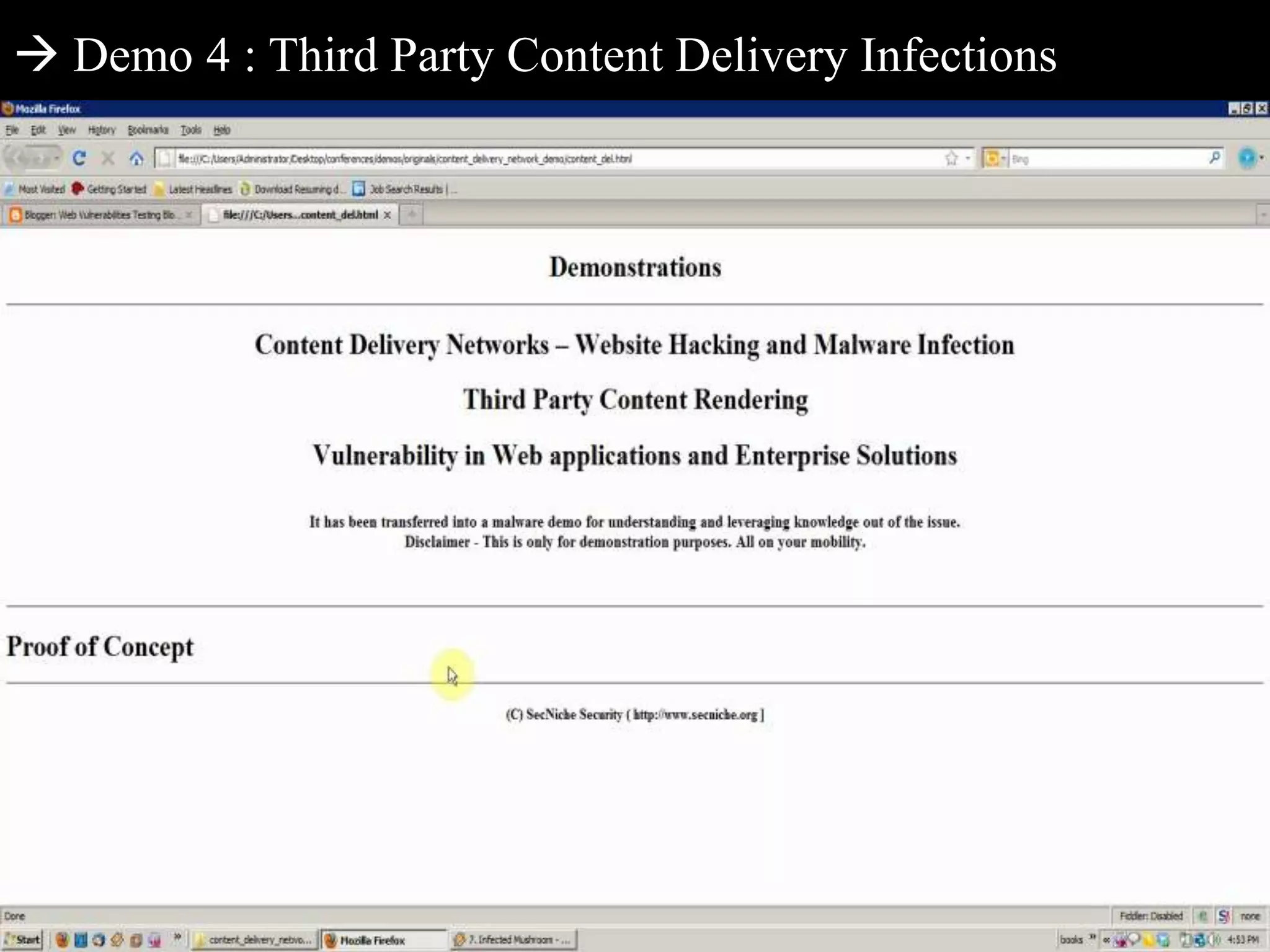
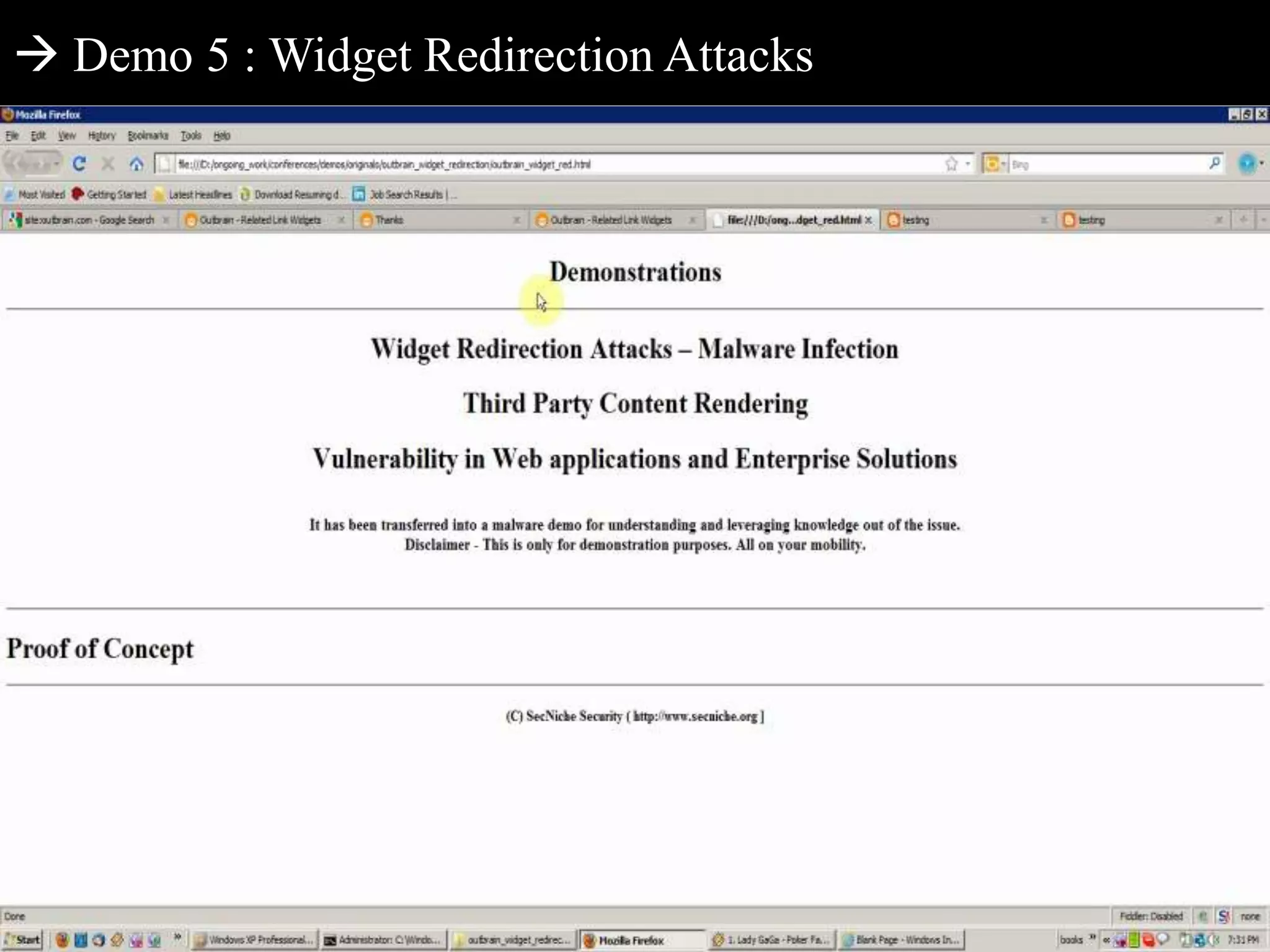
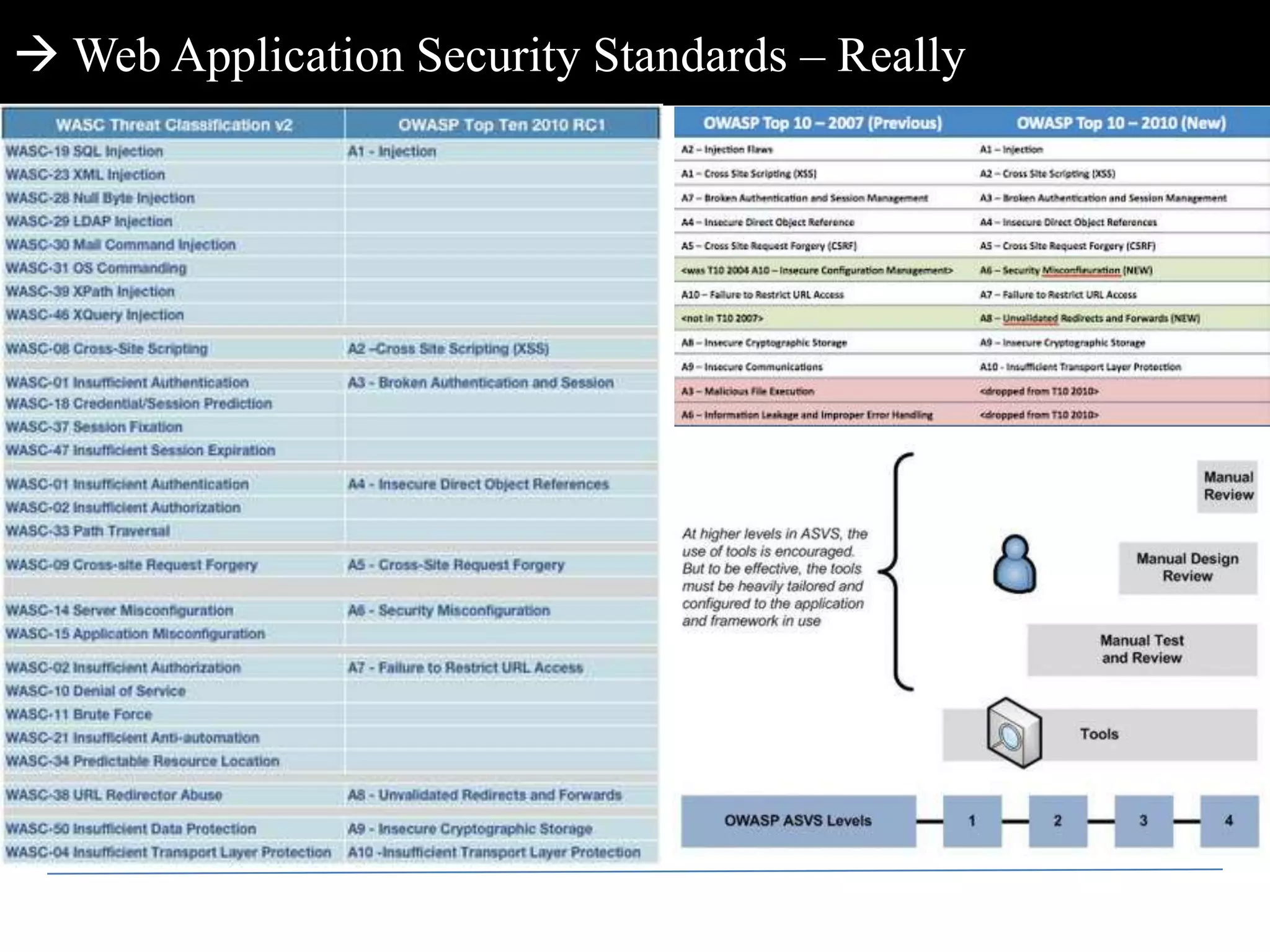
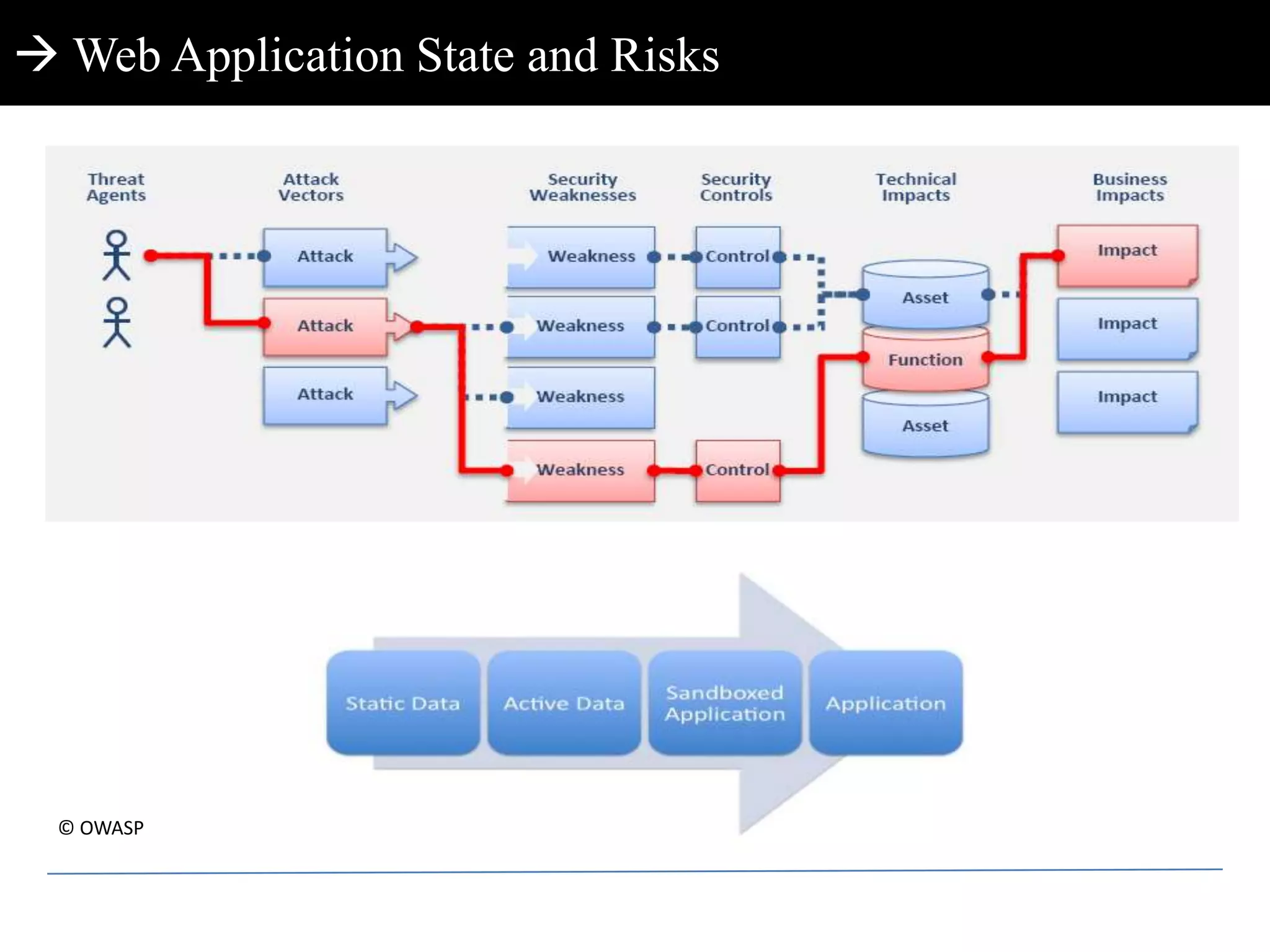
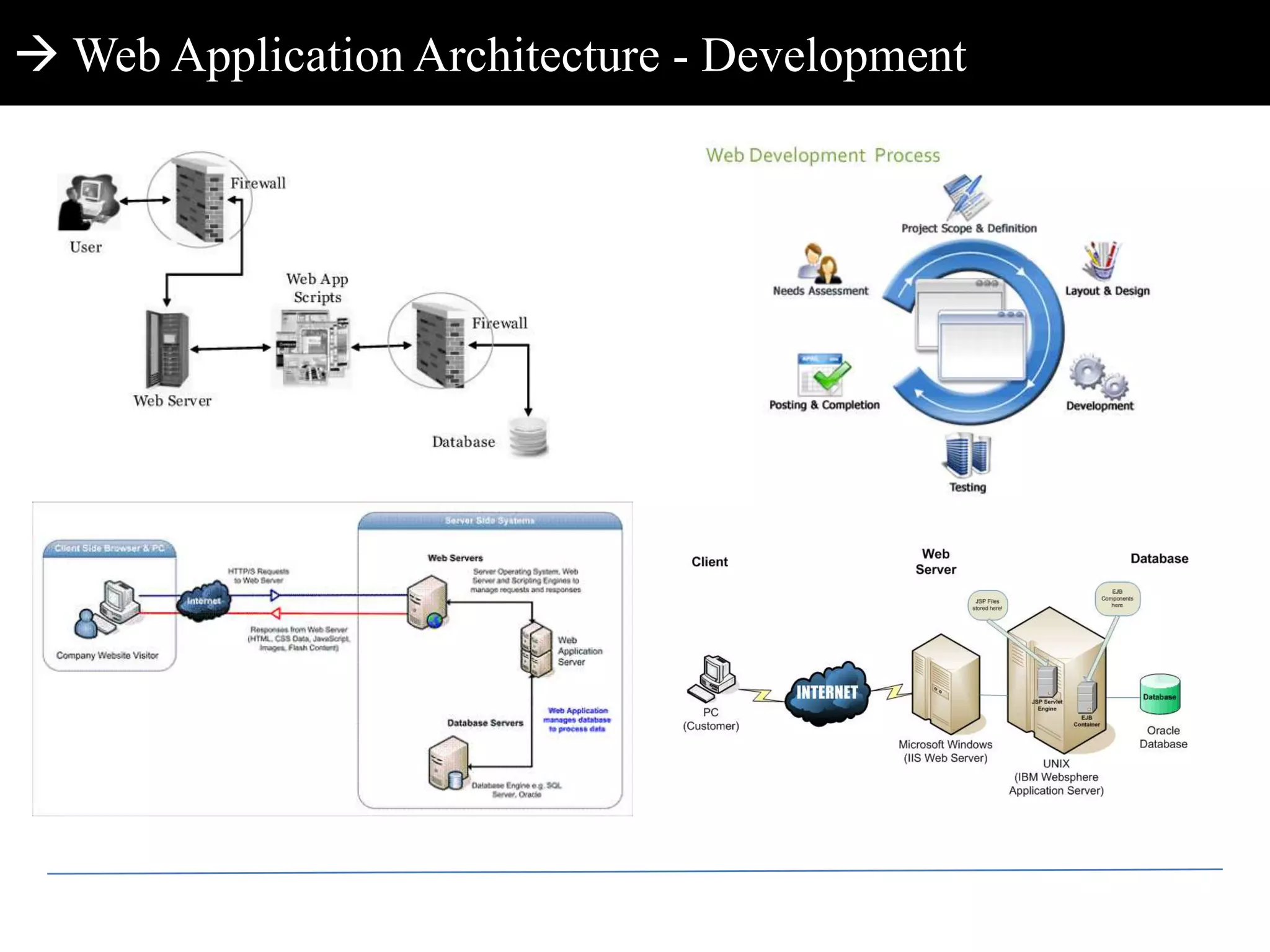
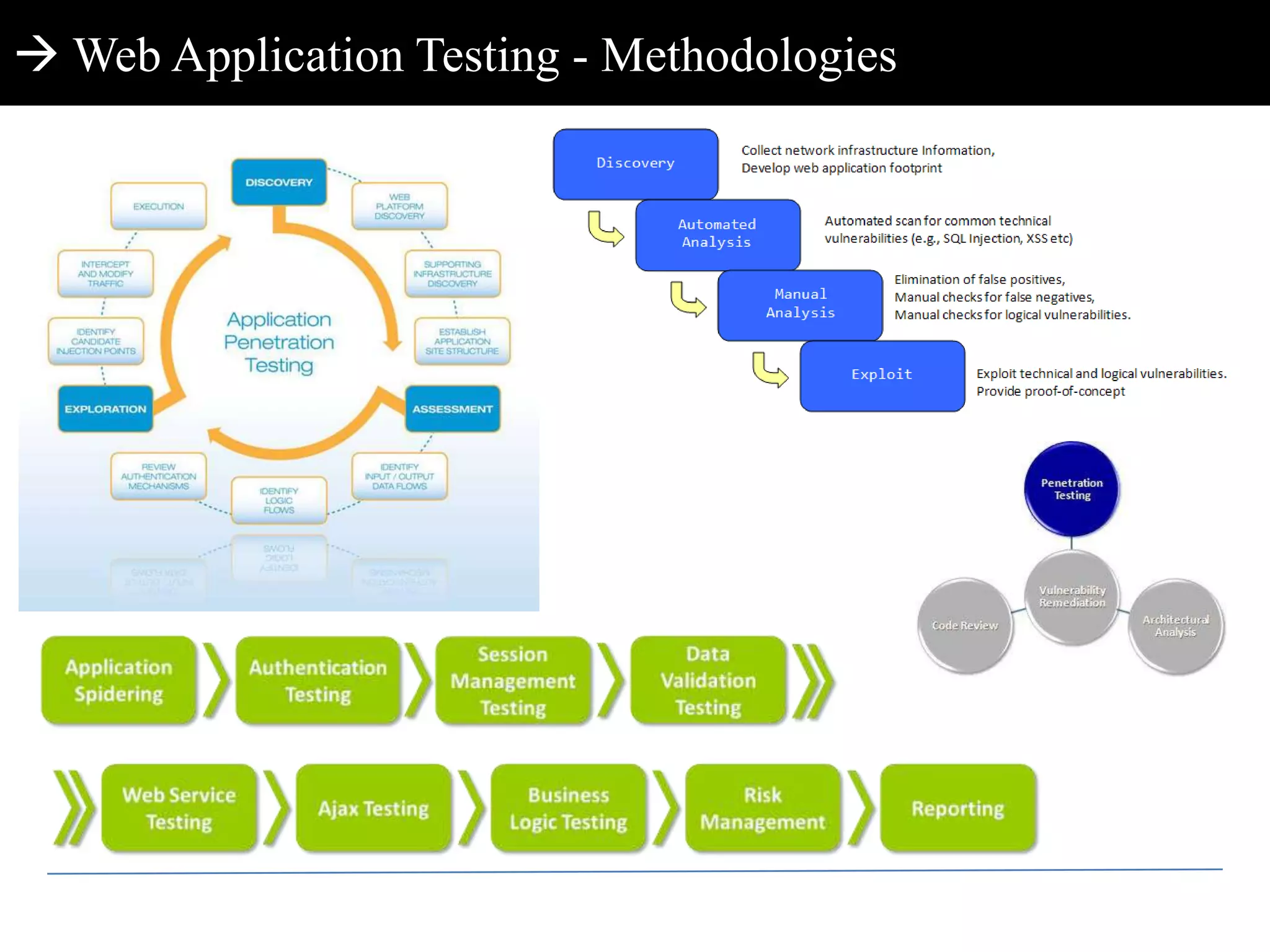
This document discusses web application penetration testing and security. It begins with an overview of web application security standards and realities, noting that standards do not encompass all vulnerability types or attacks. It then discusses web application testing methodologies and realities of security testing. The main part of the document focuses on facets of web application penetration testing, highlighting the importance of thinking beyond surface issues to more hidden vulnerabilities. It concludes with demonstrations of different web application attacks.
![Web Maniac Hacking TrustAditya K Sood [adi_ks [at] secniche.org] SecNiche Security](https://image.slidesharecdn.com/hackerhalted2010-101015182523-phpapp01/75/Hacker-Halted-Miami-USA-2010-1-2048.jpg)



![Do you think the design of web application matters? [to what extent ]](https://image.slidesharecdn.com/hackerhalted2010-101015182523-phpapp01/75/Hacker-Halted-Miami-USA-2010-16-2048.jpg)