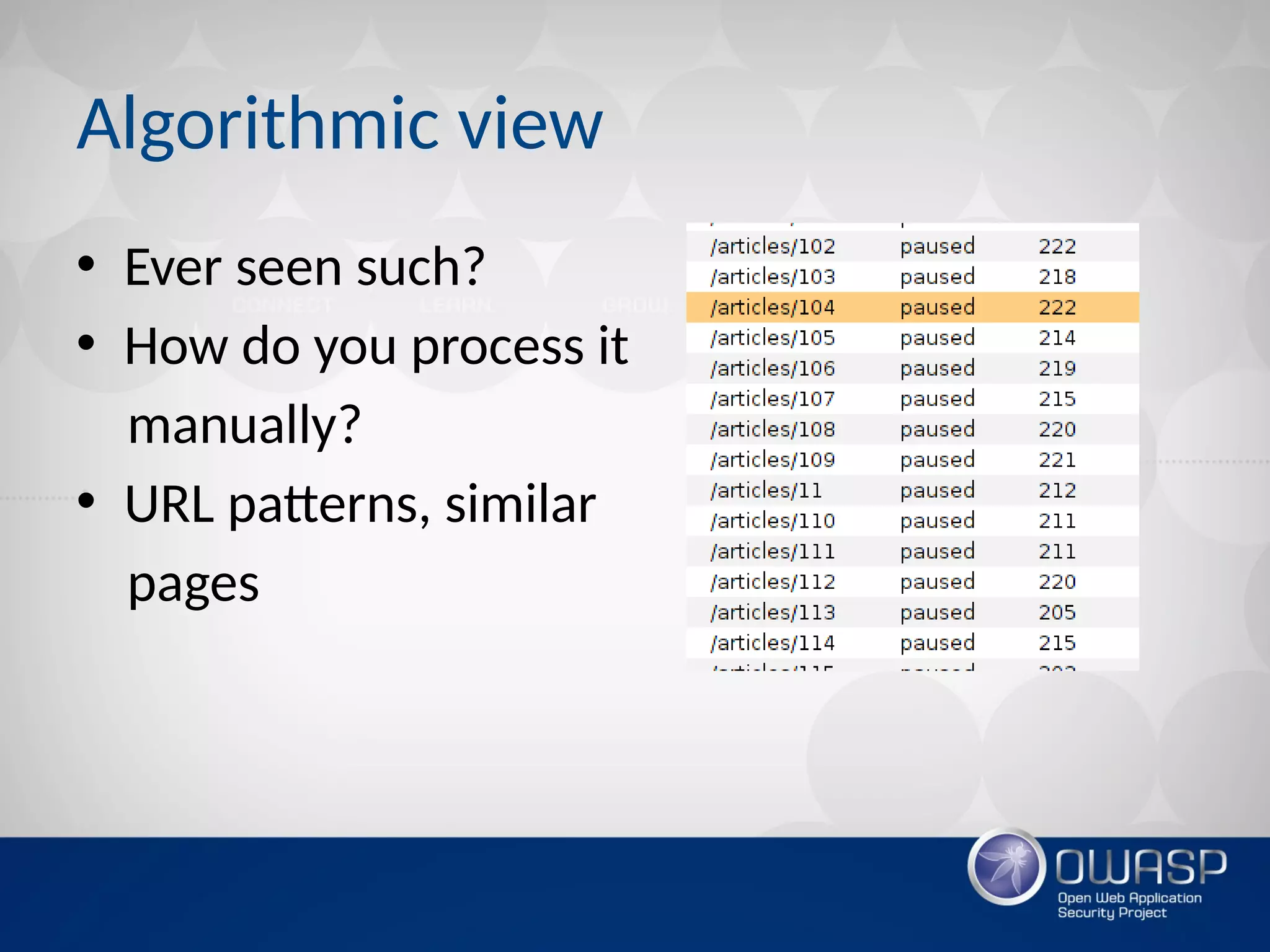
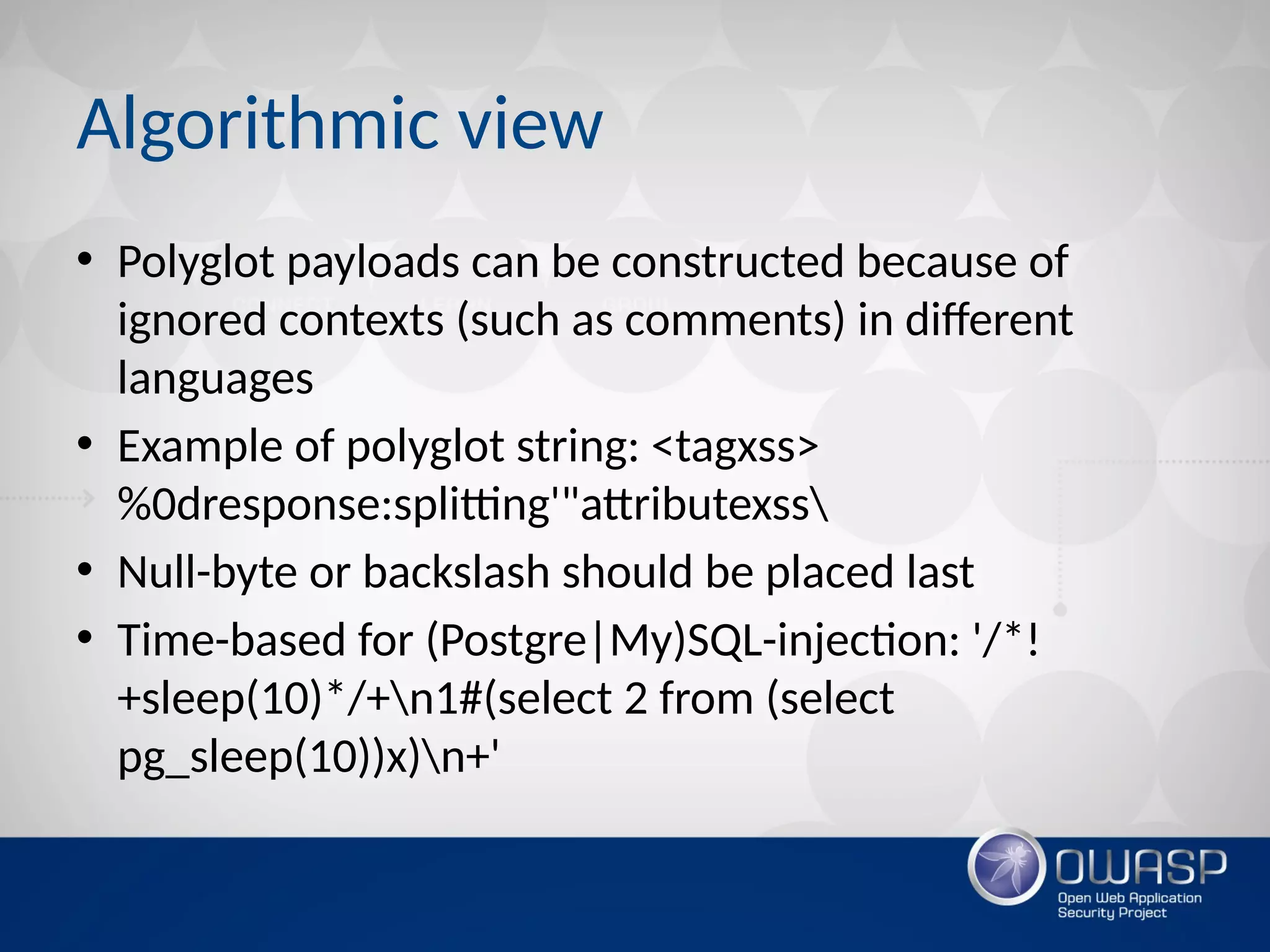
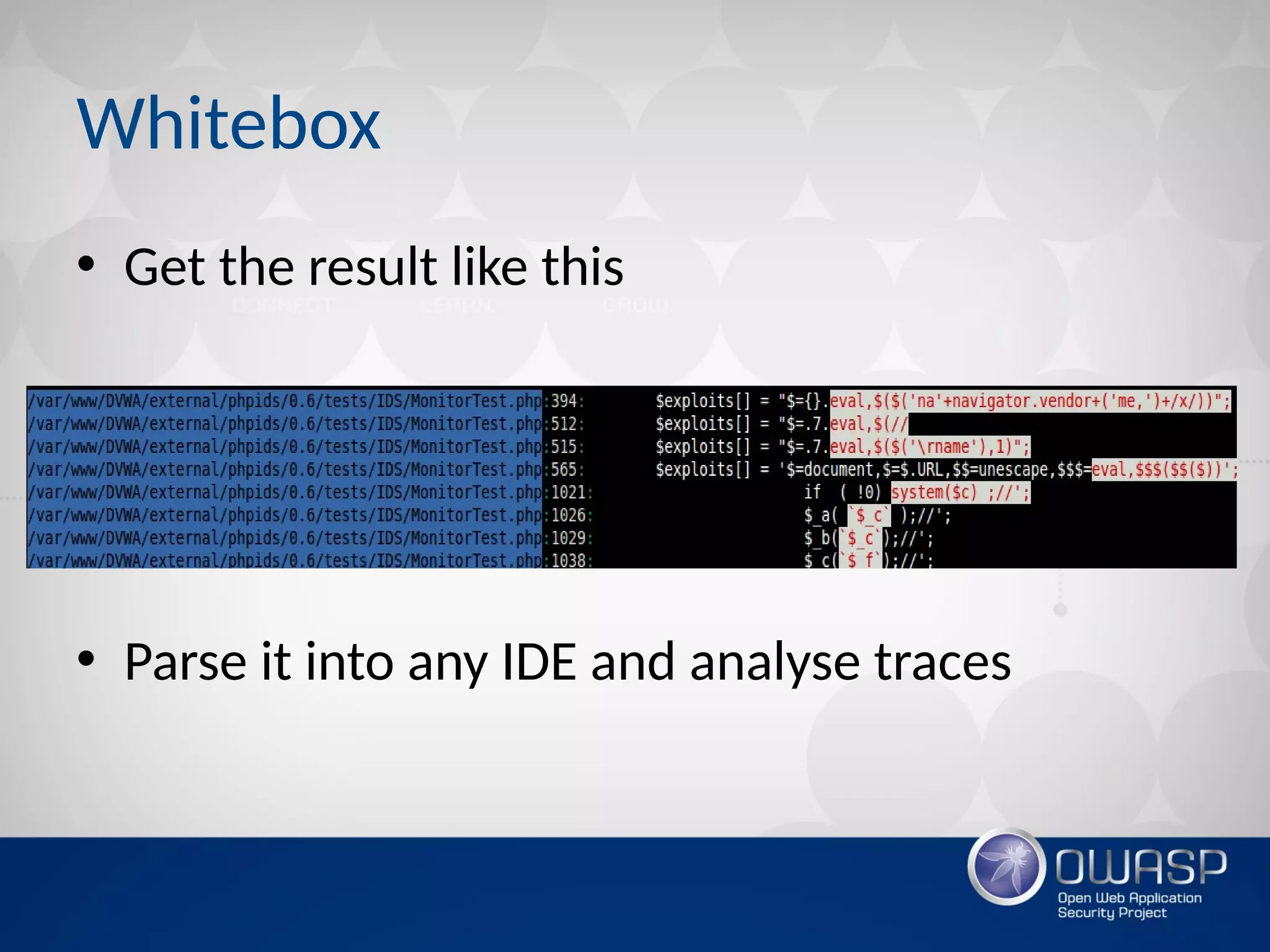
The document discusses techniques for rapidly testing web applications through automation to find security vulnerabilities within a limited time frame (T) and network requests (Q). It proposes prioritizing testing based on features like platform, number of inputs, and response status. Algorithmic approaches are suggested like using polyglot payloads to check for multiple issues simultaneously, building a decision tree to classify hackability, and calculating page priorities to guide the scan. Whitebox testing techniques like custom grep scripts to find code vulnerabilities are also covered. The goal is to build an efficient automated web application scanner that traverses the "pwning paths graph" to find bugs within the constraints.