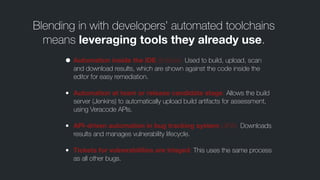
The document outlines eight patterns for integrating continuous code security within agile development processes, emphasizing the necessity of addressing security vulnerabilities early in the software development lifecycle. It advocates for collaboration between security assessments and development tools to help automate code analysis, streamline vulnerability management, and enhance overall security without compromising efficiency. Implementing these practices allows organizations to reduce risks associated with web applications, ultimately leading to more secure and efficient code deployment.