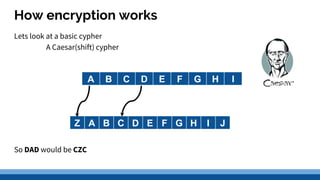
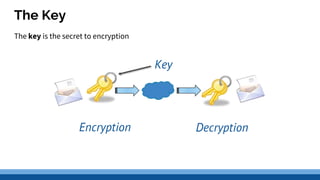
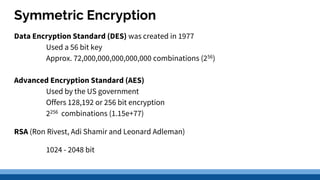
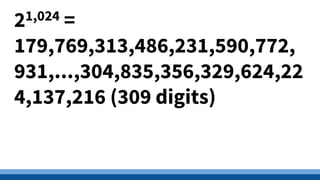
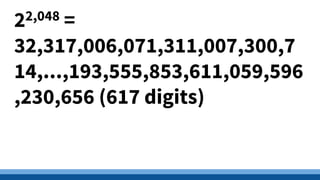
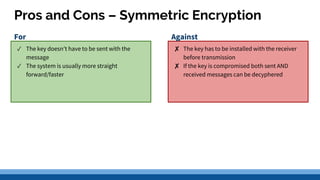
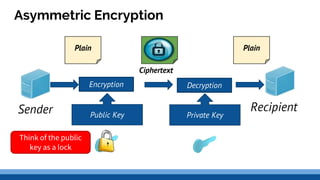
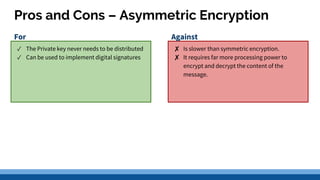
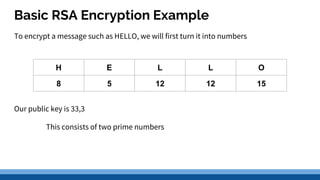
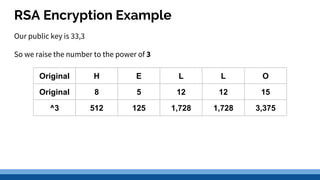
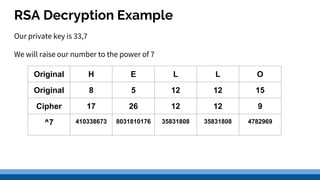
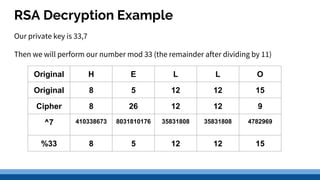
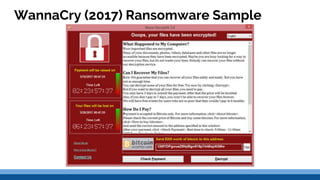
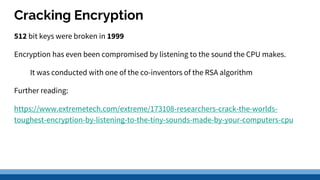
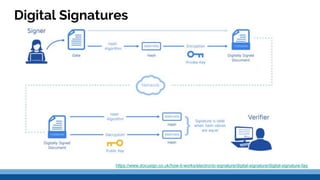
This document discusses security precautions and encryption. It begins by describing encryption as encoding data into another form using a key so that intercepted data is meaningless without decrypting. There are two main encryption methods: symmetric key using the same secret key for encryption and decryption, and asymmetric key using a public/private key pair. Digital certificates and signatures are also discussed as a way to prove digital identity and verify message authenticity. UK computer crime law, the Computer Misuse Act of 1998, is summarized as prohibiting unauthorized computer access, access with criminal intent, and unauthorized/reckless computer impairment.