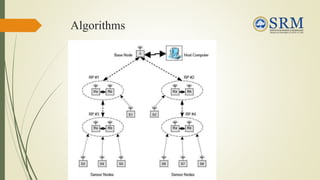
This document discusses security methods for data acquisition in wireless sensor networks. It first introduces wireless sensor networks and some of their challenges, including security issues. It then outlines the objectives of exploring routing algorithms and an intrusion prevention system to authenticate nodes and ensure data integrity and confidentiality. The document describes the proposed system of sensor nodes communicating with router pairs running dual routing algorithms and an intrusion prevention system to filter unauthorized data packets. It presents some experimental results on security and power consumption and concludes that the existing system focuses on self-powered routing but more research is still needed on secure and energy-efficient solutions.