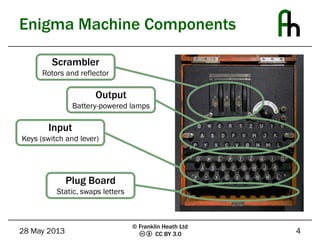
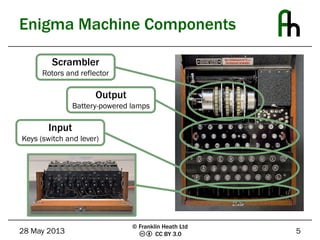
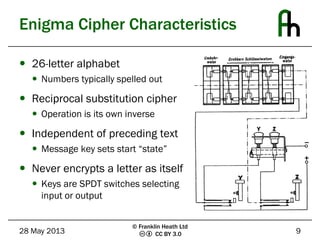
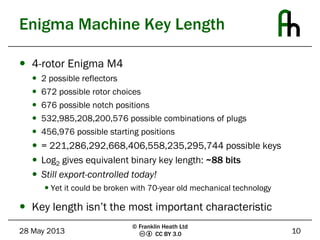
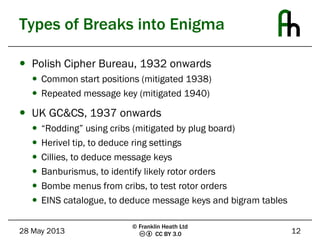
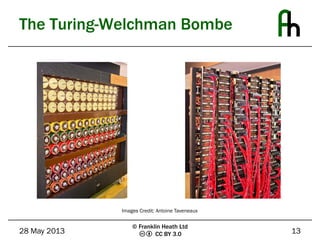
The document discusses the Enigma machine used by the German military during WWII and how Bletchley Park successfully exploited its flaws for codebreaking. It outlines five key lessons learned from this historical event: the subtle flaws in cryptosystems, the necessity of planning for key compromise, the tendency of users to choose weak passwords, the importance of selecting and trusting a good random number generator, and the need to not underestimate adversaries. The Enigma cipher, while sophisticated, was ultimately vulnerable due to weaknesses in key management and predictable user behavior.