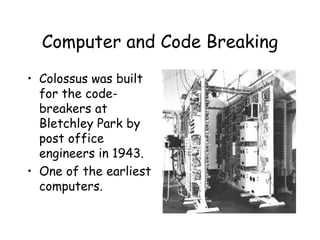
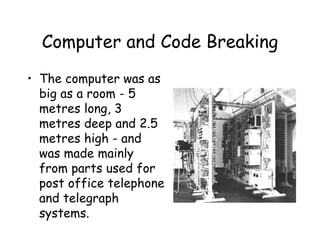
The document discusses the history of cryptography and various cipher machines used during World War II. It describes the German Enigma machine, which could encrypt messages in over 150 million million million ways and how Polish and British codebreakers eventually cracked the Enigma code. It also mentions the American Sigaba machine which was the only system not broken during the war and various other cipher machines developed by other countries during that time period like the Swedish B-21 and the Japanese Purple machine.