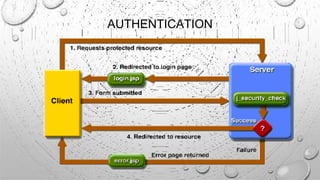
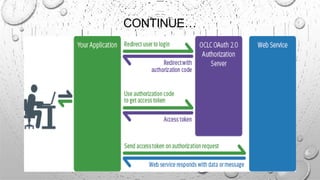
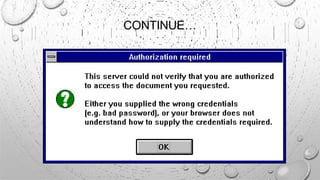
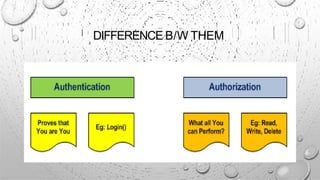
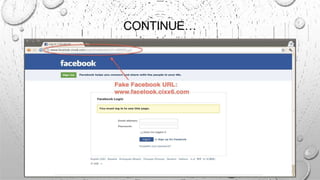
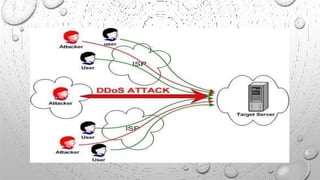
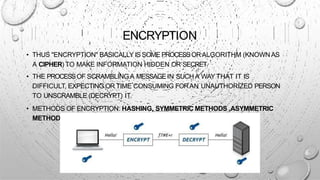
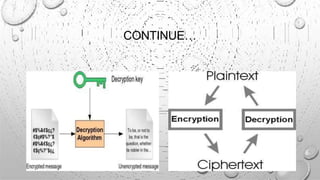
This document discusses various security issues related to e-commerce. It covers types of issues like privacy, authentication, non-repudiation, and phishing. It also discusses security threats including denial of service attacks, unauthorized access, and theft and fraud. Additionally, it outlines different types of securities used like encryption, decryption, cryptography, and biometric authentication.