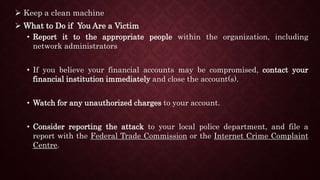
The document summarizes information about data security and privacy. It discusses common cyber attacks like malware, viruses, worms and trojans. It provides online safety basics like protecting against phishing, safe online shopping, and backing up important files. It also covers securing key accounts and devices, managing privacy settings, and issues around India's Aadhaar card system. The document emphasizes that data security is important for organizations to maintain trust and protect against risks from security breaches.



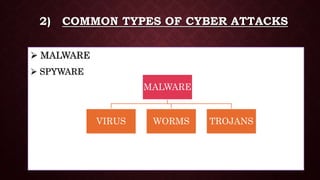
![ VIRUS: Damage Particular file or software
• First Virus Term : Fred Cohen (1985)
• First Network Virus : Creeper [ARPANET - 1970],
oAnti Virus – Reaper (Bob Thomas)
• First PC Virus – ELK Cloner (Richard Skrenla, 1982)
WORMS : Multiples & Copy, affects speed & Memory
TROJANS : Fake software i.e. ads like speed boosters, Memory
clearness, Antivirus, affects Backdoor security](https://image.slidesharecdn.com/datasecurity-191224104324/85/Data-security-5-320.jpg)