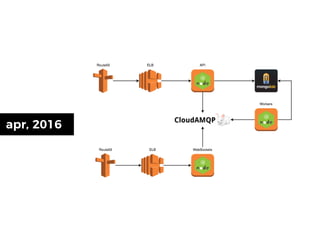
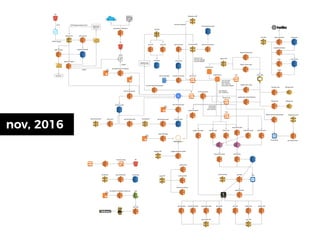
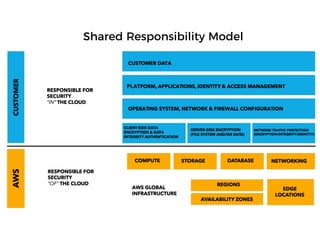
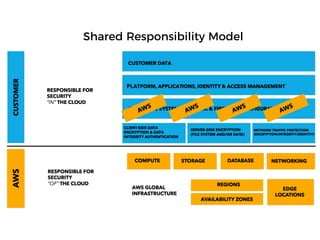
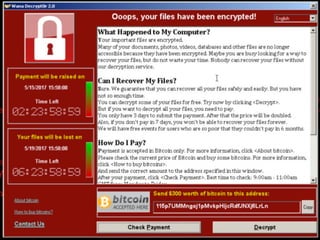
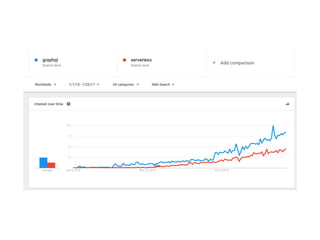
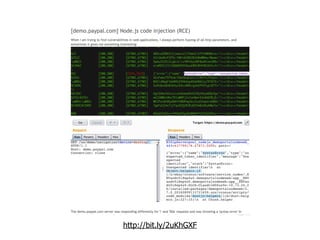
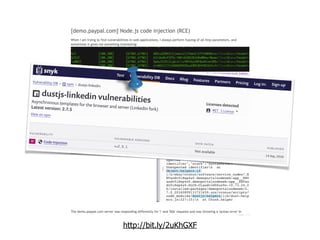
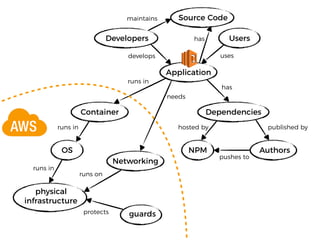
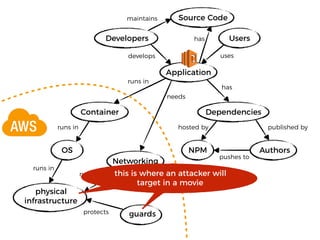
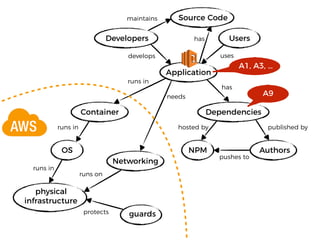
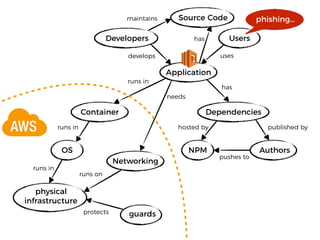
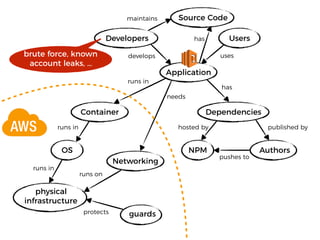
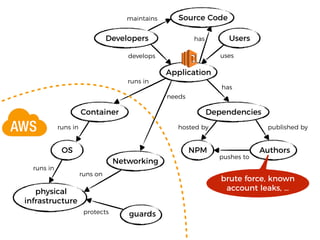
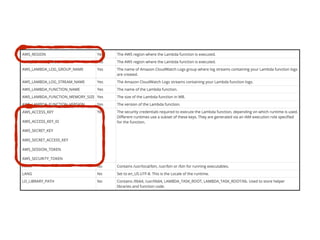
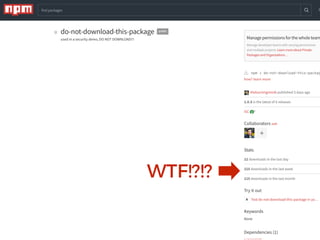
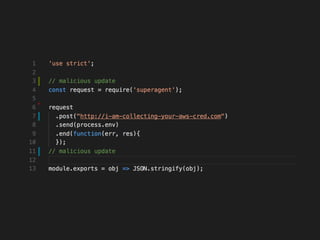
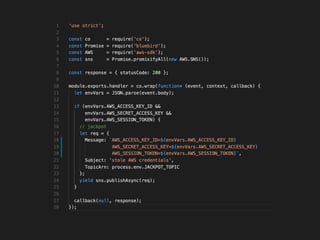
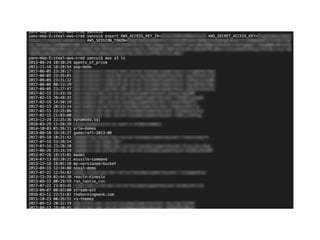
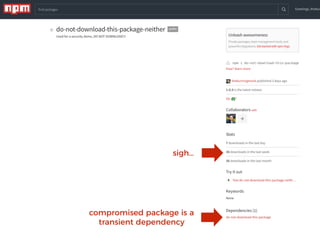
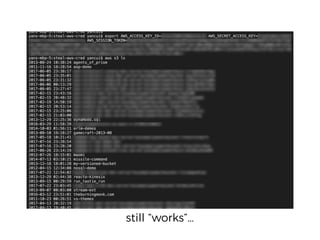
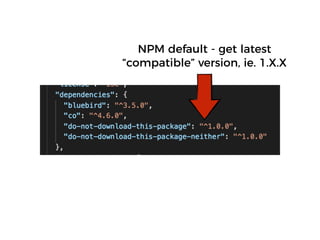
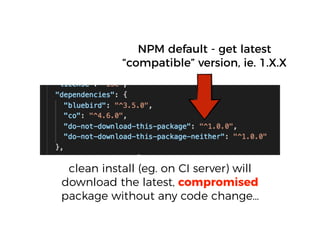
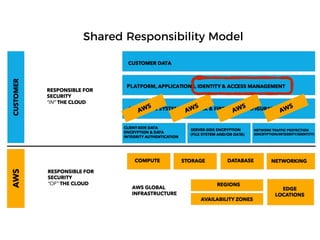
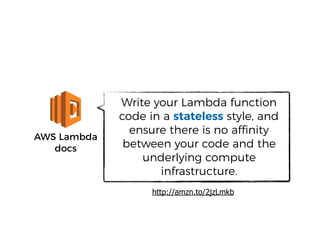
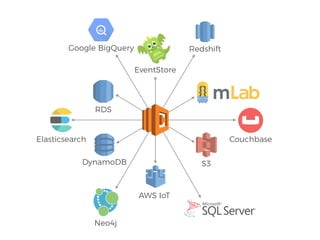
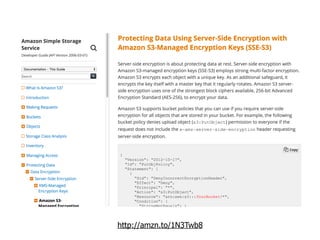
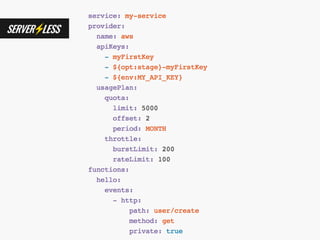
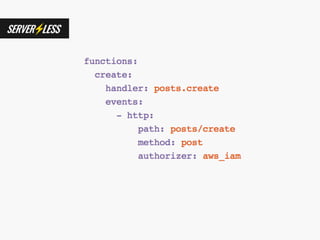
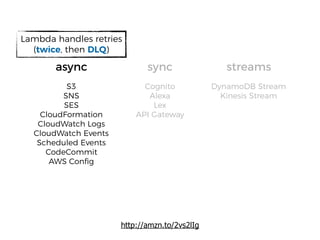
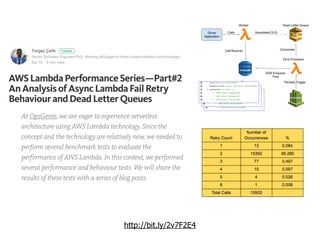
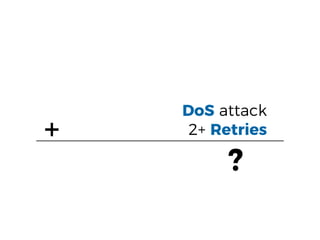
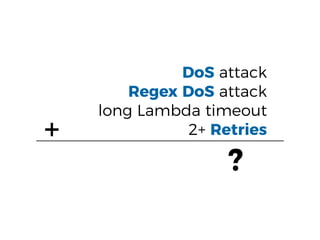
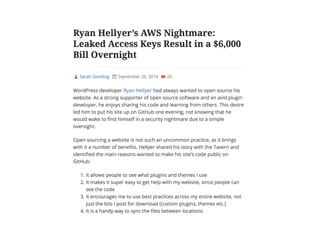
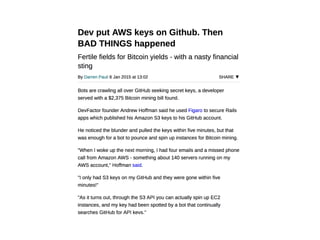
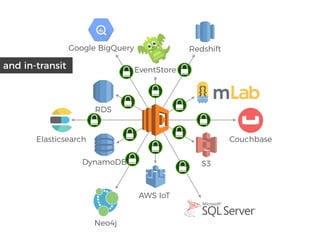
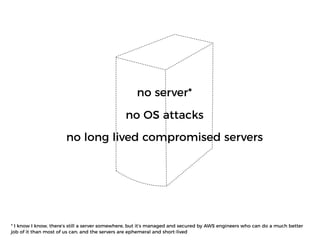
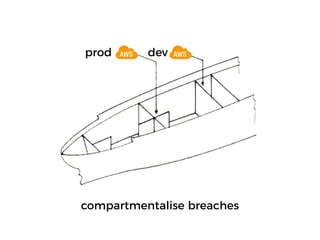
The document discusses the security challenges and risks associated with serverless architecture, particularly focusing on AWS Lambda. It highlights the importance of understanding the shared responsibility model, securing code and dependencies, and implementing the least privilege principle for function access. The author emphasizes the need for vigilance against vulnerabilities introduced by third-party packages and the human element in security breaches.