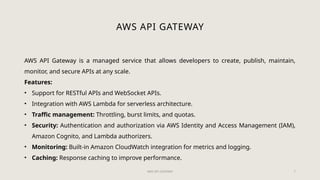
API gateways are crucial in microservice architectures, acting as reverse proxies that manage, route, and secure API traffic. Public cloud API gateways, such as Azure API Management and AWS API Gateway, offer features like traffic management, security enforcement, and integration with other services. Ensuring strong API security through request-based measures and effective authentication and authorization strategies is essential for safeguarding data and services.