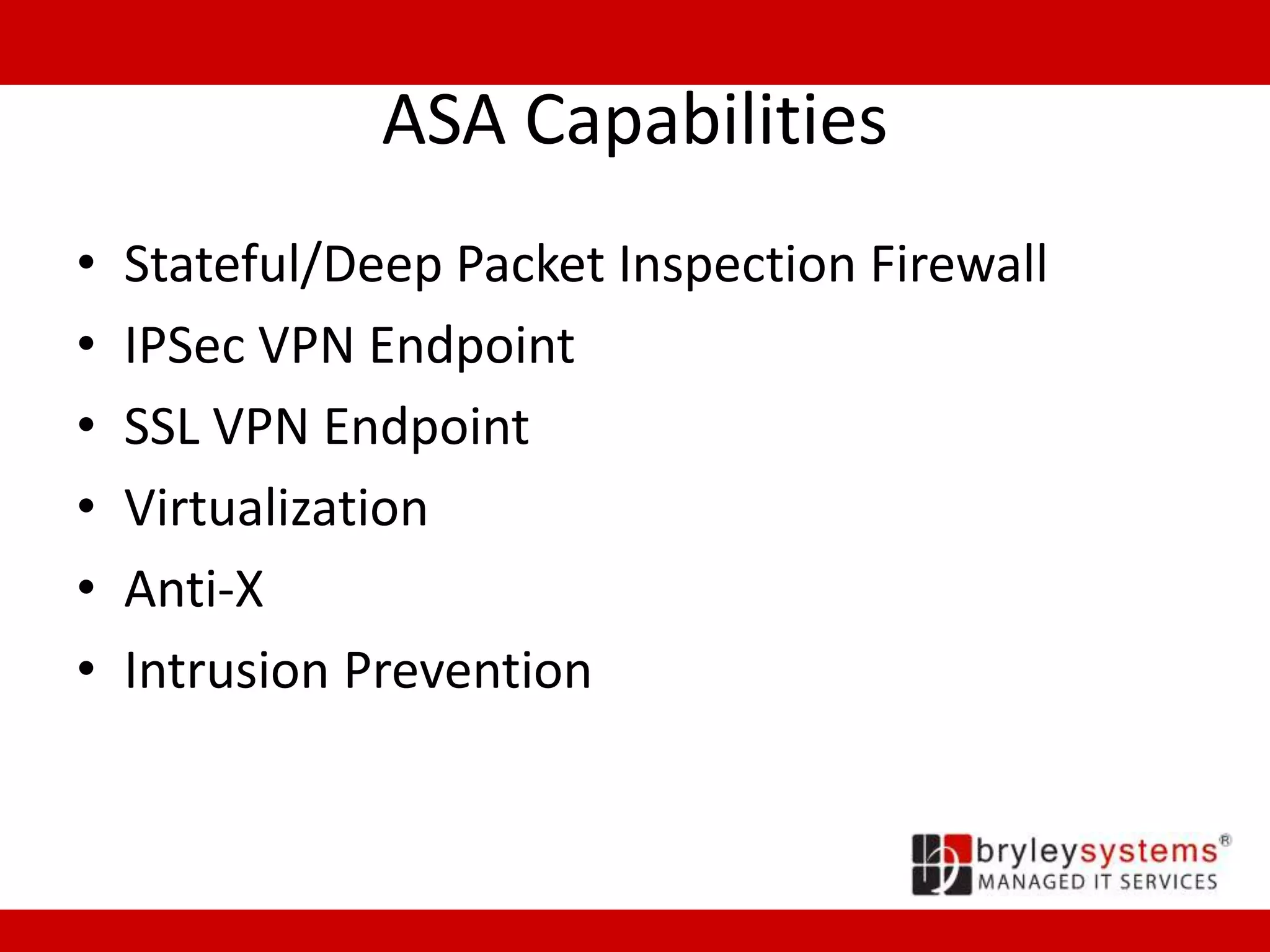
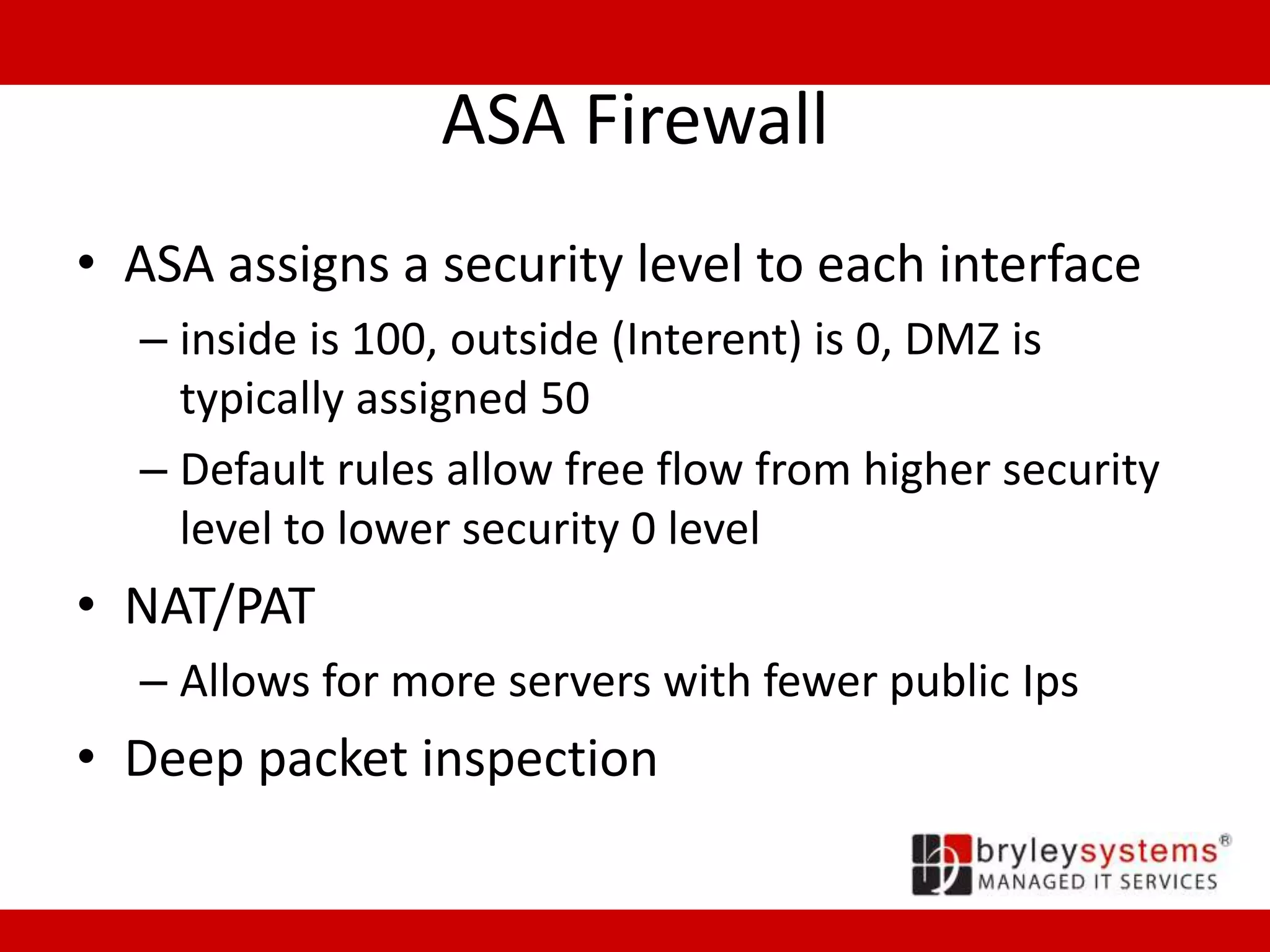
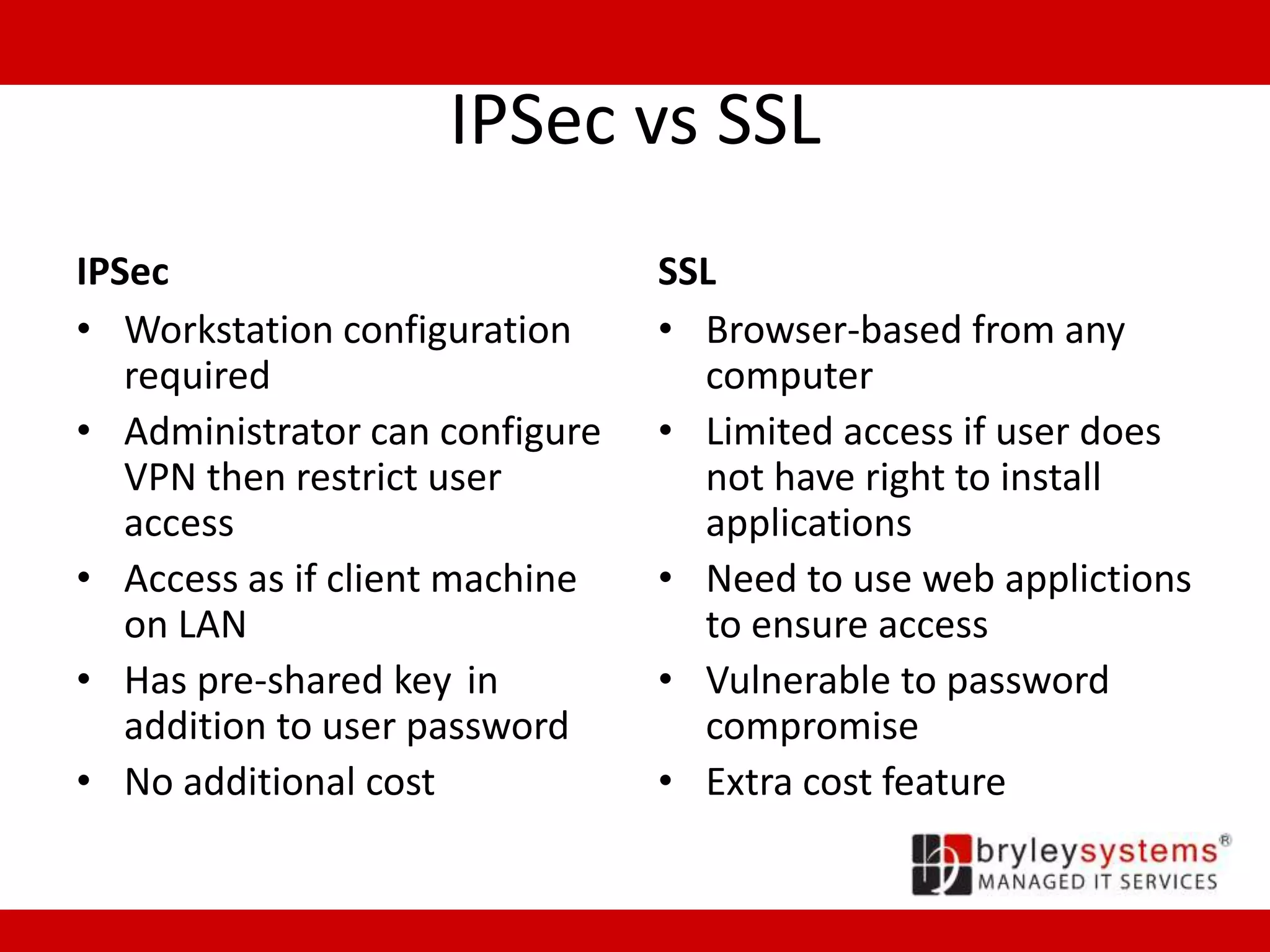
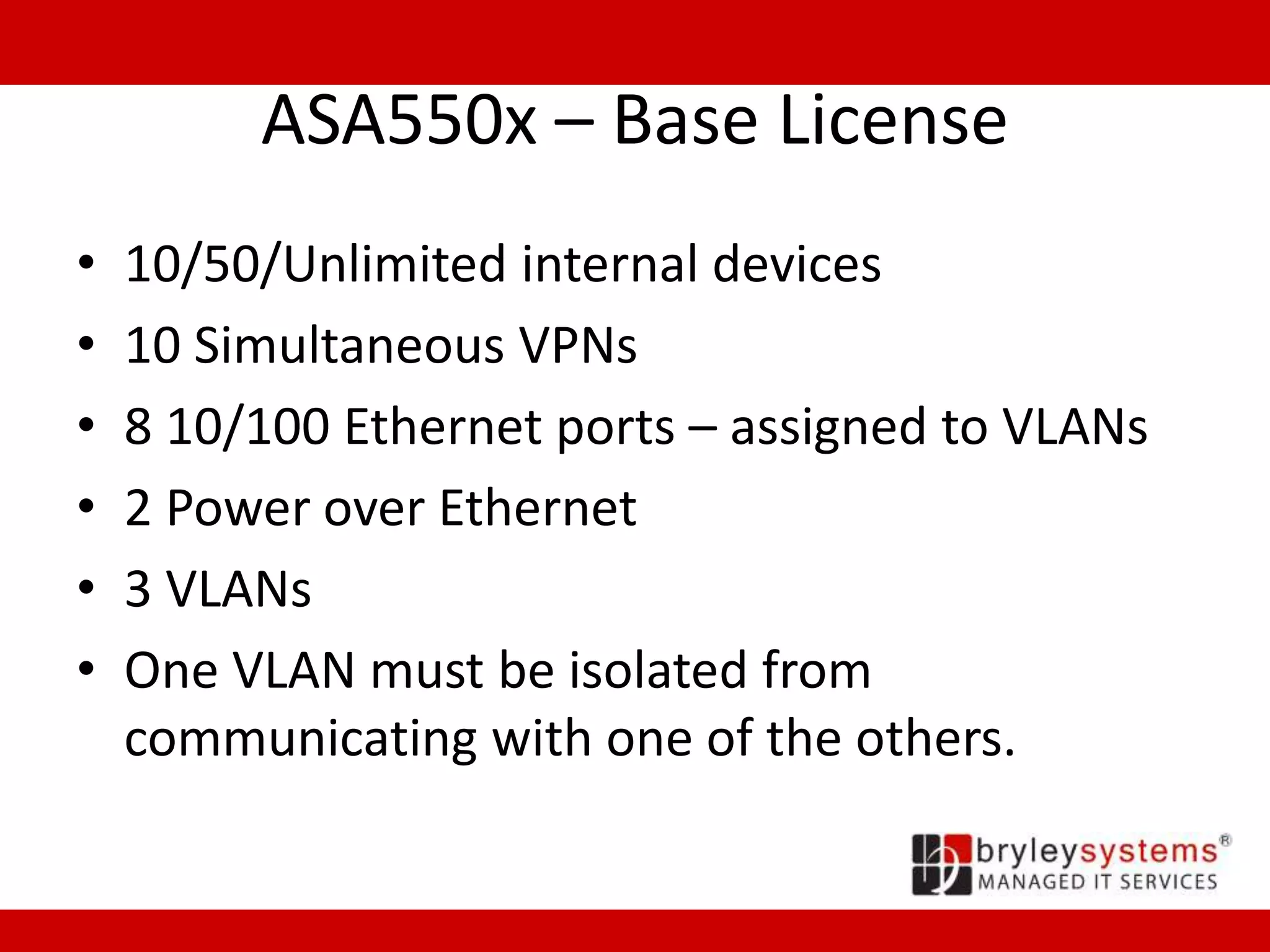
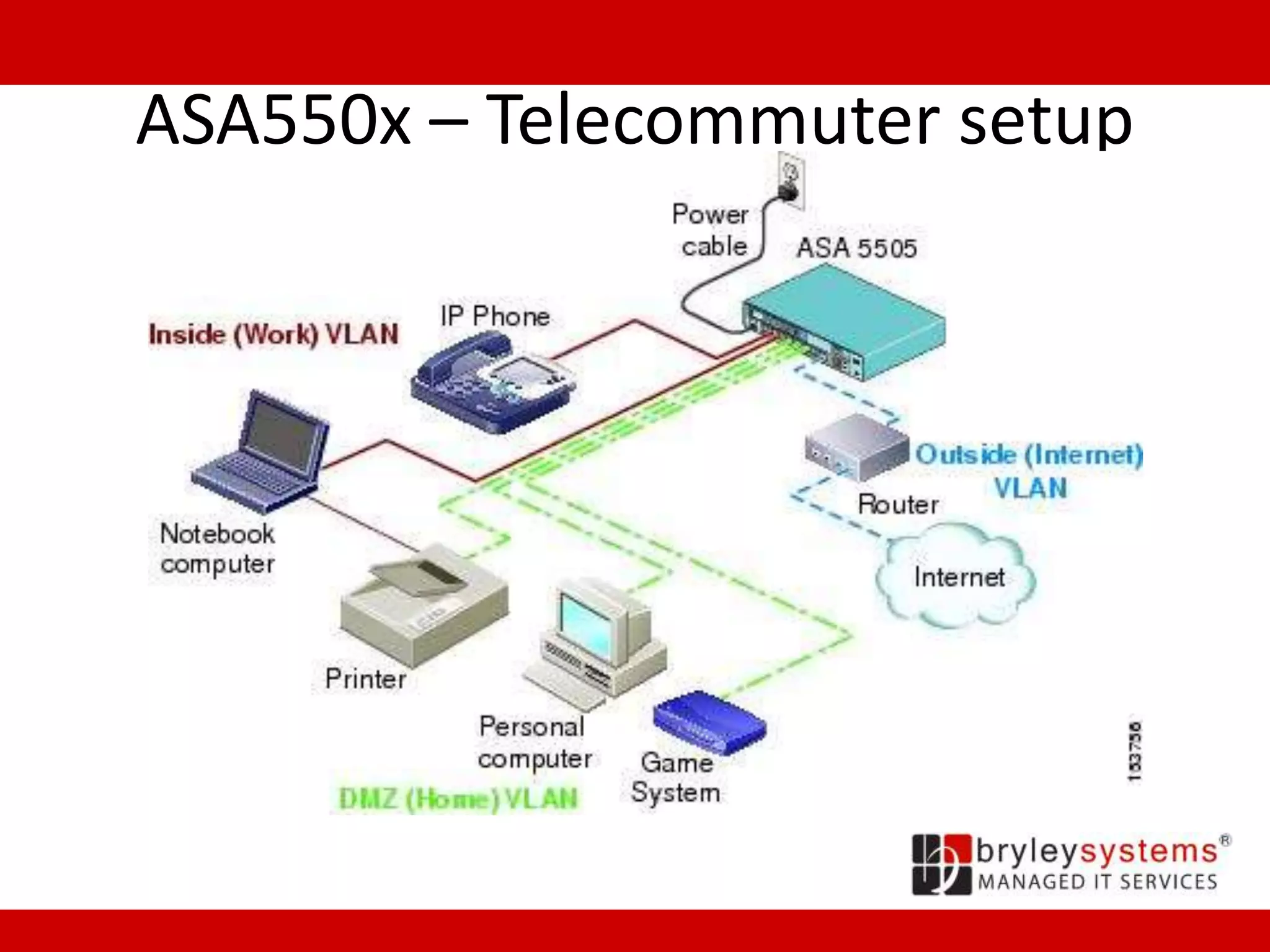
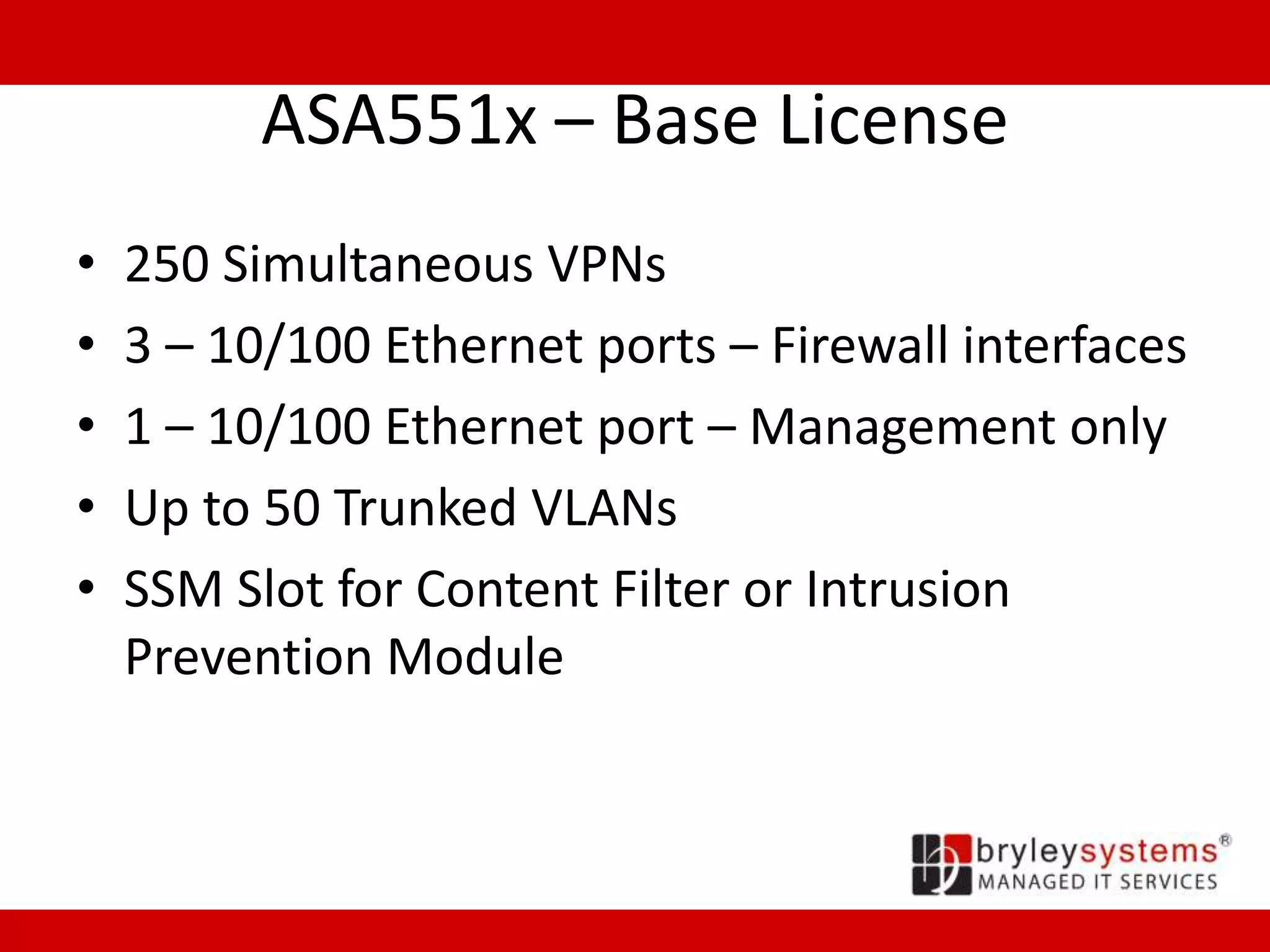
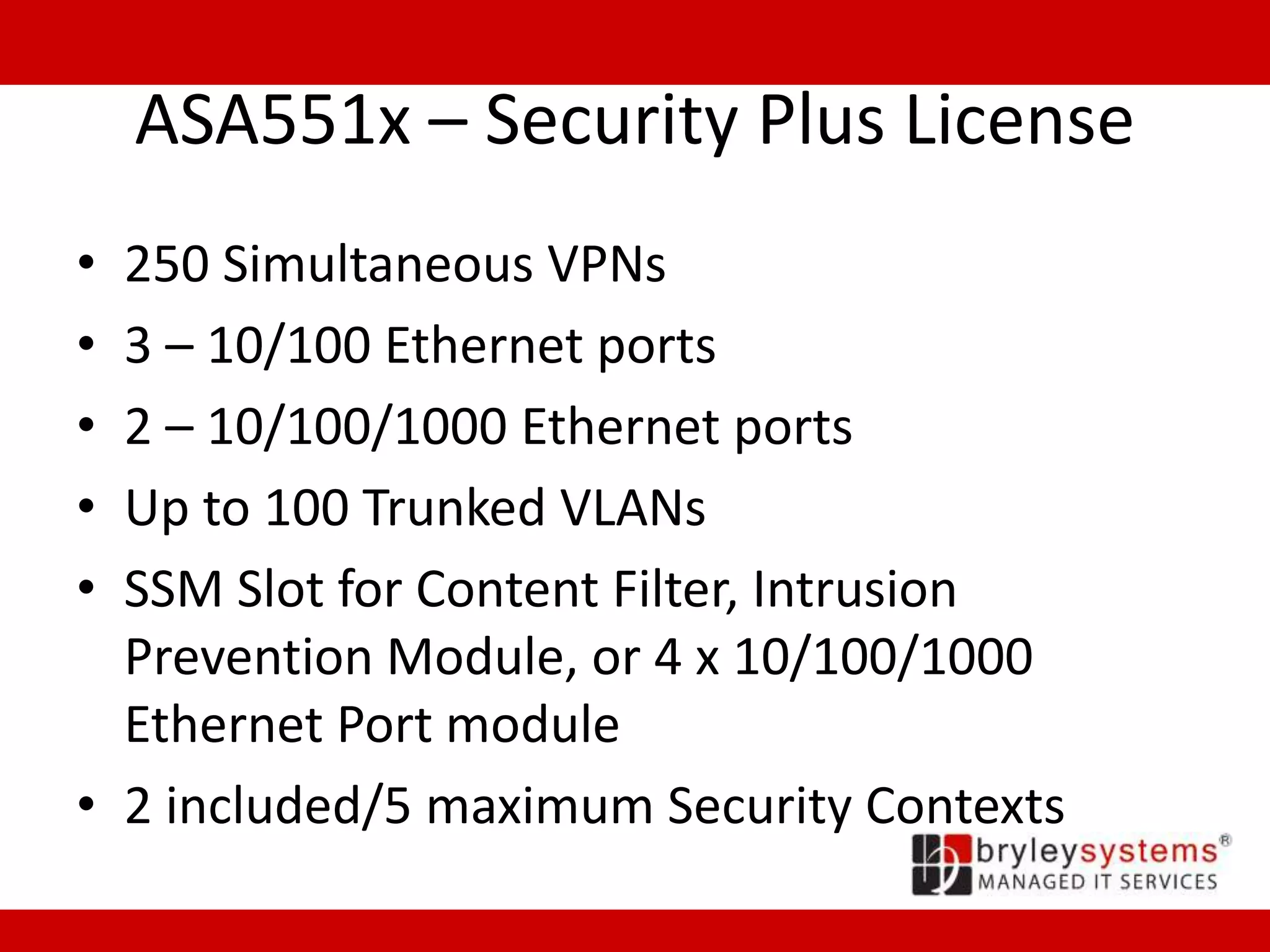
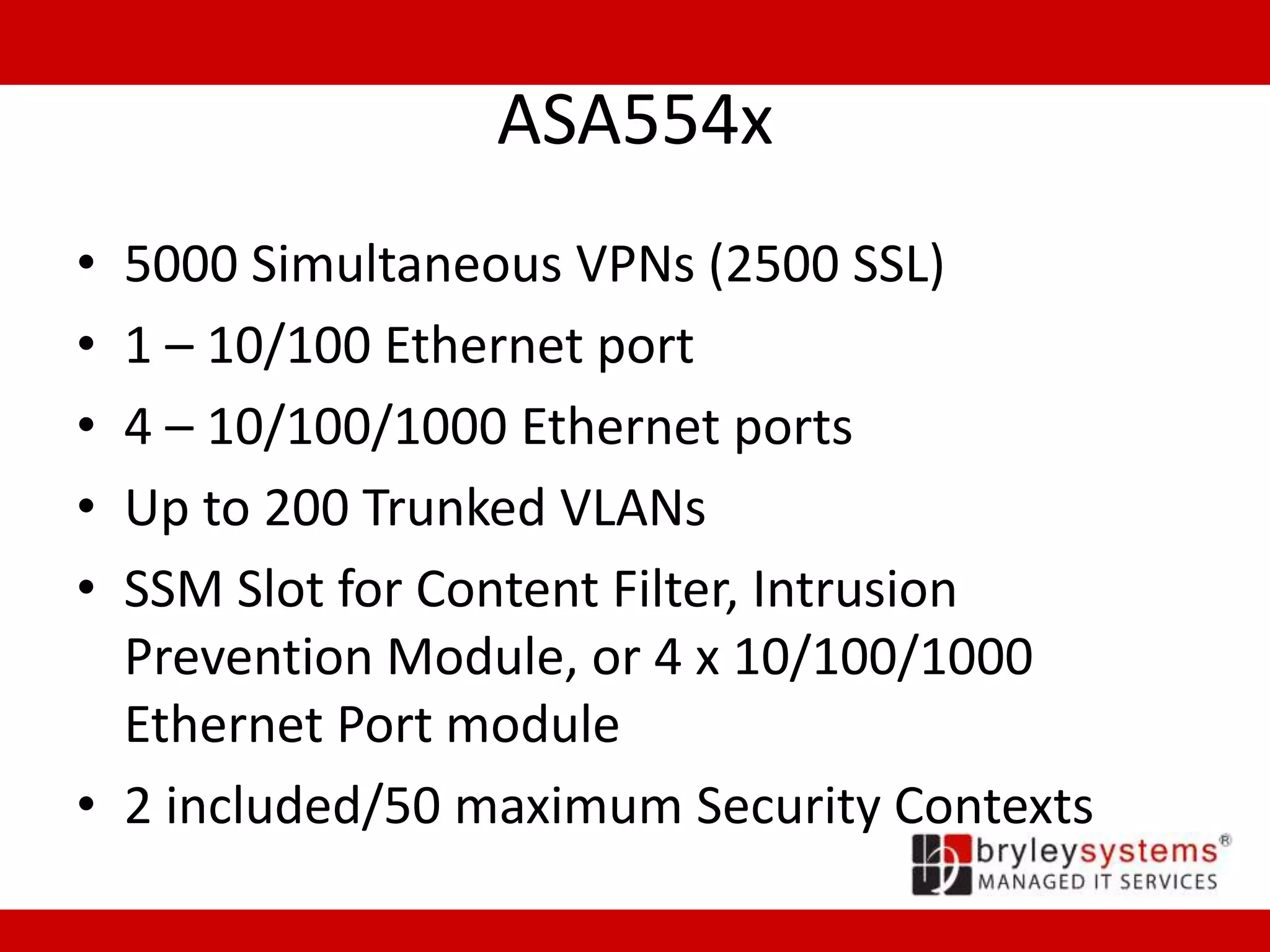
Cisco's ASA55xx series are adaptive security appliances that provide firewall, IPSec and SSL VPN capabilities. The appliances range from small office/home office models like the ASA550x to data center models like the ASA558x. All models support stateful packet inspection firewalls and VPN endpoints. Optional modules allow for intrusion prevention, content filtering, and additional network interfaces. Licenses determine the number of supported VPN connections and interfaces/VLANs.