This document discusses various security models:
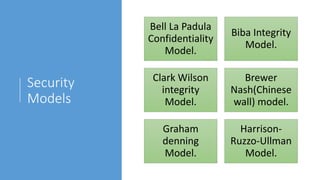
1. It describes several common security models including Bell-LaPadula (focused on confidentiality), Biba (integrity), Clark-Wilson (integrity at the transaction level), and Brewer-Nash (focused on conflict of interest).
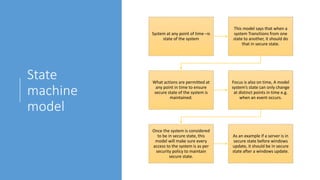
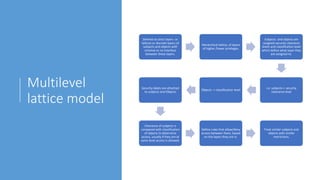
2. It explains key aspects of security models like state machine models (ensuring secure state transitions), multilevel lattice models (strict layers of subjects and objects), and non-interference models (preventing leakage of high-level information to low-level users).
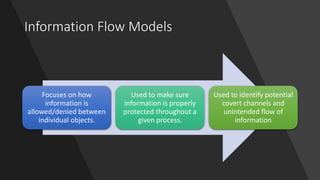
3. Matrix models and information flow models are also summarized briefly, with the latter focused on allowing and denying information flows between objects.