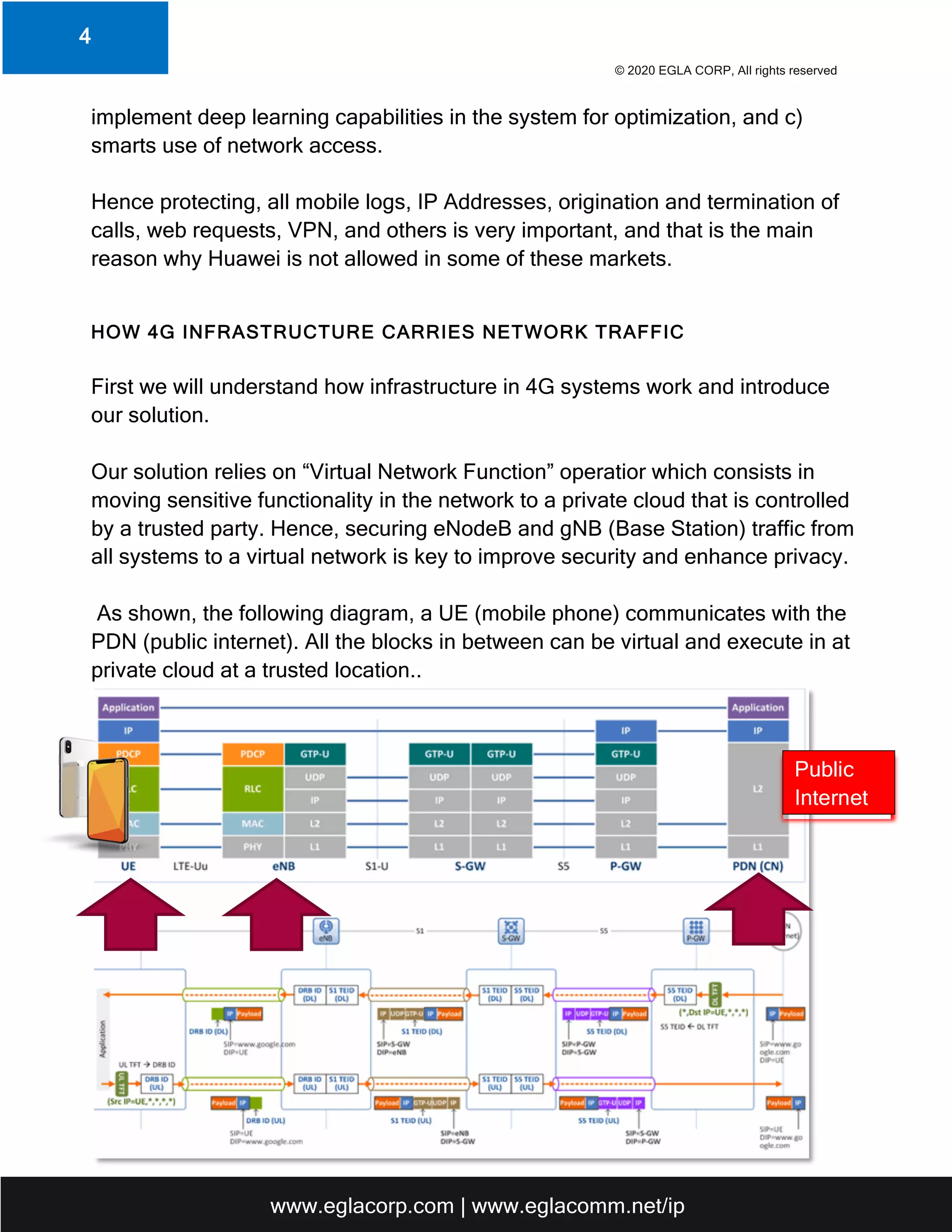
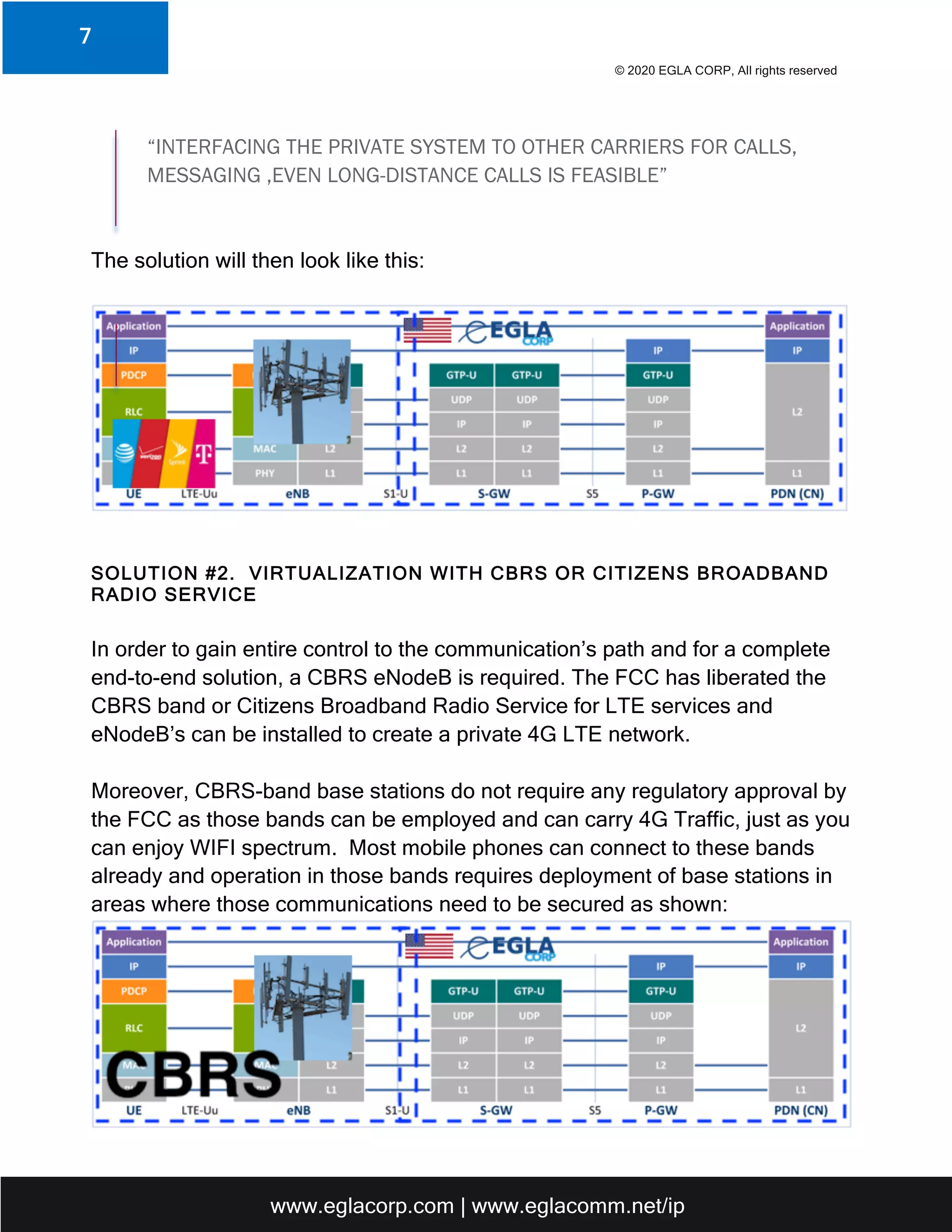
The document outlines the security challenges and solutions for 4G and 5G wireless communication systems, emphasizing the vulnerabilities associated with IP-based infrastructures, especially when control is handed over to third parties. It presents two solutions developed by Egla Corp: a virtualization solution that creates a private carrier infrastructure and another involving Citizens Broadband Radio Service (CBRS) for enhanced control and security. Additionally, the document highlights the integration of deep learning and AI technologies to bolster the security of cloud-based network communications.