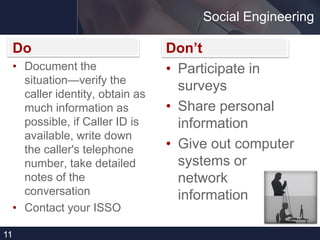
This document provides cyber security tips for protecting sensitive information and systems. It discusses defining cyber security as protecting information systems from unauthorized access. It recommends encrypting sensitive data, only storing it on accredited systems, and properly disposing of papers with personal information. Specific tips include not storing personally identifiable information (PII) on unencrypted devices; removing smart cards when leaving computers; using strong, unique passwords; and reporting suspicious activity. The document cautions against social engineering and sharing work information outside the office. It advises maintaining control of mobile devices and reporting unusual computer problems.