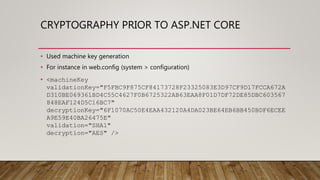
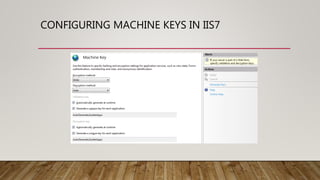
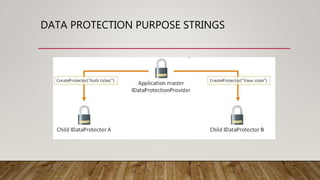
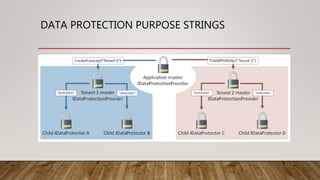
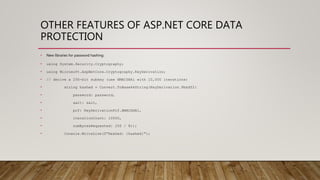
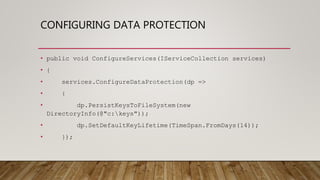
This document summarizes securing an ASP.NET Core web application with data protection. It begins with an overview of encryption in ASP.NET prior to Core and introduces the new Data Protector framework. Through demos, it shows how to build an MVC app, encrypt data using the framework, and deploy the application to Azure with an SSL certificate from Let's Encrypt. It discusses key features of the framework like key management, lifetime, and algorithms. The document provides guidance on configuration and deployment considerations for data protection in ASP.NET Core.