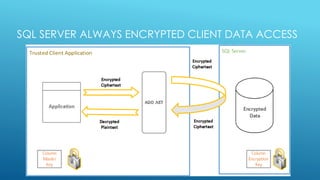
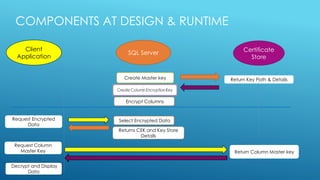
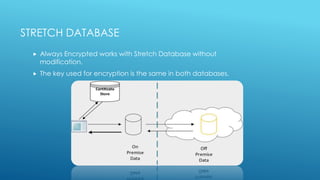
The document discusses the SQL Server 2016 feature 'Always Encrypted' which protects sensitive data by storing it as encrypted cipher text in the database, allowing client applications to access it securely without revealing the master key. It covers encryption methods, key management, client application requirements, and implementation considerations to mitigate data breach risks. Emphasizing a defense in depth approach, it positions encryption as crucial for securing data at rest, in transit, and in memory.