Embed presentation
Download as PDF, PPTX




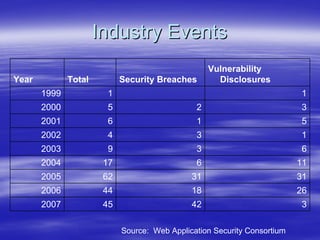
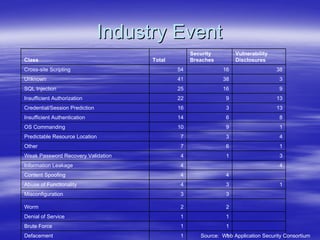


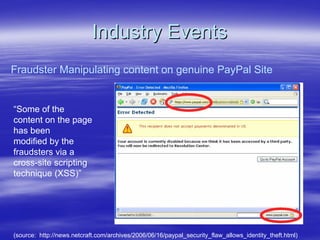
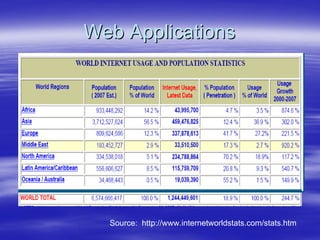




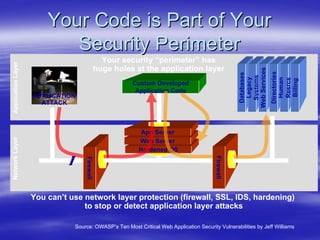
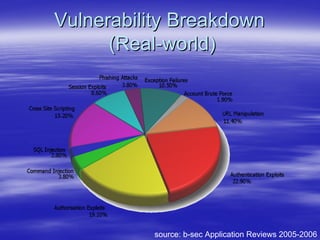





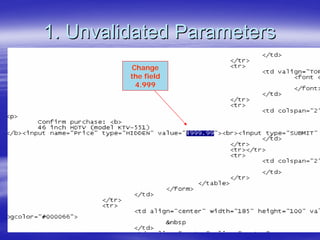
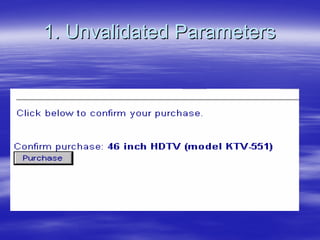
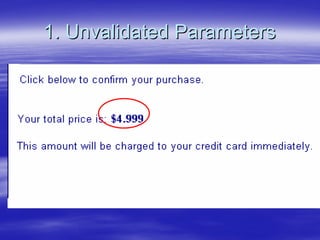







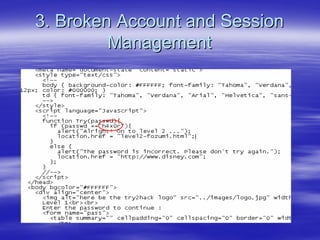













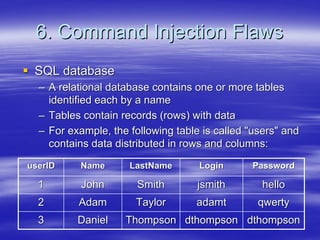
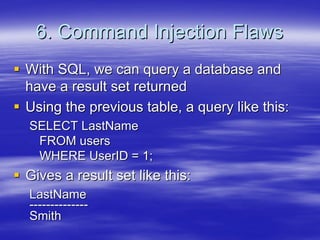



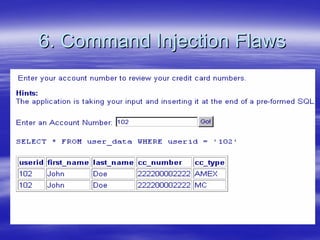
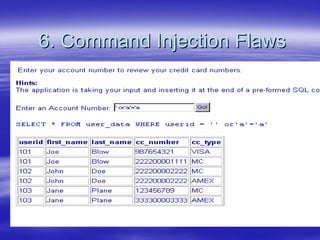


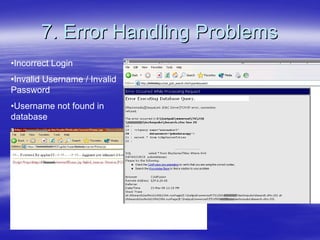









Securing Web Applications provides guidance on integrating the OWASP Top 10 framework to mitigate common web application security vulnerabilities. It defines an application as user software made up of configuration files, programs, and data files that run on an operating system. Applications use the operating system for functionality and security, while also containing their own security features beyond the operating system. The document aims to teach best practices for securing web applications against vulnerabilities.































































