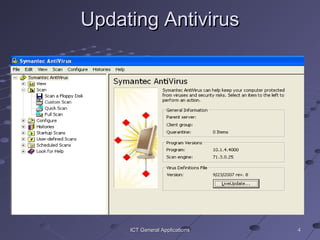
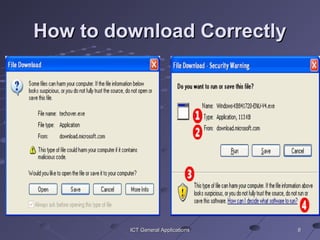
The document discusses good internet habits and how to avoid malware and viruses when using ICT applications. It notes that viruses can be obtained by visiting compromised websites, downloading unknown files from the internet, opening suspicious emails or attachments, and using untrusted external storage devices. It provides tips for reducing risks like using antivirus software, only downloading from trusted sources, using firewalls and strong passwords. The document outlines different types of storage media and characteristics of malware like replicating (worms), using system resources, transmitting across networks, and fulfilling the designer's intentions like deletion or corruption. It emphasizes keeping antivirus software current to protect devices and networks from various cyber threats.