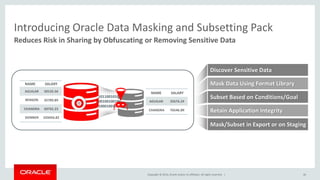
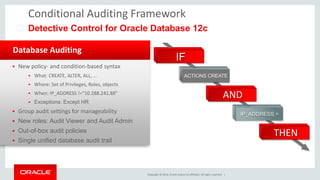
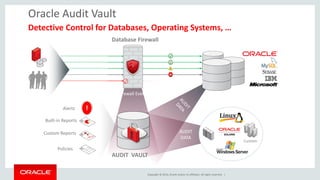
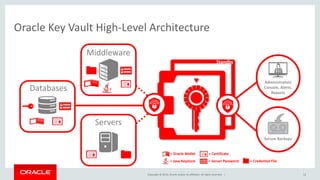
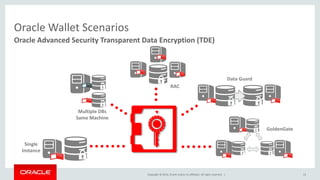
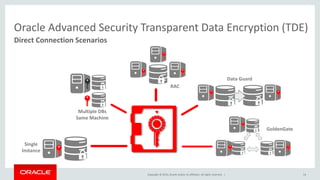
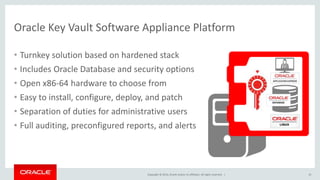
The document discusses security features in Oracle Database 12c including Transparent Data Encryption (TDE), Privilege Analysis, Database Vault, Database Firewall, Data Redaction, Data Masking, and Audit Vault. It provides an overview of each technology and how they can be used to secure data at rest and in motion, monitor and control privileged access, and audit database activity. The document also outlines an agenda to cover these security controls in more depth.











![Copyright © 2014, Oracle and/or its affiliates. All rights reserved. |
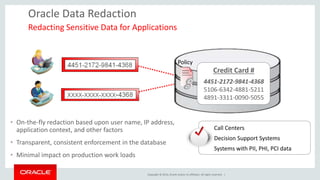
Supported Transformations
Original Redacted
Full
Redaction
05/24/75 01/01/01
11 Rock Bluff Dr. XXXXXXX
Partial
Redaction
068-35-2299 ***-**-2299
D1L86YZV8K D1******8K
RegExp
Redaction jim.lee@acme.com [redacted]@acme.com
94025-2450 94025-[hidden]
Random
Redaction
4022-5231-5531-9855 4943-6344-0547-0110
09/30/73 11/14/85](https://image.slidesharecdn.com/con7485securingdatainoracledatabase12cbulgaria-181002042937/85/Securing-data-in-Oracle-Database-12c-2015-25-320.jpg)