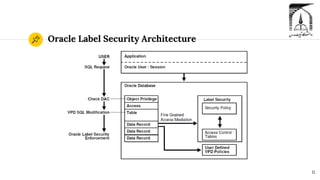
The document discusses security in Oracle databases. It covers several topics: Oracle Label Security which allows row-level access control based on user privileges; data masking and subsetting tools for replacing sensitive data; auditing of database activities for accountability, investigation, and problem detection; and encryption technologies like Transparent Data Encryption and Key Vault for securing data. Presenters Zahra Taghipoor kolaei and Seyyedeh Fatemeh Mousazadeh Mousavi led the discussion under Professor Dr. Sadegh Dorri Nogoorani during a winter 2022 class.