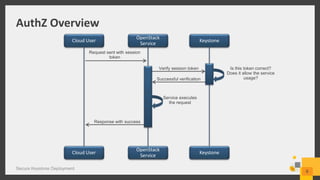
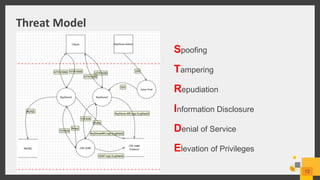
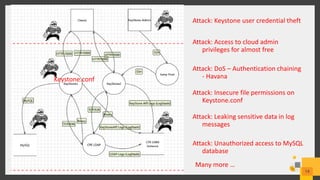
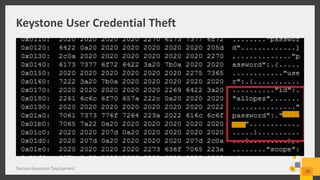
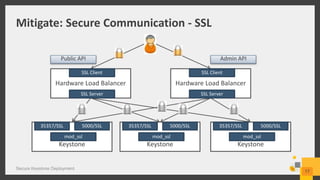
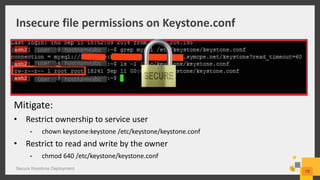
The document discusses best practices for deploying a secure Keystone in OpenStack, highlighting the critical nature of Keystone security in managing access to cloud services. It covers risks such as credential theft and insecure file permissions, along with mitigation strategies, including secure communication, restricting file access, and managing admin privileges. Key vulnerabilities identified include denial of service attacks and leaking sensitive information, which can be addressed through configuration changes and upgrades.









![Mitigate: Disable Service Token
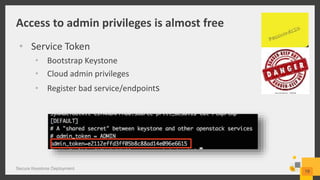
• Comment out admin_token from /etc/keystone/keystone.conf:
admin_token=e2112effd3ff05b8c88ad14e096e6615
• Remove admin token auth middleware from
/etc/keystone/keystone-paste.ini:
[filter:admin_token_auth]
paste.filter_factory =
keystone.middleware:AdminTokenAuthMiddleware.factory
Secure Keystone Deployment
20](https://image.slidesharecdn.com/securekeystonedeployment-150106180605-conversion-gate02/85/Secure-Keystone-Deployment-20-320.jpg)
![Create Cloud Admin
• Leveraging Keystone Domain
• Before disabling service token:
• Create a domain “cloud_admin_domain”
• Grant “admin” role to appropriate user “Bob Smith”
• Update keystone policy.json file:
• Replace:
"cloud_admin": [["rule:admin_required", "domain_id:admin_domain_id"]],
• With:
"cloud_admin”: [["rule:admin_required”,"domain_id:<cloud_admin_domain_id>"]],
Secure Keystone Deployment
22](https://image.slidesharecdn.com/securekeystonedeployment-150106180605-conversion-gate02/85/Secure-Keystone-Deployment-22-320.jpg)
![Leaking Sensitive Information in Log Messages
• Debug mode include plaintext request logging
• Passwords
• Tokens
• Mitigate:
• Disable debug mode in keystone.conf with:
• With debug mode ON, upgrade keystone client:
• python-keystoneclient >= 0.10.1 (OSSN-0024)
Secure Keystone Deployment
23
[DEFAULT]
debug=False](https://image.slidesharecdn.com/securekeystonedeployment-150106180605-conversion-gate02/85/Secure-Keystone-Deployment-23-320.jpg)
![Leaking Sensitive Information in Log Messages
Identity API V2 - INFO level logs contains auth tokens (OSSN-0023)
Mitigate:
• Set the log level to WARN in logging.conf:
Secure Keystone Deployment
24
[handler_file]
class = FileHandler
Level = WARN](https://image.slidesharecdn.com/securekeystonedeployment-150106180605-conversion-gate02/85/Secure-Keystone-Deployment-24-320.jpg)