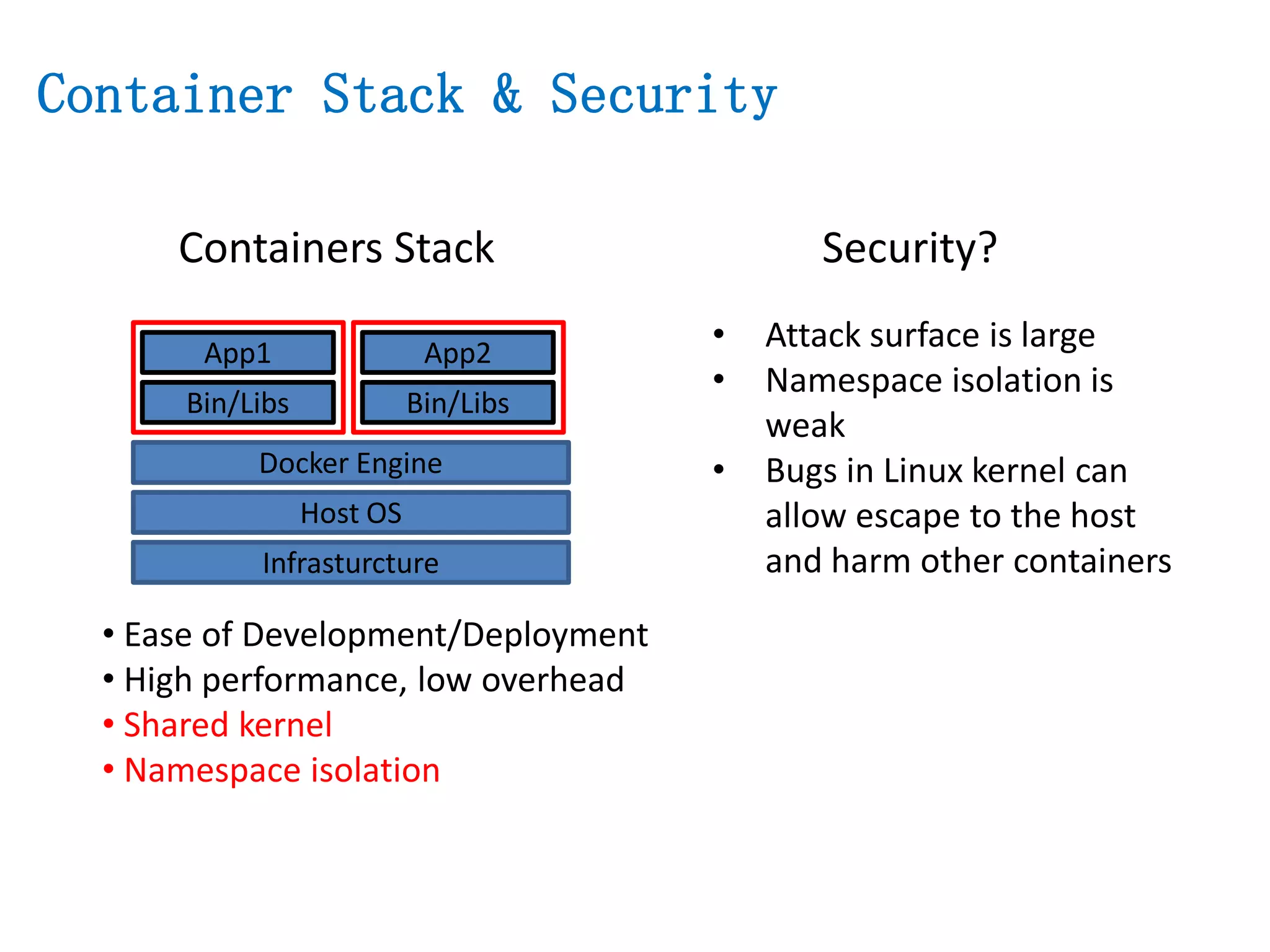
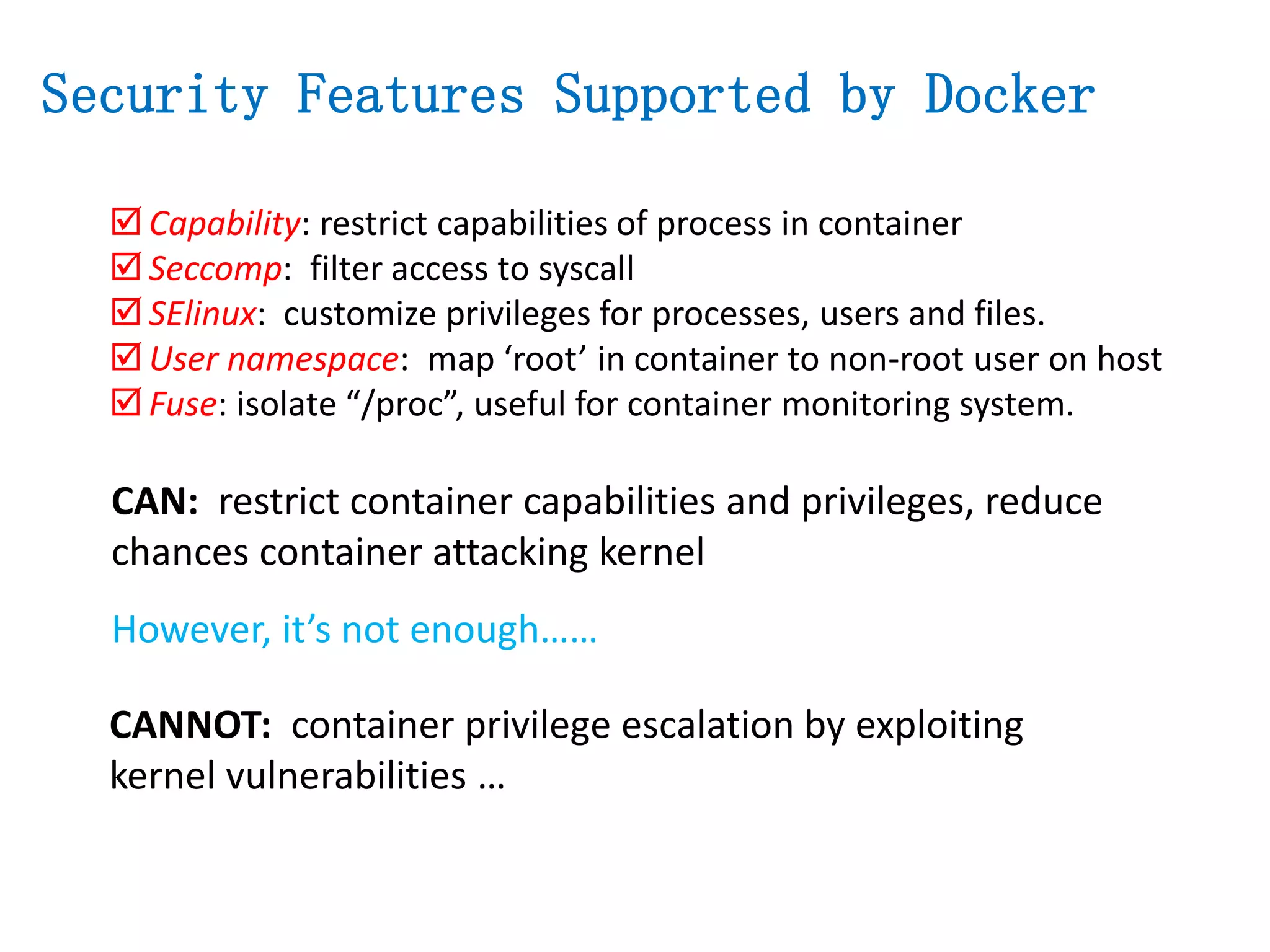
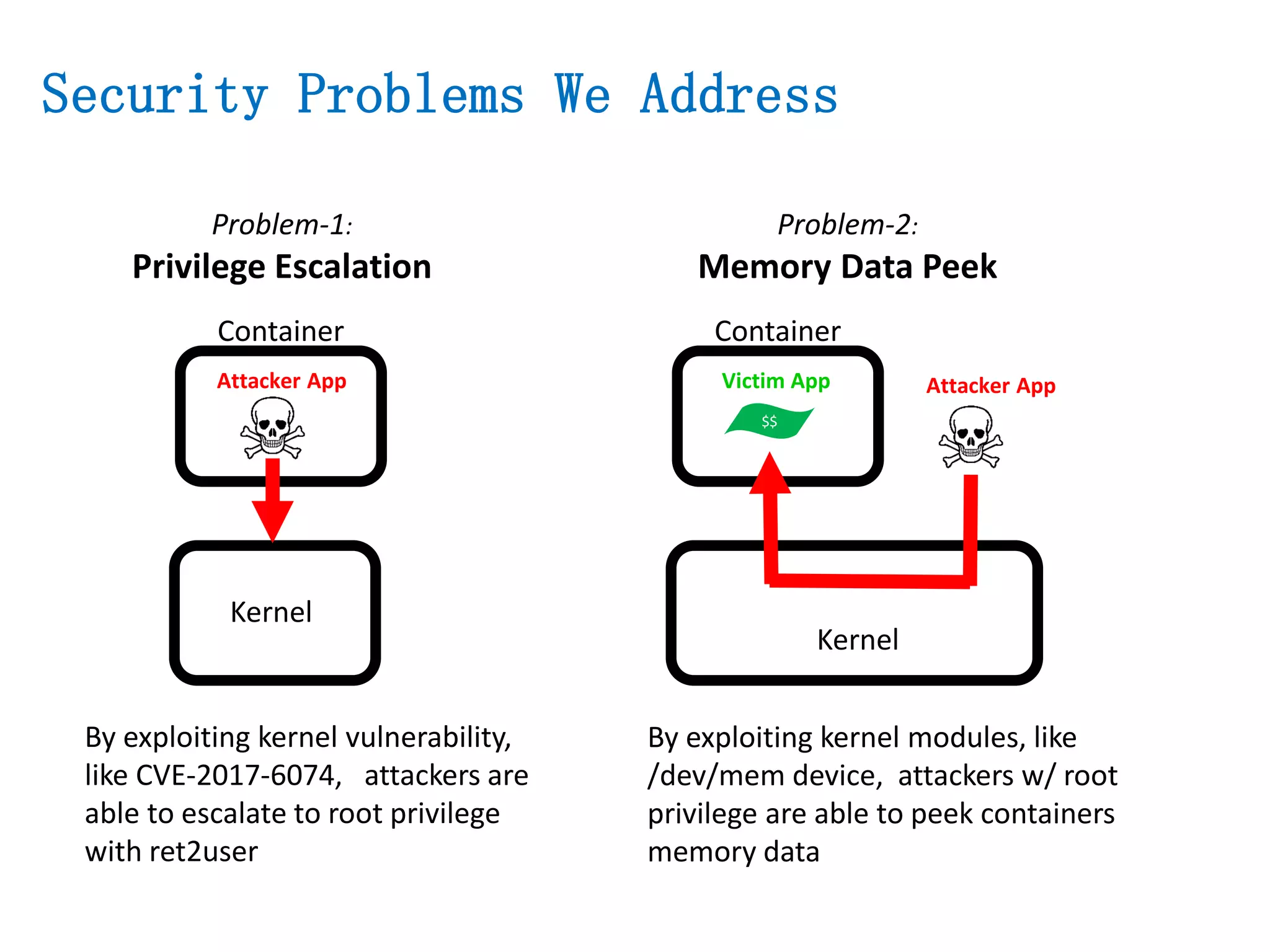
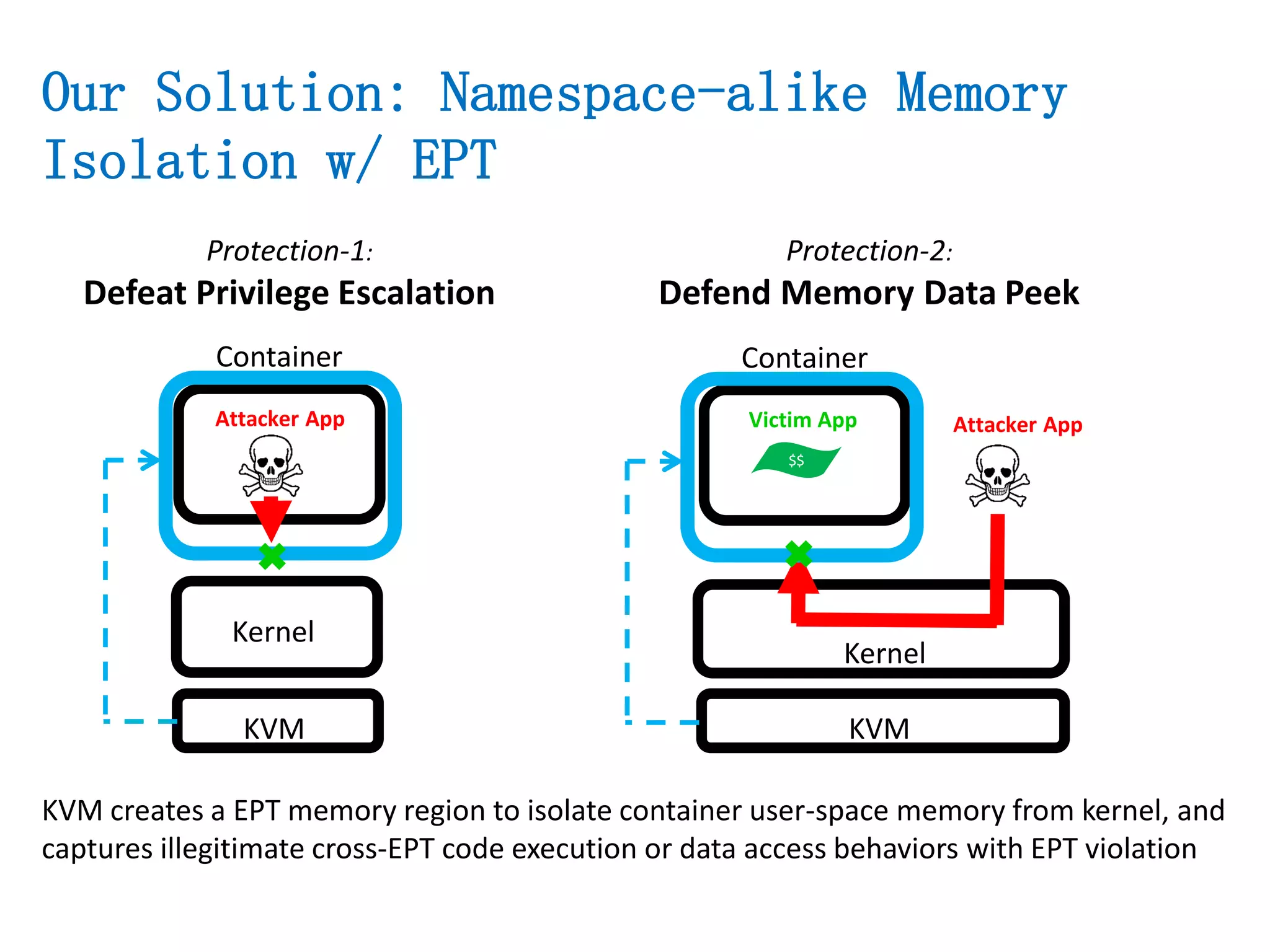
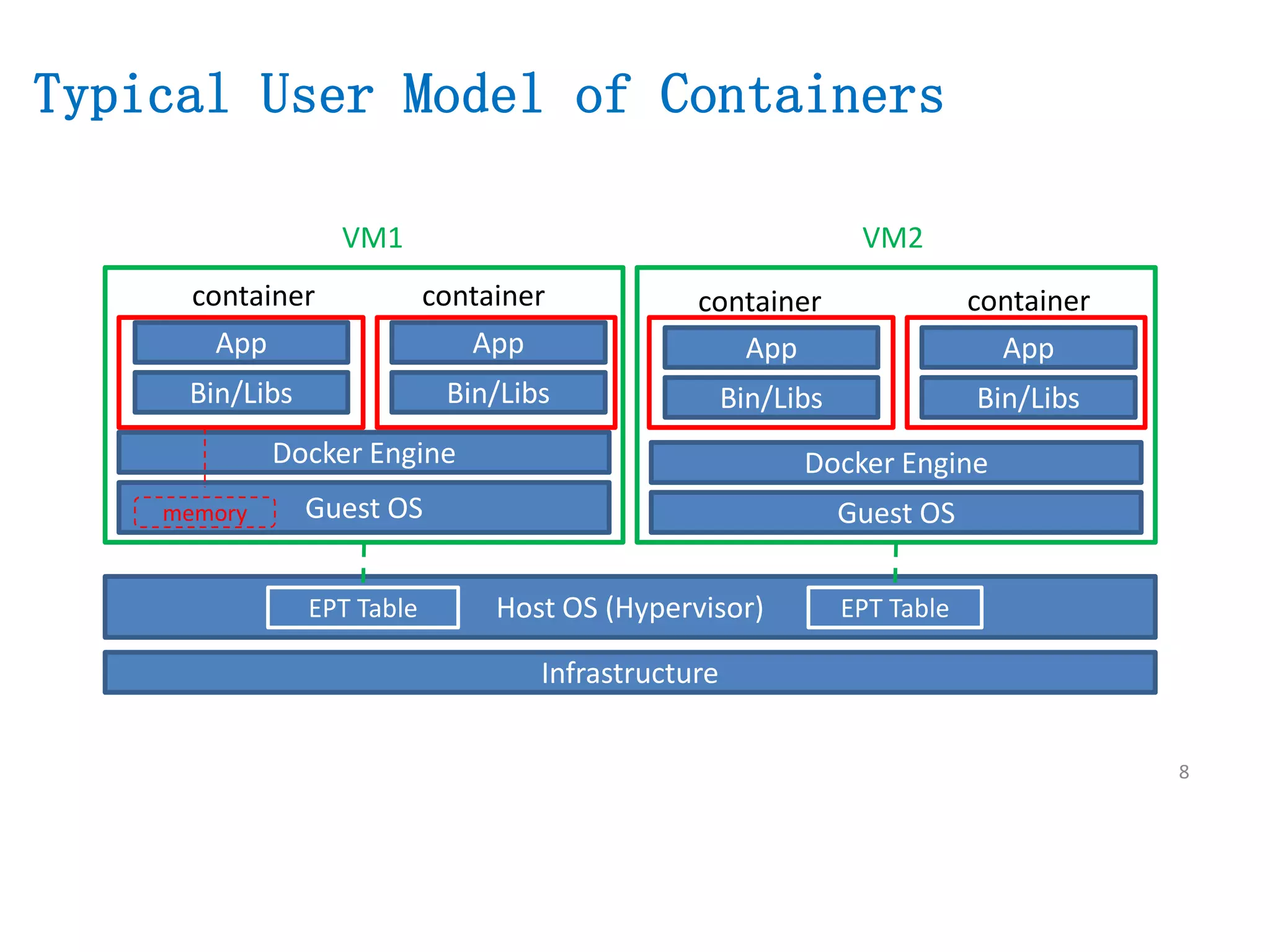
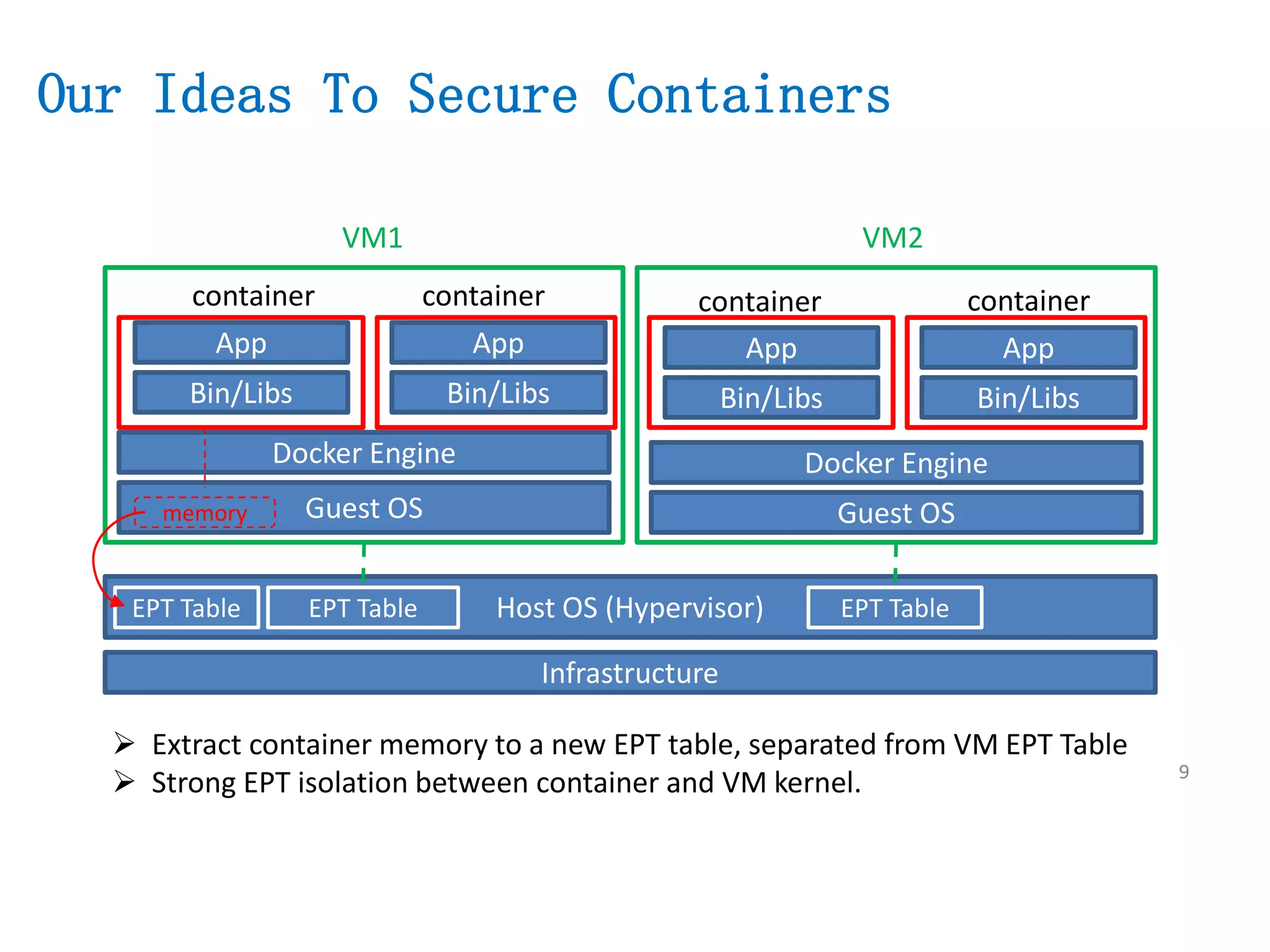
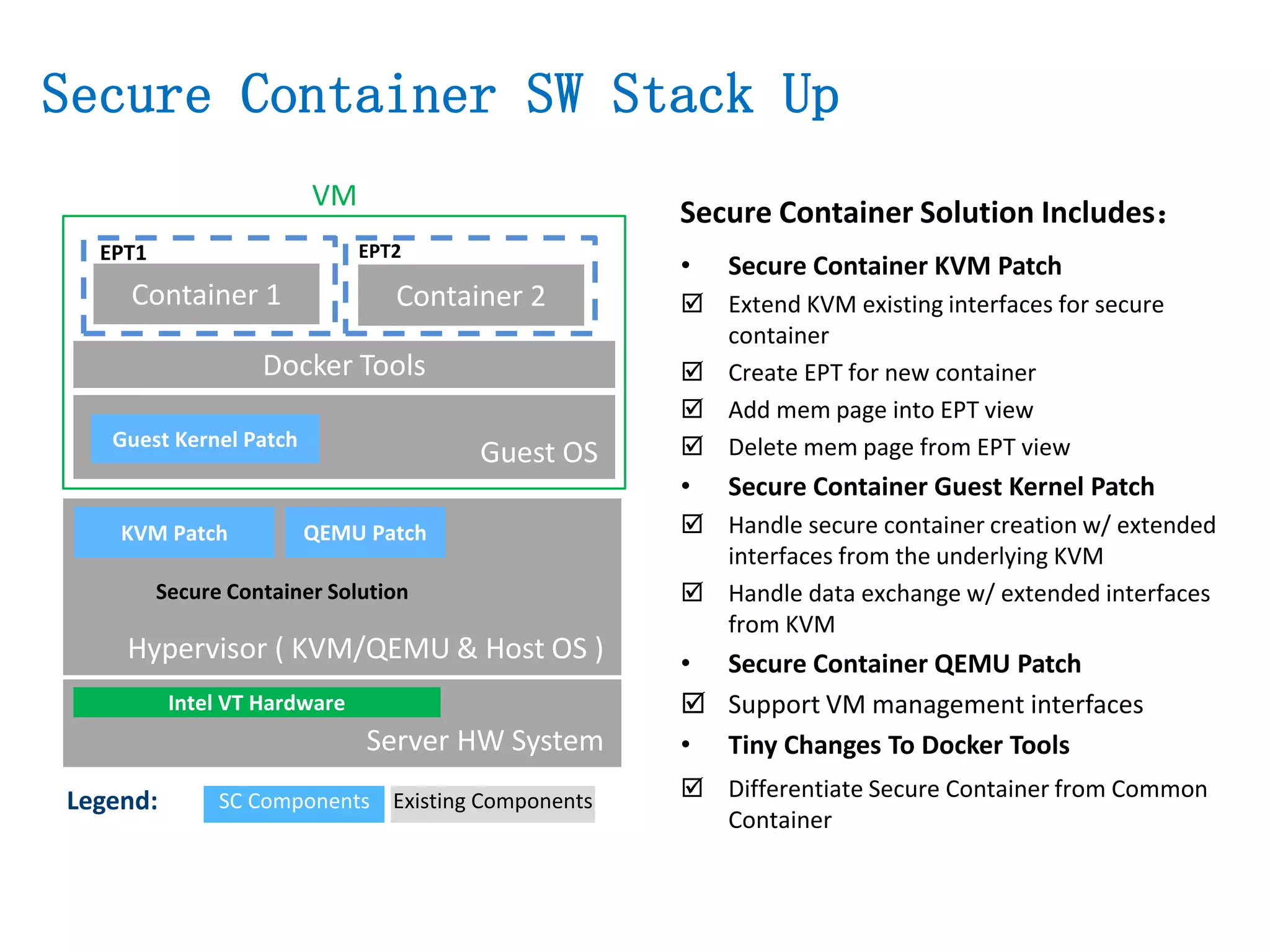
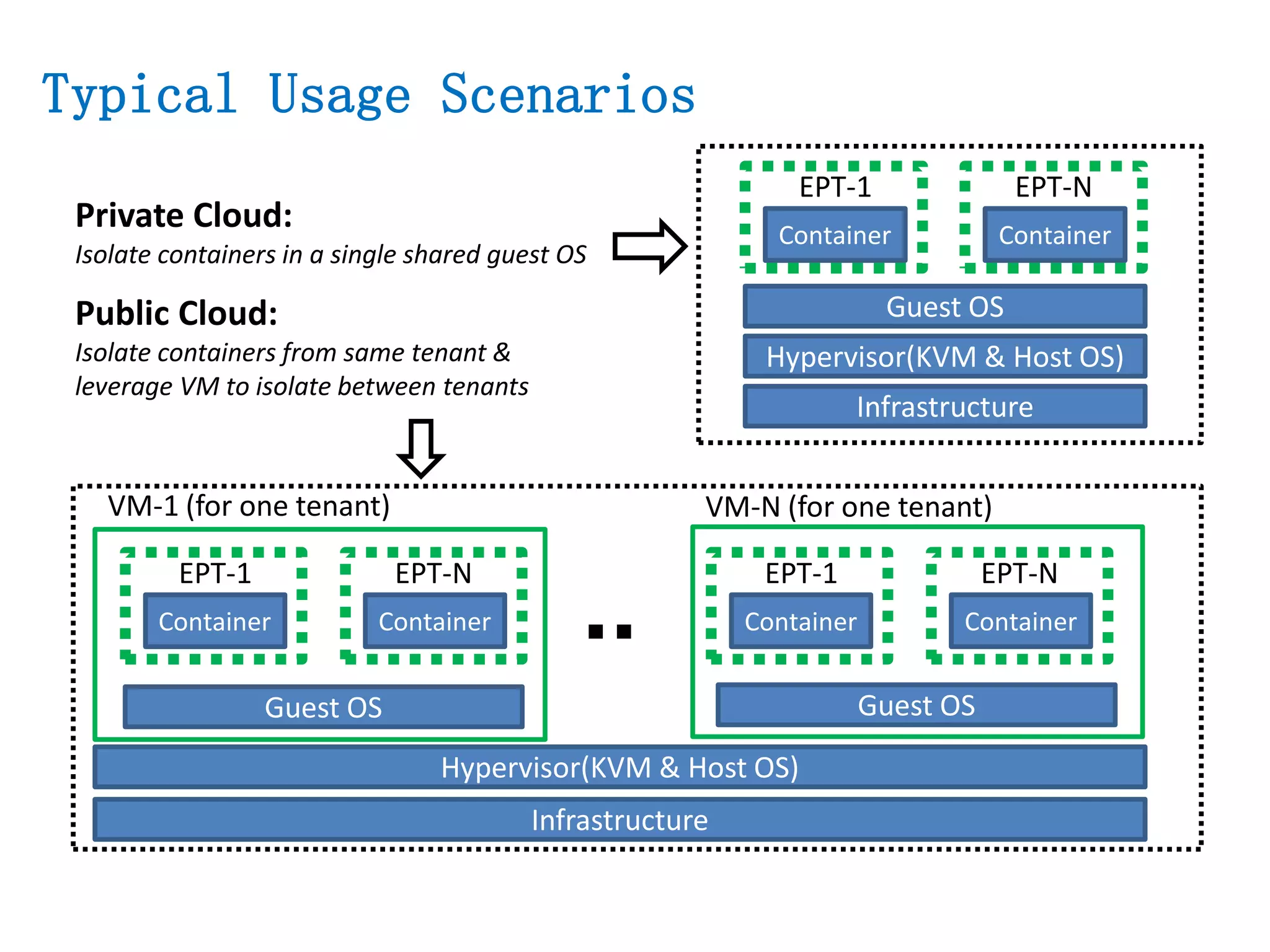
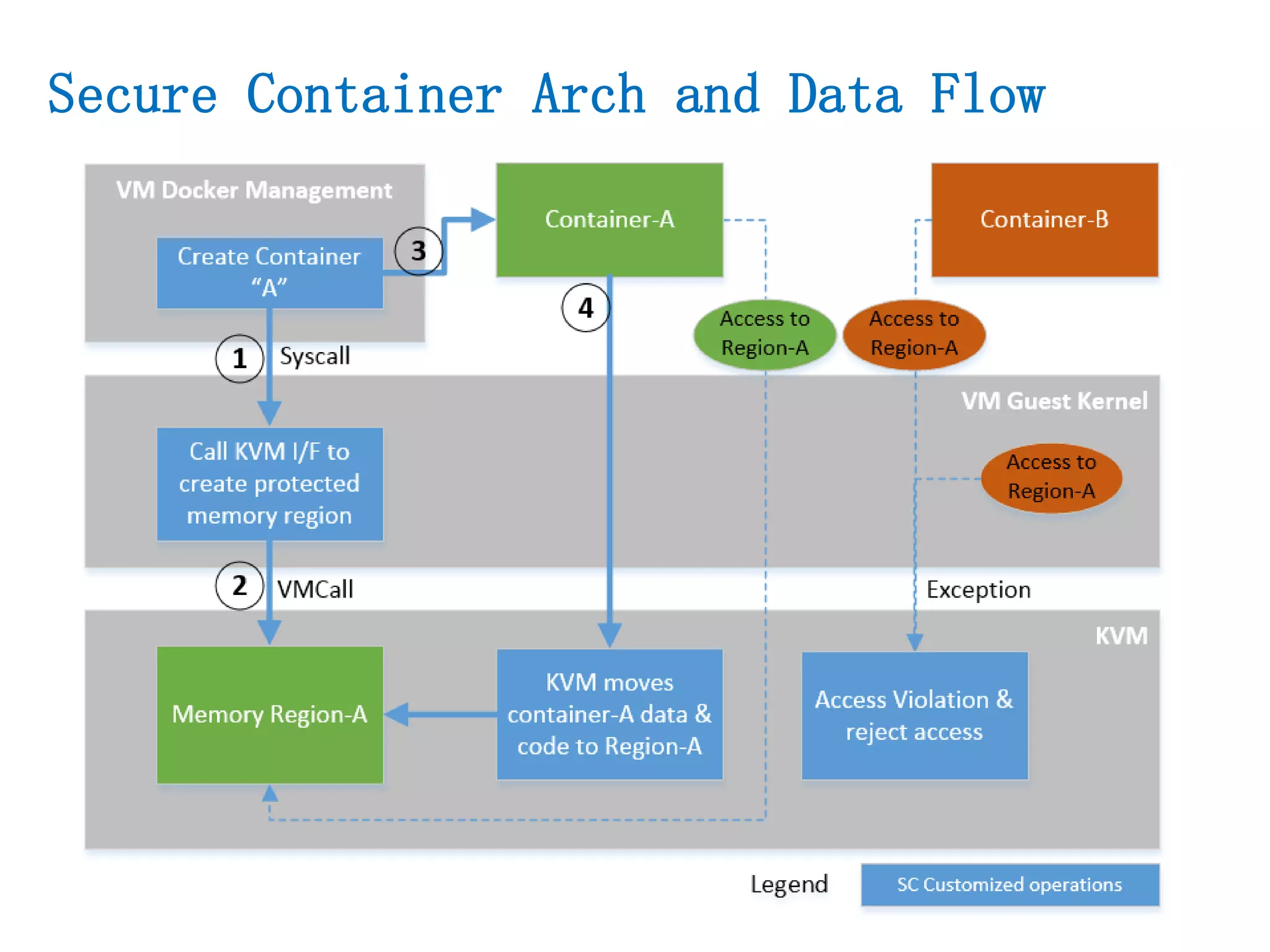
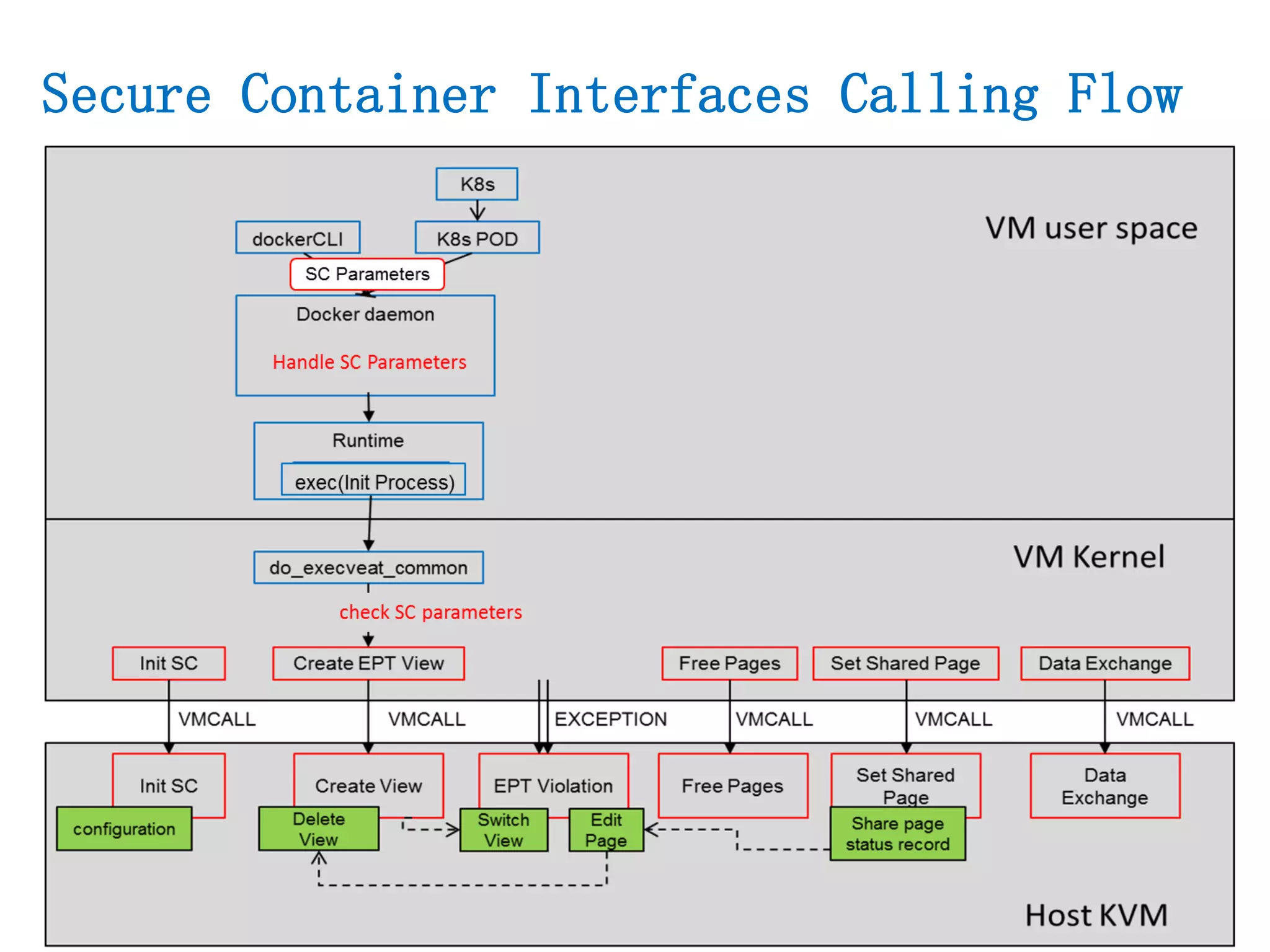
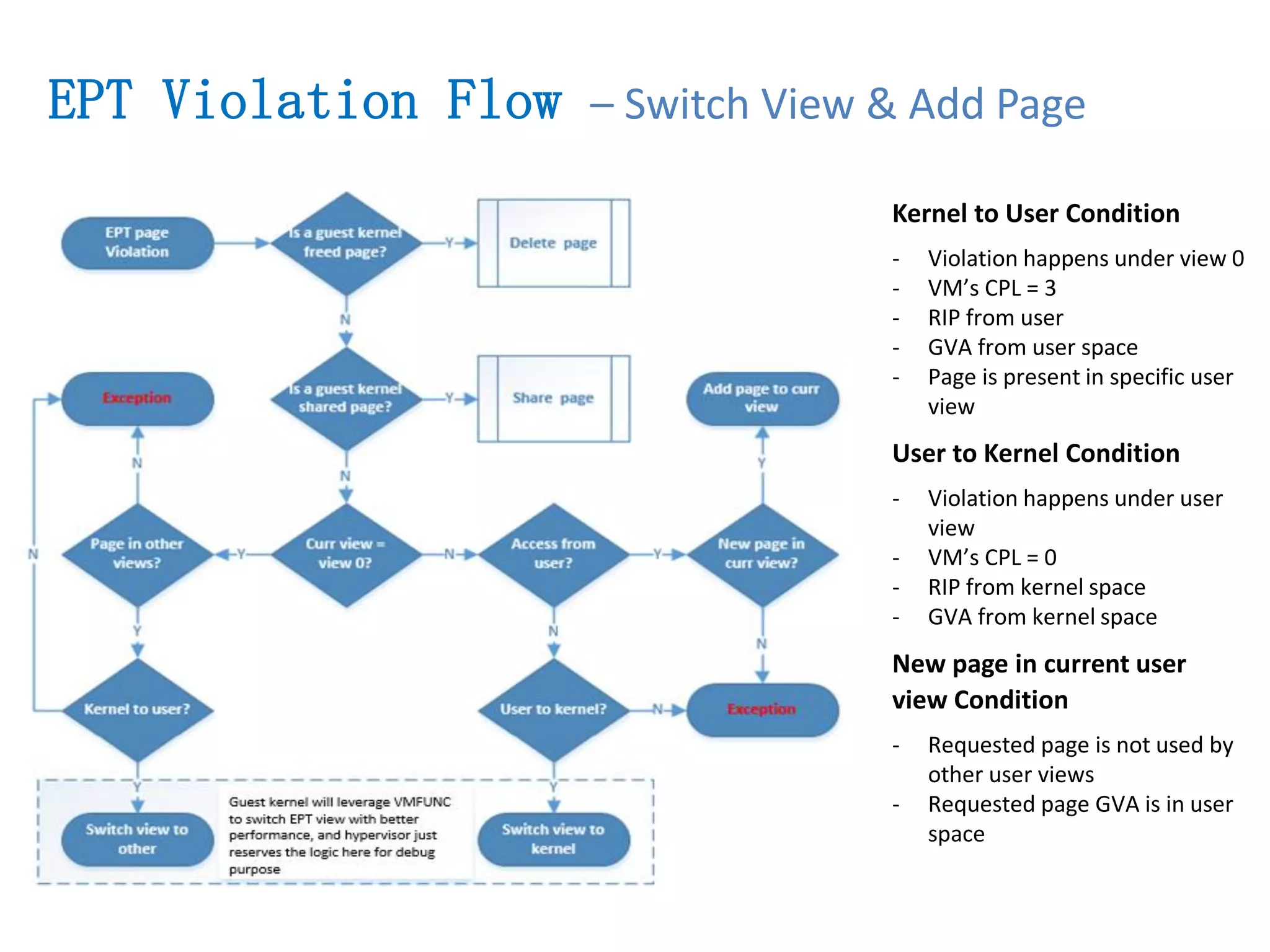
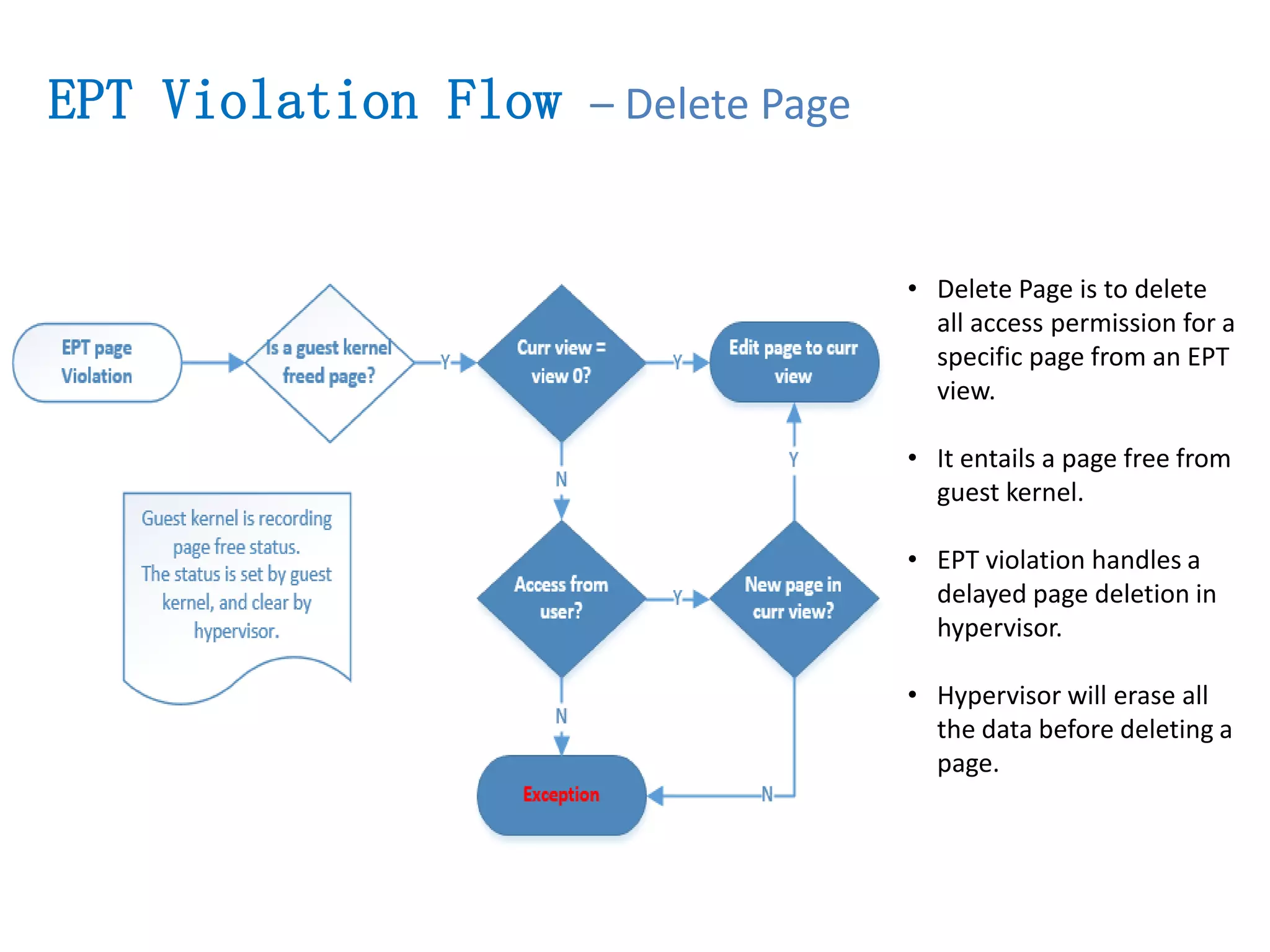
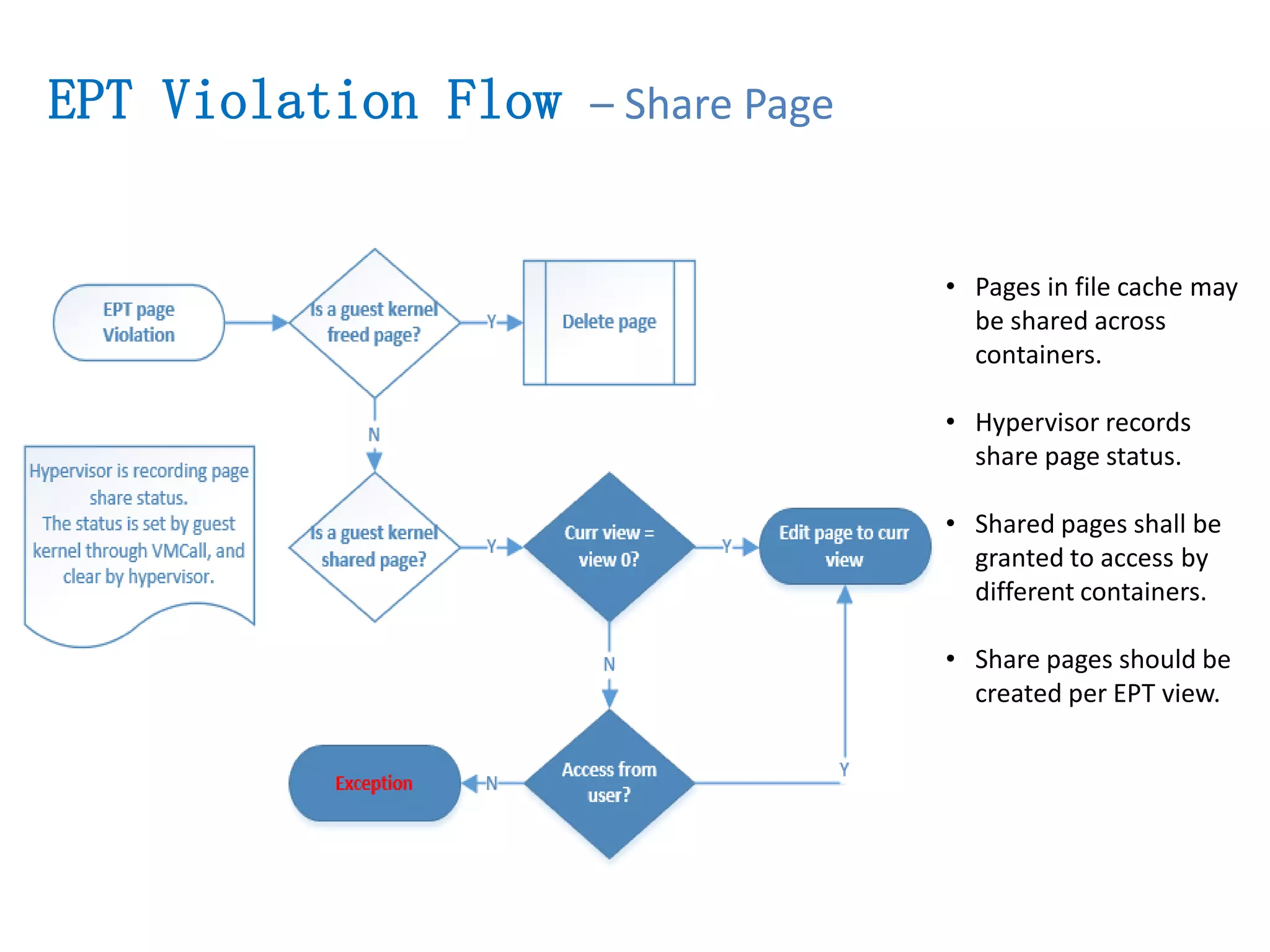
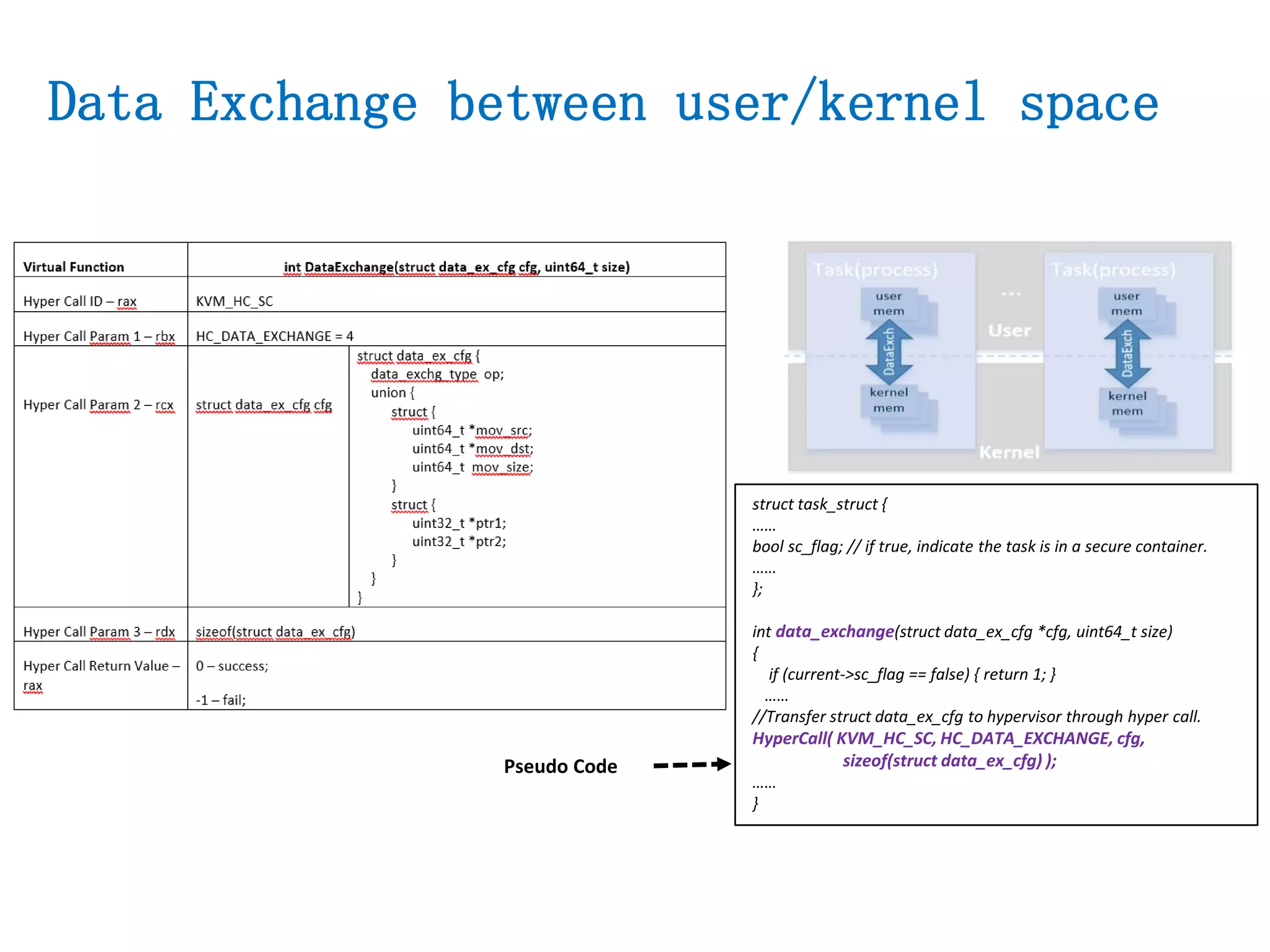
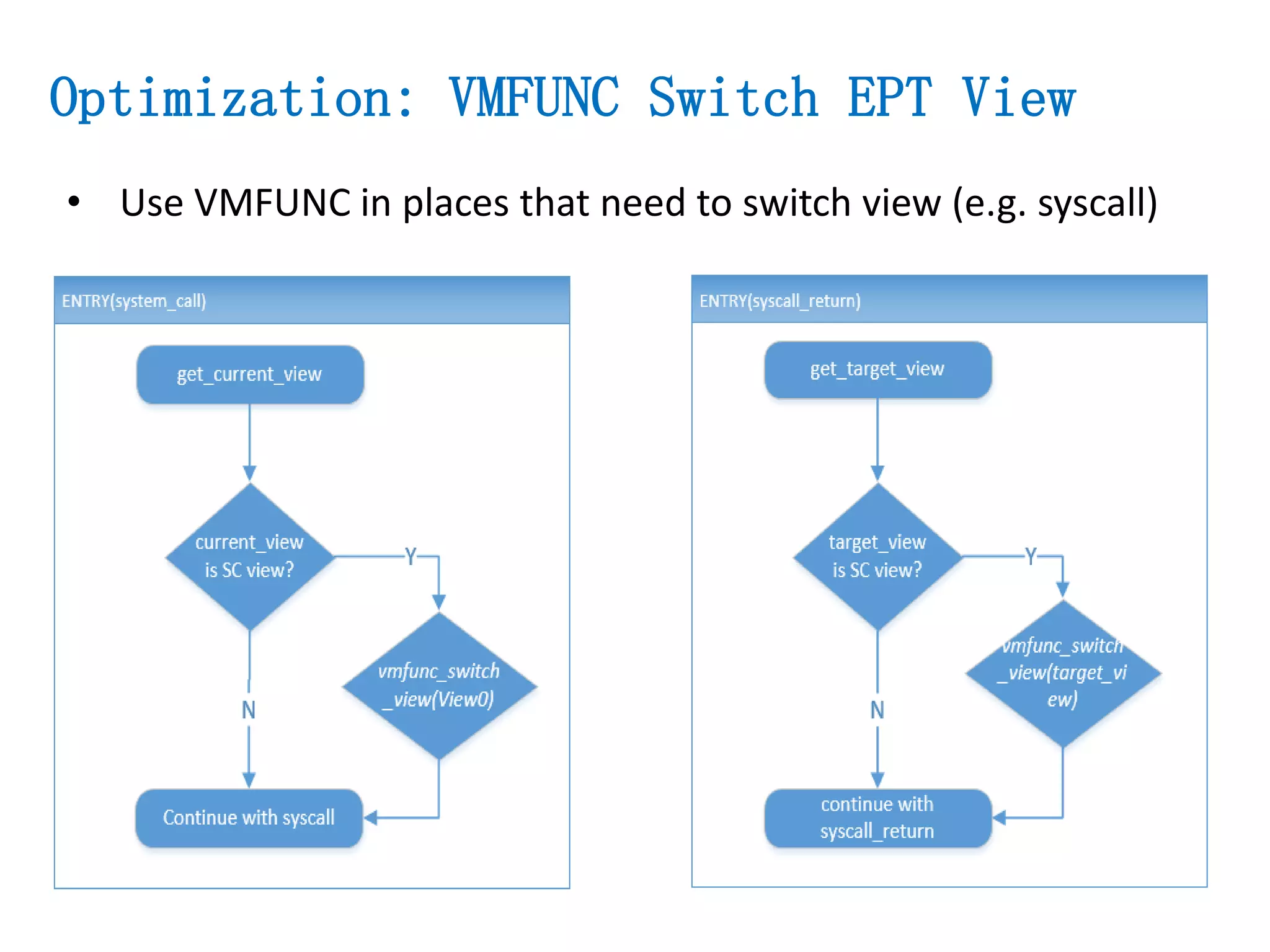
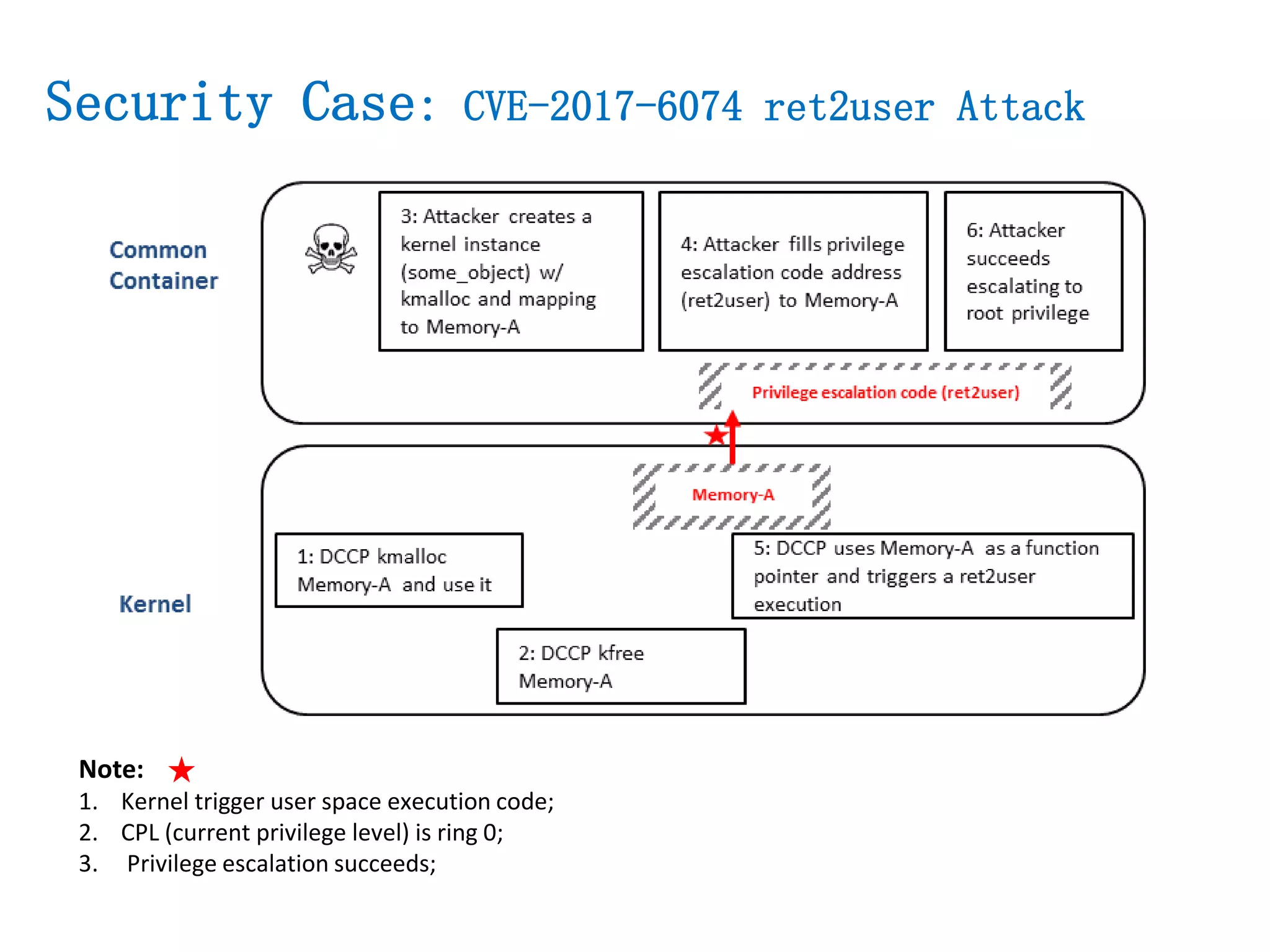
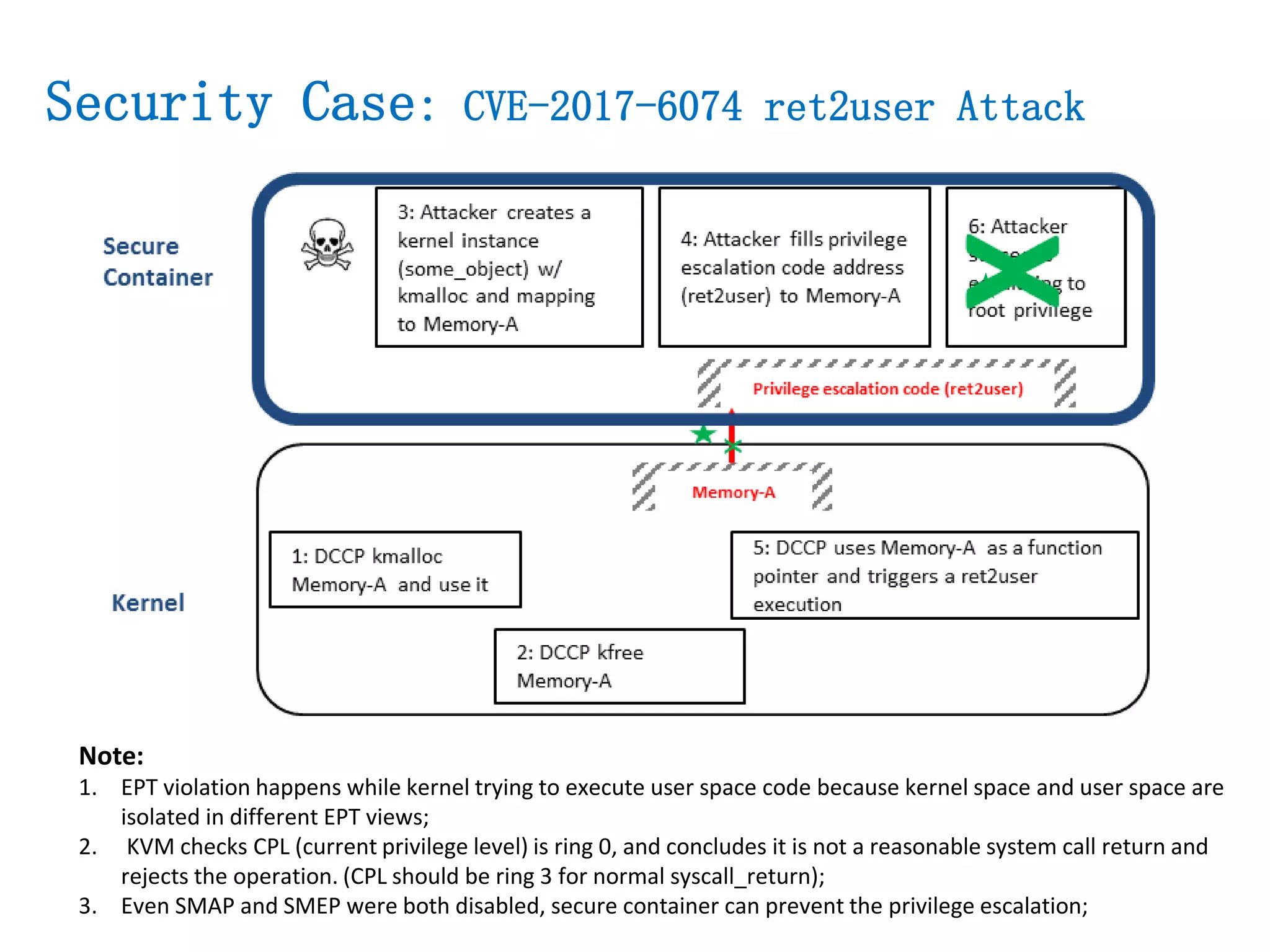
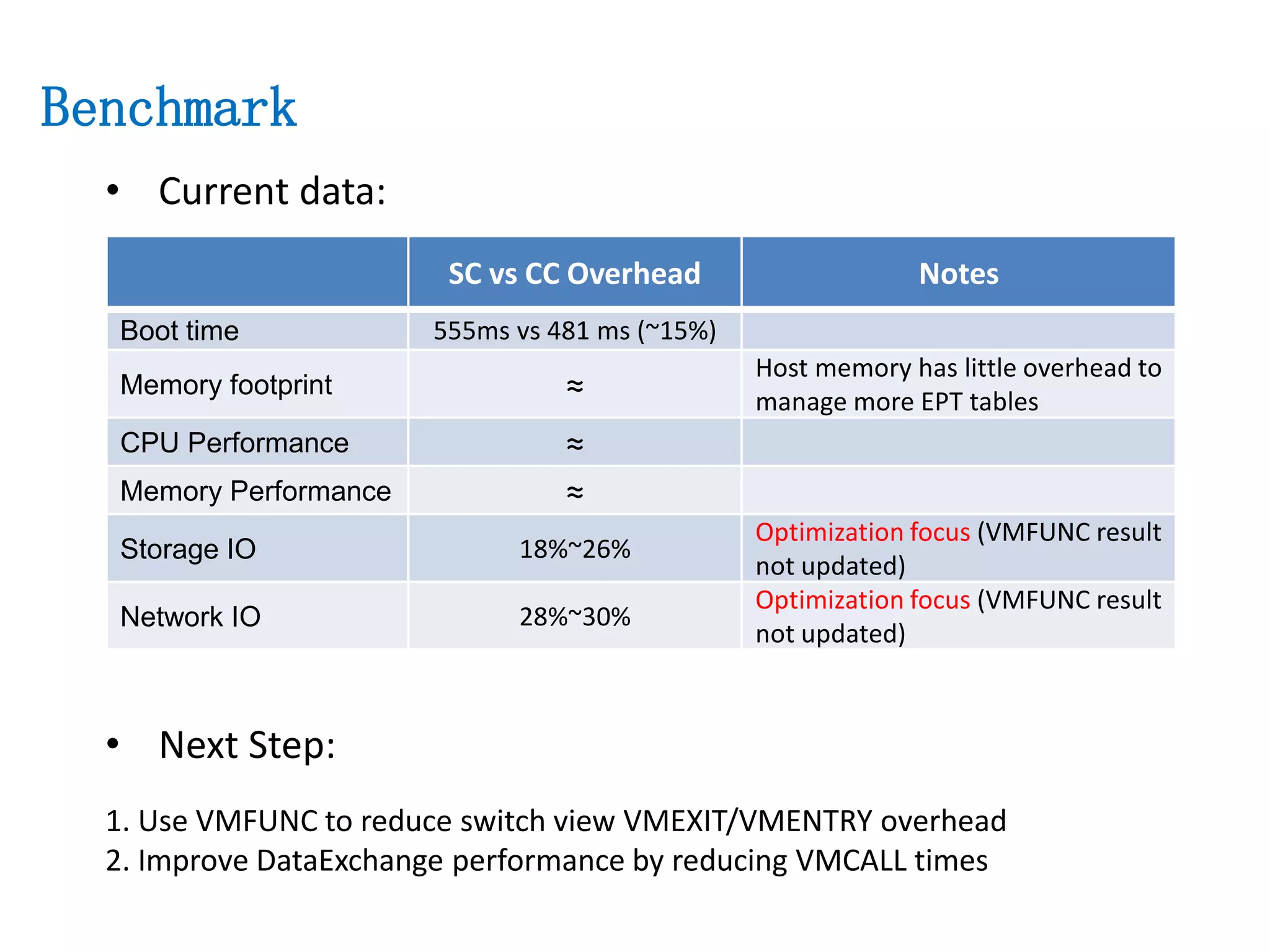
The document presents a secure container solution utilizing Extended Page Table (EPT) isolation to enhance security against kernel vulnerabilities in container environments. It addresses issues such as privilege escalation and memory data leakage through a design that creates separate EPT tables for each container, enhancing isolation between user and kernel spaces. The solution incorporates patches for KVM and QEMU, along with minor modifications to Docker tooling, and includes benchmark results demonstrating performance impacts of the secure container approach.