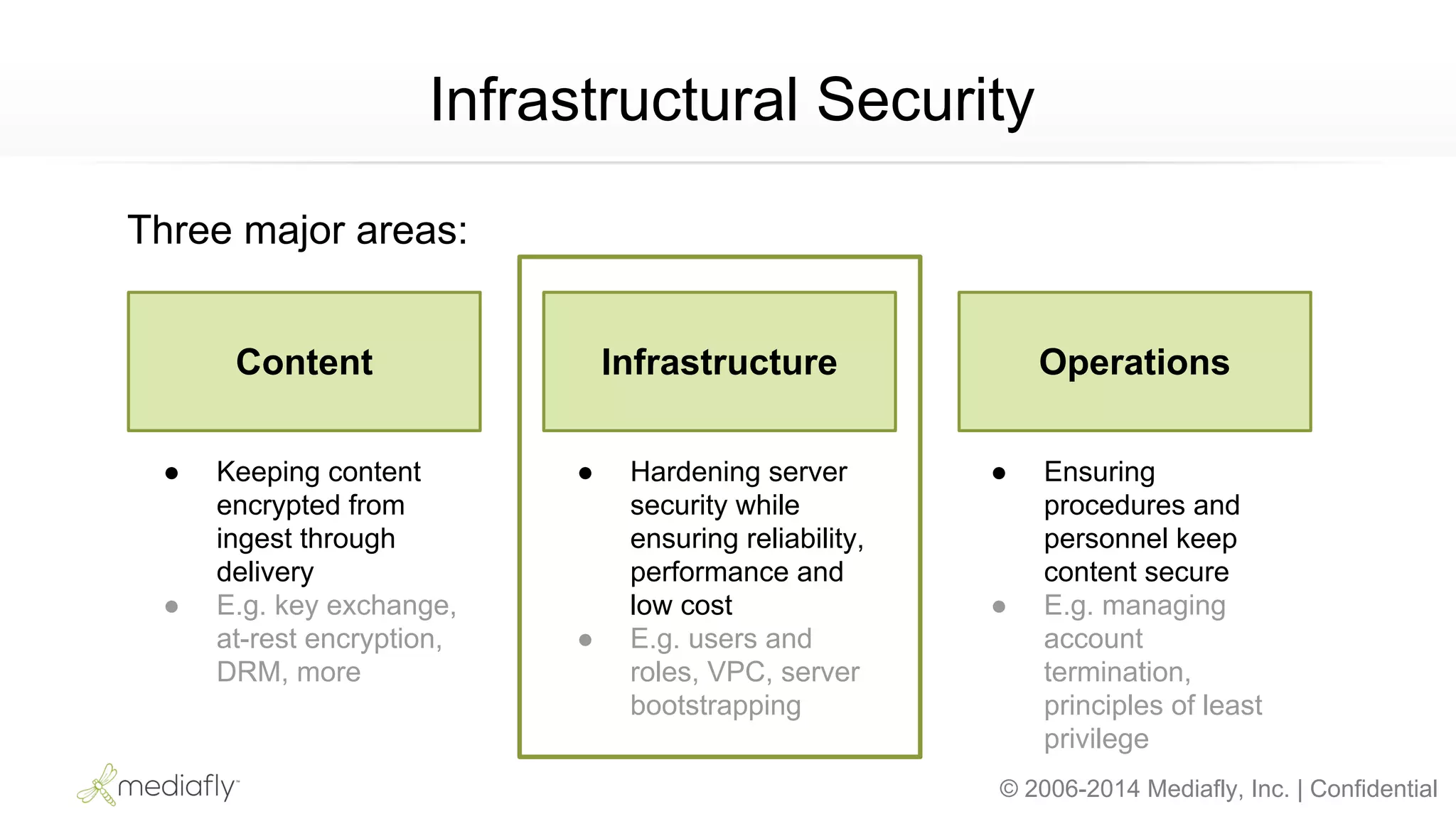
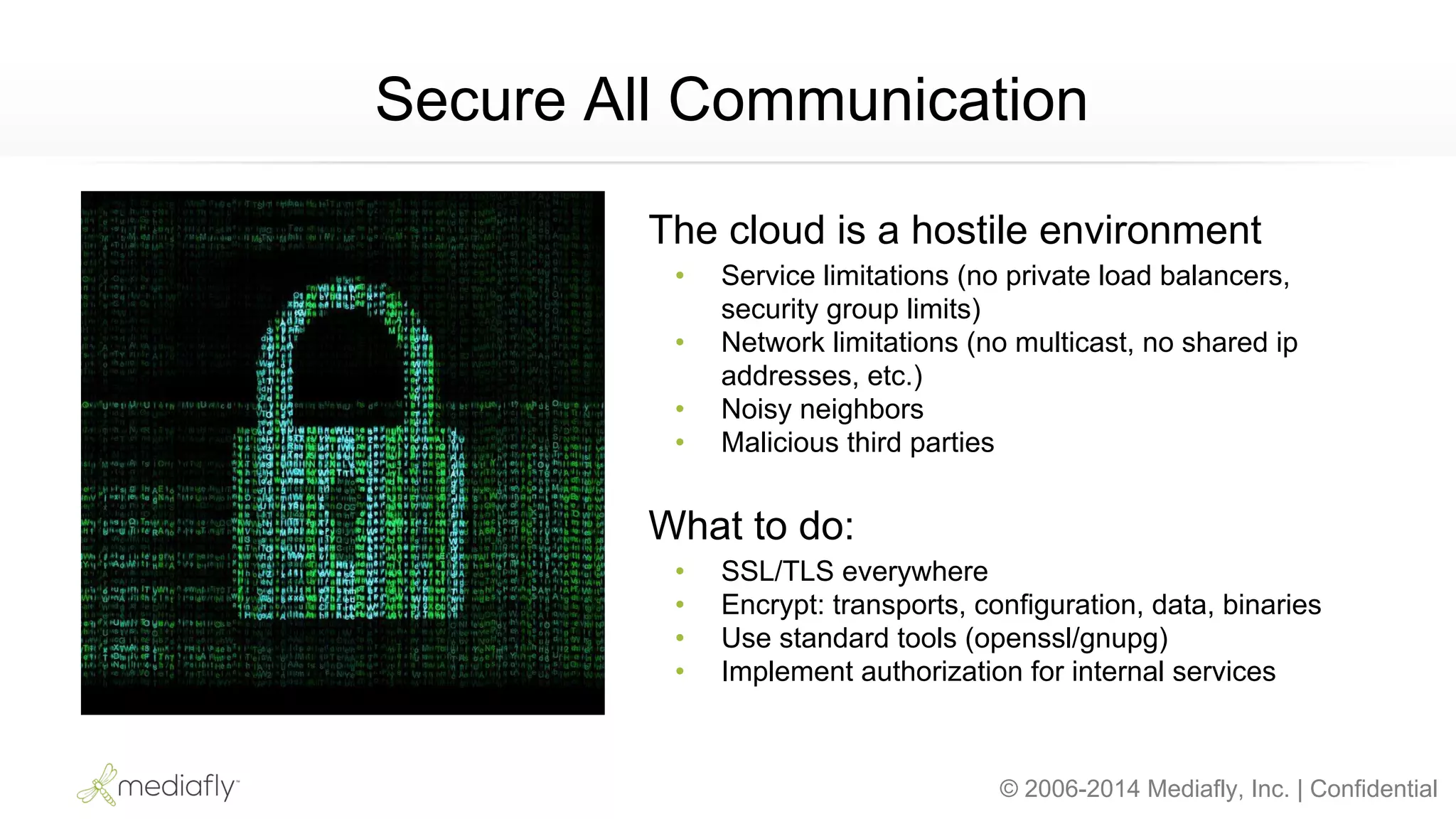
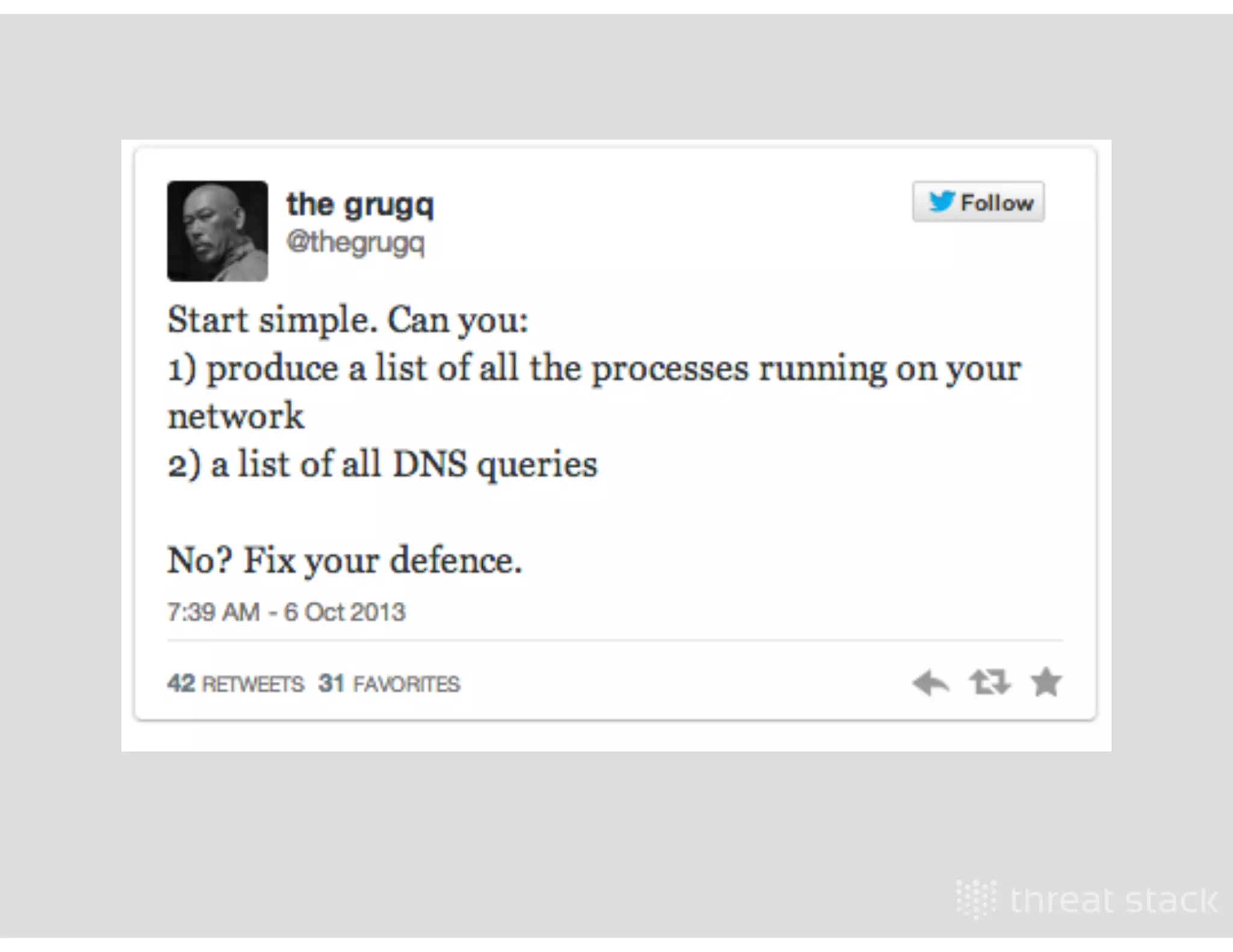
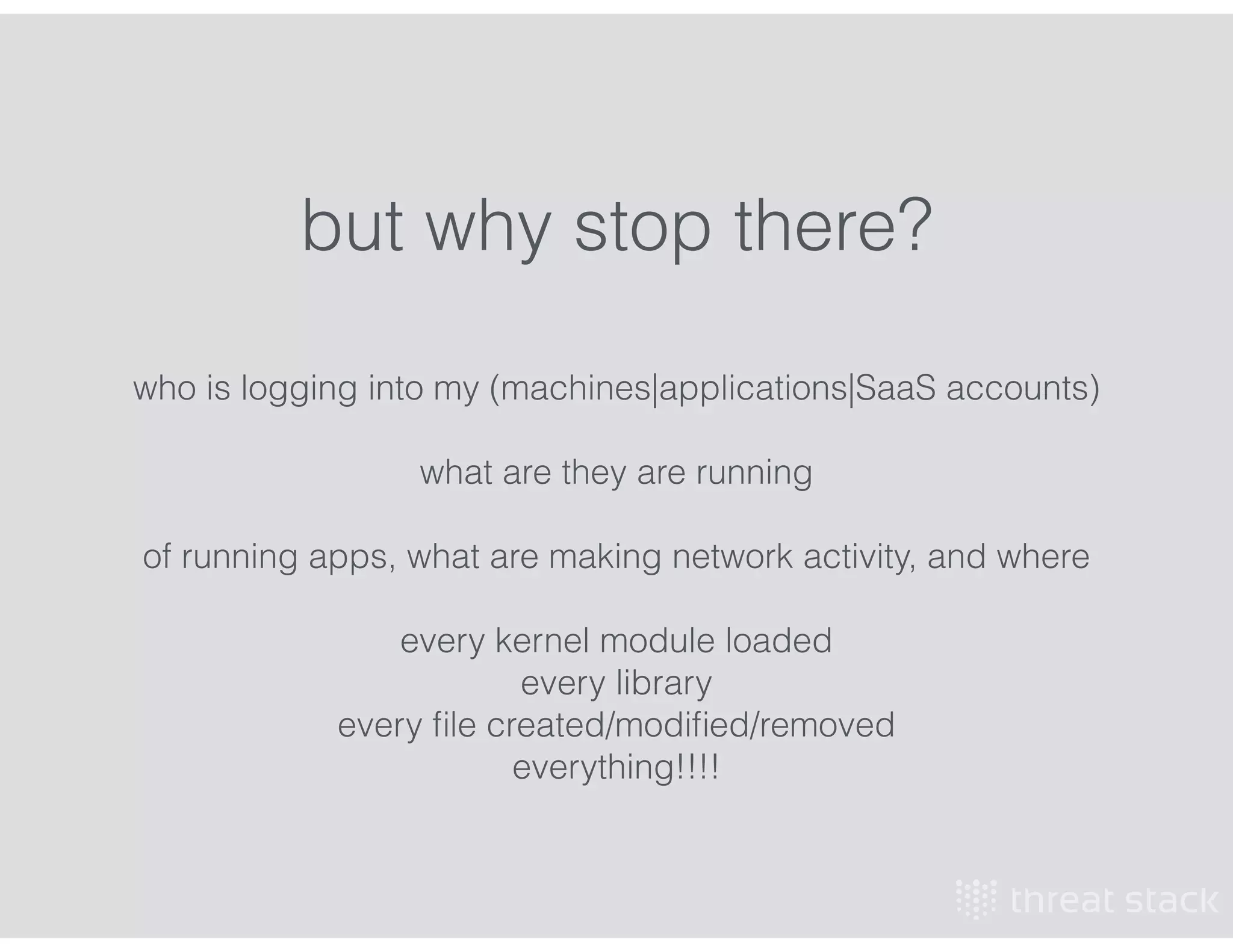
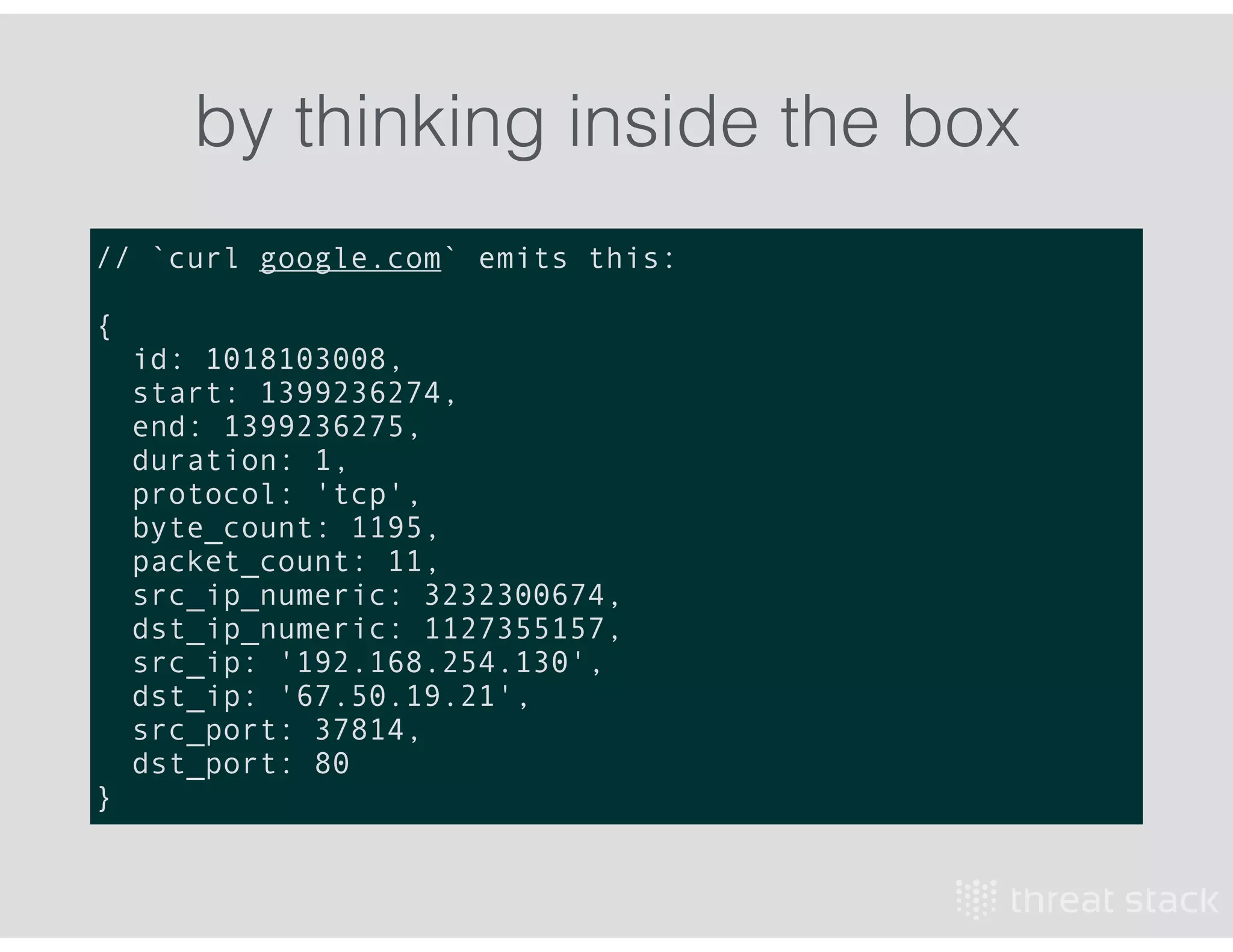
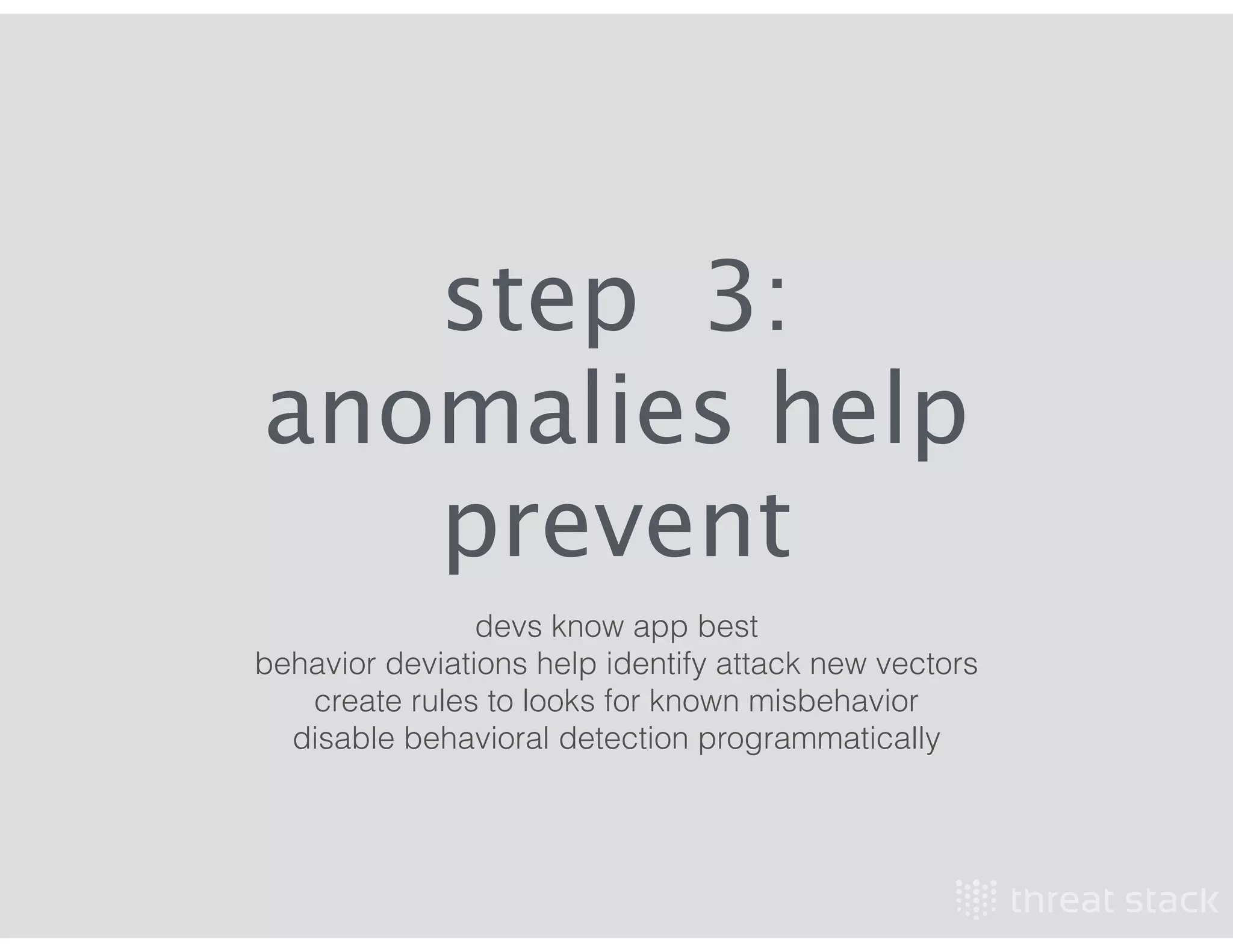
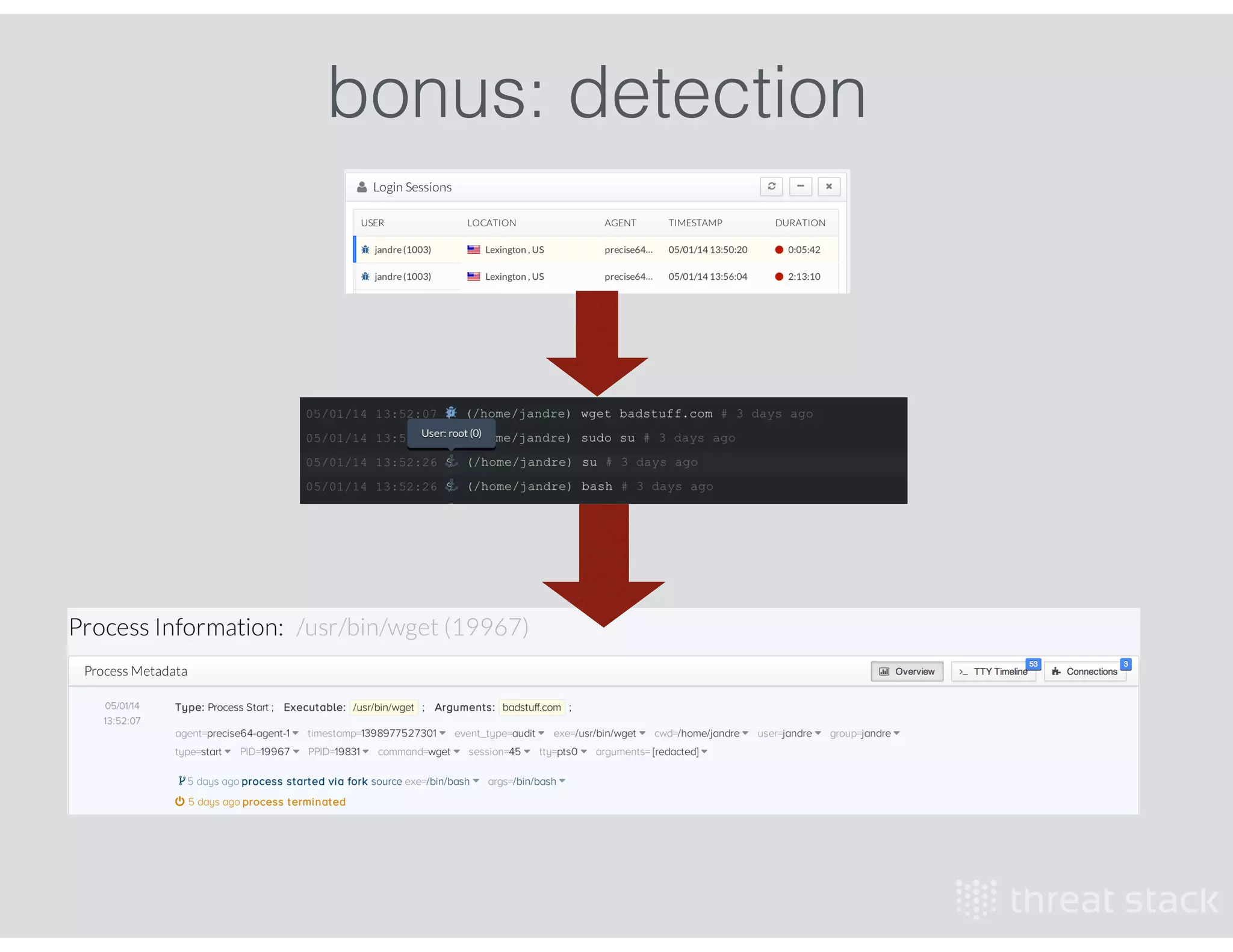
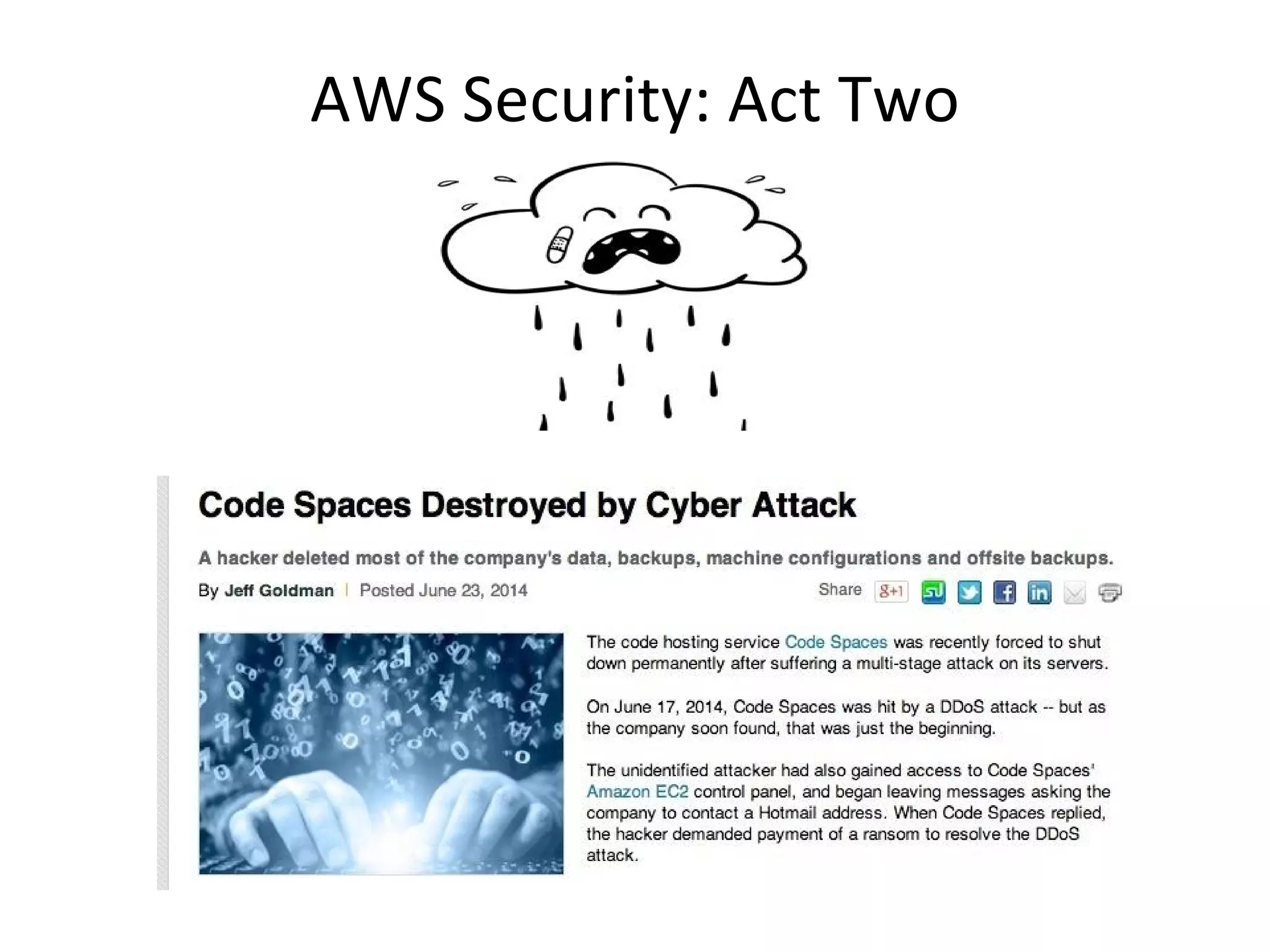
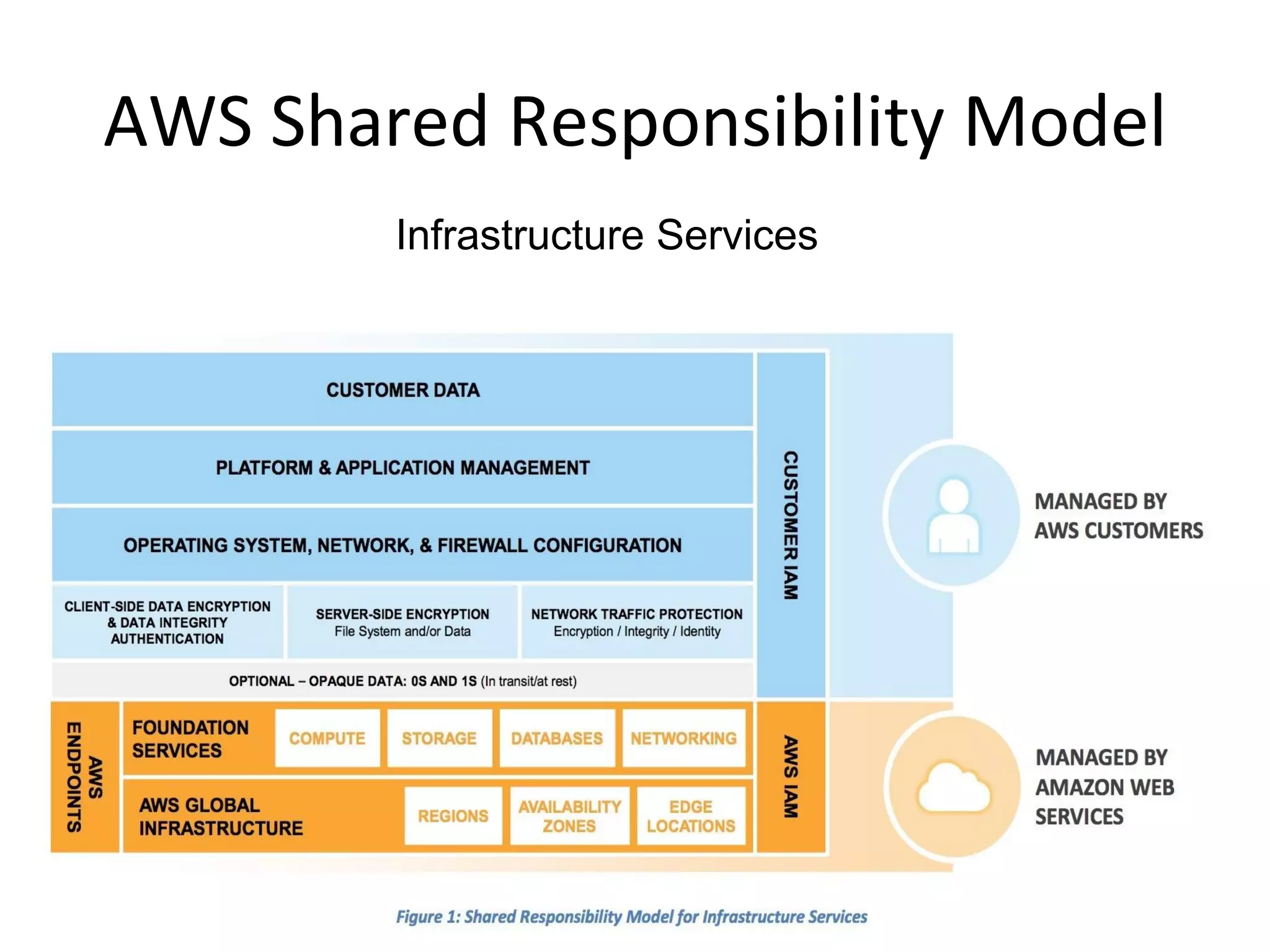
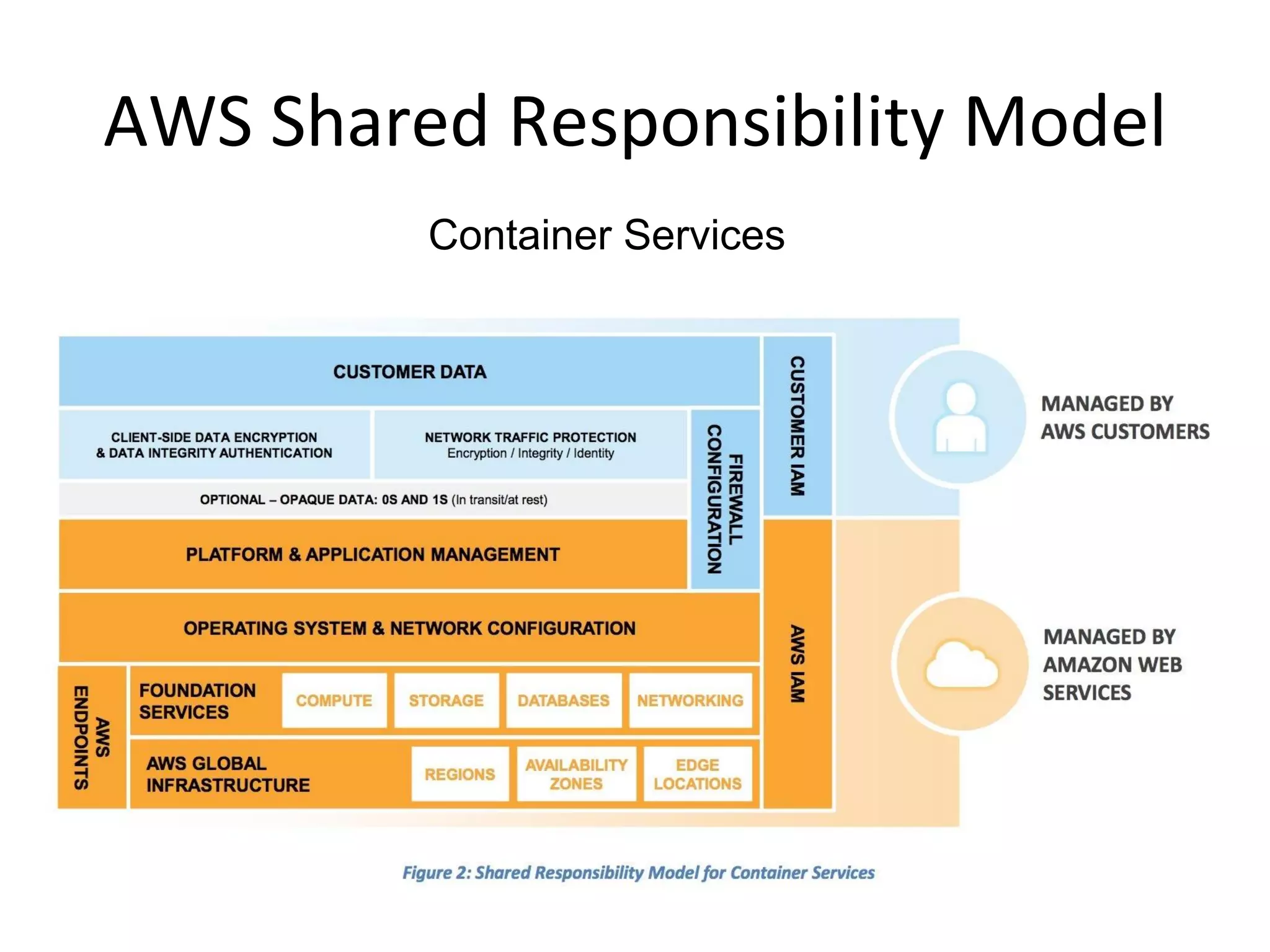
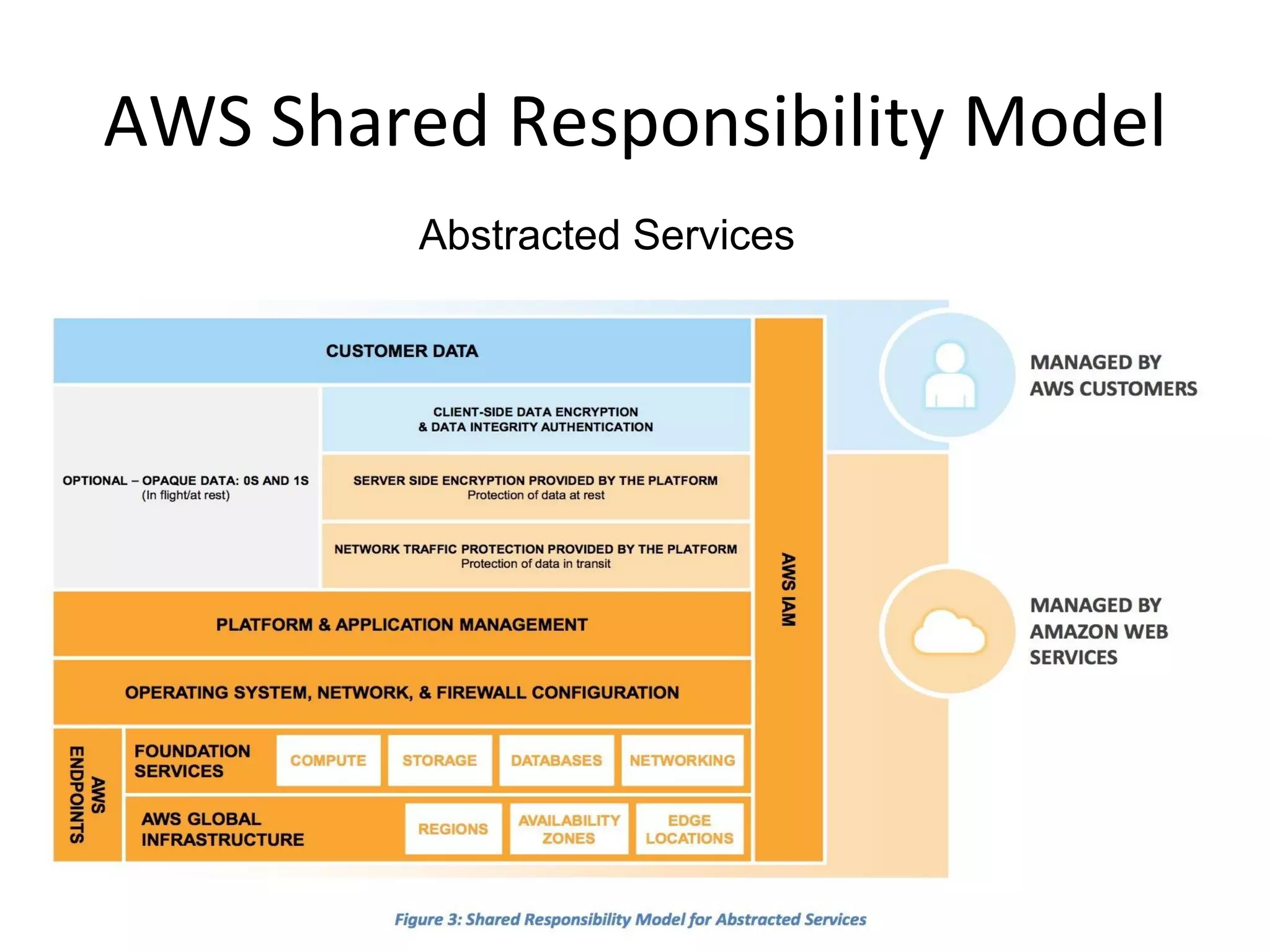
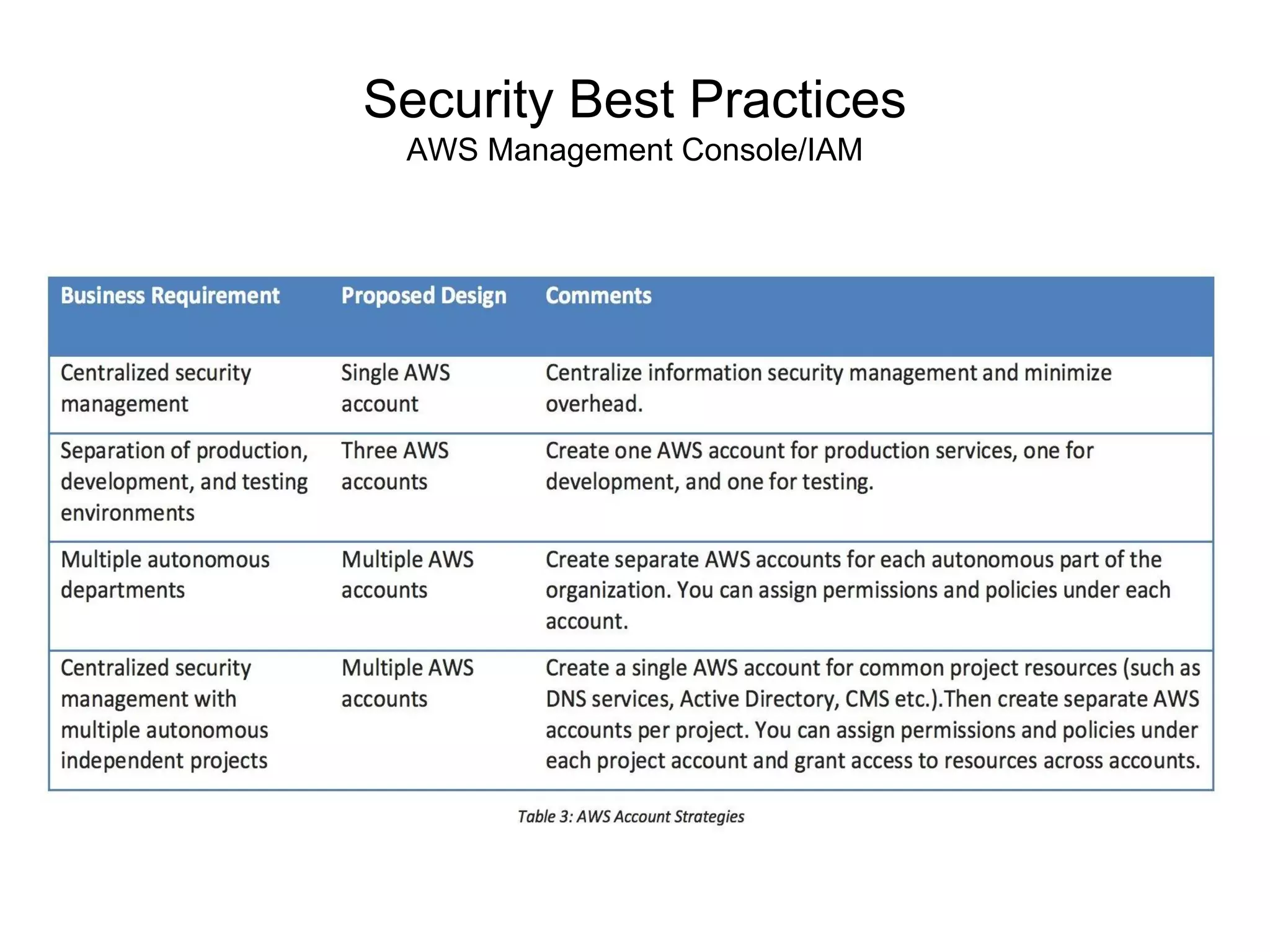
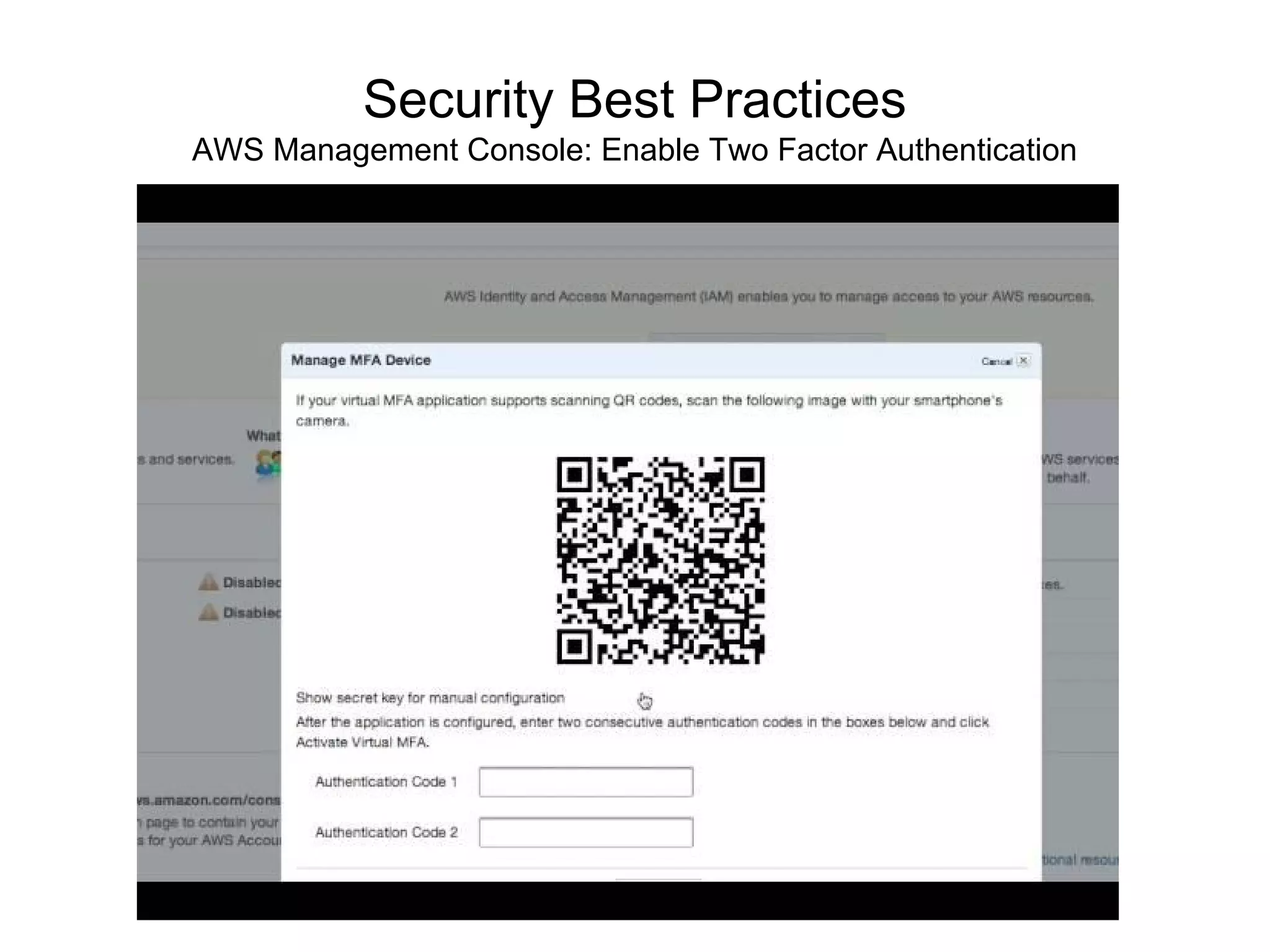
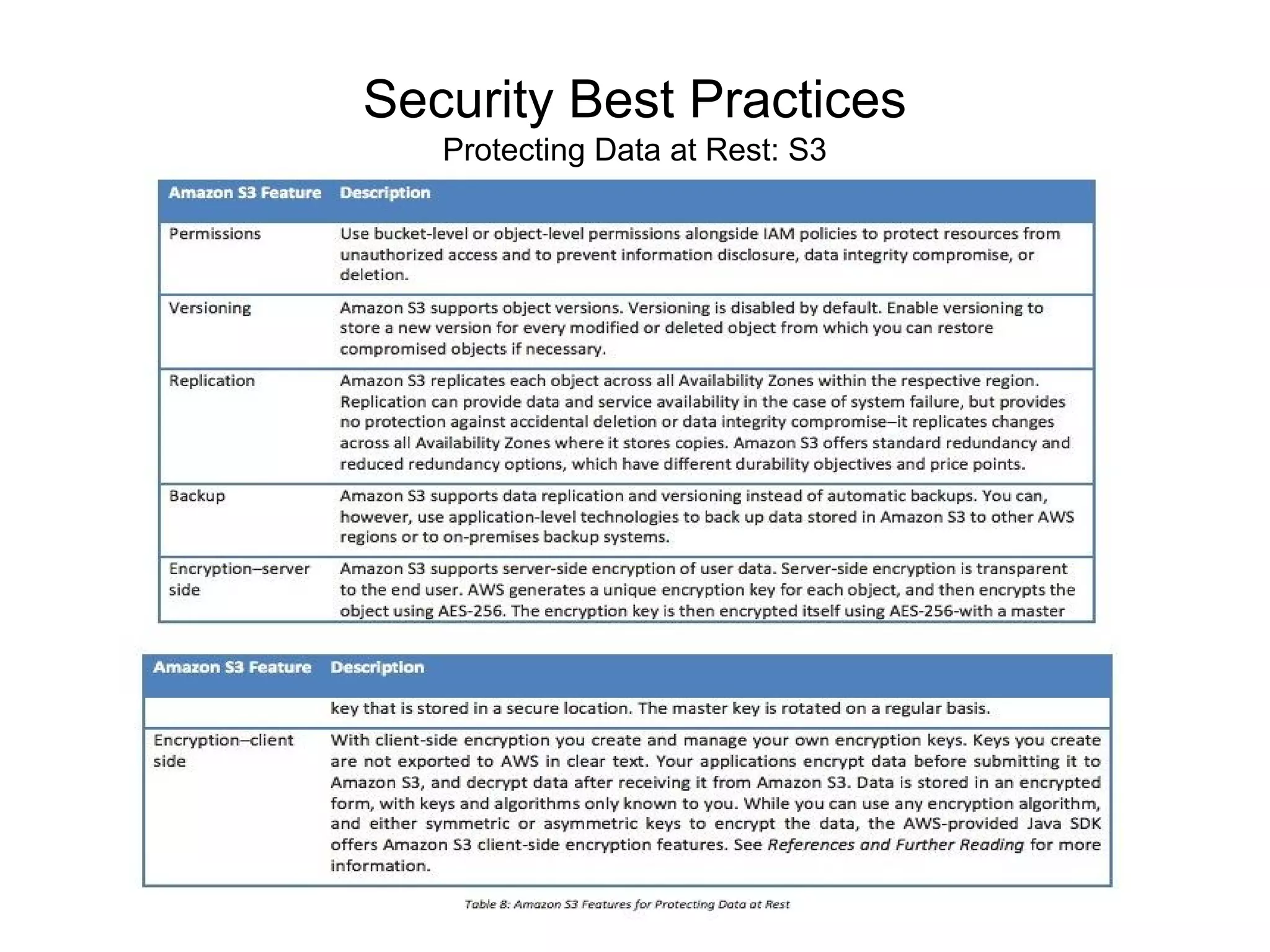
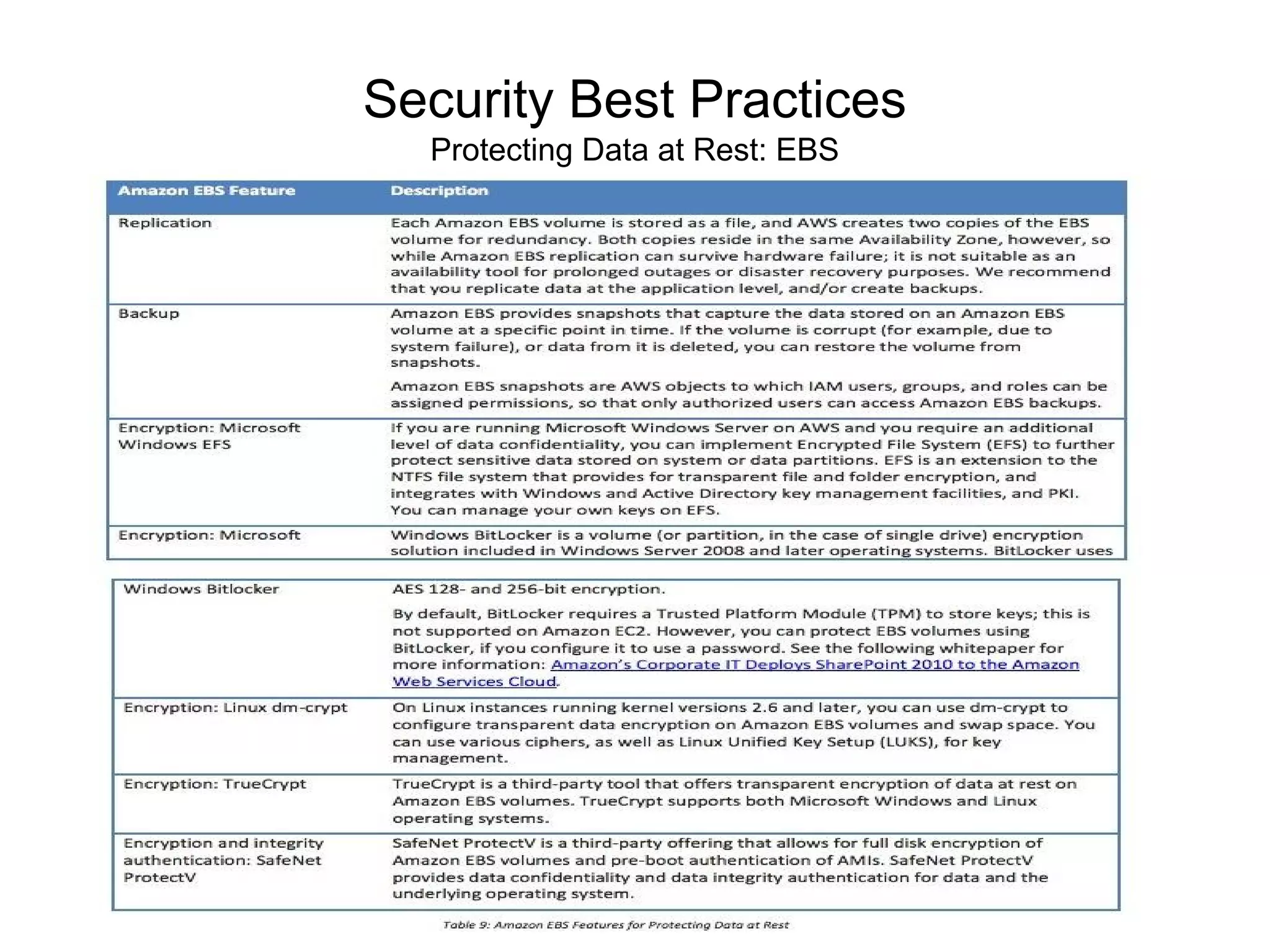
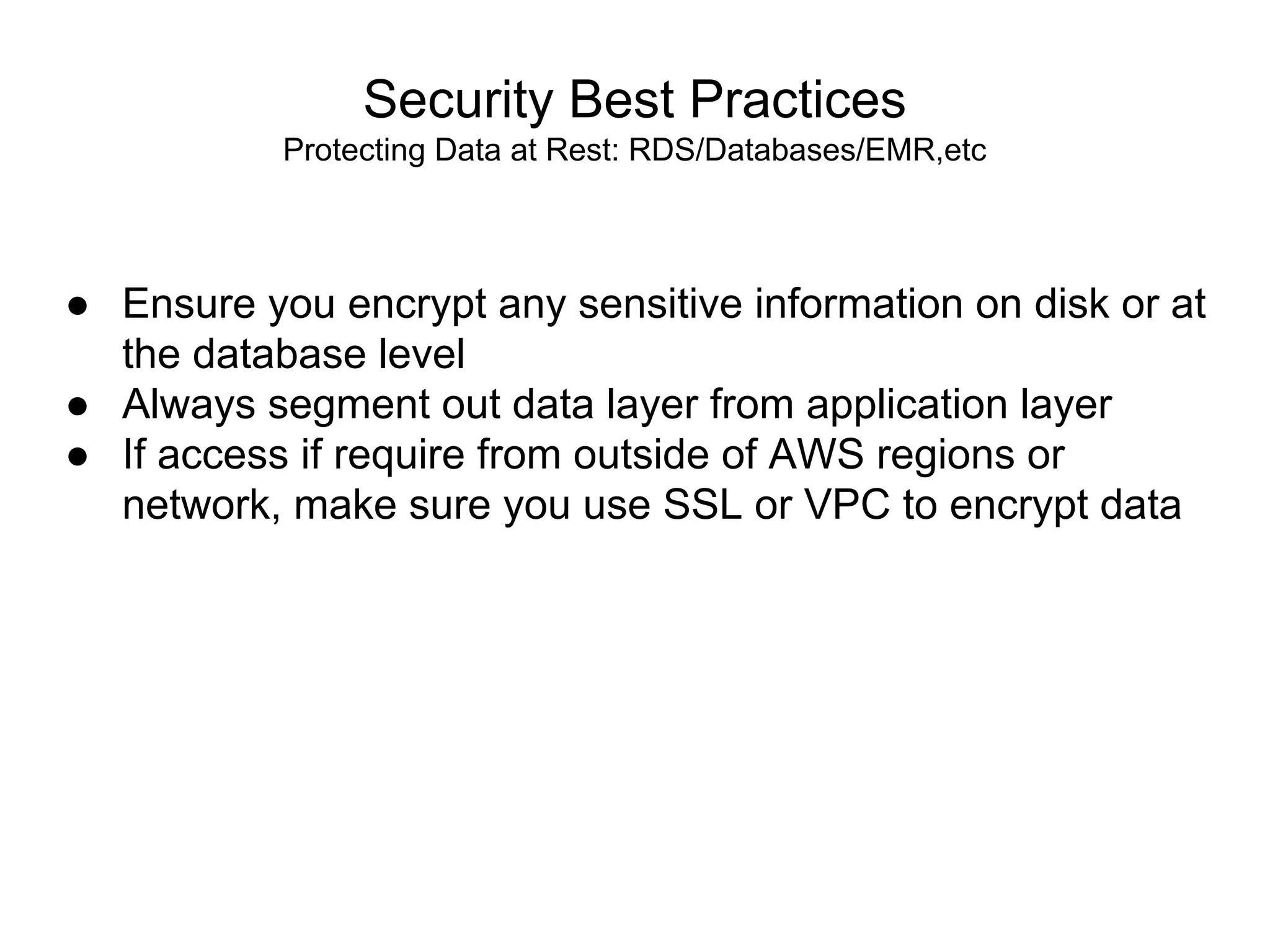
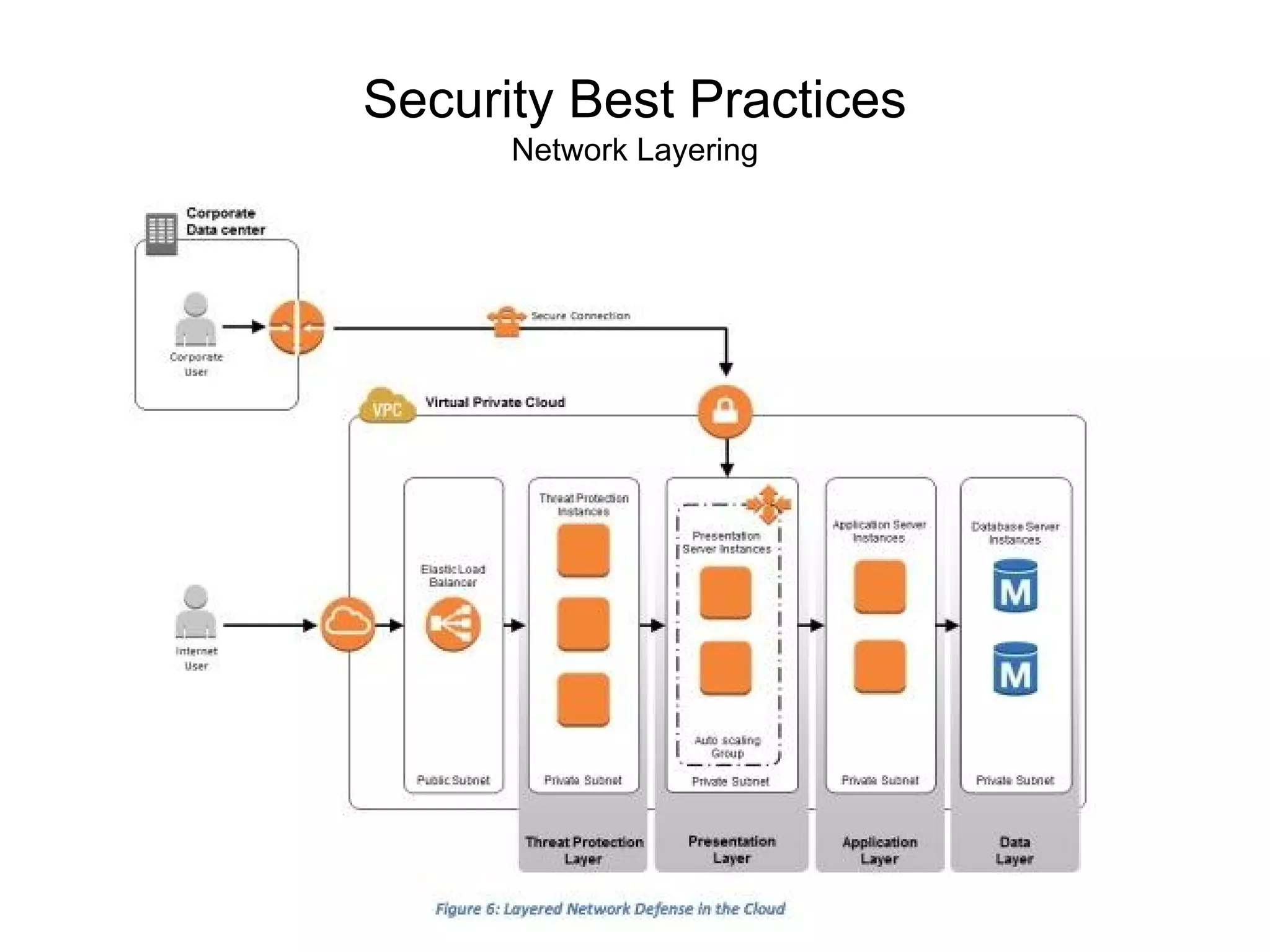
The document outlines an AWS Chicago meetup featuring talks on security practices in AWS, including presentations from experts on topics such as securing AWS installations and advanced monitoring techniques. It emphasizes the importance of encryption, access control, and automated security testing to protect sensitive data in the cloud. The event includes networking opportunities and a Q&A session to discuss AWS security best practices.