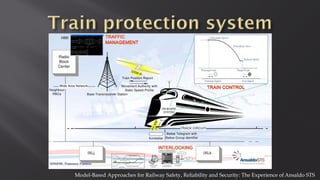
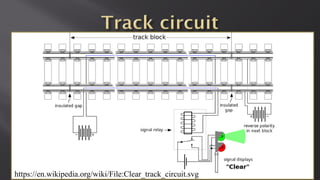
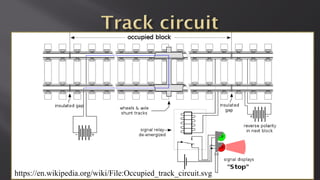
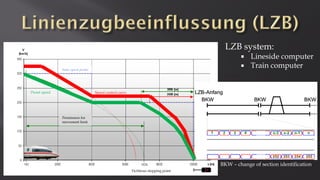
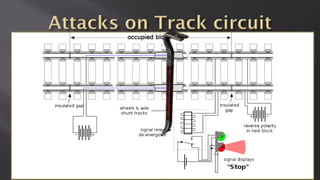
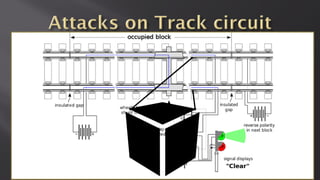
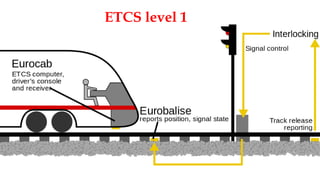
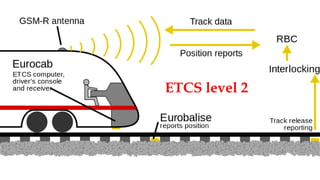
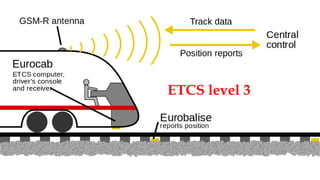
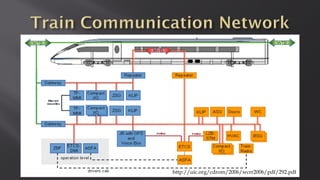
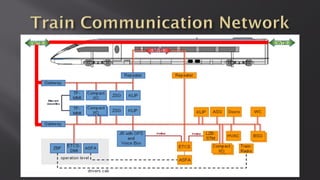
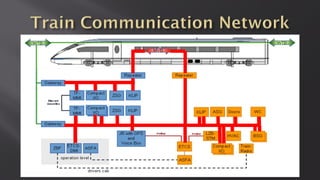
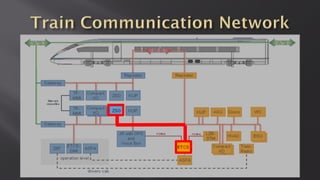
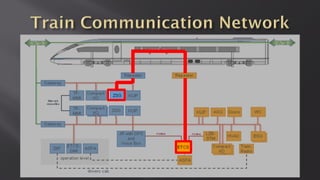
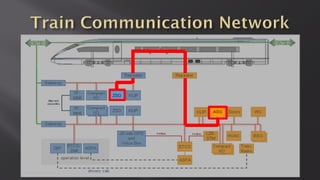
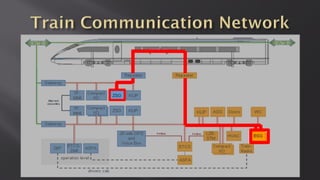
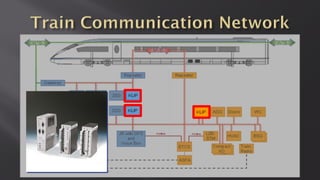
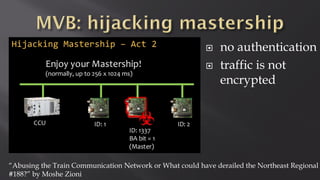
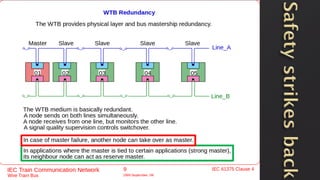
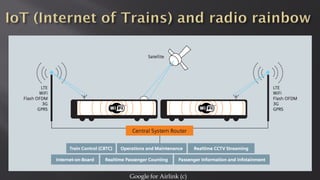
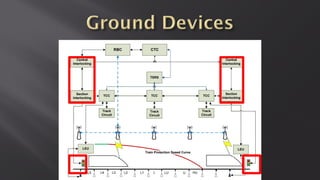
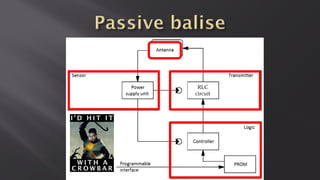
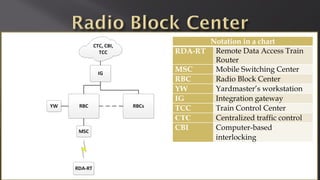
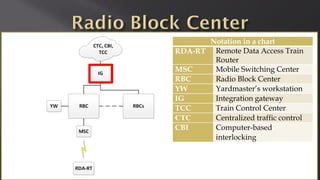
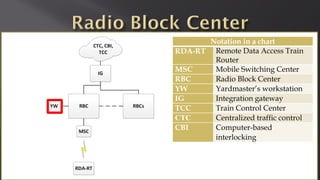
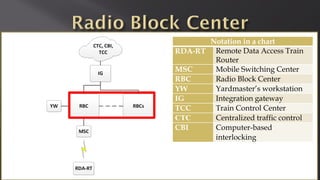
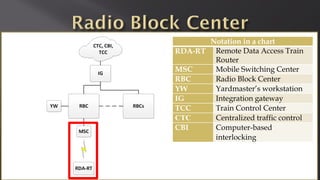
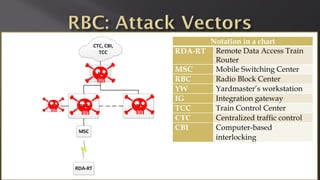
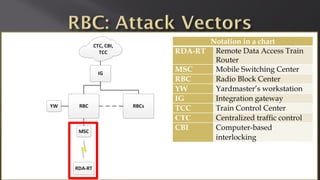
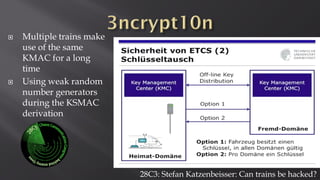
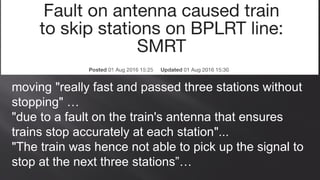
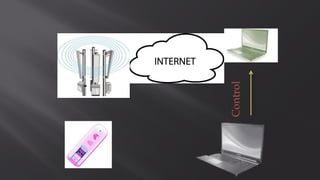
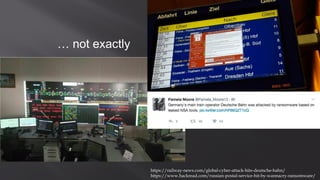
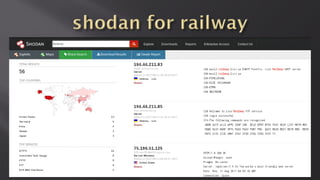
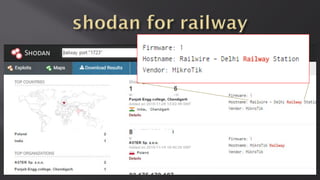
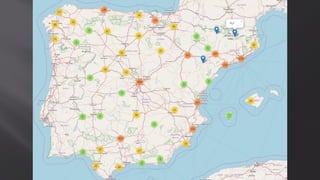
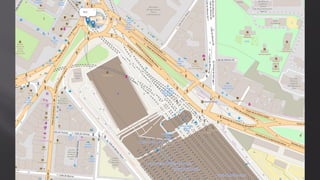
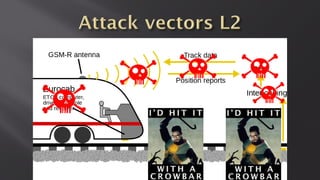
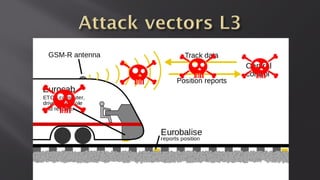
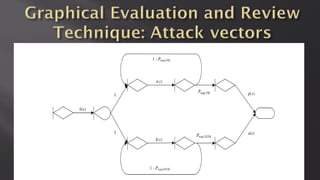
This document discusses a presentation given by the SCADA StrangeLove team, a group of security researchers focused on industrial control systems. The presentation provides an overview of railway safety and signaling systems such as ETCS and analyzes past railway accidents like those in Santiago de Compostela and Wenzhou. It also examines train communication networks and onboard control systems from a security perspective. Throughout, it emphasizes that the views expressed are those of the researchers and not their employers.