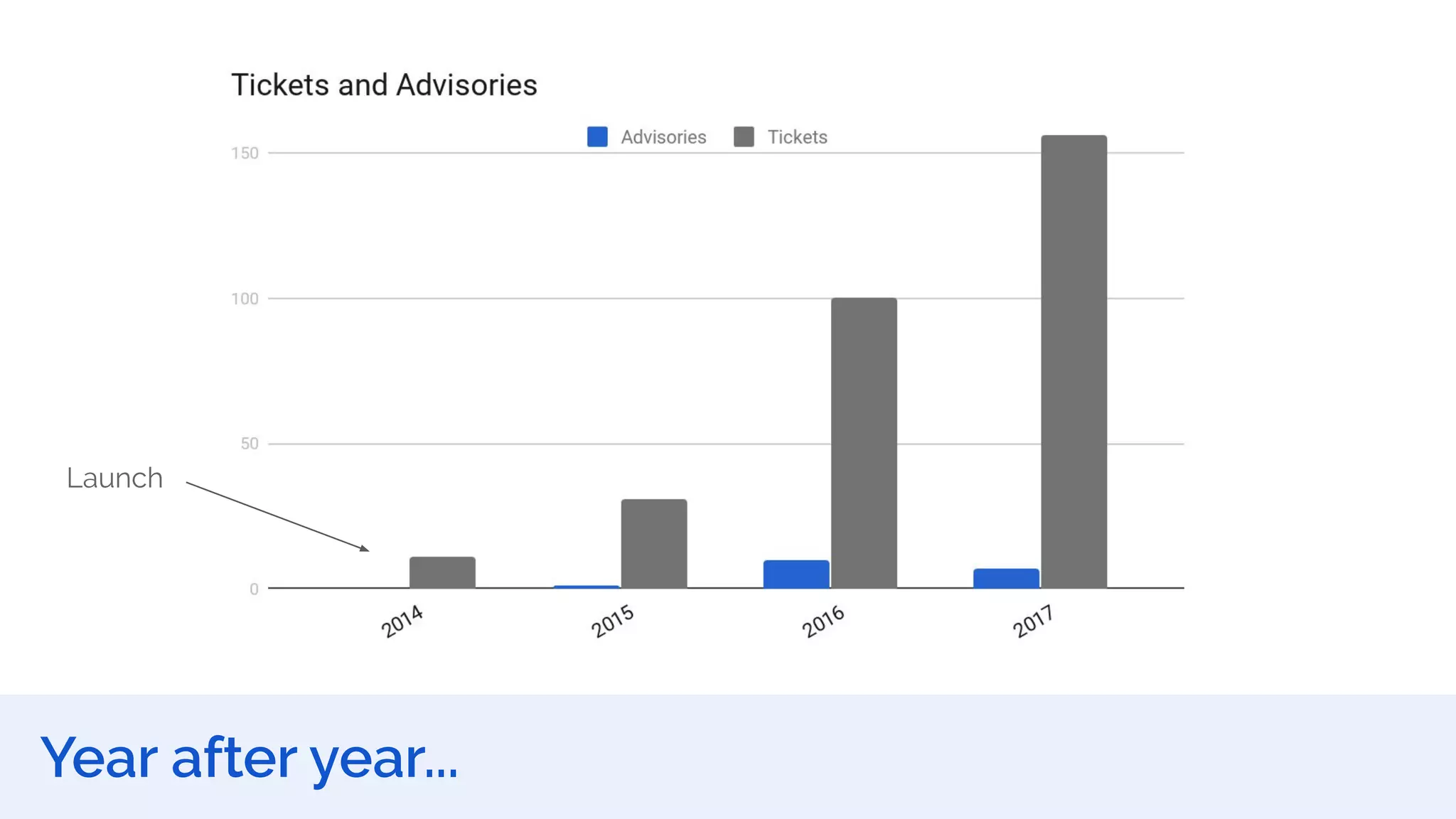
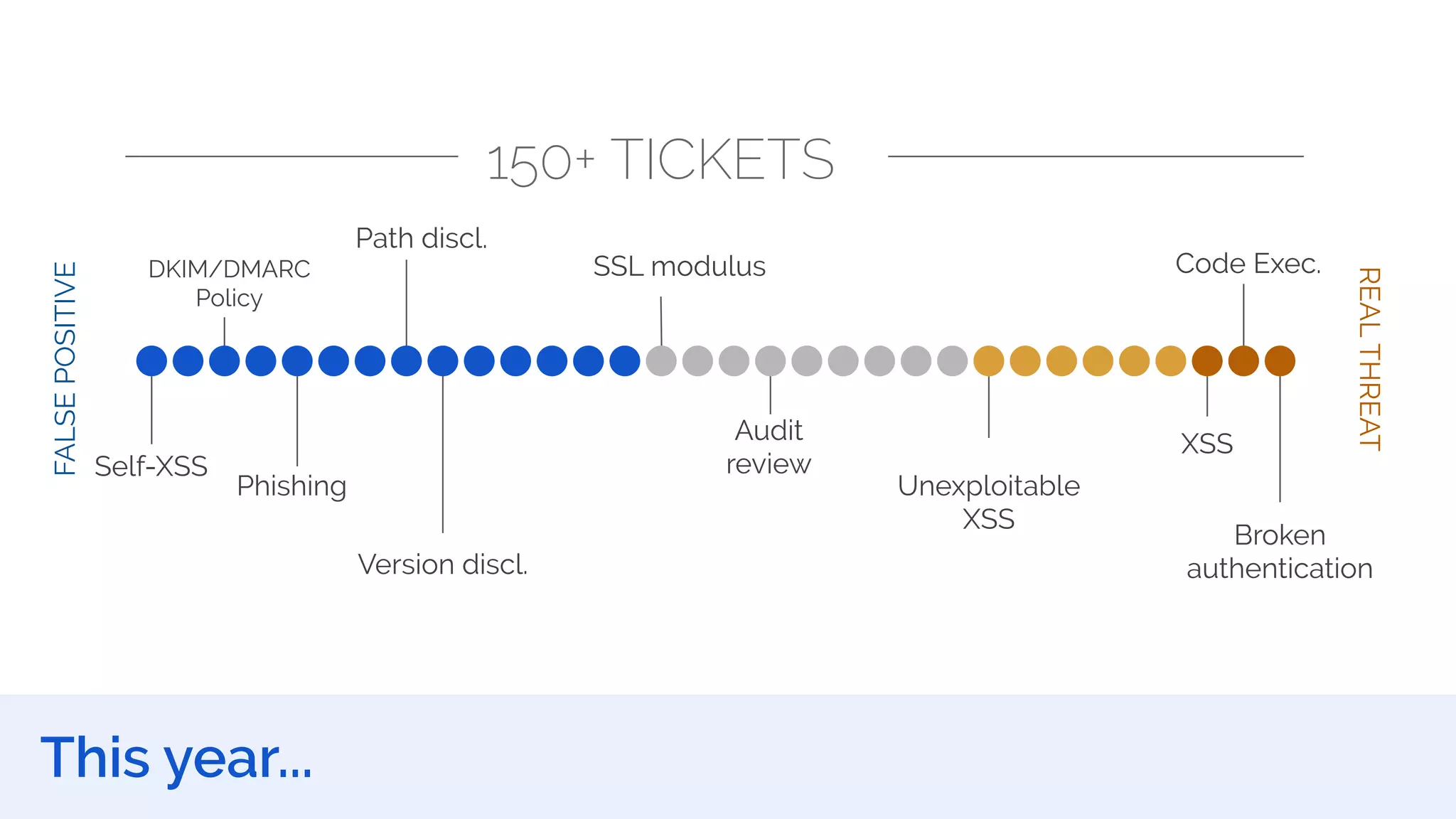
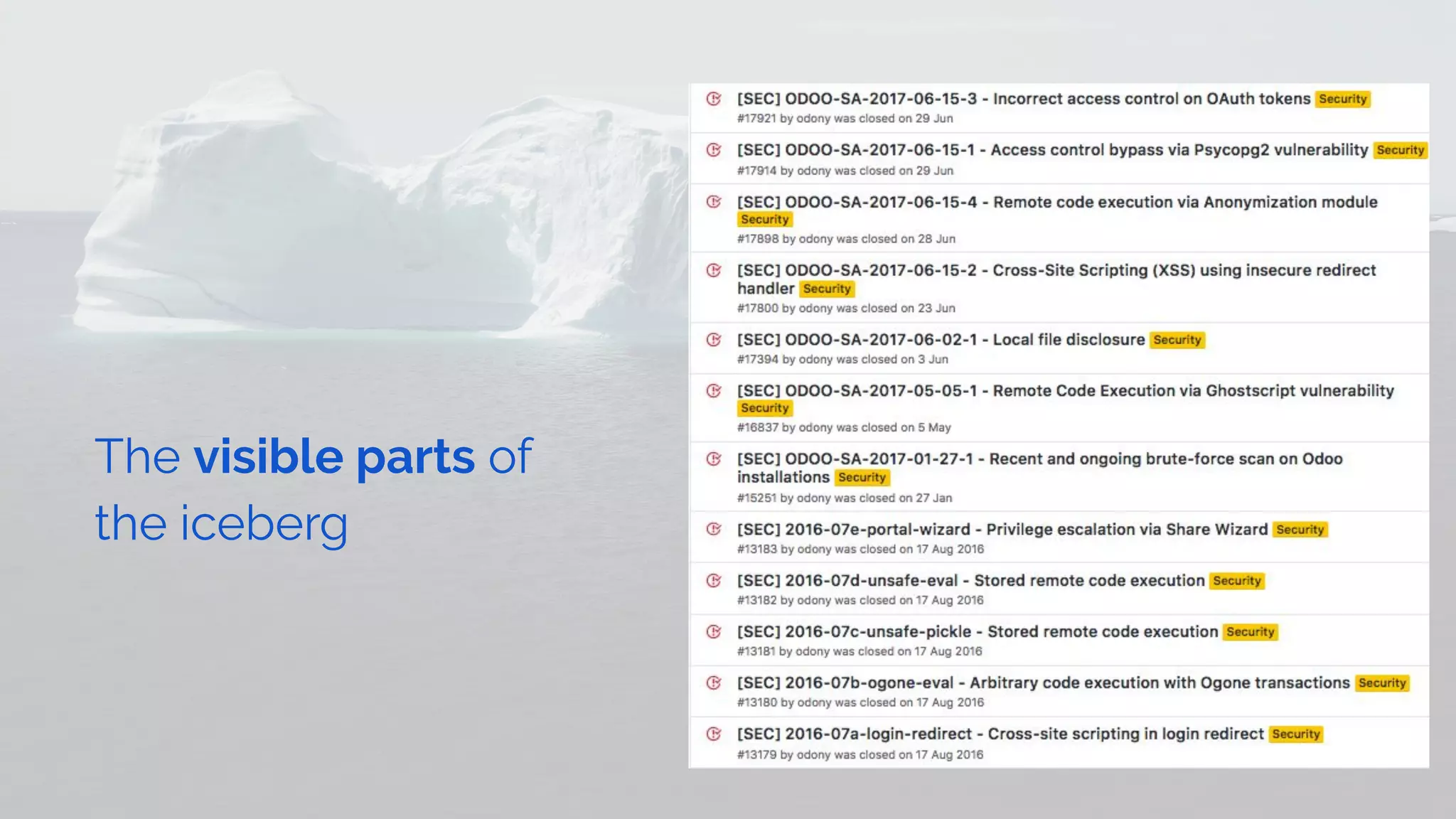
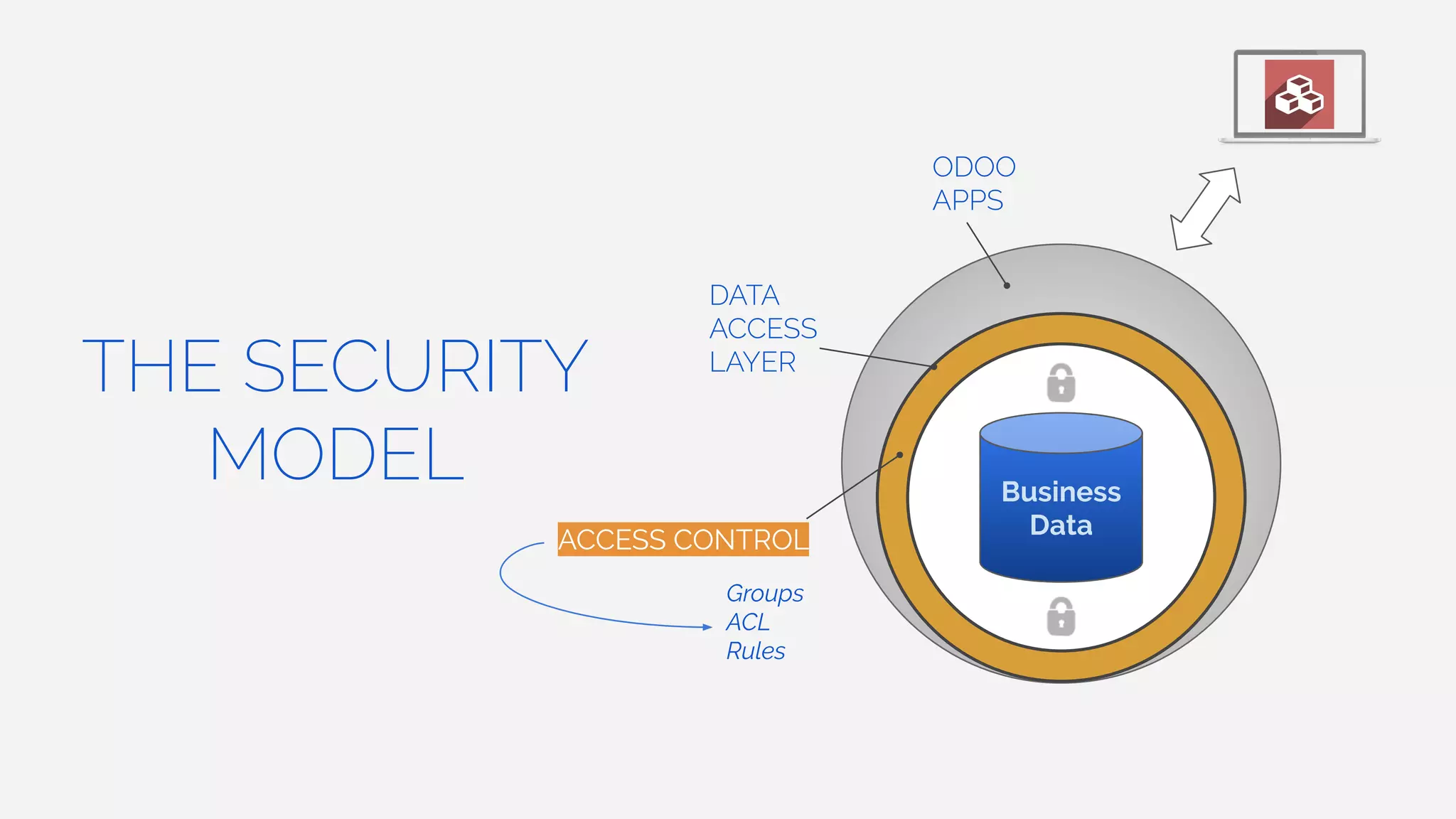
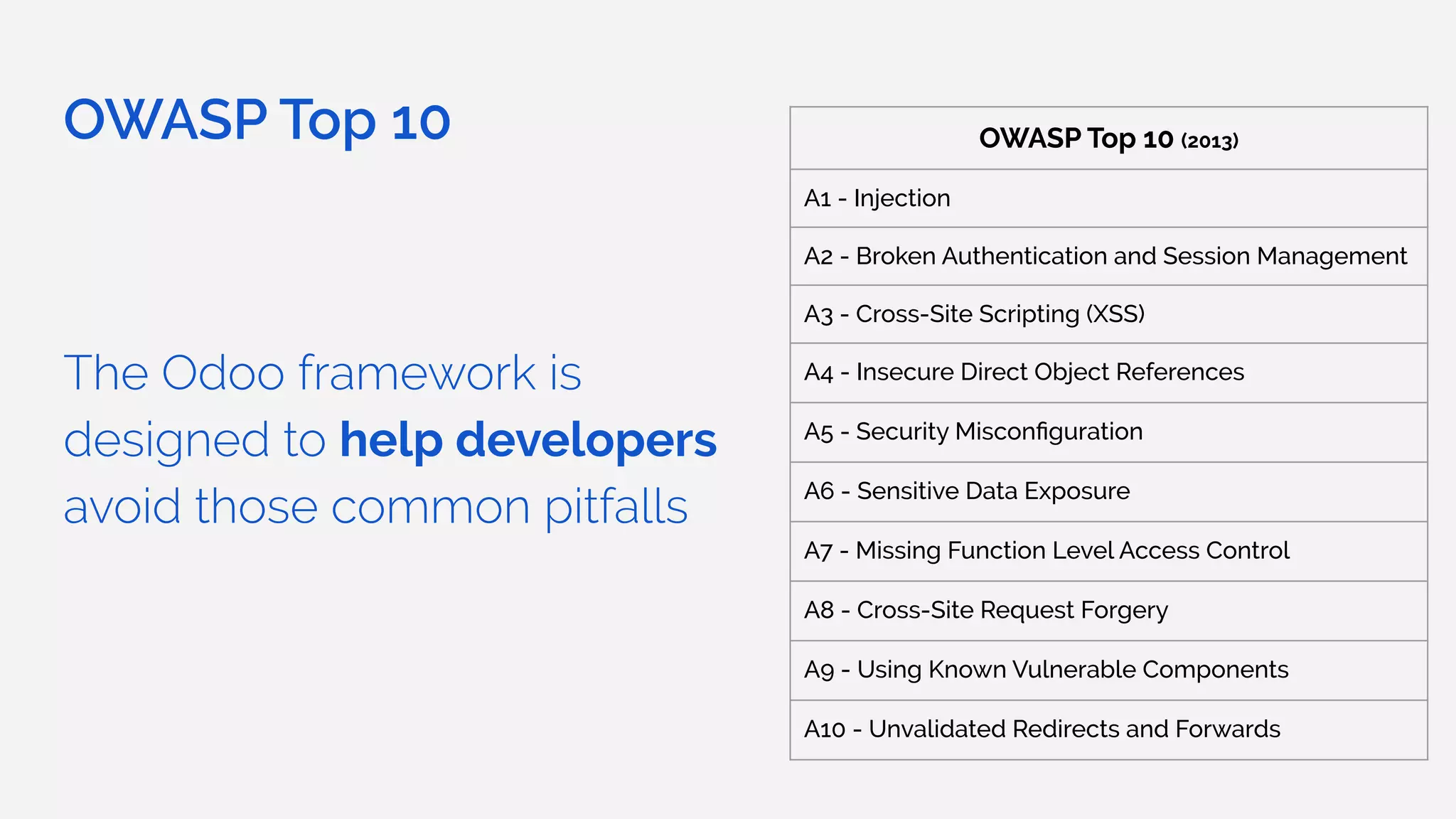
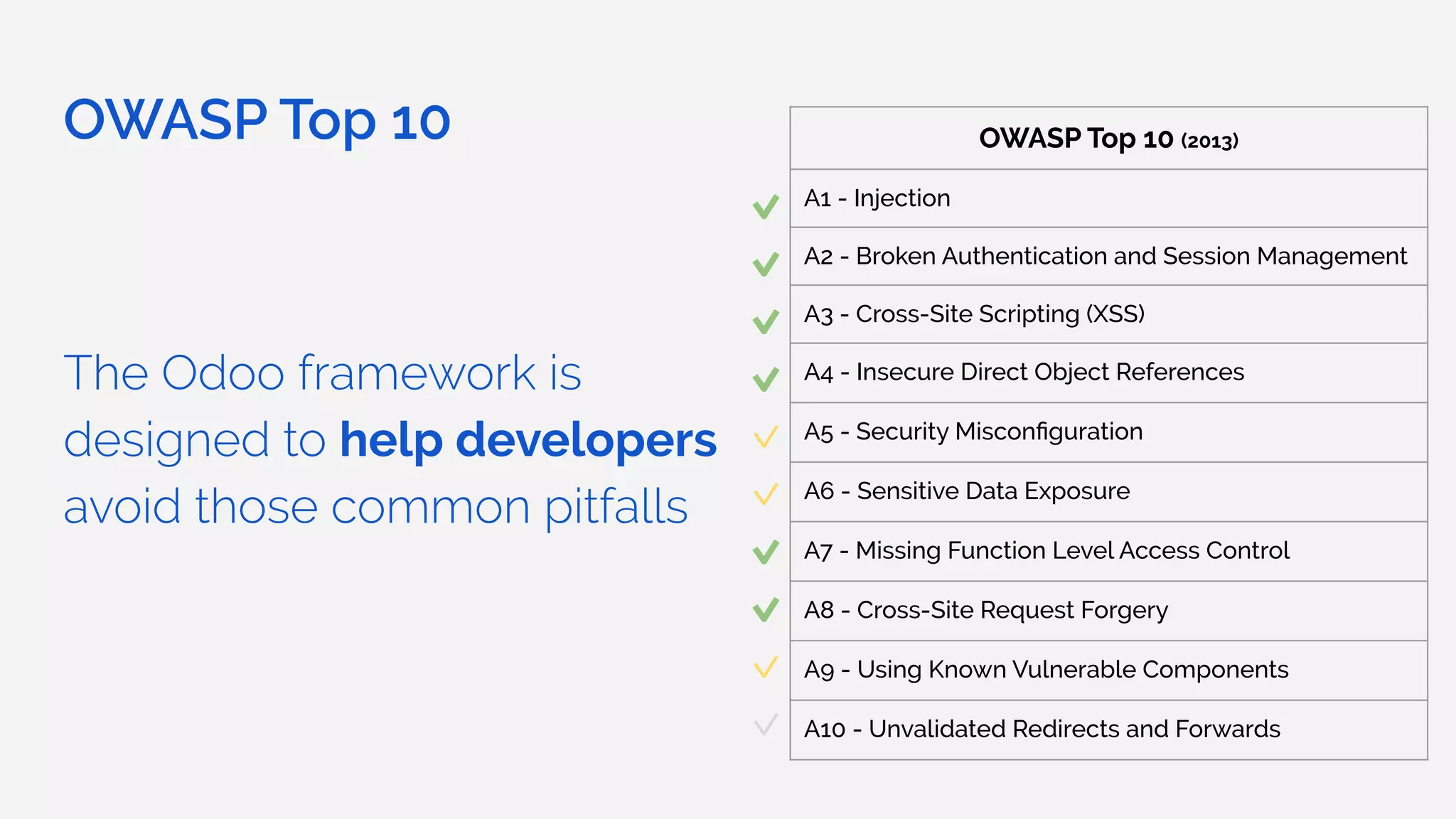
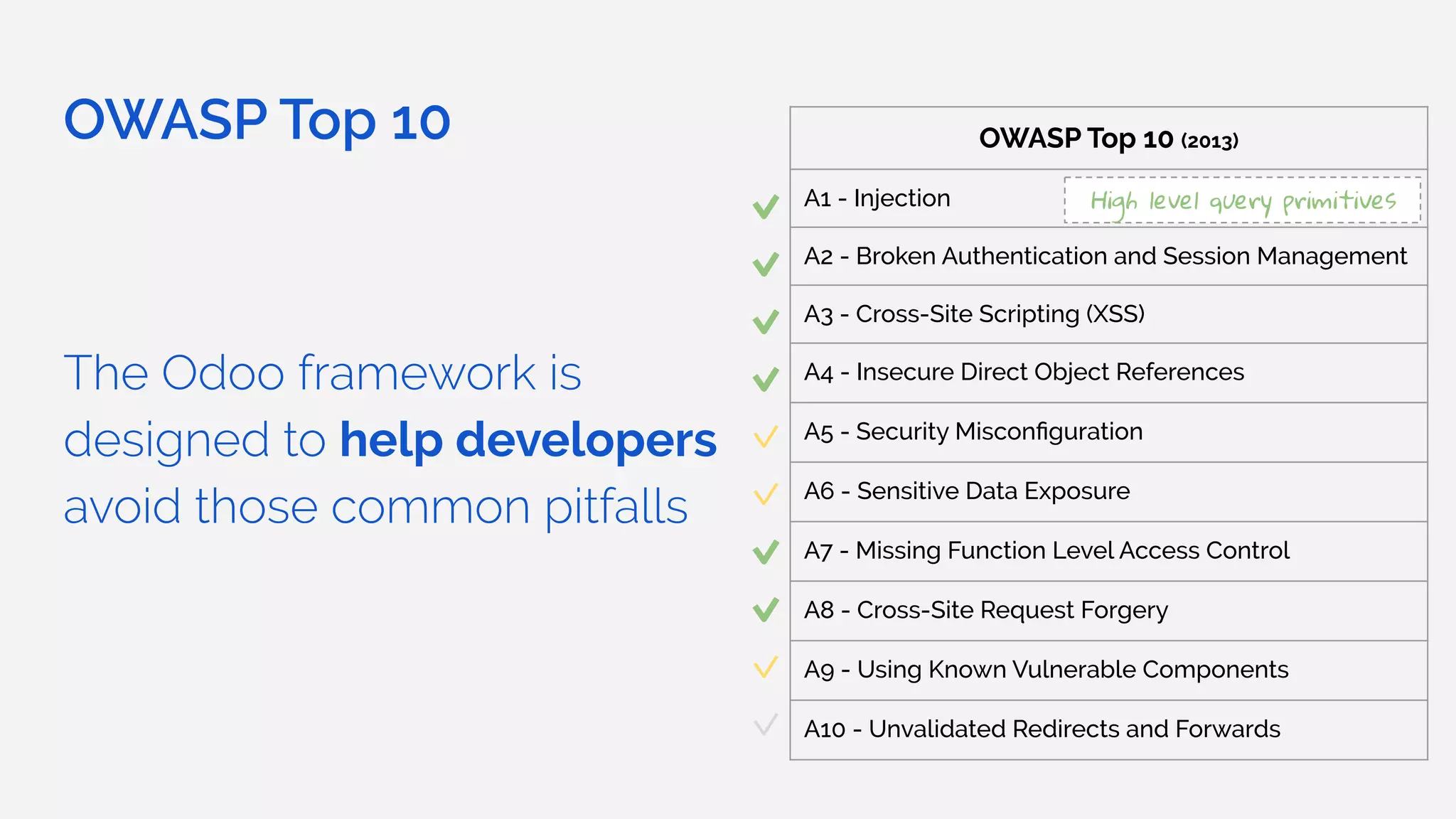
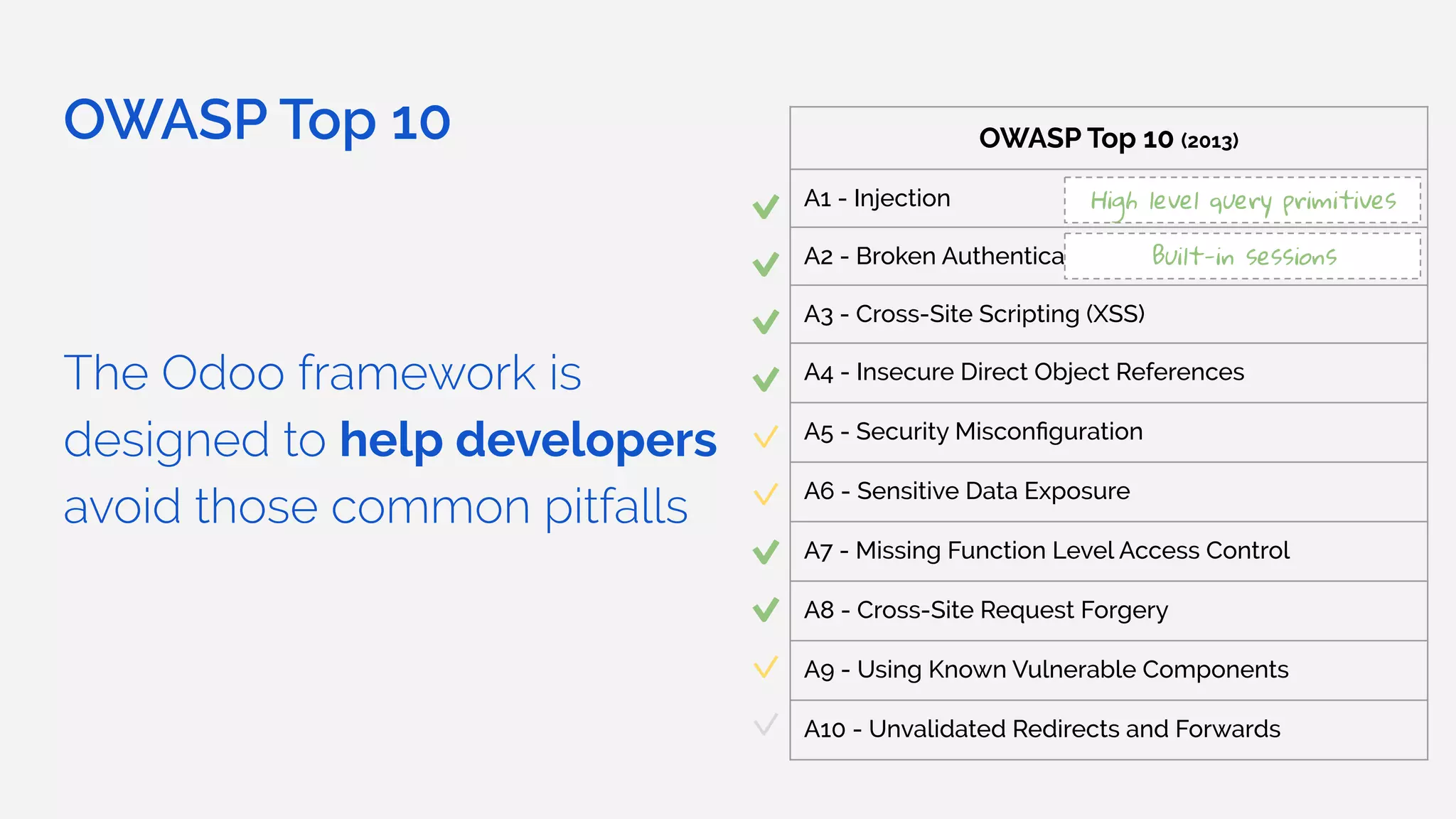
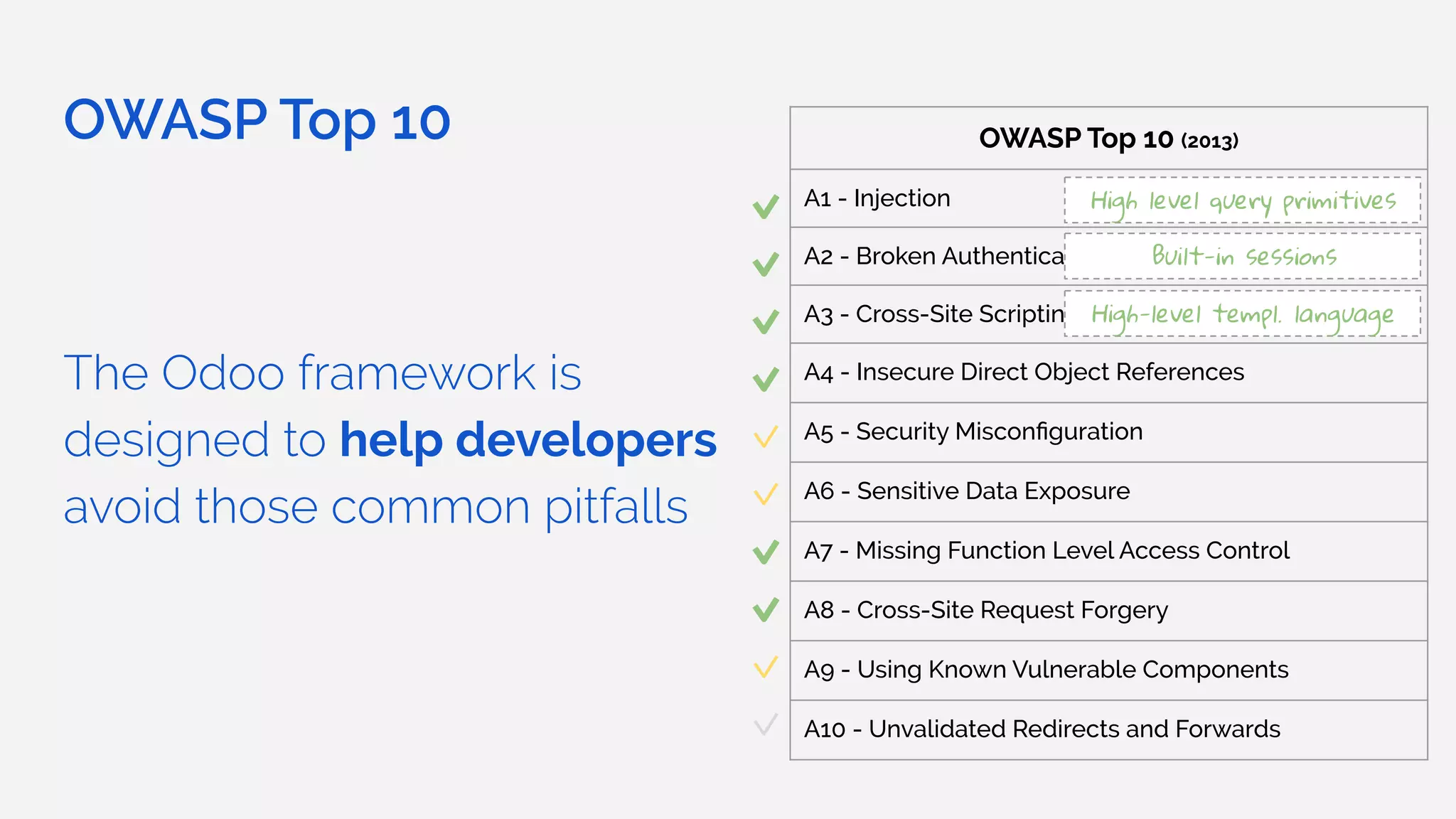
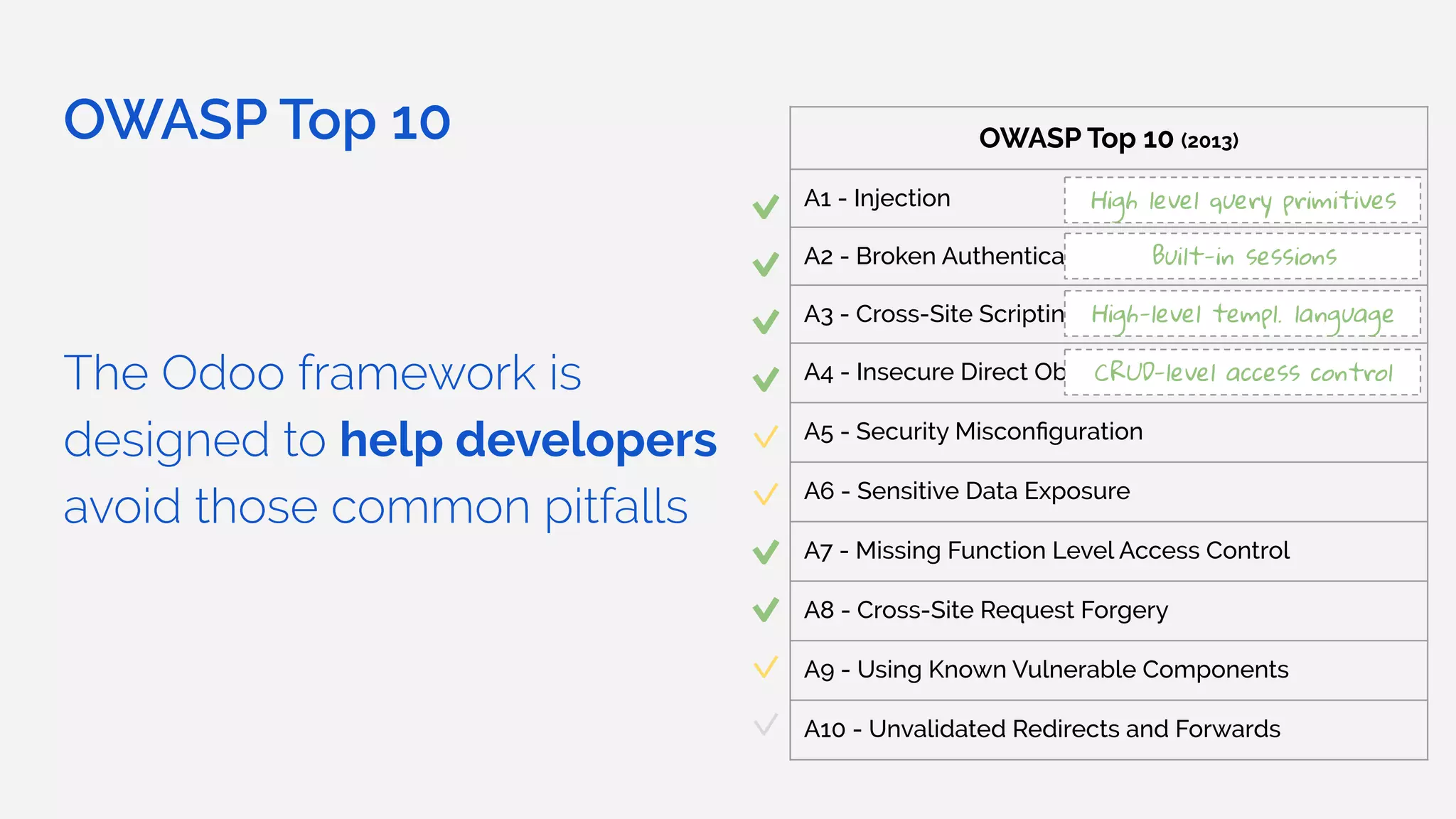
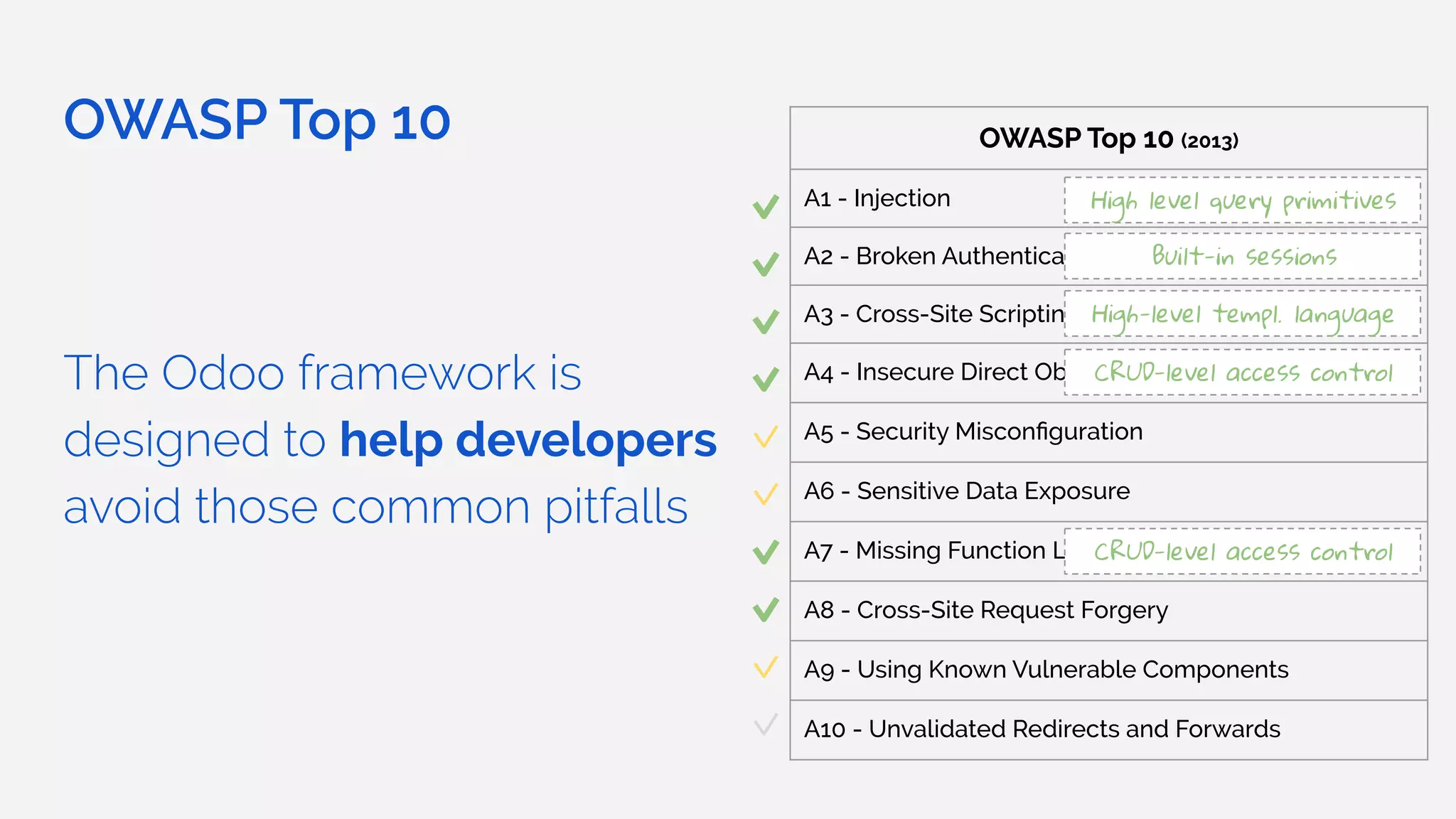
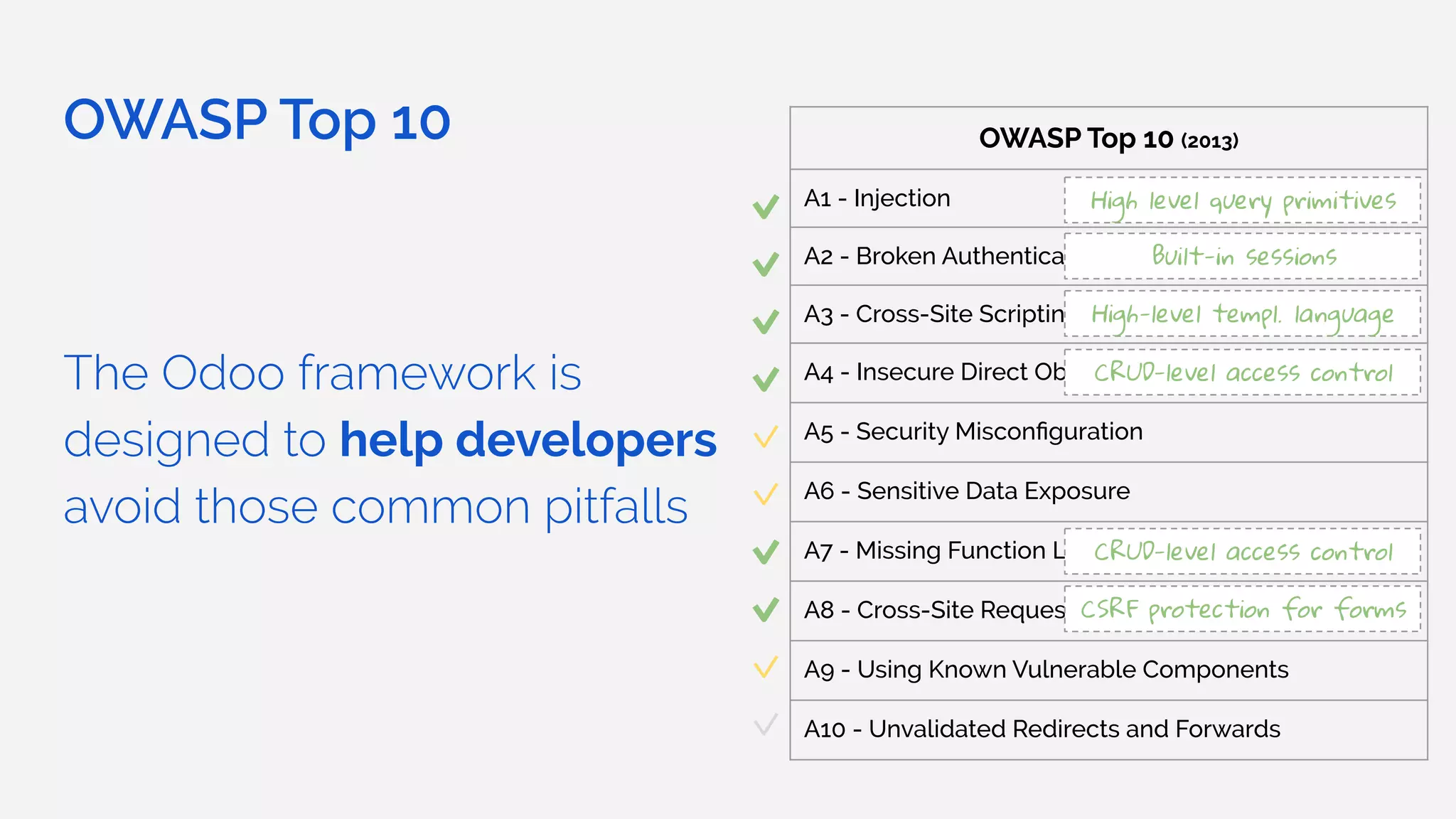
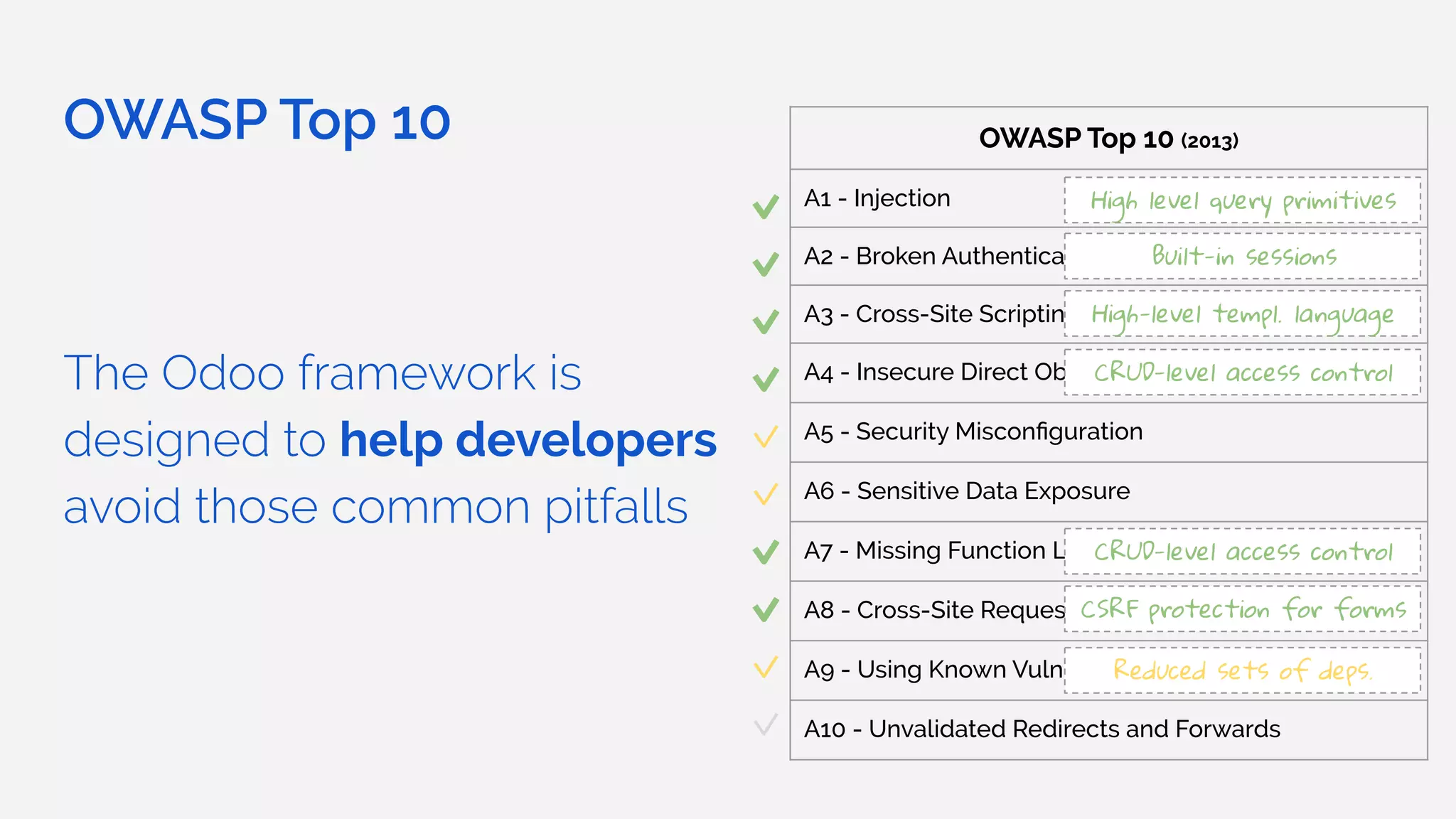
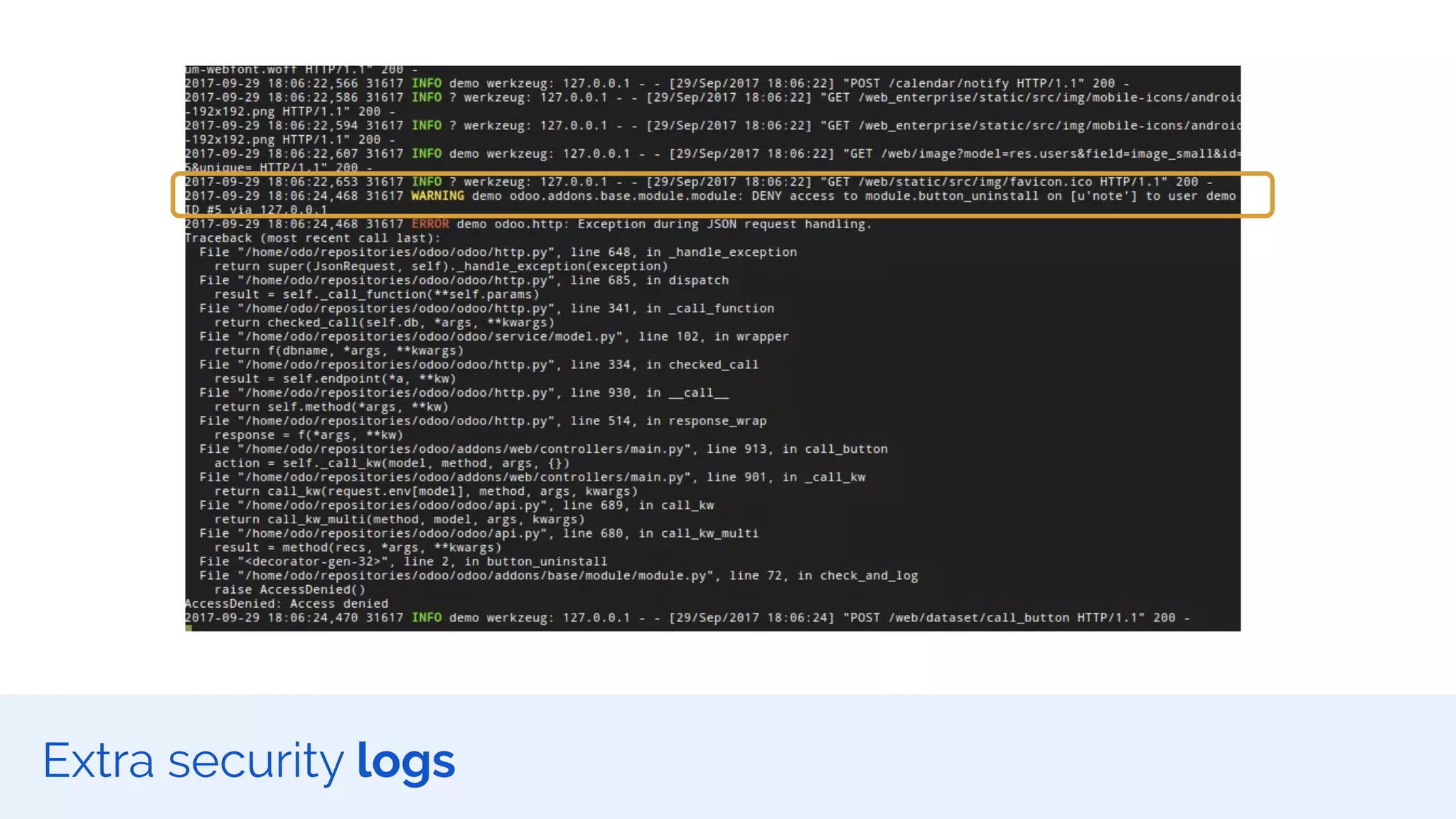
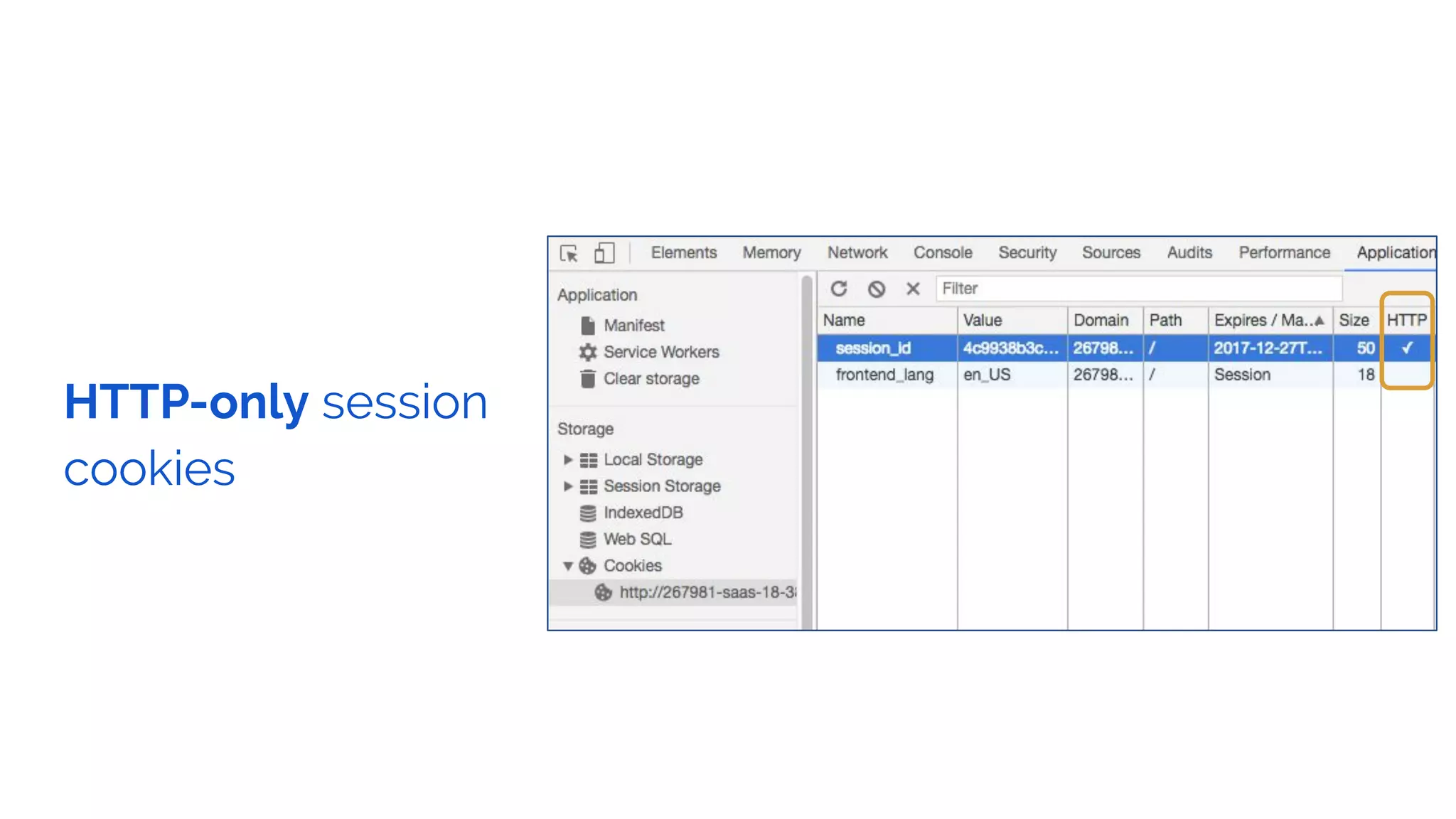
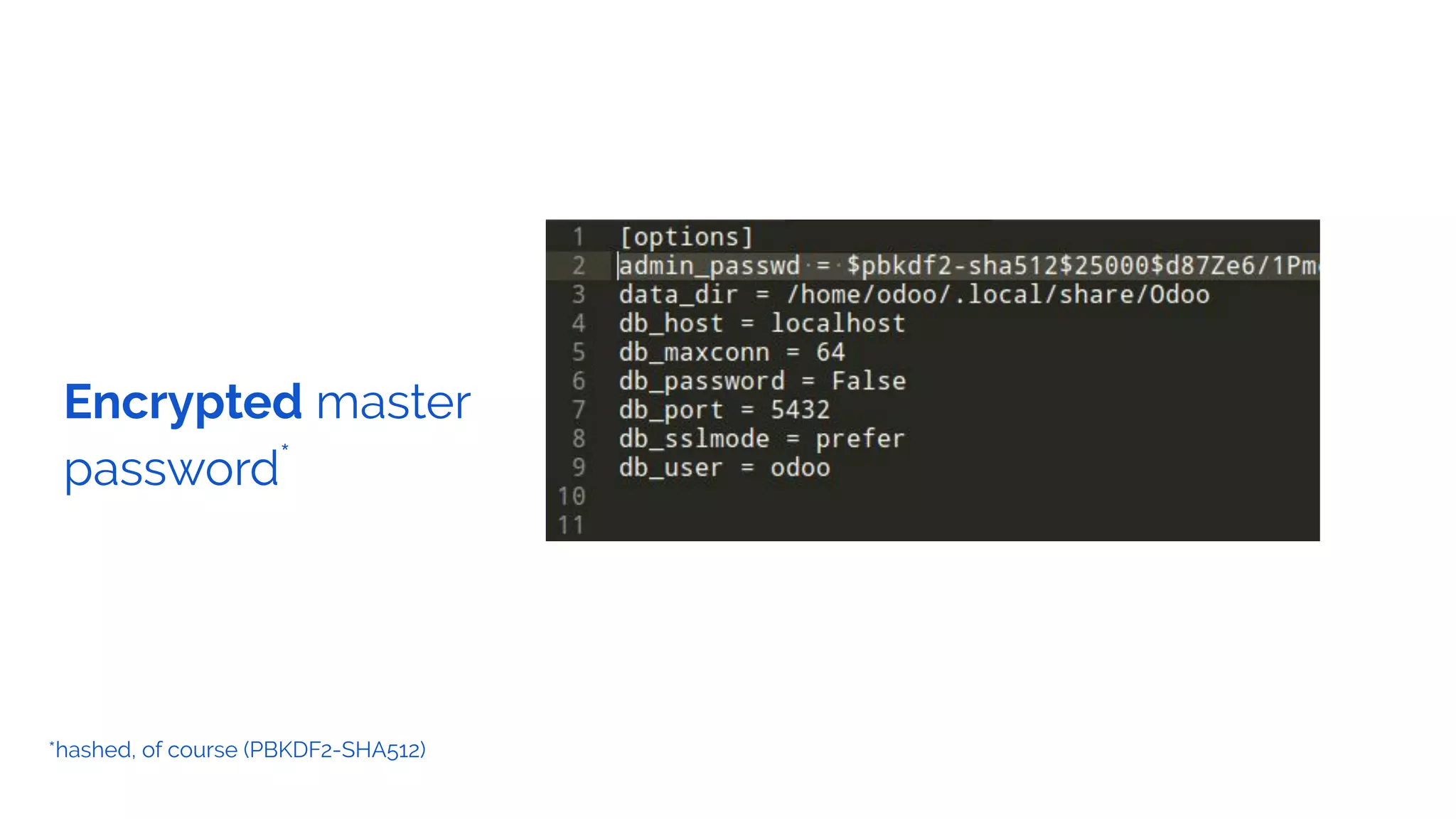
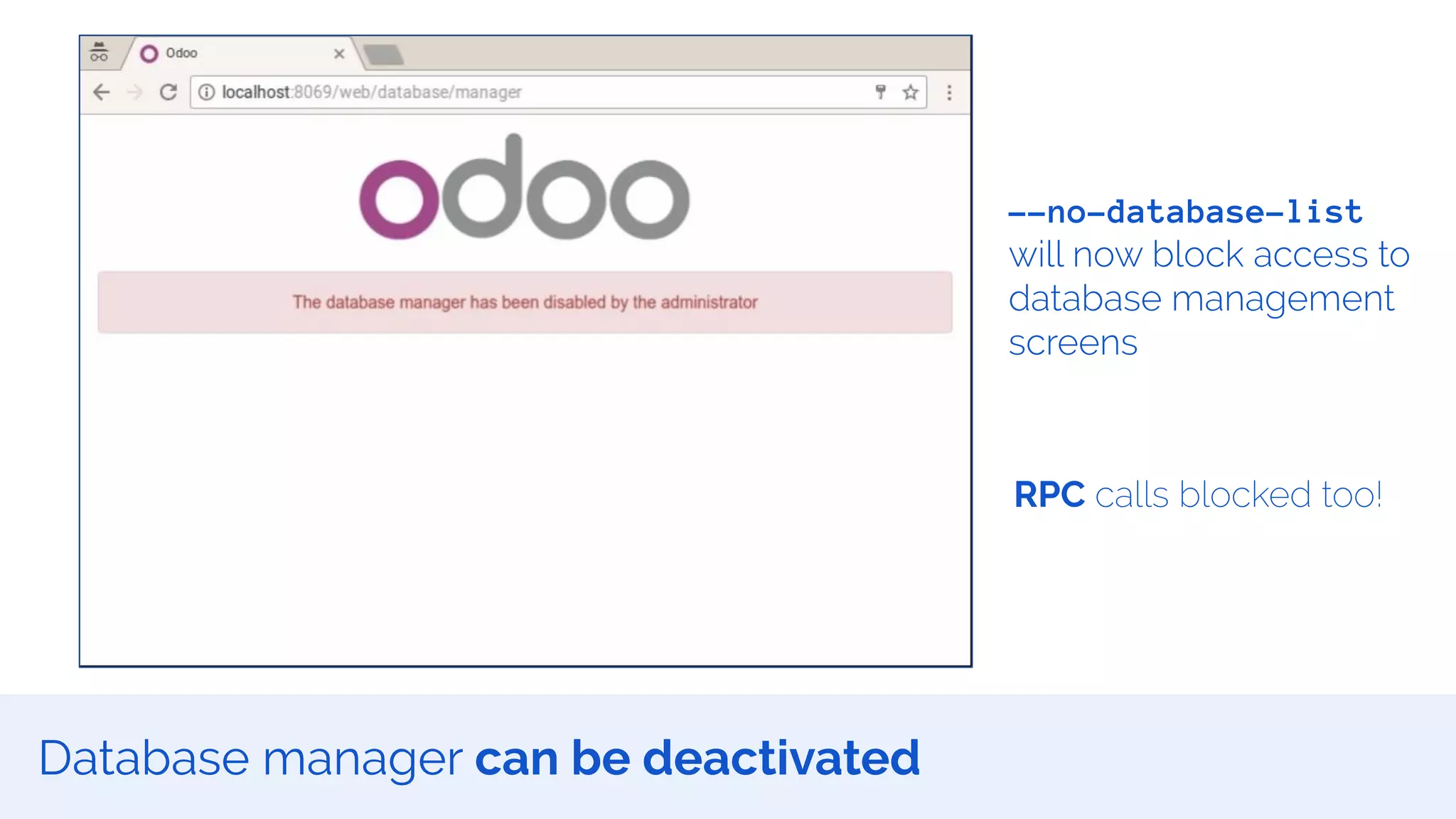
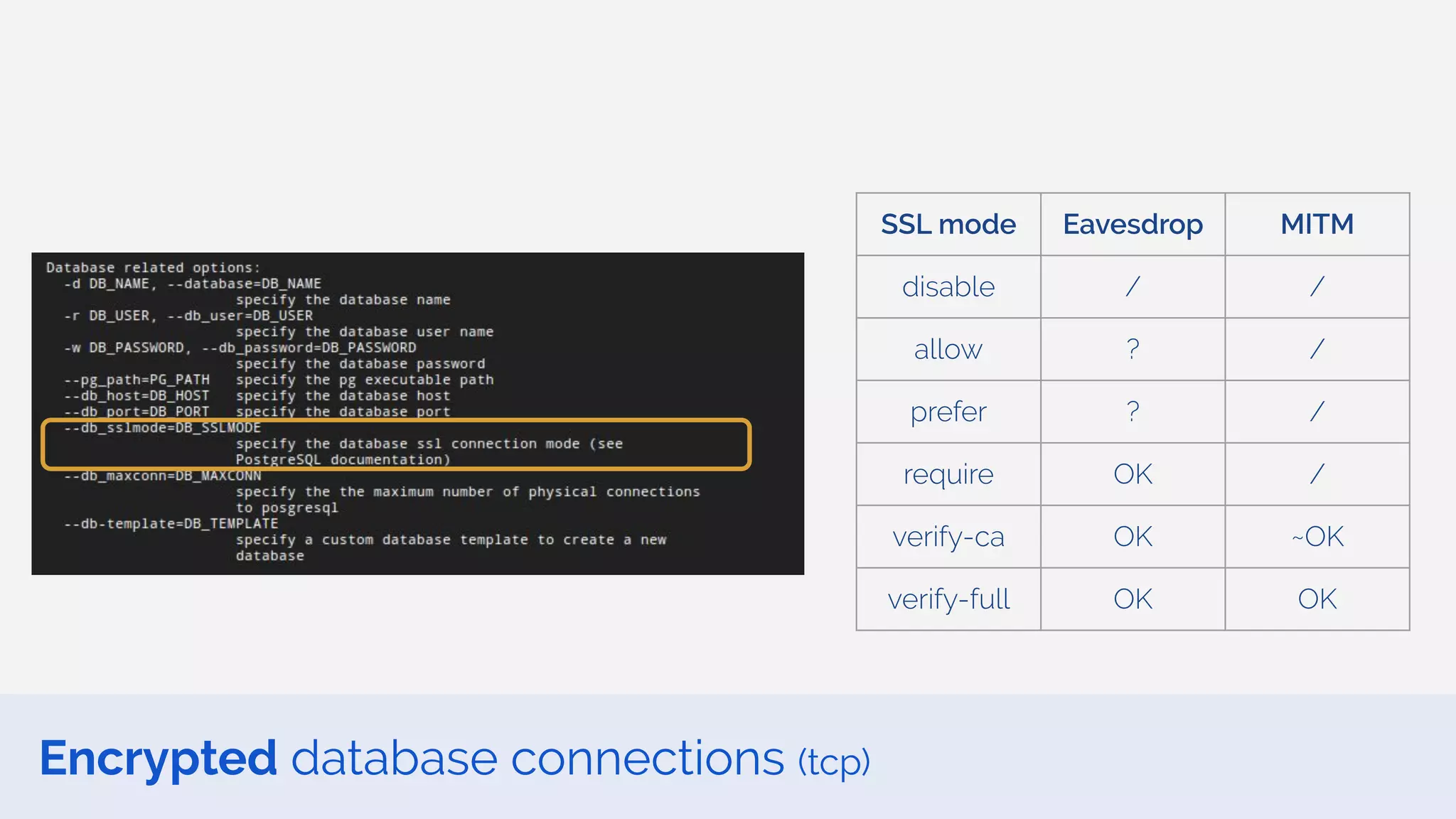
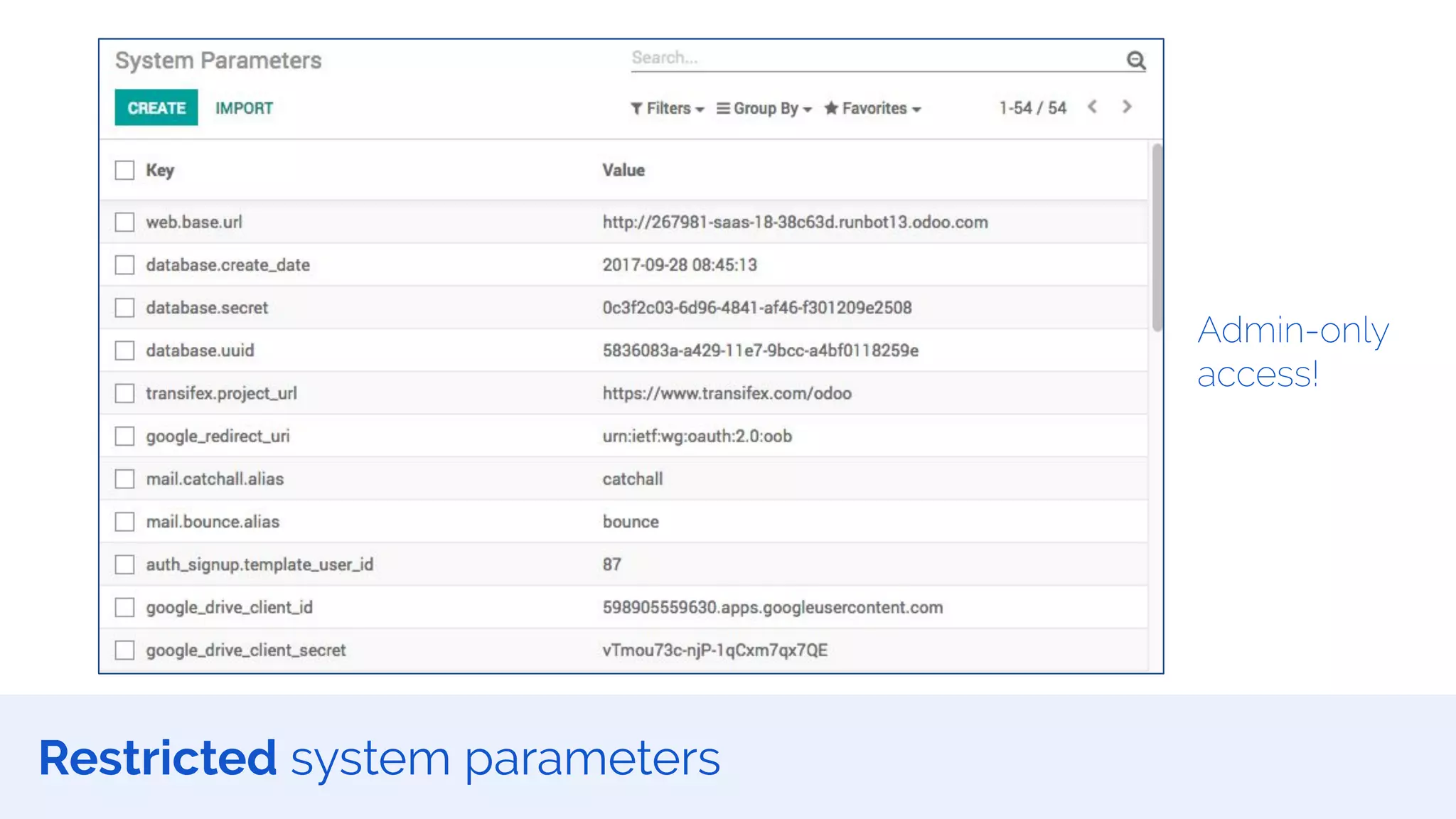
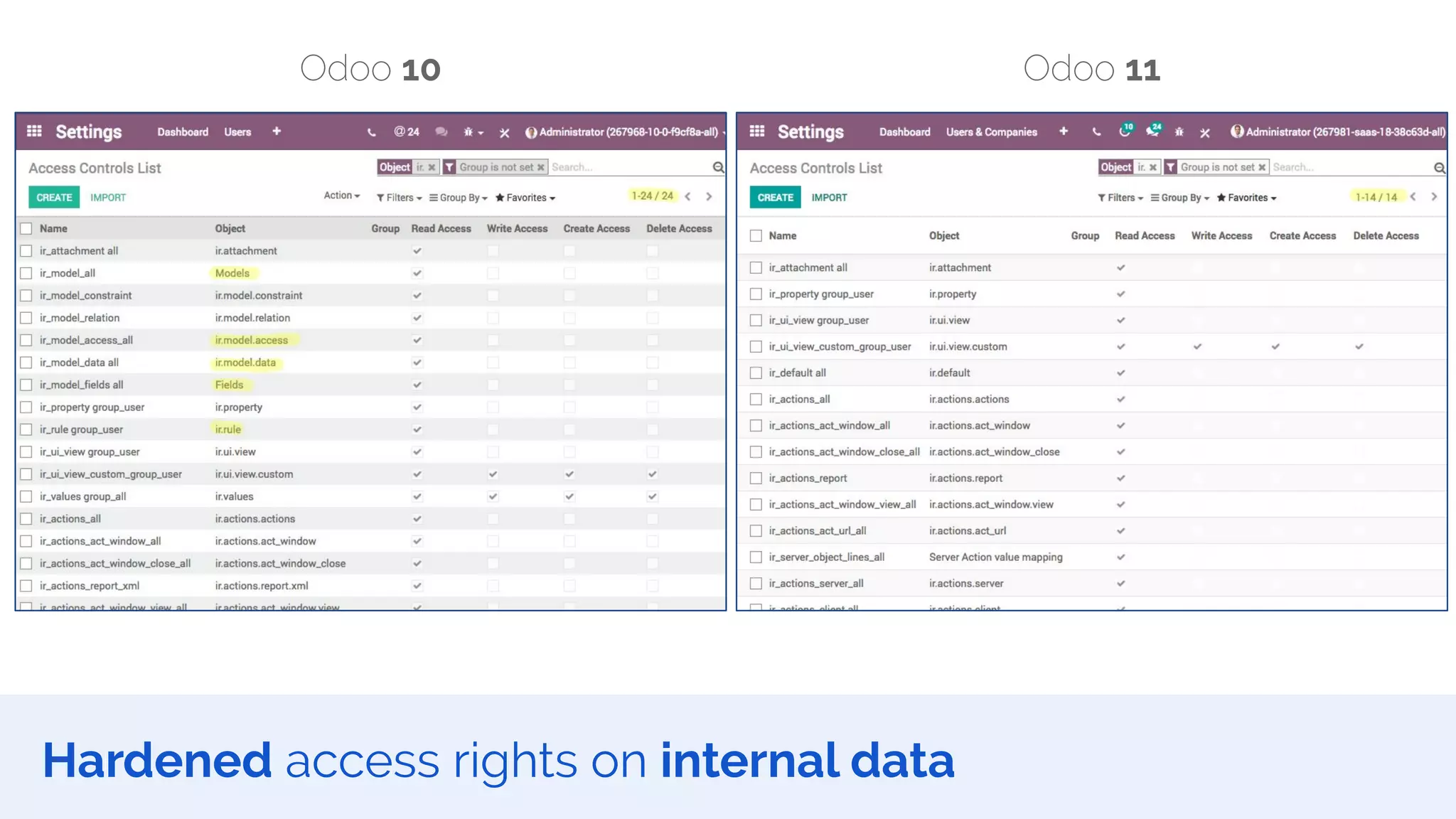
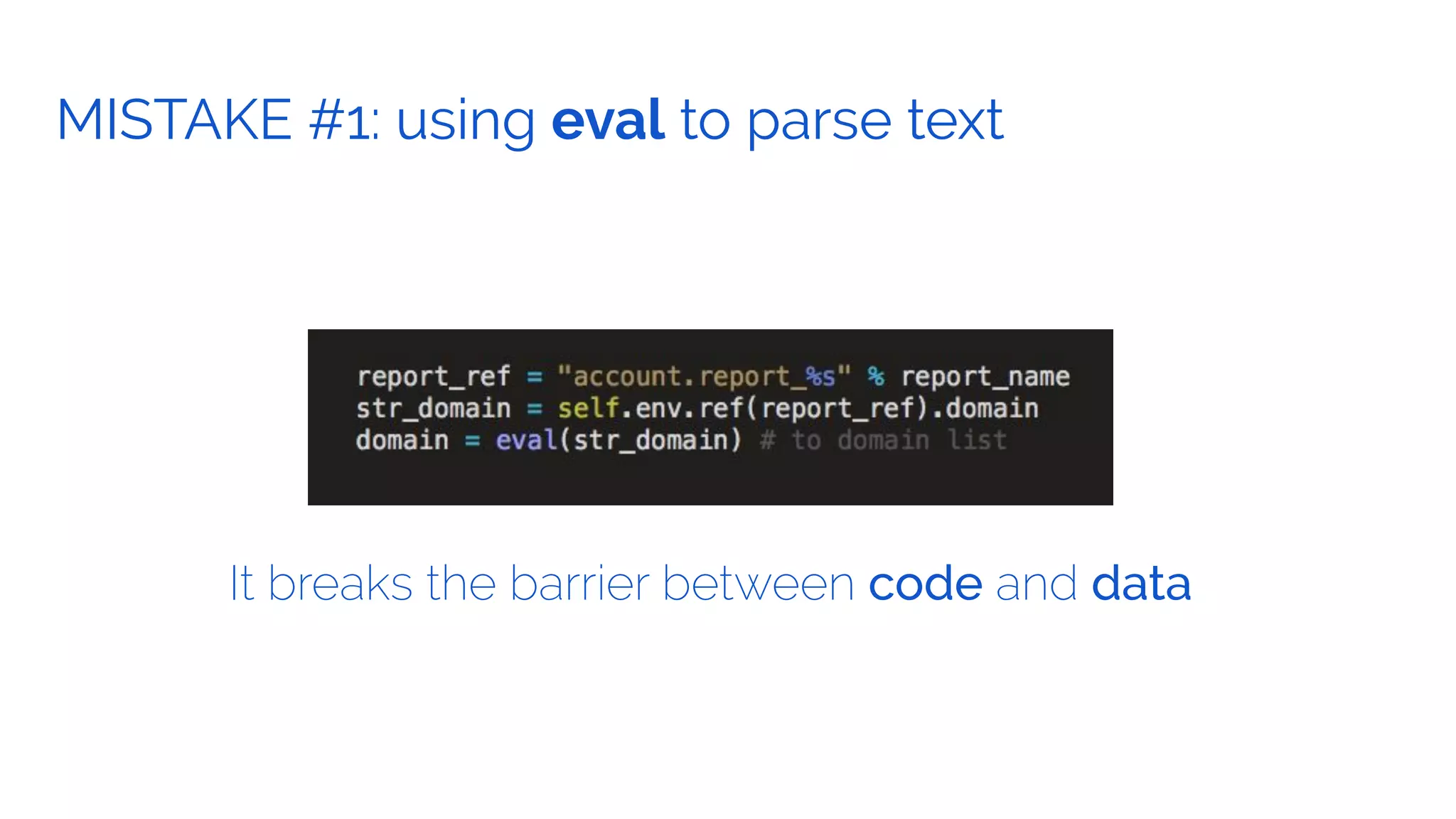
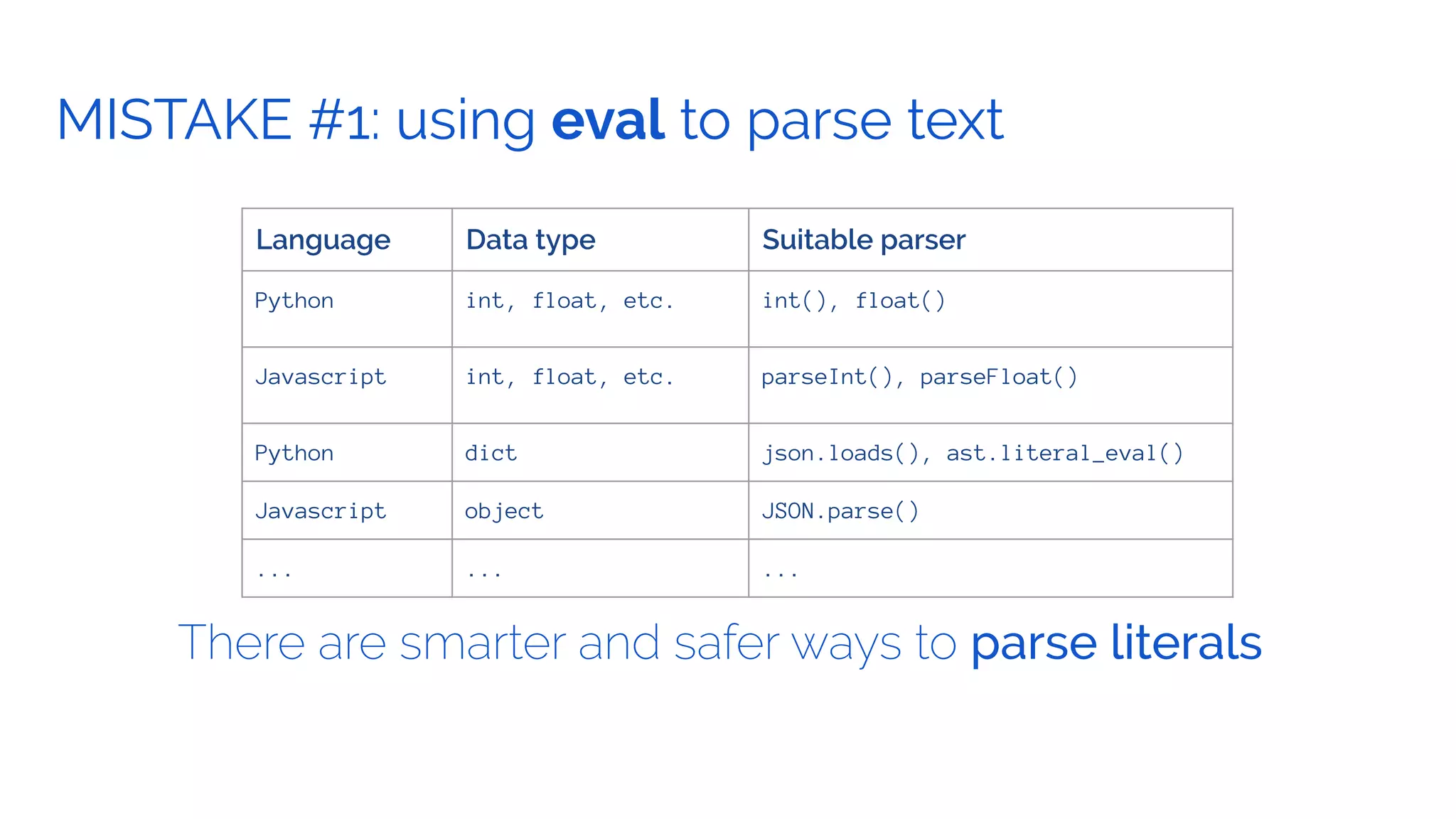
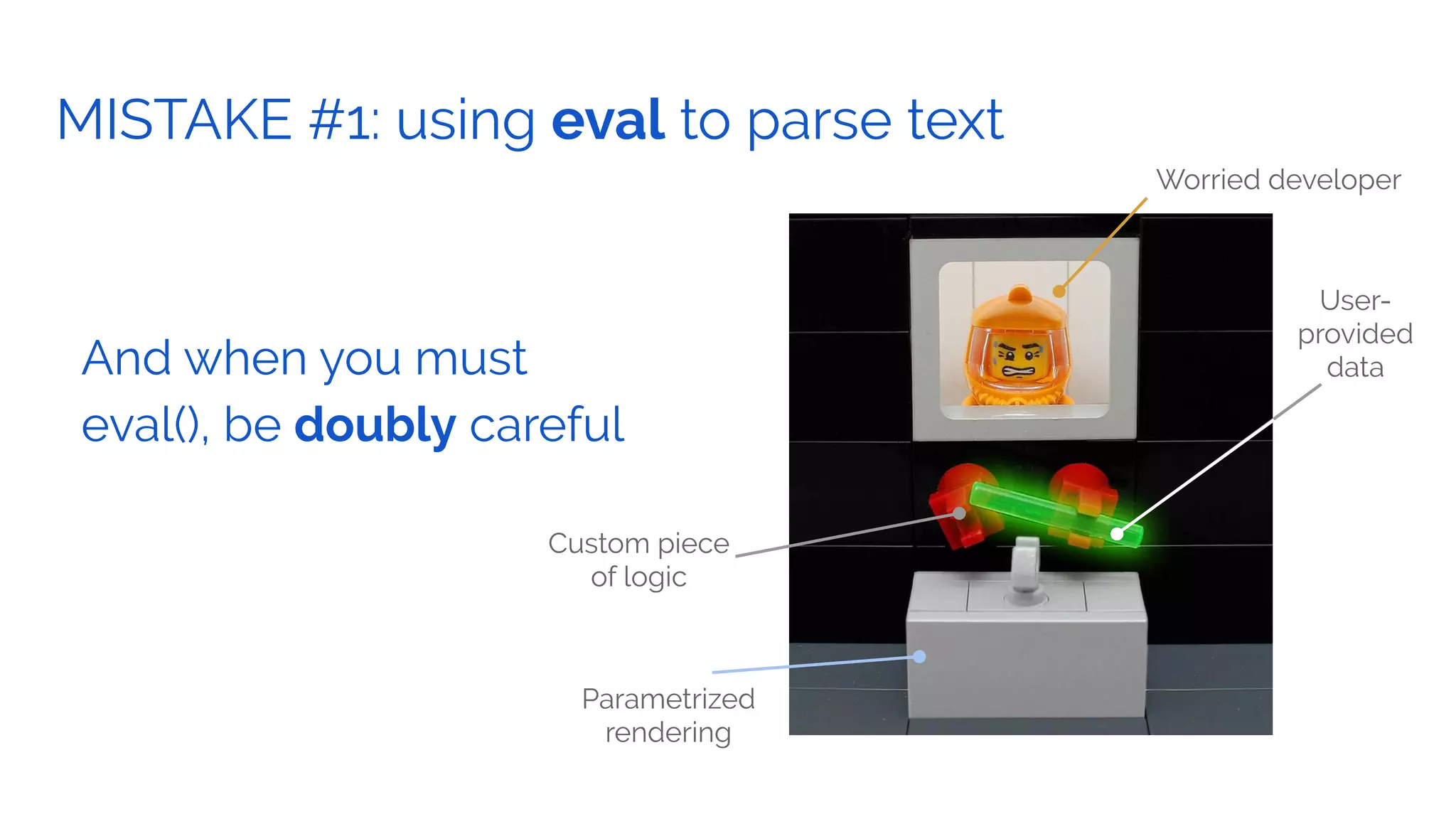
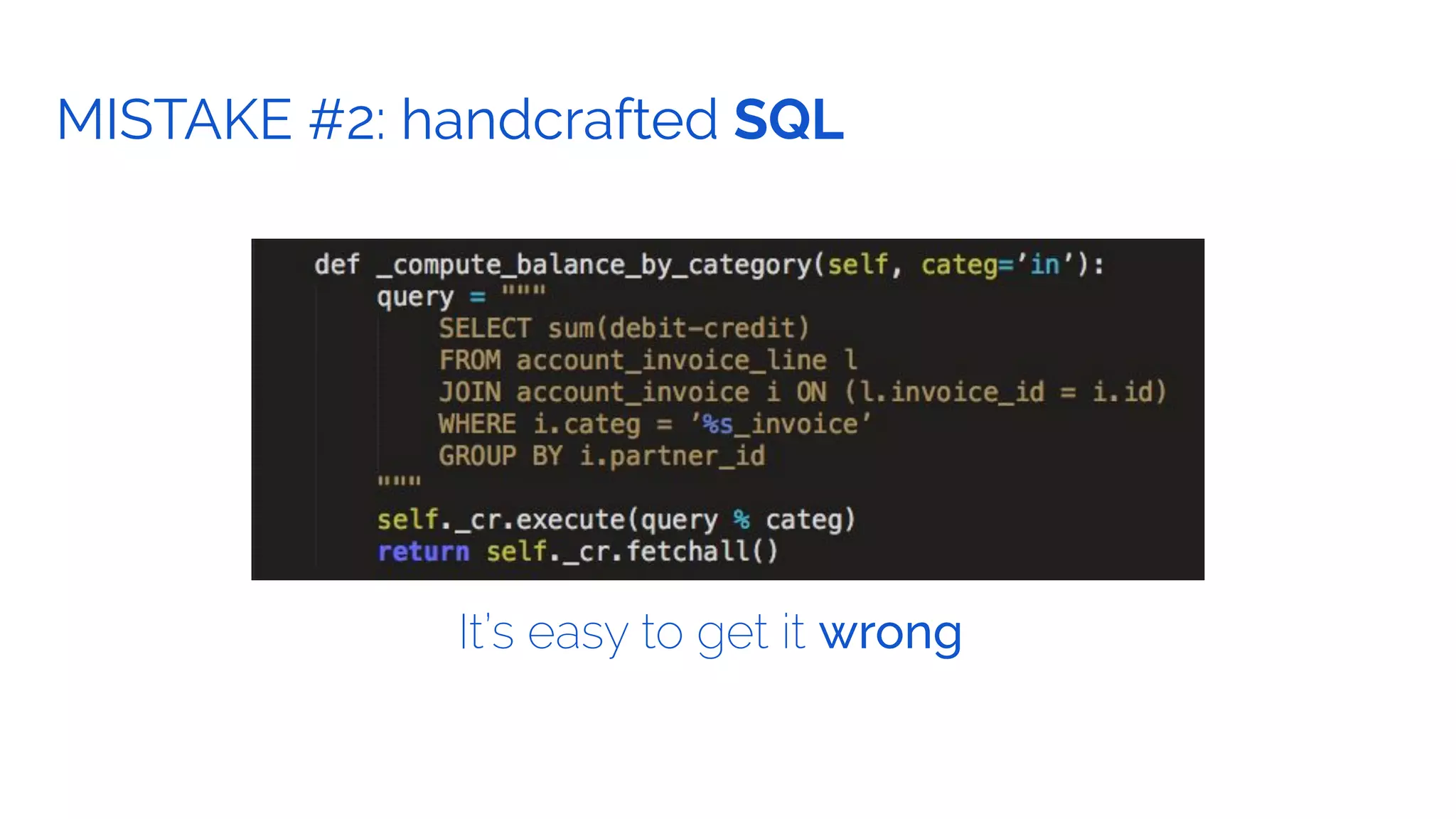
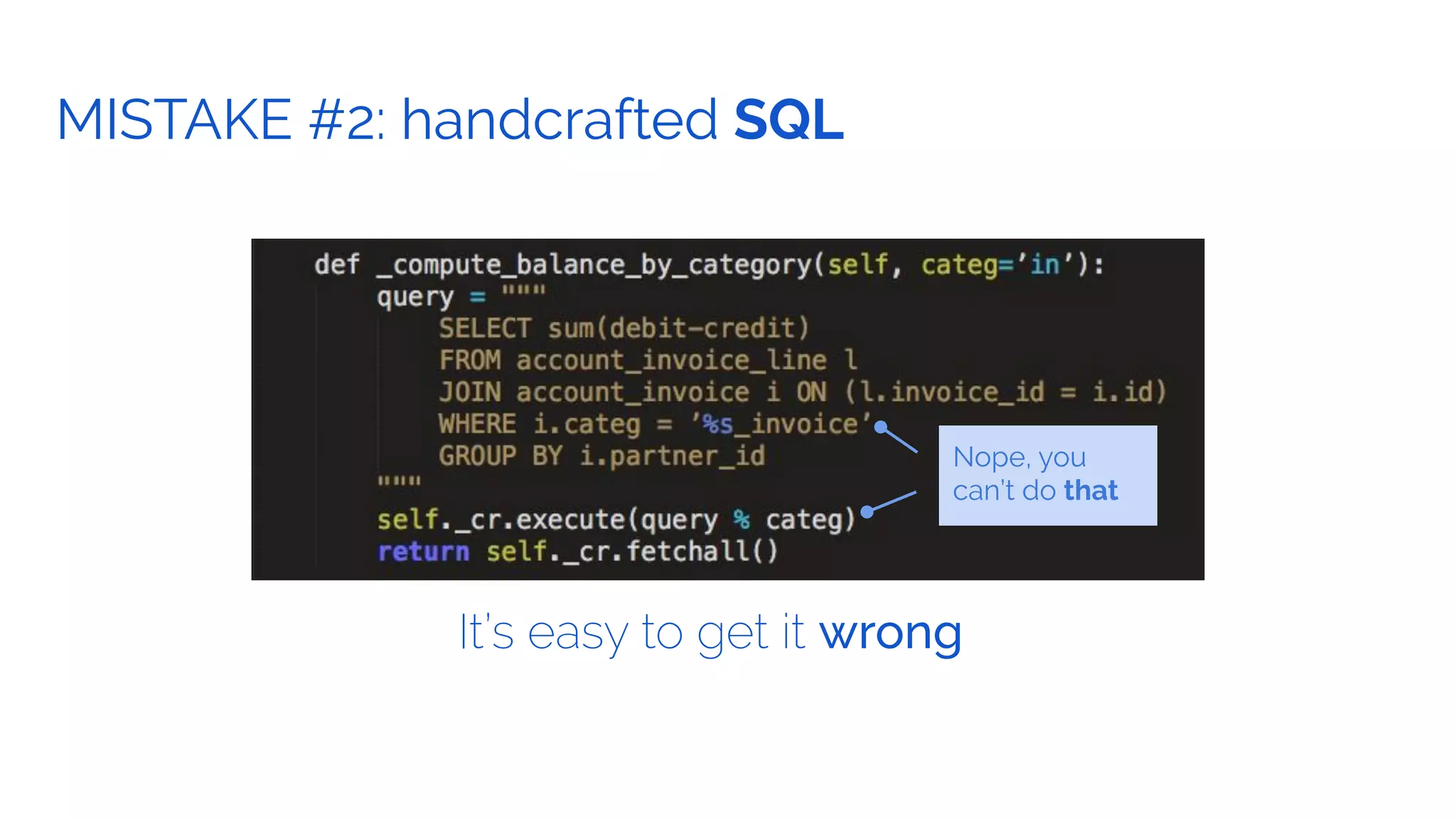
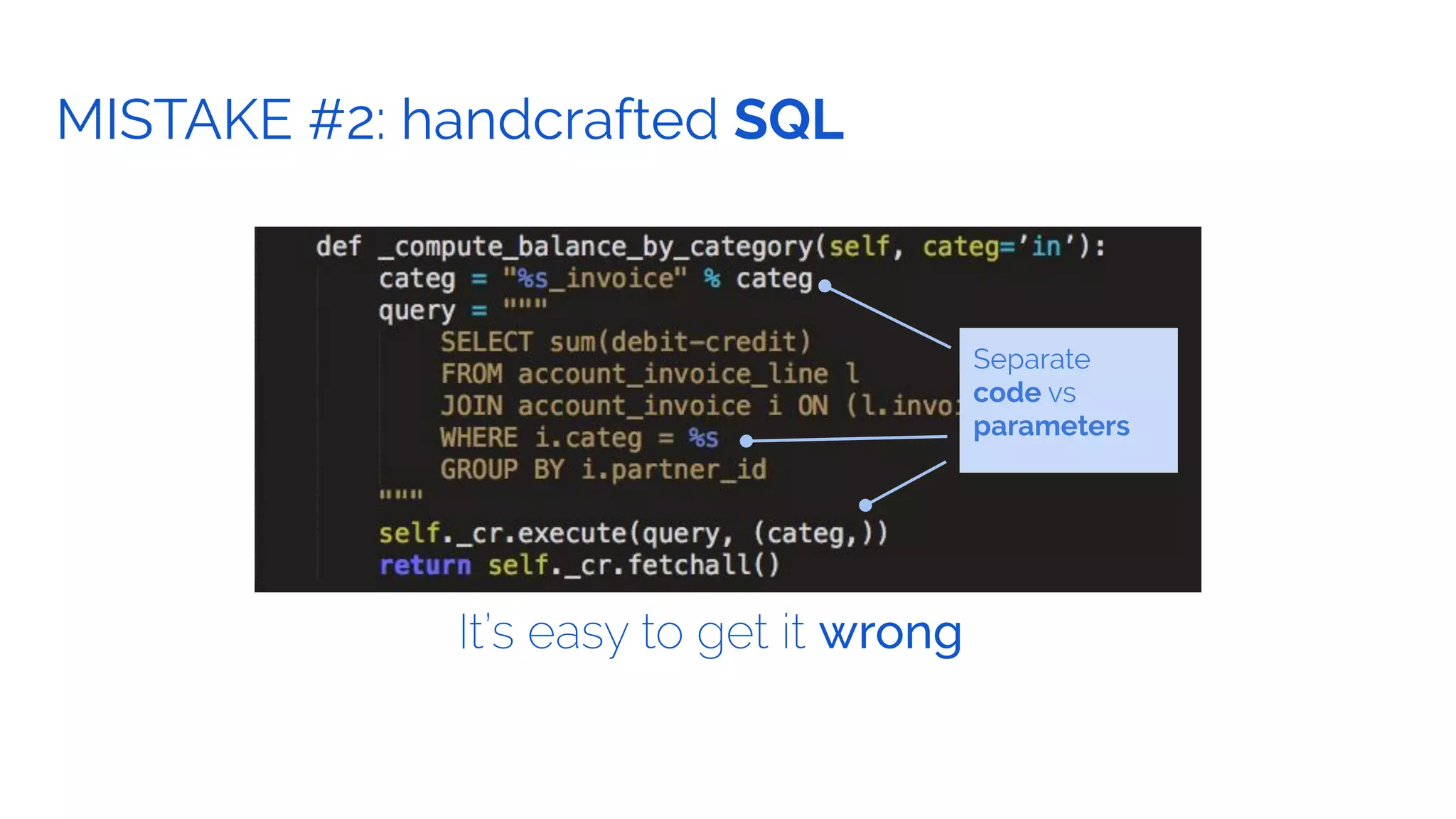
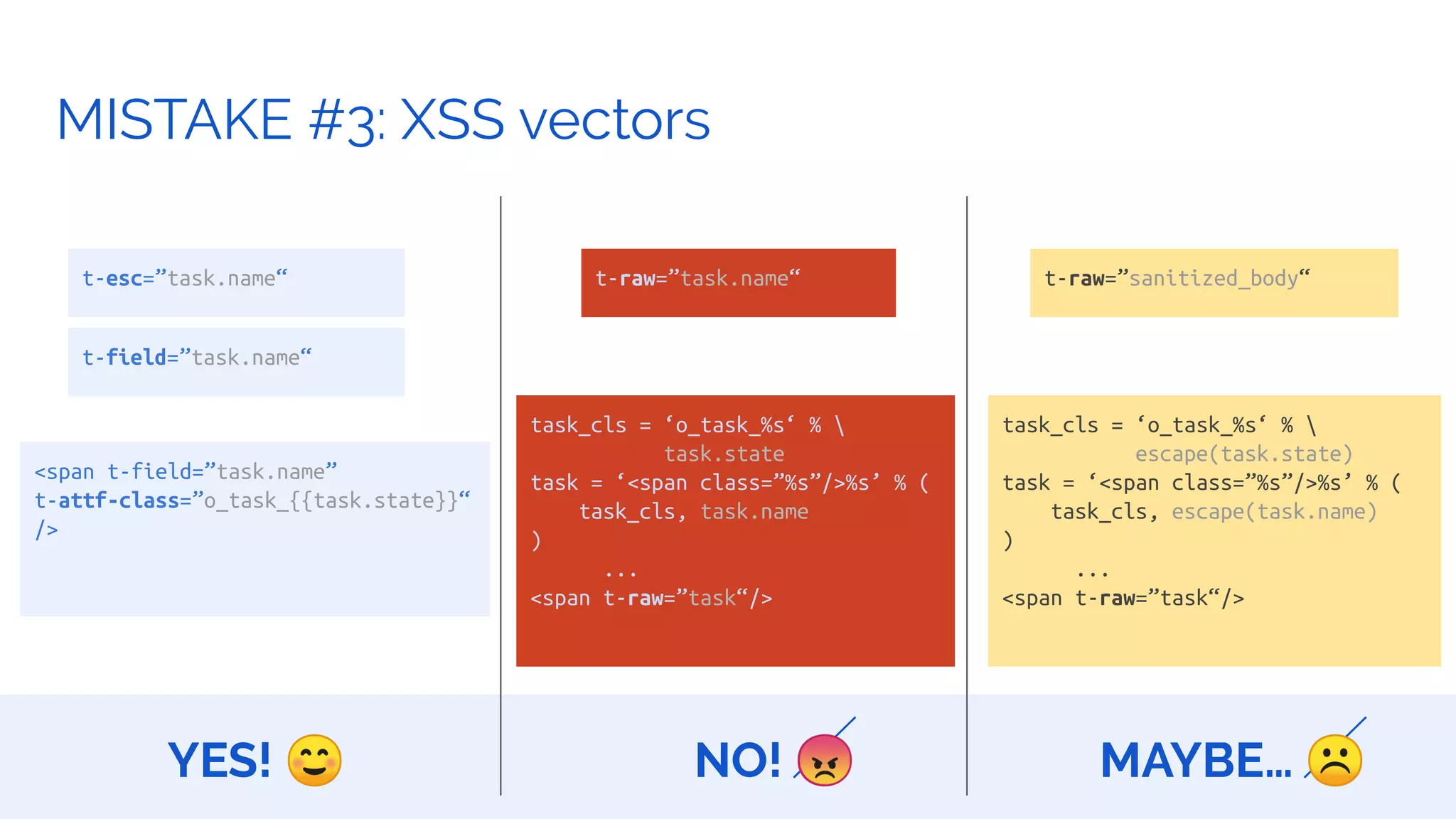
The document outlines the security framework of Odoo, detailing measures the security team implements to protect against vulnerabilities, with a focus on compliance with OWASP top 10 threats. It highlights common coding mistakes made by developers and emphasizes improved security features implemented in newer versions of the platform. The document encourages developers to engage with the security team for any inquiries or issues related to application security.