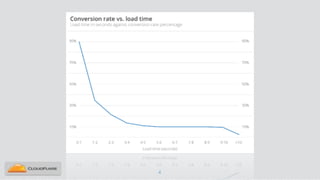
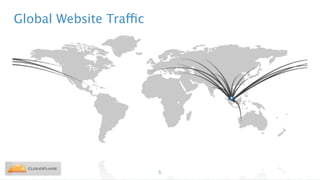
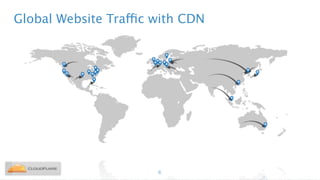
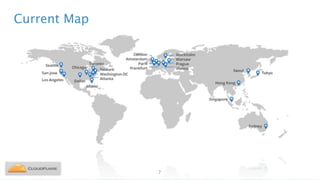
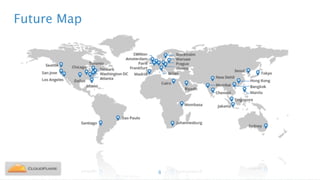
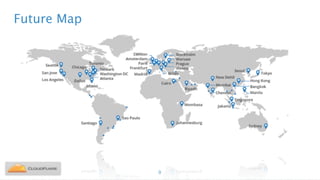
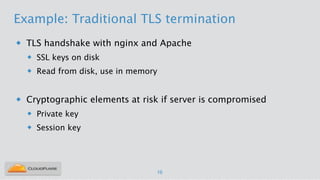
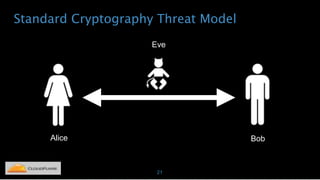
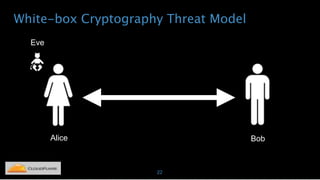
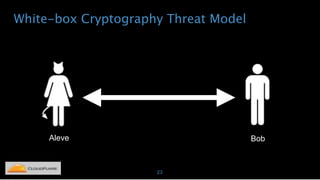
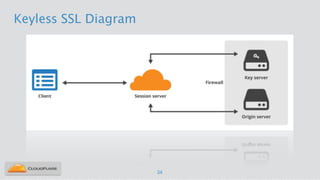
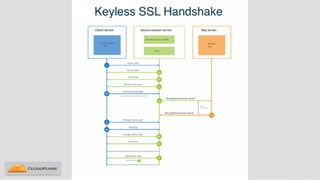
Nicholas Sullivan discusses the security challenges of running server software on globally distributed edge servers with insecure physical access. He argues for a new approach that distinguishes between long-term and short-term secrets, with the goal of refreshing secrets before attackers can compromise them. Short-term secrets use techniques from digital rights management like white-box cryptography and code obfuscation to impose computational costs on extracting secrets from memory. Long-term secrets are not stored on edge servers and are accessed through short-term secrets.