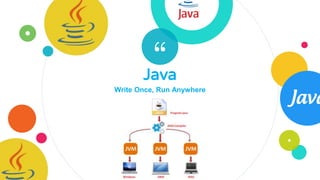
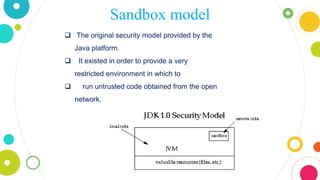
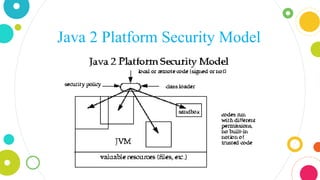
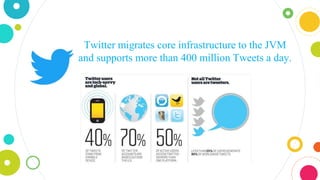
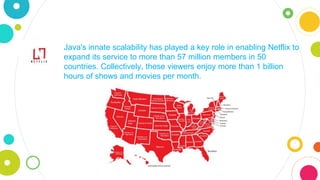
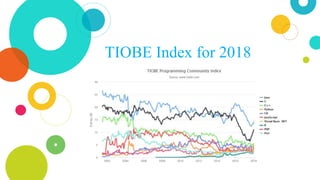
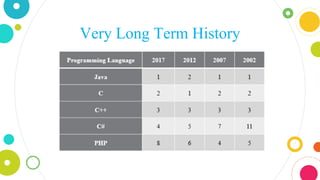
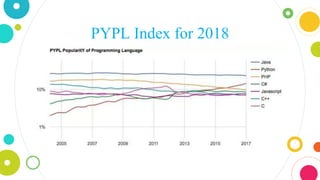
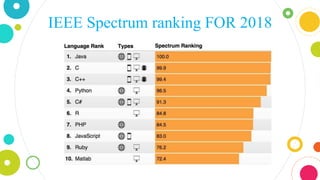
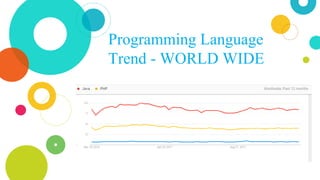
The document provides an overview of Java, discussing its definition, security models, performance, and real-world applications. It highlights Java's advantages, such as portability and scalability, and the significance of its security frameworks, including the sandbox model. Additionally, it includes statistics on Java usage and developer population, as well as references to various indices measuring its popularity.