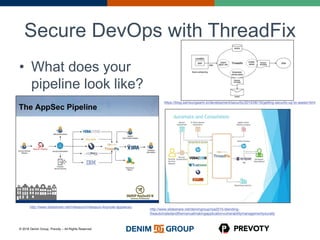
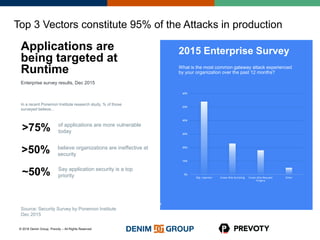
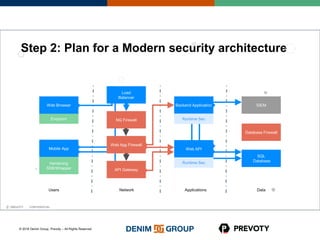
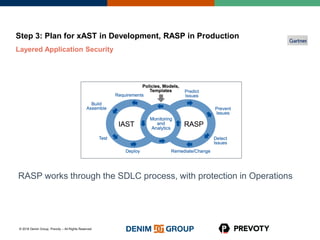
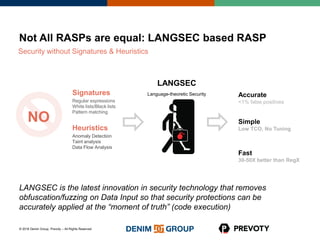
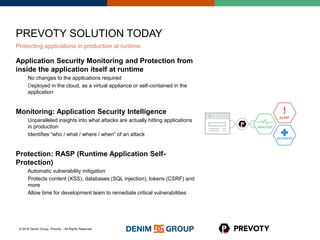
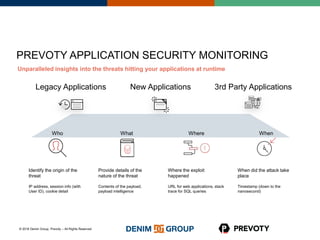
This document discusses the state of application security and the integration of Prevoty's runtime application self-protection (RASP) technology with Threadfix to enhance vulnerability management. It highlights the rising attacks on web applications and the backlog of vulnerabilities that organizations face, emphasizing the need for modern security practices. Additionally, it outlines the benefits of RASP in providing real-time protection and insights into application threats.