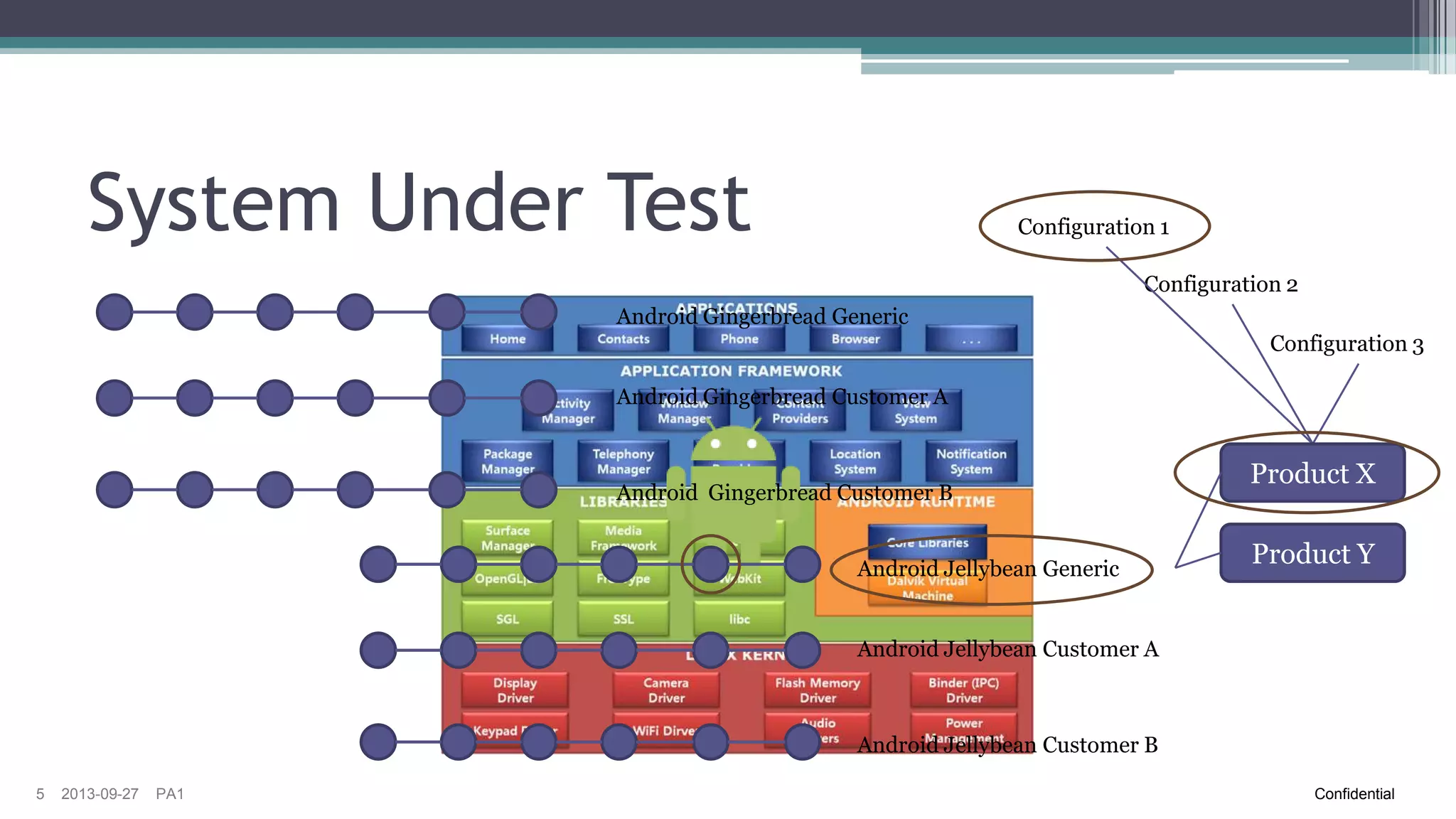
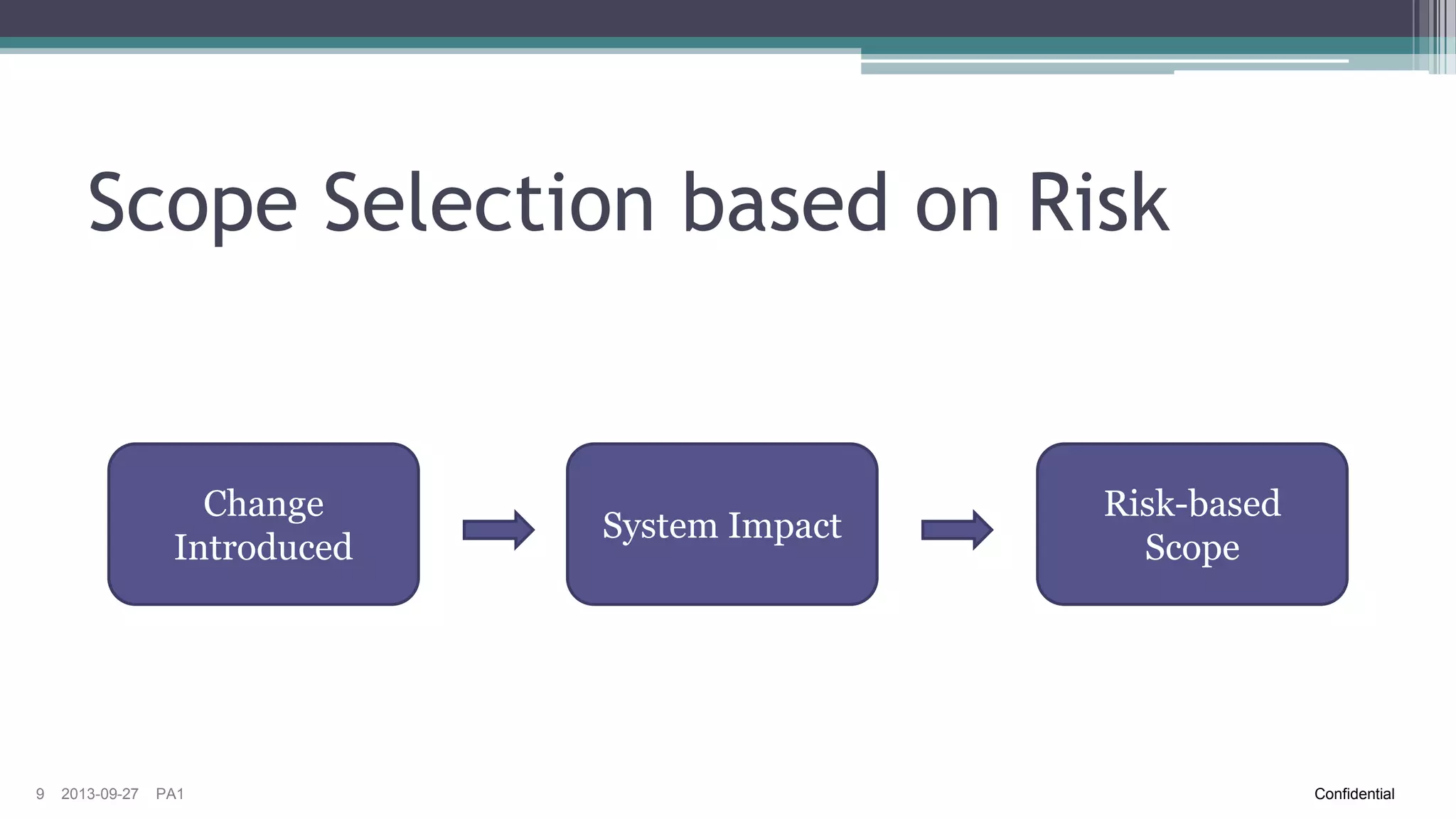
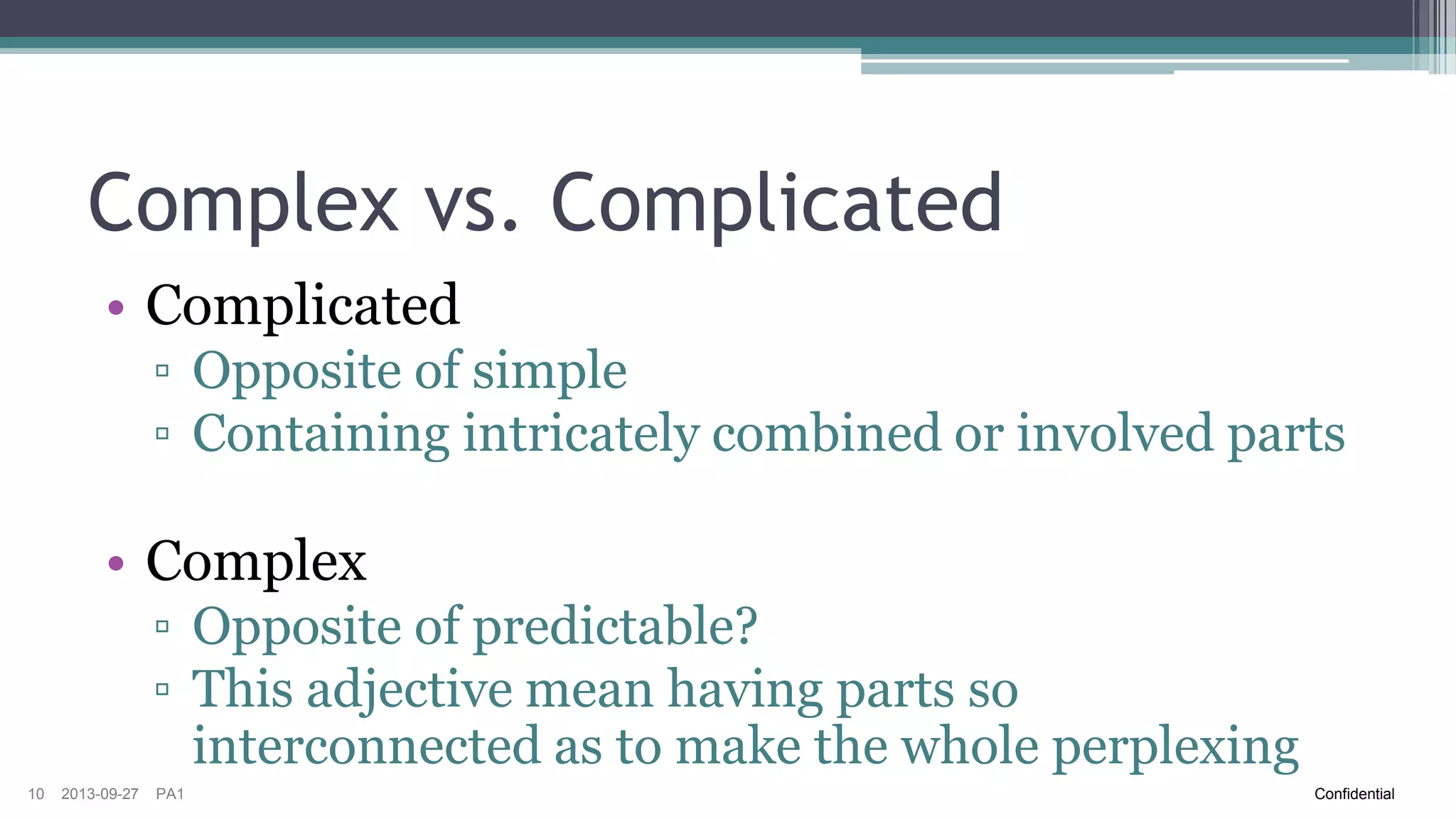
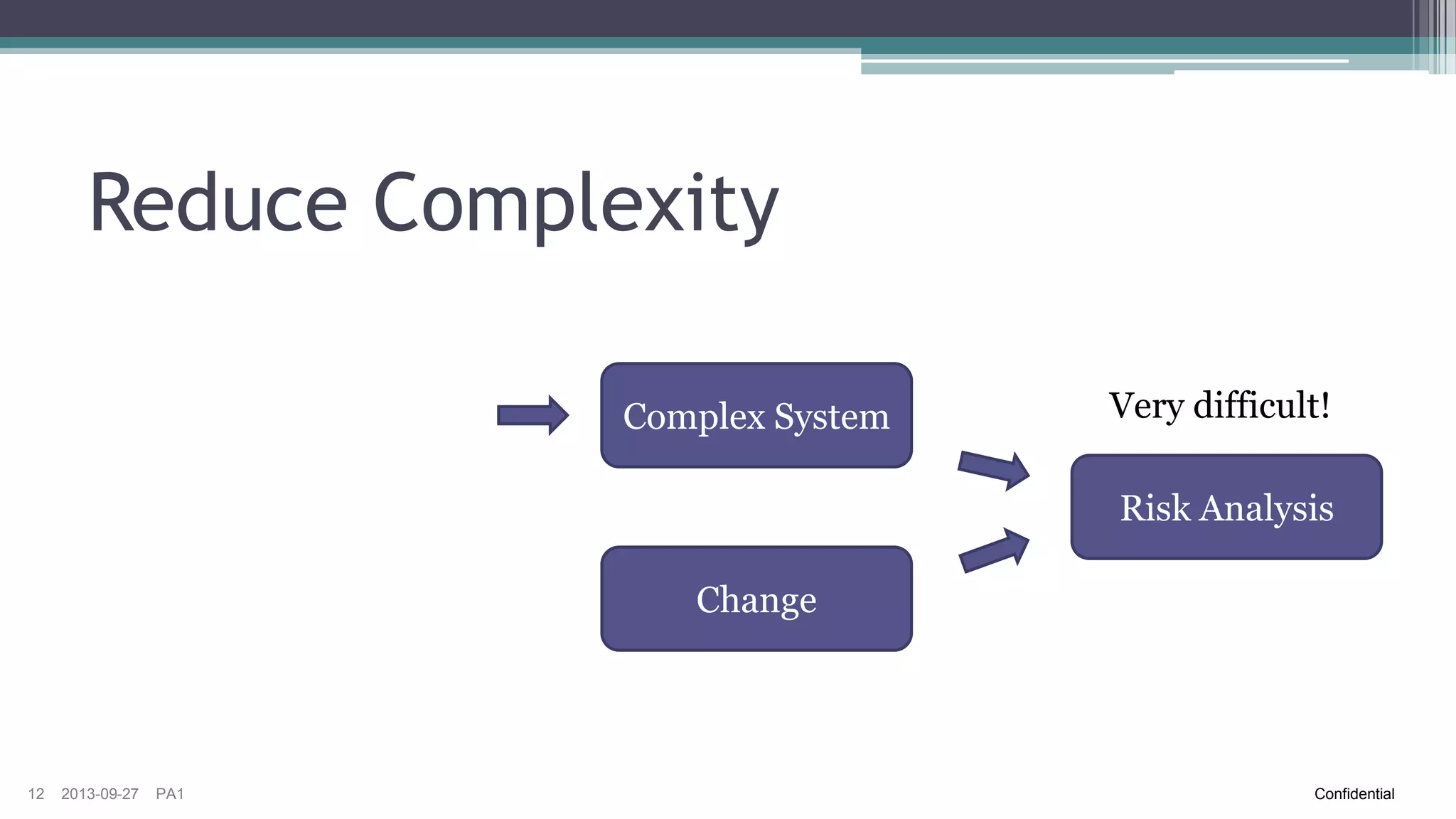
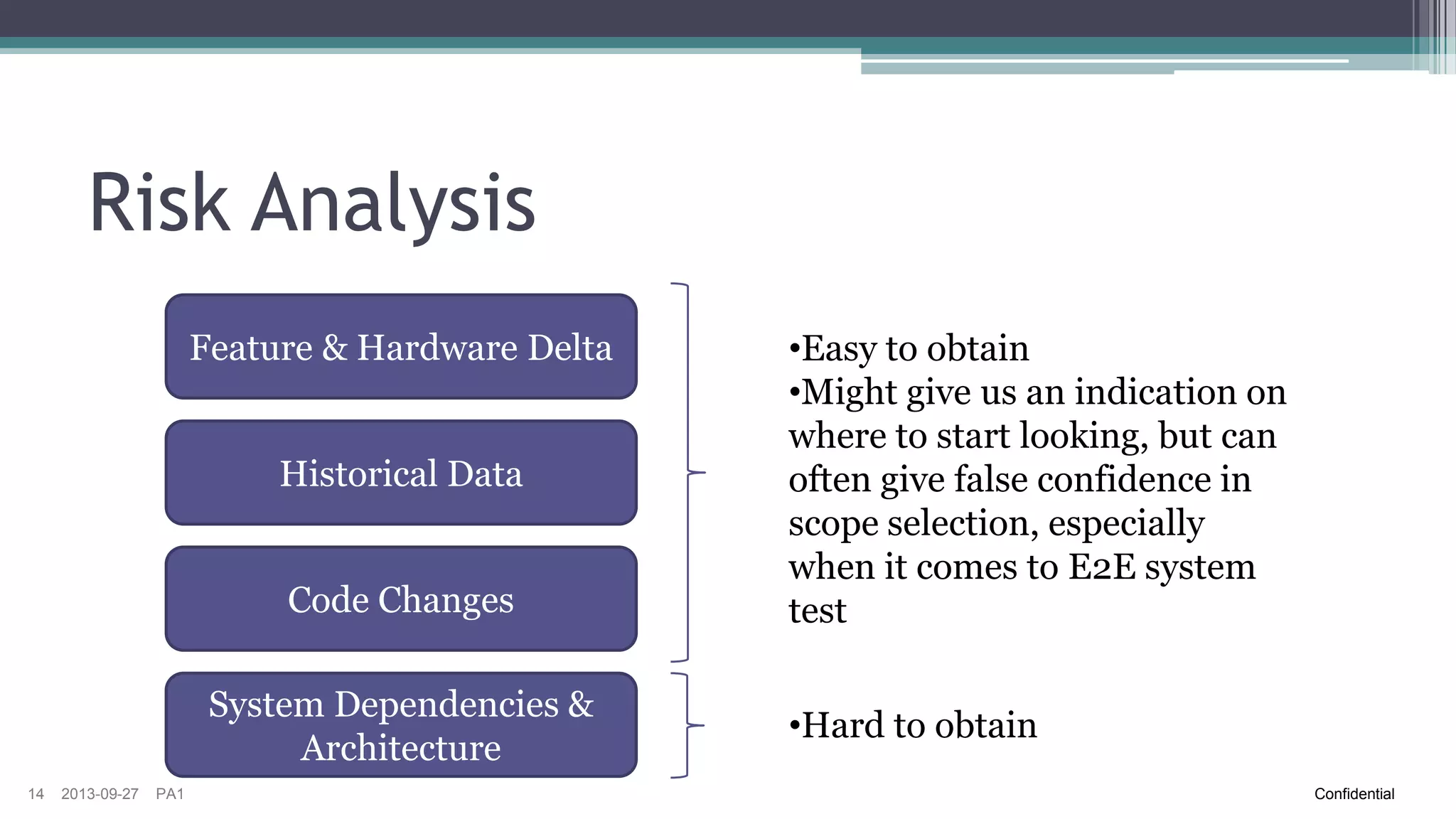
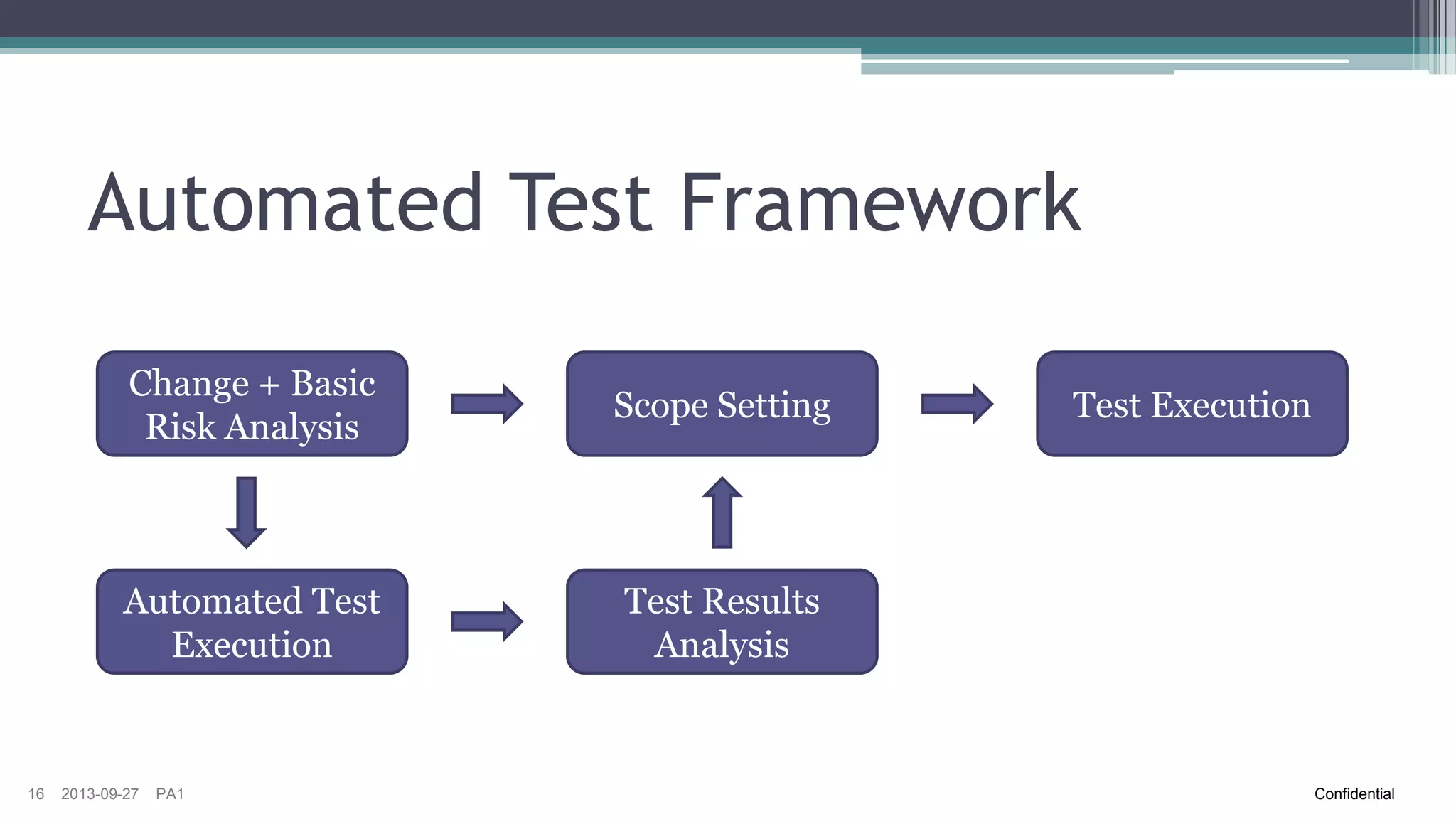
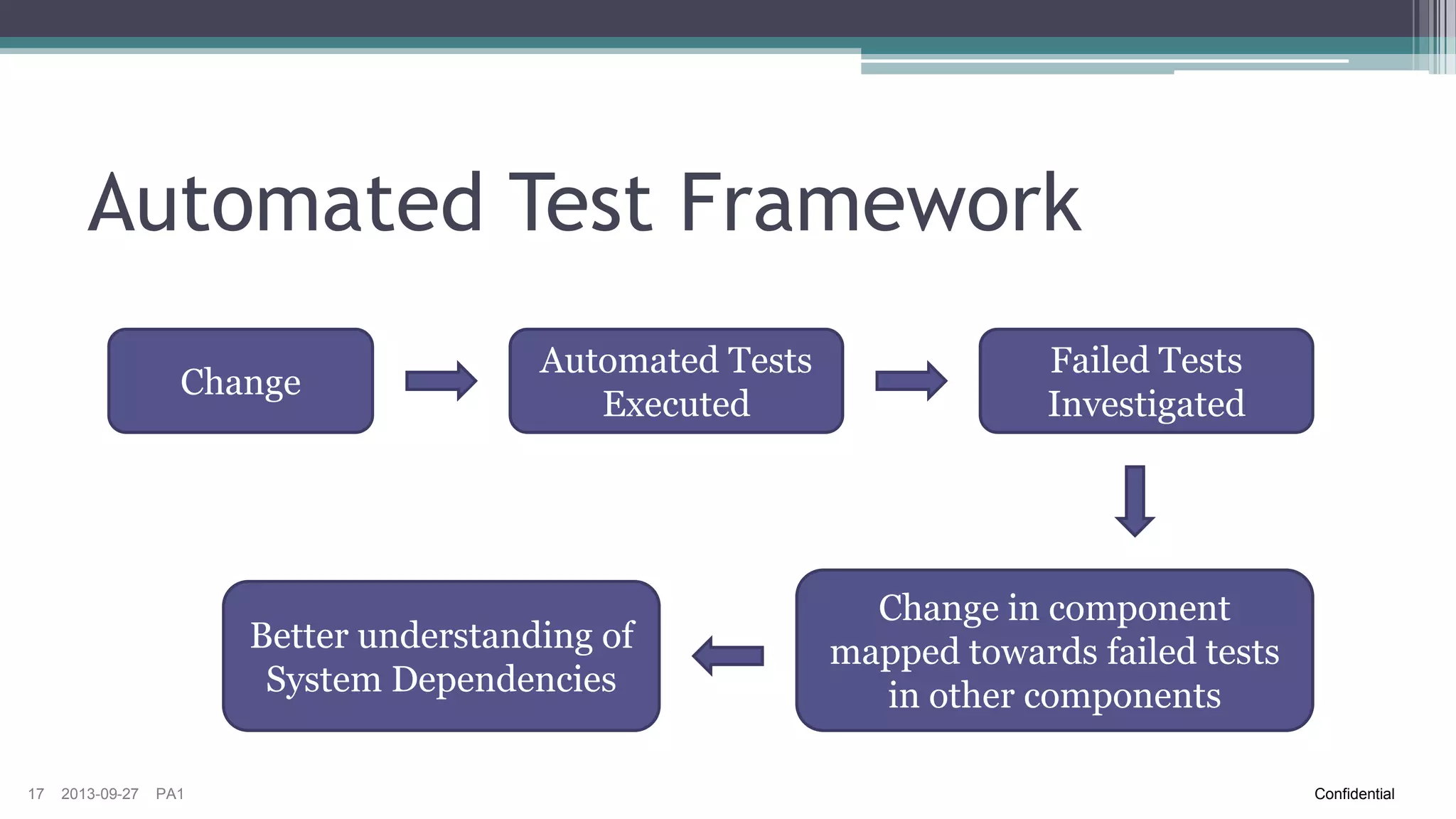
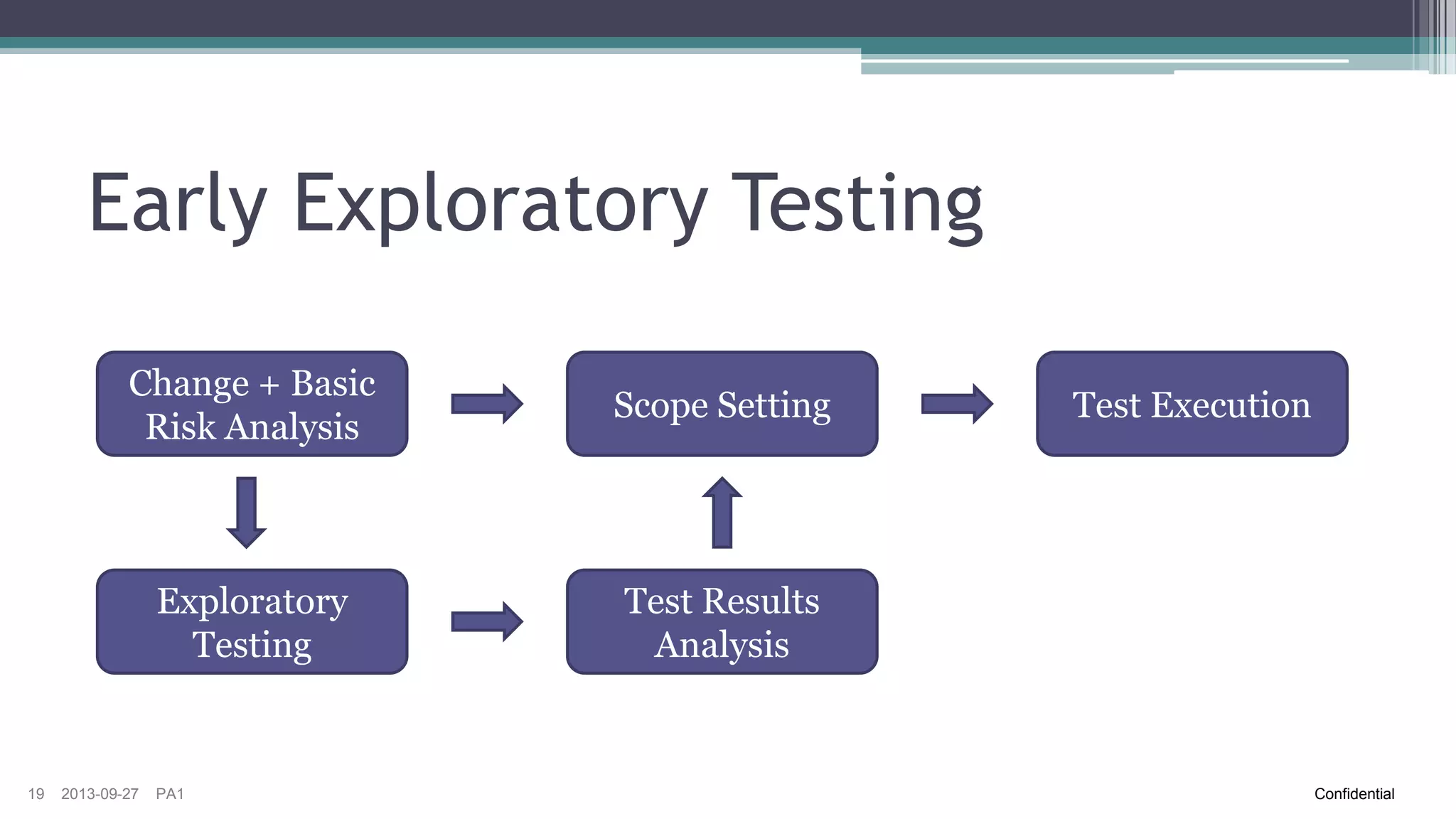
The document discusses the challenges of implementing risk-based testing for complex software systems. It explains that while risk-based testing aims to prioritize tests based on risk, determining the appropriate test scope for changes in a complex system with many configurations and dependencies is difficult. The key challenges identified are understanding the system dependencies, collecting relevant data over time to learn how changes impact the system, and ensuring tests and manual exploratory testing sessions adequately capture this information. While risk analysis, automated testing frameworks, and exploratory testing can help guide scope selection, it remains a complex problem with no simple solution.