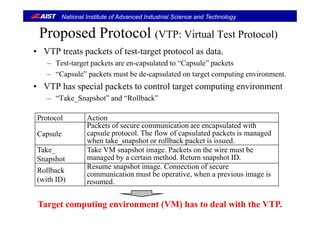
This document describes a protocol test generator that uses nested virtual machines and rollback mechanisms to perform exhaustive fuzz testing of protocol implementations. It proposes using a virtual test protocol to encapsulate test packets and control the target virtual machine. Special packets allow taking snapshots of the target VM state and rolling back to previous snapshots to repeatedly test protocol states with different fuzzed packets. The current prototype implements this approach with KVM and QEMU virtual machines to find bugs in TLS/SSL protocol implementations through fuzz testing of the handshake process.
![National Institute of Advanced Industrial Science and Technology
Motivation 1/2Motivation 1/2
• Sec re protocols (SSL/TLS SSH etc) are important for• Secure protocols (SSL/TLS, SSH, etc) are important for
Internet commerce.
l bili i f i l i f• However, vulnerabilities of implementation of secure
protocols are discovered repeatedly.
– Incidents of SSL/TLS vulnerabilities
• Insufficient entropy of random numbers [2012]
– It creates same secret-keys for SSL/TLS certificates.It creates same secret keys for SSL/TLS certificates.
– EFF offers a site to check SSL certificates.
» https://www.eff.org/observatory
• CRIME[2012]• CRIME[2012]
– It attacks to the data compression used by the TLS and SPDY.
• Lucky Thirteen[2013]
– It attacks padding oracle using timing side-channel.](https://image.slidesharecdn.com/acm-sac2014-suzaki-140501200238-phpapp02/85/Slide-used-at-ACM-SAC-2014-by-Suzaki-2-320.jpg)
![National Institute of Advanced Industrial Science and Technology
Motivation 2/2Motivation 2/2
• The implementations of secure protocols should be verified.
• Our group increases TLS security with 2 approaches.
F l ifi i– Formal verification
• Verify important parts of protocol hander program.
– “Formal Network Packet Processing with Minimal Fuss: Invertible Syntax Descriptions atFormal Network Packet Processing with Minimal Fuss: Invertible Syntax Descriptions at
Work.” [PLPV’12]
– “Towards Formal Verification of TLS Network Packet Processing Written in C”
[PLPV’13]
– Exhaustive Protocol Fuzz Testing
• Try to check all reaction of protocol handler.
– Protocol Test Generator creates and sends many fuzzed packets to check implementation
of protocol handler.
– (Today’s Topic) Computing environment for protocol fuzz testing](https://image.slidesharecdn.com/acm-sac2014-suzaki-140501200238-phpapp02/85/Slide-used-at-ACM-SAC-2014-by-Suzaki-3-320.jpg)

![National Institute of Advanced Industrial Science and Technology
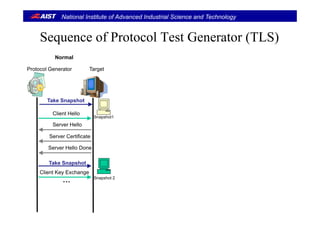
Sequence of Protocol Test Generator (TLS)Sequence of Protocol Test Generator (TLS)
Normal Fuzz for Client Hello
TargetProtocol Generator TargetProtocol Generator
Client Hello
Take Snapshot
[Fuzz1] Client Hello
Rollback Snapshot1
Client Hello
Server Hello
Server Certificate
Snapshot1
[Fuzz1] Client Hello
????
Good or Bad?
Rollback1
Server Hello Done
Take Snapshot Rollback Snapshot1
Good or Bad?
Take Snapshot
Client Key Exchange
… Snapshot 2
[Fuzz2] Client Hello
????
Rollback 1
Good or Bad?
[FuzzN] Client Hello](https://image.slidesharecdn.com/acm-sac2014-suzaki-140501200238-phpapp02/85/Slide-used-at-ACM-SAC-2014-by-Suzaki-7-320.jpg)
![National Institute of Advanced Industrial Science and Technology
Sequence of Protocol Test Generator (TLS)Sequence of Protocol Test Generator (TLS)
Normal Fuzz for Client Hello Fuzz for Client Key Exchange
TargetProtocol Generator TargetProtocol Generator TargetProtocol Generator
Client Hello
Take Snapshot
[Fuzz1] Client Hello
Rollback Snapshot1
[Fuzz1] Client Key
Rollback Snapshot2
Client Hello
Server Hello
Server Certificate
[Fuzz1] Client Hello
????
Good or Bad?
Snapshot1 Rollback
1
[Fuzz1] Client Key
Exchange
???
Rollback2
Server Hello Done
Take Snapshot Rollback Snapshot1
Good or Bad?
Rollback Snapshot2
Good or Bad?
Take Snapshot
Client Key Exchange
…
[Fuzz2] Client Hello
????
Snapshot 2 Rollback 1 Rollback 2
[Fuzz2] Client Key
Exchange
???
[FuzzN] Client Hello
Good or Bad?
???
Good or Bad?
[FuzzN] Client Key
Exchange](https://image.slidesharecdn.com/acm-sac2014-suzaki-140501200238-phpapp02/85/Slide-used-at-ACM-SAC-2014-by-Suzaki-8-320.jpg)

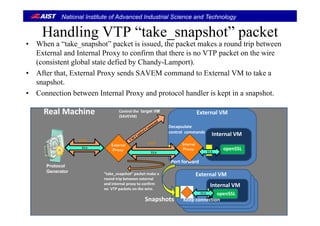
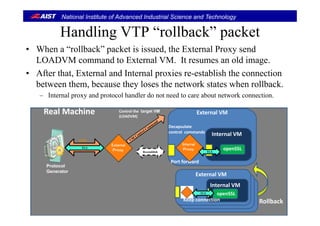
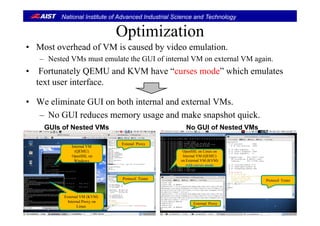
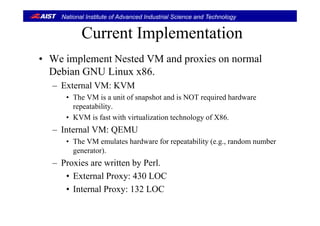
![National Institute of Advanced Industrial Science and Technology
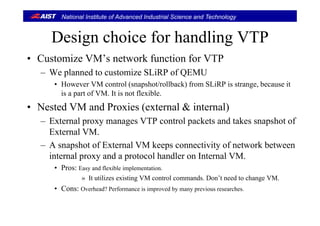
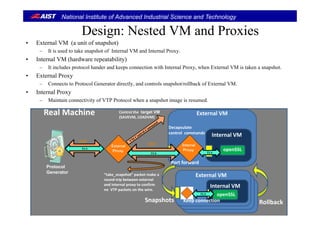
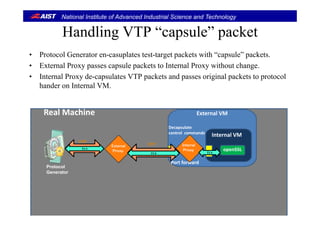
Design Issues for VM (Computing environment)Design Issues for VM (Computing environment)
• Virtual Machine runs a protocol handler.
• En-capsulated packets by VTP must be de-capsulated on a target VM.
– Original packets must be passed to a target protocol handler on the VM.
• The control packets (take_snapshot and rollback) must be dealt by the VM.
• The VTP packets on the network must be maintained.
– We have to deal with consistent global state defied by [Chandy-Lamport, 1985].
Protocol
Generator
Target Environment
Snapshots of VM
VTP
Protocol
handler
TLS
VTP
VM deals with VTP protocol.
Packets on the network
must be maintained.
VM](https://image.slidesharecdn.com/acm-sac2014-suzaki-140501200238-phpapp02/85/Slide-used-at-ACM-SAC-2014-by-Suzaki-11-320.jpg)
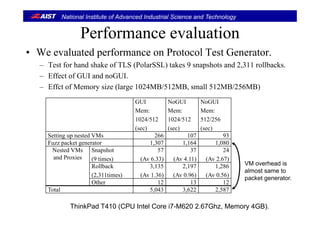
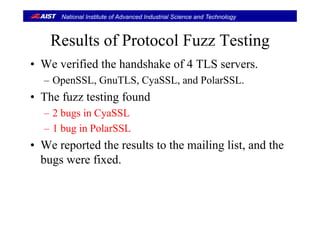
![National Institute of Advanced Industrial Science and Technology
R l t d kRelated works
• Nested VM• Nested VM
– Migration
• Xen-Blanket [EuroSys’12] enables user level migration on CloudXen Blanket [EuroSys 12] enables user level migration on Cloud.
– Security
• CloudVisor [SOSP’11] is inserted on existing VM on multi-tenant
Cloud.
• Process level snapshot
– DMTCP: Distributed Multi Threaded Check Pointing
• http://dmtcp.sourceforge.net/
If d ’t t d t b t h d l l t bilit f• If we don’t not need to care about hardware-level repeatability for
rollback, DMTCP will be a candidate for protocol test generator.](https://image.slidesharecdn.com/acm-sac2014-suzaki-140501200238-phpapp02/85/Slide-used-at-ACM-SAC-2014-by-Suzaki-21-320.jpg)