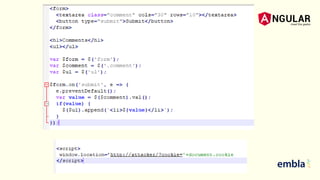
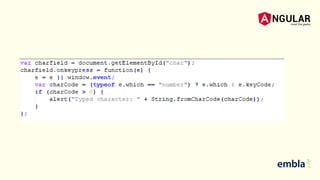
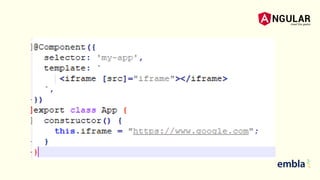
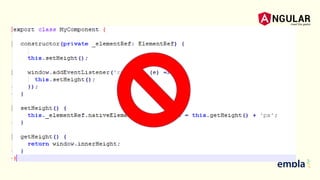
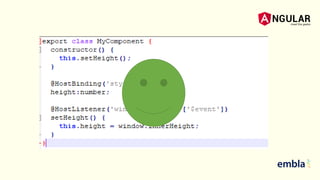
- The document discusses best practices for securing an Angular application including using the latest version of Angular, preventing XSS and XSRF attacks, avoiding direct DOM manipulations, using ahead-of-time compilation for faster rendering and better security, and never using Angular templating from the server side.
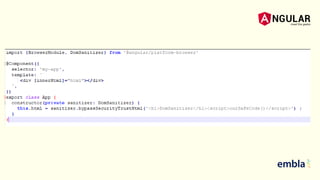
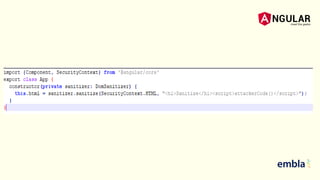
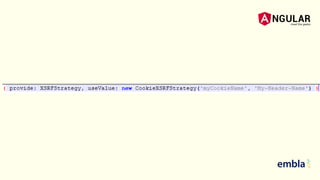
- It explains that Angular sanitizes and escapes untrusted values by default to prevent XSS and that the HttpClient has support for cookie-based XSRF protection.
- Macaroons are also mentioned as a way to implement decentralized authorization across multiple languages.