The document outlines a presentation by Matt Raible on Java web application security, focusing on development, penetration, protection, and relaxation techniques. It covers topics such as Java EE 6 security features, Spring Security, Apache Shiro, OWASP Top 10 vulnerabilities, and testing methodologies. The session aims to enhance participants' understanding of implementing security measures in Java web applications and demonstrates practical security implementations.










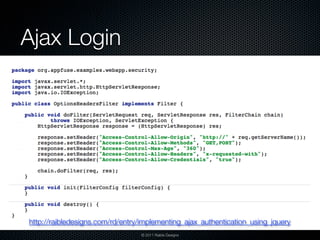
![Securing Methods
<global-method-security secured-annotations="enabled"/>
@Secured("IS_AUTHENTICATED_ANONYMOUSLY")
public Account readAccount(Long id);
@Secured("IS_AUTHENTICATED_ANONYMOUSLY")
public Account[] findAccounts();
@Secured("ROLE_TELLER")
public Account post(Account account, double amount);
<global-method-security jsr250-annotations="enabled"/>
© 2011 Raible Designs](https://image.slidesharecdn.com/javawebapplicationsecurityujug2011-110505121131-phpapp02/85/Java-Web-Application-Security-Utah-JUG-2011-15-320.jpg)
![Securing Methods 3.0
<global-method-security pre-post-annotations="enabled"/>
@PreAuthorize("isAnonymous()")
public Account readAccount(Long id);
@PreAuthorize("isAnonymous()")
public Account[] findAccounts();
@PreAuthorize("hasAuthority('ROLE_TELLER')")
public Account post(Account account, double amount);
© 2011 Raible Designs](https://image.slidesharecdn.com/javawebapplicationsecurityujug2011-110505121131-phpapp02/85/Java-Web-Application-Security-Utah-JUG-2011-16-320.jpg)

![Apache Shiro
Filter defined in web.xml
shiro.ini loaded from classpath
[main], [urls], [roles]
Cryptography
Session Management
© 2011 Raible Designs](https://image.slidesharecdn.com/javawebapplicationsecurityujug2011-110505121131-phpapp02/85/Java-Web-Application-Security-Utah-JUG-2011-18-320.jpg)