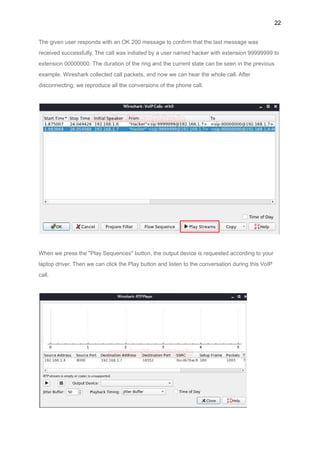
This document provides a comprehensive overview of Voice over Internet Protocol (VoIP), detailing its functionalities, history, and methods for hacking VoIP networks. It highlights the advantages and disadvantages of VoIP technology, how it works, and the protocols involved, along with a step-by-step guide on how to conduct penetration testing on VoIP systems. Key topics include VoIP equipment, system components, protocols, and the ethical considerations in security testing.